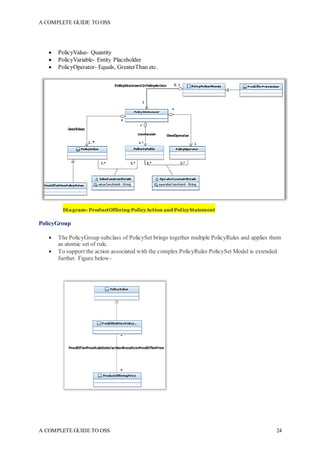
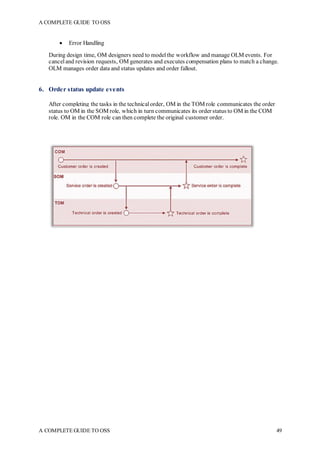
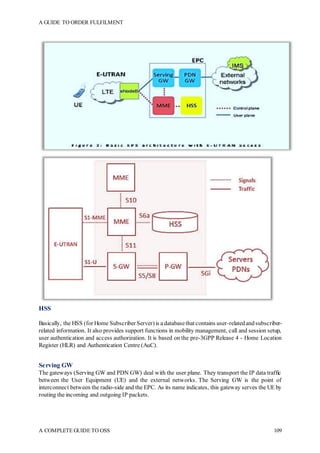
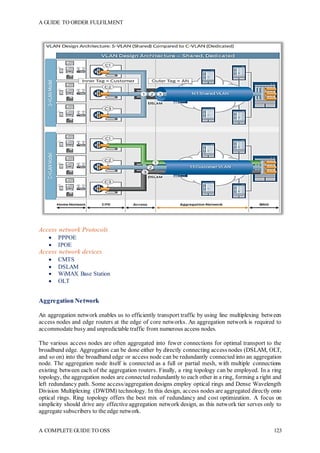
The document is a comprehensive guide to Operations Support Systems (OSS) aimed at professionals in the telecom domain, divided into two sections focusing on the create-sell-deliver journey and basic networking concepts. Section I covers product design, sales order creation, and order fulfillment processes, while Section II introduces network architecture and automation. The guide emphasizes the importance of understanding product offerings and service modeling in the telecom enterprise environment.









![A COMPLETE GUIDE TO OSS
A COMPLETE GUIDE TO OSS 10
A Resource Facing Service is an abstraction that defines the characteristics and behavior of a service
that is used internally as part of the composition of a Customer Facing Service. Resource Facing
Services are services internal to the service provider and may be composed of other Resource Facing
Services and Resources.
A Resource Facing Service is indirectly part of a Product, but is invisible to the Customer – it exists to
support one or more Customer Facing Services.
The TeleManagement Forum Information Framework (SID) defines Resource Facing Service as an
abstract base class for ResourceFacingServices. AResourceFacingService is an abstraction that defines
the characteristics and behavior of a particular Service that is not directly seen or purchased by the
Customer. ResourceFacingServices are “internal” Services that are required to support
a CustomerFacingService. The Customer obtains CustomerFacingServices via Products, and is not
aware of the ResourceFacingServices which support the CustomerFacingService(s) that is being
obtained directly by the Customer via a Product. CustomerFacingServices are directly related to
Products as well as to ResourceFacingServices. ResourceFacingServices are indirectly related to
Products through the relationship between Product and Resource. This enforces the relationship to
Products while keeping Services that are not directly obtainable via Products (i.e.,
ResourceFacingServices) separated from Products.
Users of the Information Framework’s (SID) Customer and ResourceFacingService (CFS/RFS)
typically consider that one or more ResourceFacingService(s) associated with a
CustomerFacingService specify how the later will be configured within an enterprise’s resource
infrastructure. They also tend to assume that the association between
ResourceFacingServiceSpecifications and one or more ResourceSpecification(s) themselves define the
types of Resources that will be used, in some way, to support a CustomerFacingService.
An Example
Here is an example from the definition of a ResourceFacingService: “A[virtual private network] VPN
is an example of a customer-facing service. This particular type of VPN may require border gateway
protocol (BGP) to support it. Customers don’t purchase the BGP, and hopefully aren’t even aware that
BGP is running. Therefore, BGP is an example of a resource-facing service.”
Now the enigma begins to surface: BGP is a Logical Resource, Protocol Service, v Routing Protocols
business entity. At this juncture, users of the Information Framework wonder why BGP in needed in
boththe Serviceand Resourcedomains. Onesolution is torefer tothe ResourceFacingServiceas aBGP
service, but is this enough?
The enigma grows when Information Framework users try to use the simple association from a
ResourceFacingServiceSpecification to one or more ResourceSpecification(s) to define all aspects of
how a ResourceFacingService, in this case the BGP, is configured. For instance, as the BGP is part of
the configuration of the VPN, what is the sequence of configuring it within the overall VPN? Which
properties of BGP can be selected and which are fixed? What other resources must be configured as
part of configuring the BGP?
There have been discussions going on to get rid of ResourceFacingServices at some time in the future.](https://image.slidesharecdn.com/acompleteguidetoosspublish-190731131643/85/A-Complete-Guide-to-OSS-10-320.jpg)