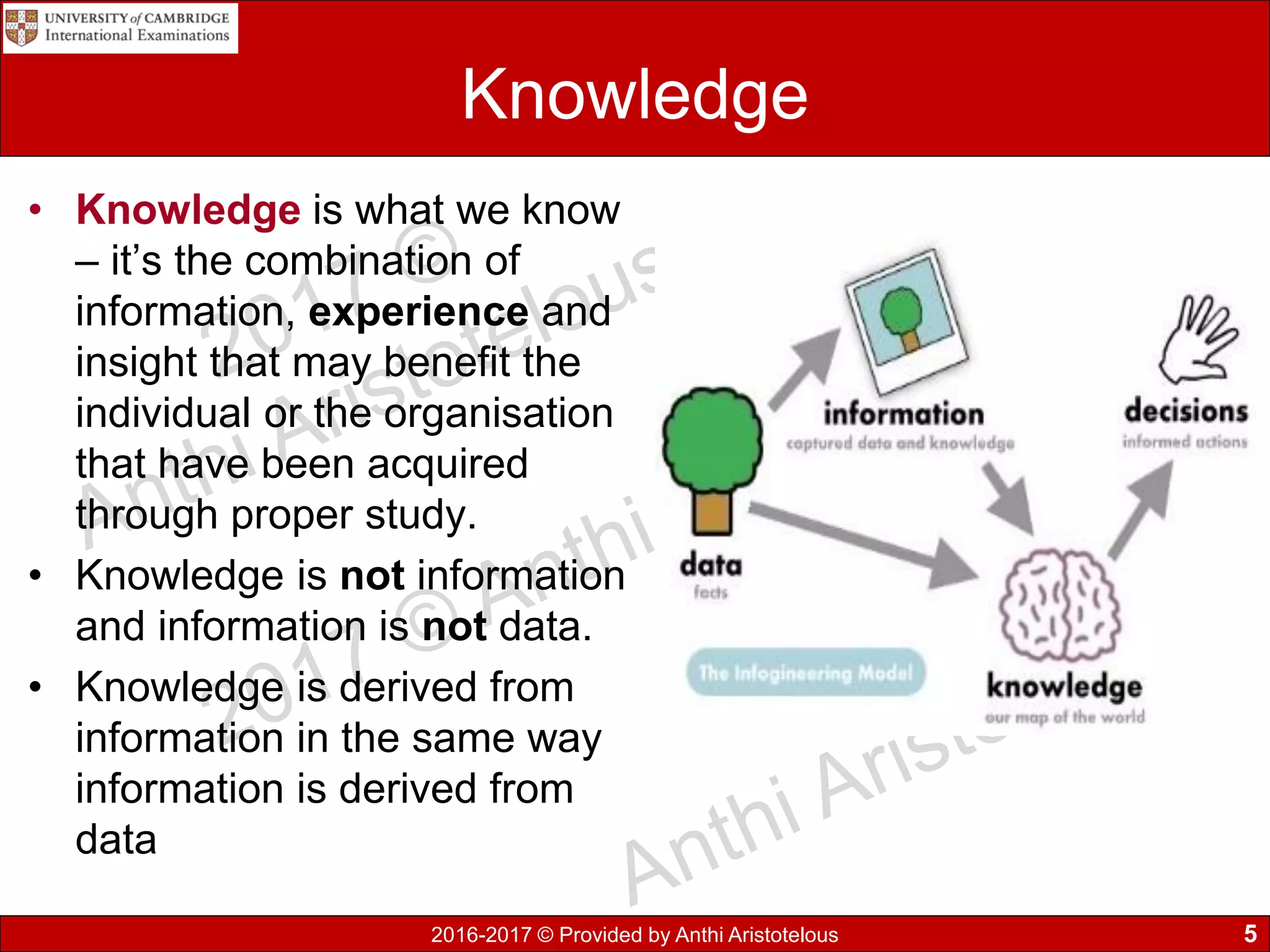
