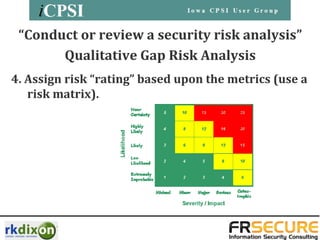
The presentation by Evan Francen covers the importance of conducting security risk analyses in healthcare to comply with HIPAA and meaningful use requirements. It emphasizes the need for organizations to identify and mitigate risks to electronic health information, while also outlining common mistakes and best practices for effective risk management. The document stresses that a thorough and documented risk analysis should be a regular part of an organization's security strategy.






![Measure 14 of 14 - Protect Electronic Health
Information
45 CFR Section 164.308(a)(1)(ii)(A) of the HIPAA Security Rule requires that
the organization "Conduct an accurate and thorough assessment of the
potential risks and vulnerabilities to the confidentiality, integrity and
availability of electronic protected health information [ePHI] held by the
covered entity.”
45 CFR Section 164.308(a)(1)(ii)(B) requires an organization to ―implement
security measures sufficient to reduce risks and vulnerabilities to a reasonable
and appropriate level to comply with CFR 45 164.306(a) which is the General
Requirements of the Security Rule.](https://image.slidesharecdn.com/icpsi-111020151849-phpapp02/85/Meaningful-Use-and-Security-Risk-Analysis-7-320.jpg)