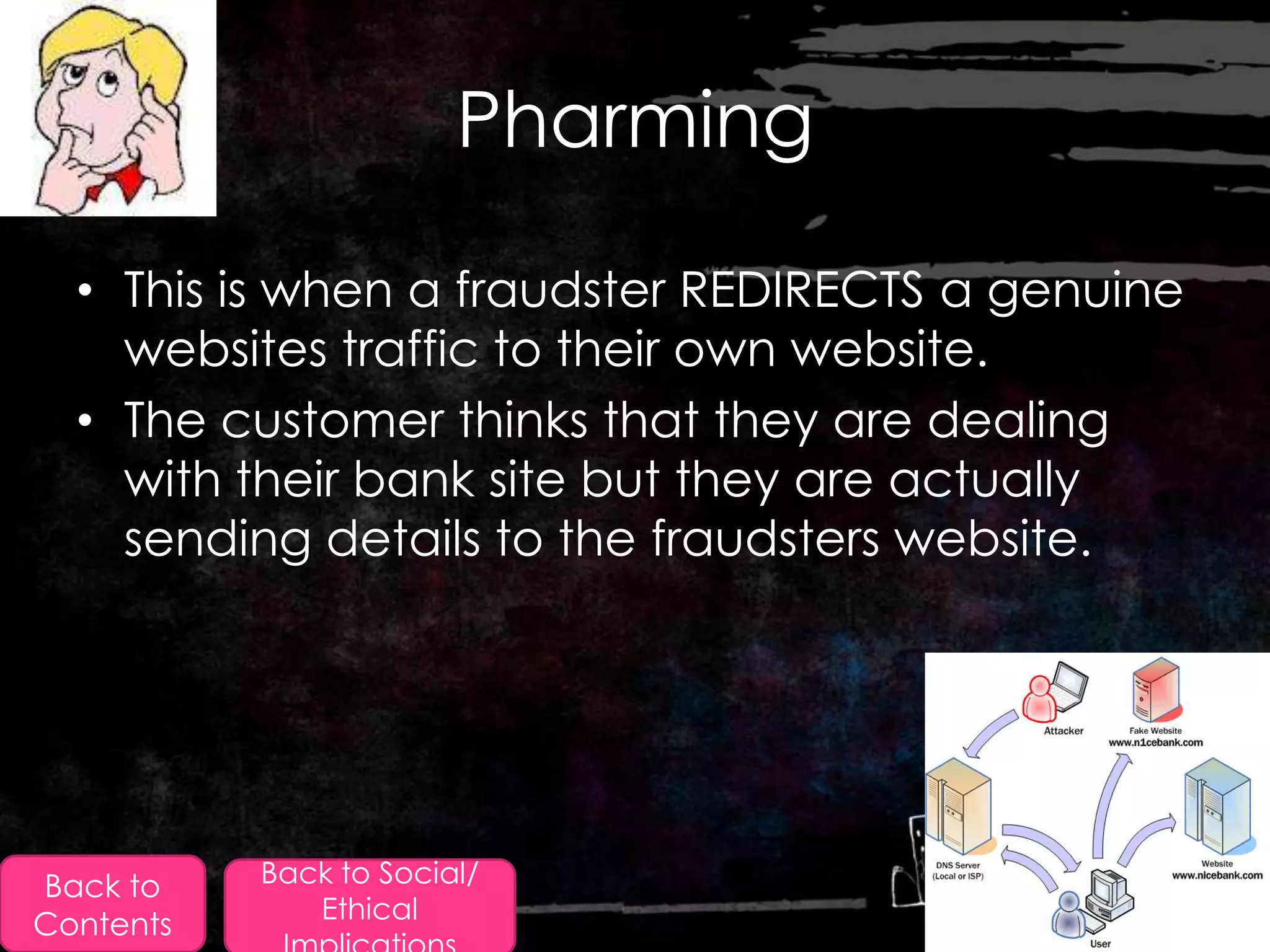
This document discusses various topics related to data protection and privacy when conducting transactions online or with technology. It covers encryption techniques used to protect confidential data, such as public and private key systems. It also discusses legislation around data protection, social and ethical implications of accessing personal information, and security measures used by online banks and stores.