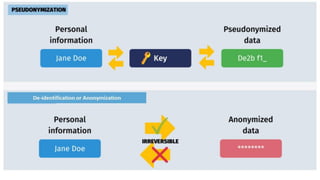
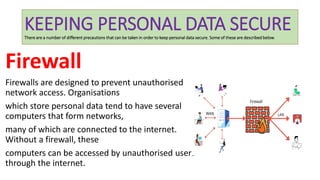
This document discusses various methods for keeping personal data secure and preventing unauthorized access. It describes de-identification and pseudonymization as strategies to prevent identity revelation from personal data. It also discusses encryption, firewalls, penetration testing, authentication techniques like passwords and biometrics, restricting access levels, software updates, and policies to control network use. Specific risks like pharming and phishing that try to steal login credentials are explained, along with recommendations to avoid them like using antivirus software and verifying website URLs.