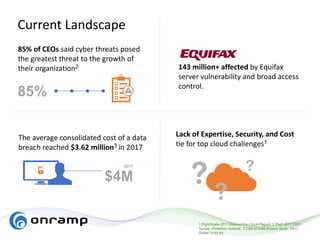
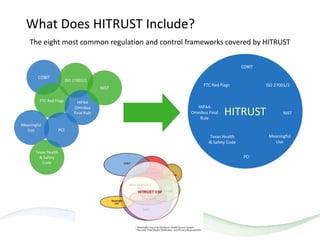
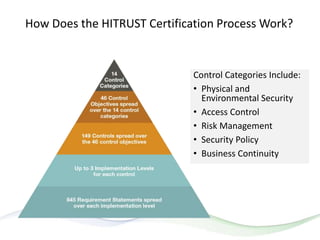
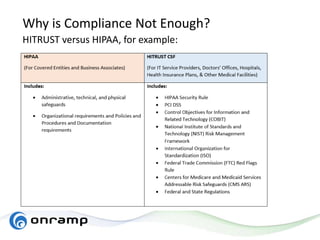
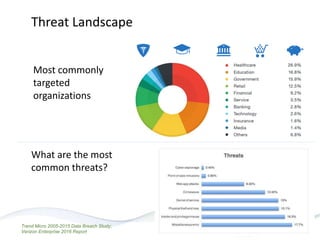
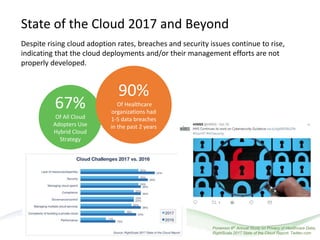
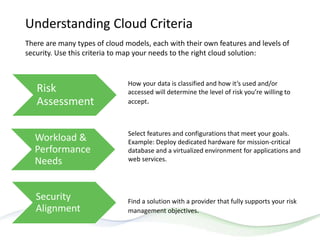
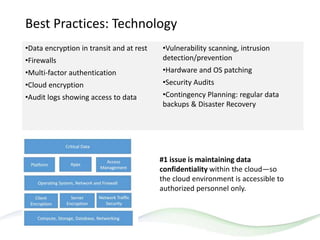
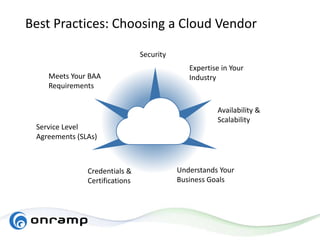
The document discusses HITRUST, a certifiable framework designed to address compliance challenges and enhance cybersecurity, particularly for organizations handling sensitive data. It outlines the benefits of HITRUST, common challenges in cloud deployments, and best practices for securing cloud infrastructure. Key topics include the importance of proper data governance, security practices, and choosing the right cloud vendor to safeguard information.