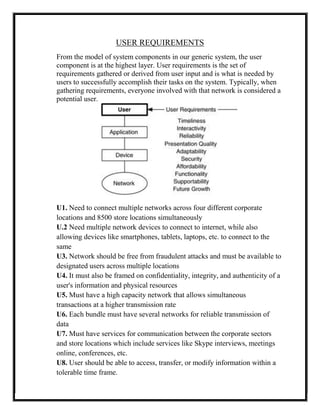
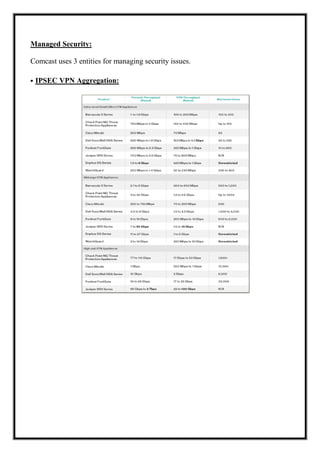
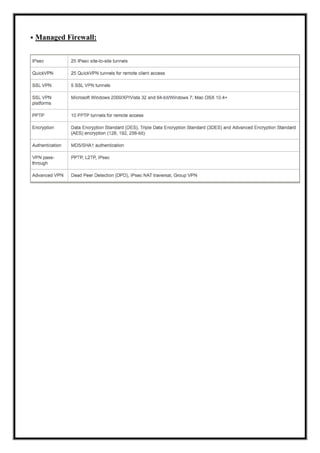
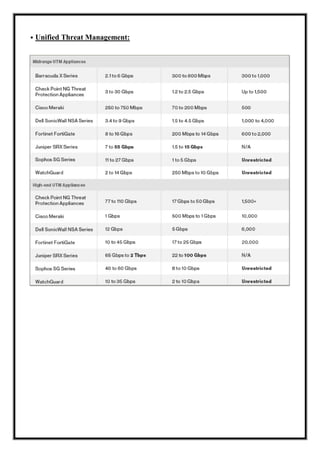
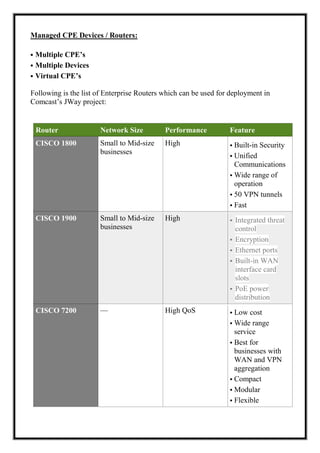
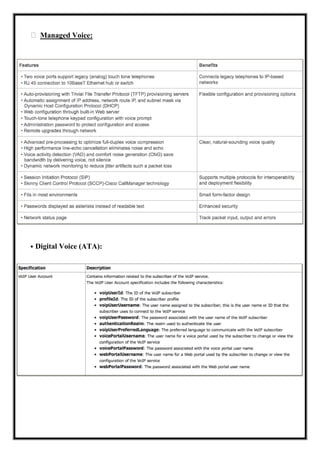
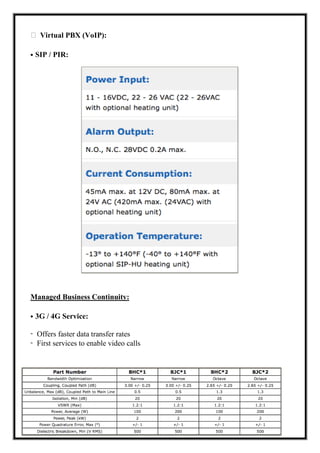
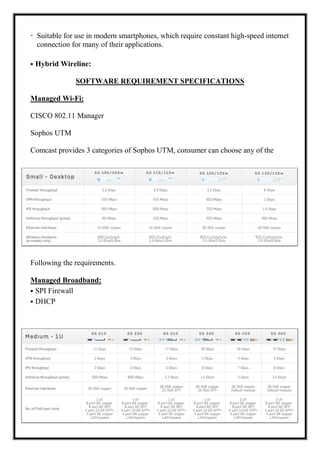
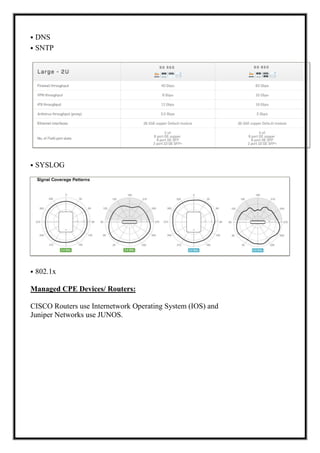
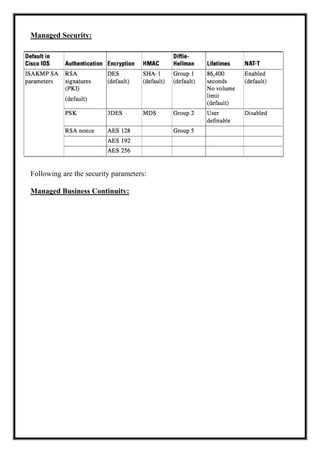
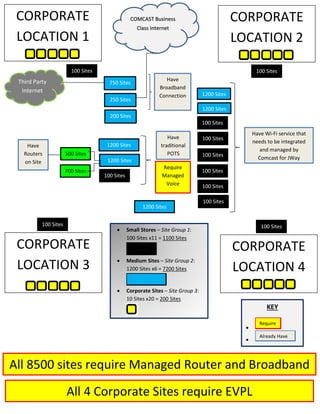
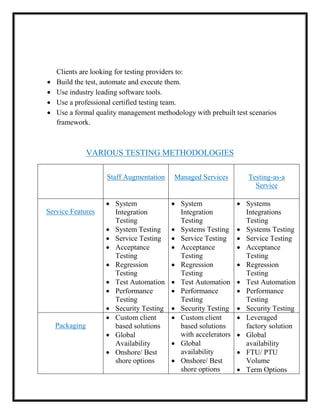
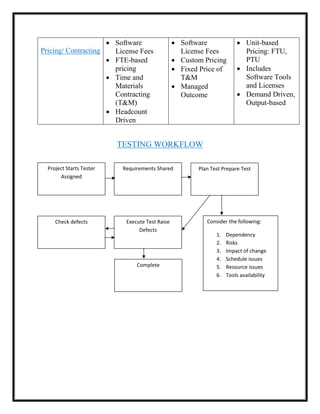
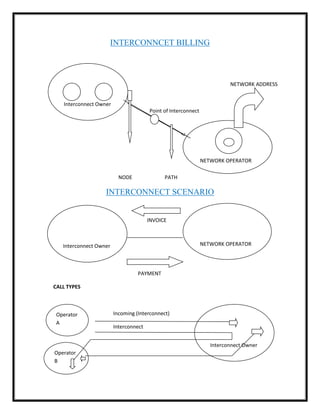
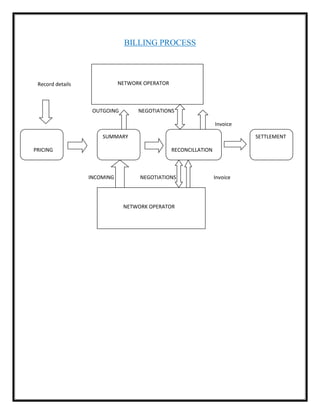
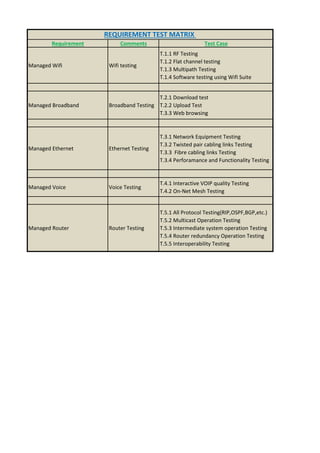
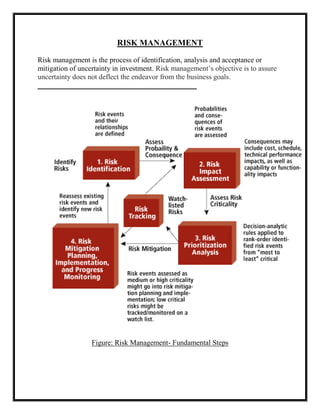
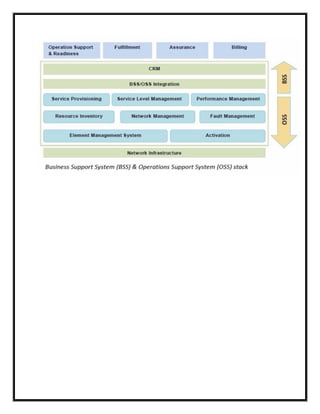
Here are the key user requirements for the Comcast Enterprise Services BSS/OSS Solution:
1. Users must be able to place orders for new services, such as broadband, Ethernet, Wi-Fi, security, routers, and voice services through an online portal or by contacting a sales representative.
2. The system must track orders from placement through fulfillment and provisioning to allow users to view order status.
3. Users must be able to manage existing services, such as viewing invoices, paying bills, upgrading/downgrading services, and submitting support tickets, through the online portal.
4. The system should provide customized views of services, invoices, reports, etc. for both corporate users and individual store owners