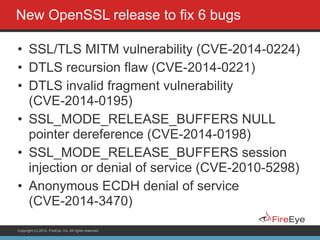
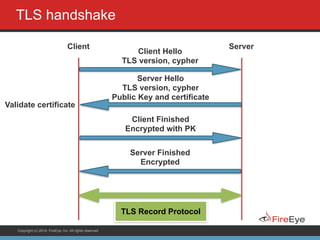
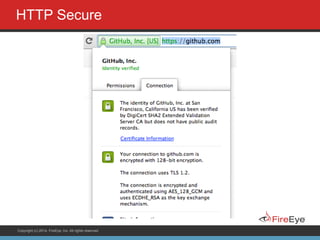
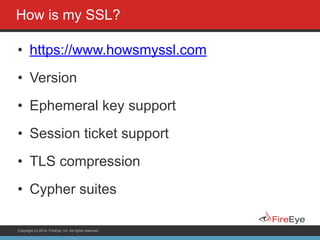
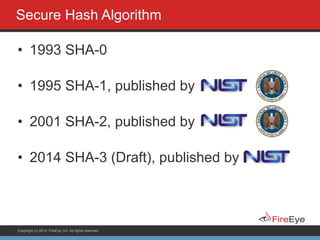
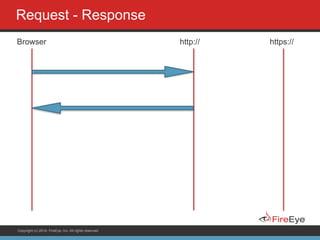
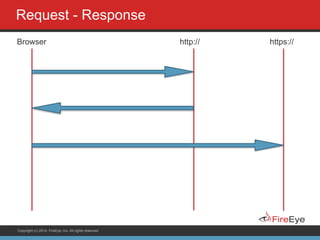
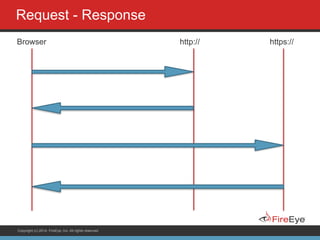
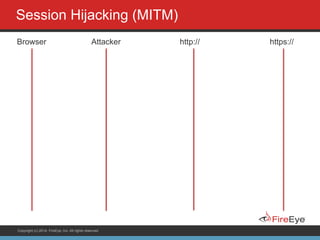
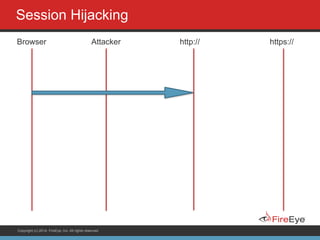
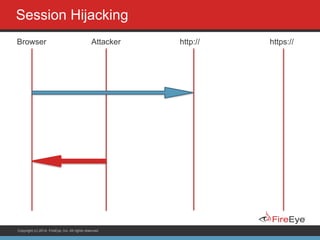
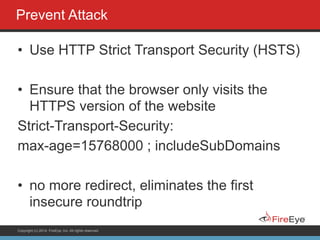
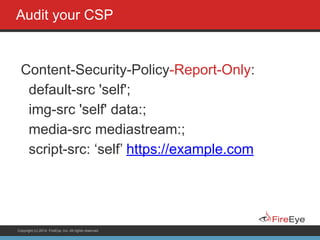
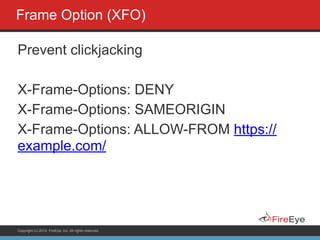
The document discusses securing Ruby on Rails applications. It covers topics like transport layer security (TLS and SSL), session hijacking, content security policy, cross-site scripting protection, and static code analysis tools. Gems like secure_headers, Brakeman, codesake-dawn and gauntlt can help audit code and build attacks to test vulnerabilities. Maintaining TLS is important to protect against man-in-the-middle attacks and securely transmit sensitive data like passwords.














![Copyright (c) 2014, FireEye, Inc. All rights reserved.
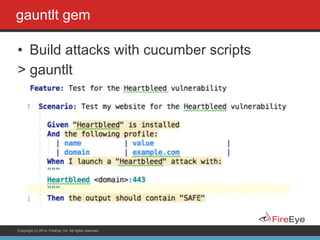
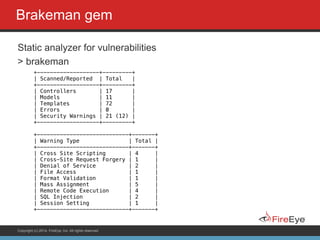
codesake-dawn gem
static code scanner
> dawn --rails .
13:37:54 [*] dawn v1.1.3 is starting up
13:37:54 [$] dawn: scanning .
13:37:54 [$] dawn: rails v4.1.1 detected
13:37:54 [$] dawn: applying all security checks
13:37:54 [$] dawn: 173 security checks applied - 0 security checks skipped
13:37:54 [$] dawn: 2 vulnerabilities found
13:37:54 [!] dawn: Owasp Ror CheatSheet: Session management check failed
13:37:54 [$] dawn: Severity: info
13:37:54 [$] dawn: Priority: unknown
13:37:54 [$] dawn: Description: By default, Ruby on Rails uses a Cookie based session
store. What that means is that unless you change something, the session will not expire
on the server. That means that some default applications may be vulnerable to replay
attacks. It also means that sensitive information should never be put in the session.
13:37:54 [$] dawn: Solution: Use ActiveRecord or the ORM you love most to handle your
code session_store. Add "Application.config.session_store :active_record_store" to your
session_store.rb file.
13:37:54 [$] dawn: Evidence:
13:37:54 [$] dawn: In your session_store.rb file you are not using ActiveRercord to
store session data. This will let rails to use a cookie based session and it can expose
your web application to a session replay attack.
13:37:54 [$] dawn: {:filename=>"./config/initializers/session_store.rb", :matches=>[]}](https://image.slidesharecdn.com/rubynation2014fe-140607084513-phpapp01/85/Securing-your-Rails-application-36-320.jpg)