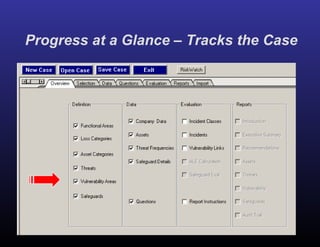
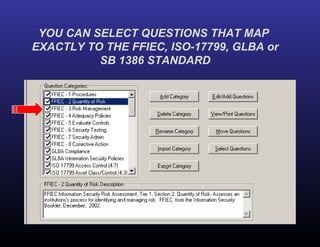
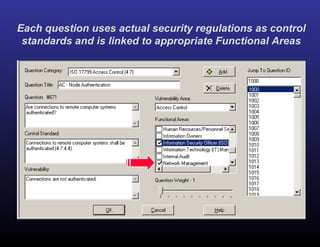
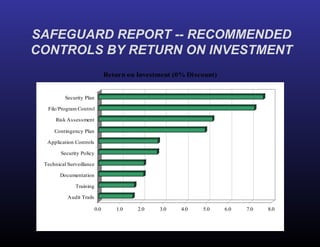
The document provides a detailed overview of risk assessments for financial institutions in compliance with FFIEC and BSA guidelines, highlighting the importance of RiskWatch software for automating the risk assessment process. It emphasizes the need for ongoing information security risk assessments, outlines various compliance regulations, and addresses responsibilities of management in maintaining an effective information security program. Additionally, it showcases the benefits of using RiskWatch, including customizable features, automated reporting, and improved ROI for risk management activities.











































![THE BOTTOM LINE Regulators are going to continue to push for more risk assessments to be performed annually. A RiskWatch risk assessment is the foundation of the IT security program, and Governance, Risk and Compliance program. RiskWatch is the best way to meet NCUA risk analysis requirements, and self-assess compliance by requirement. 4. Get Special Pricing and Free Training in Annapolis by emailing [email_address] .](https://image.slidesharecdn.com/RWFINANCIALINSTITUTIONSAPRIL2008-123394540118-phpapp03/85/RiskWatch-for-Financial-Institutions-48-320.jpg)