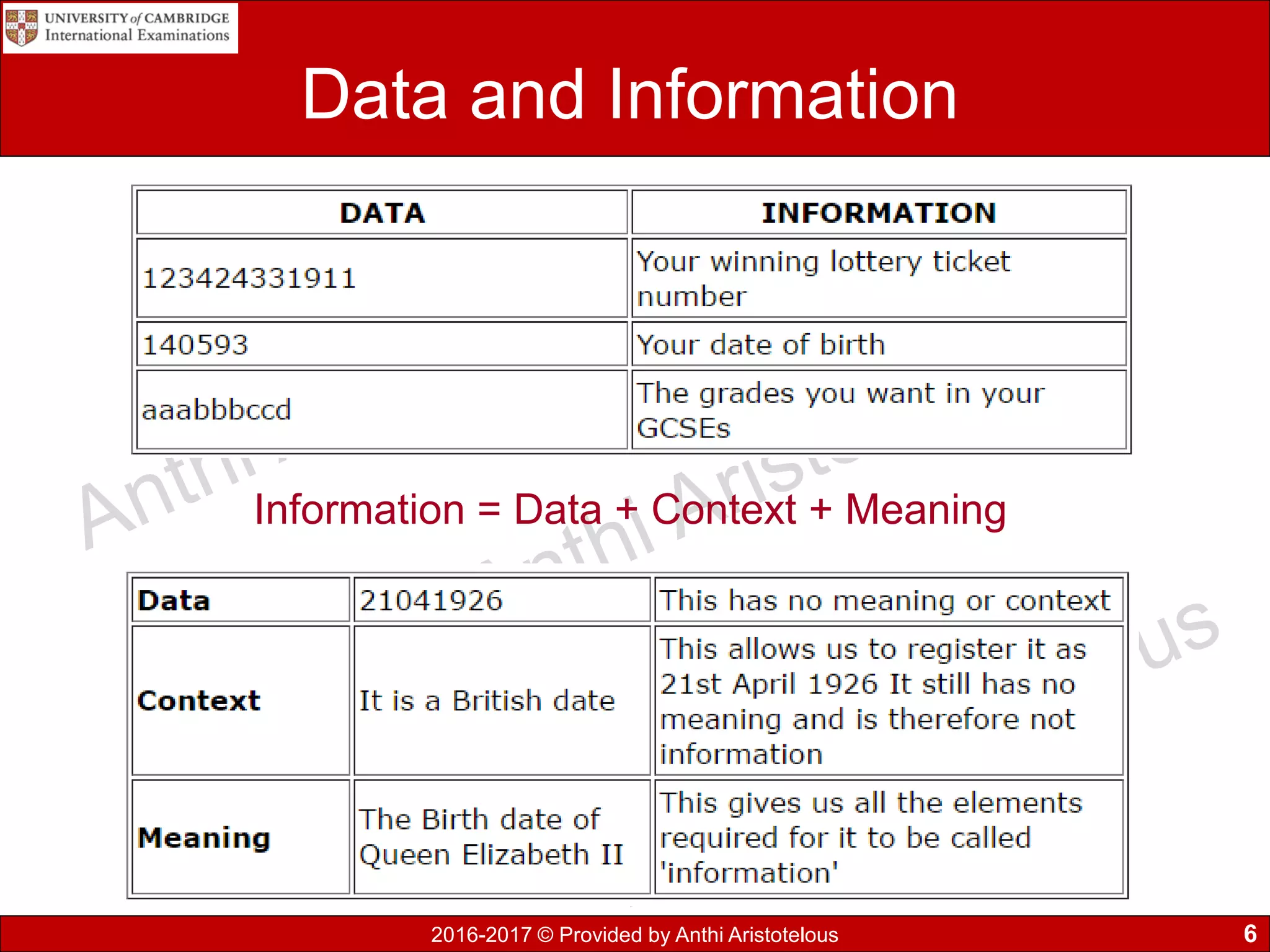
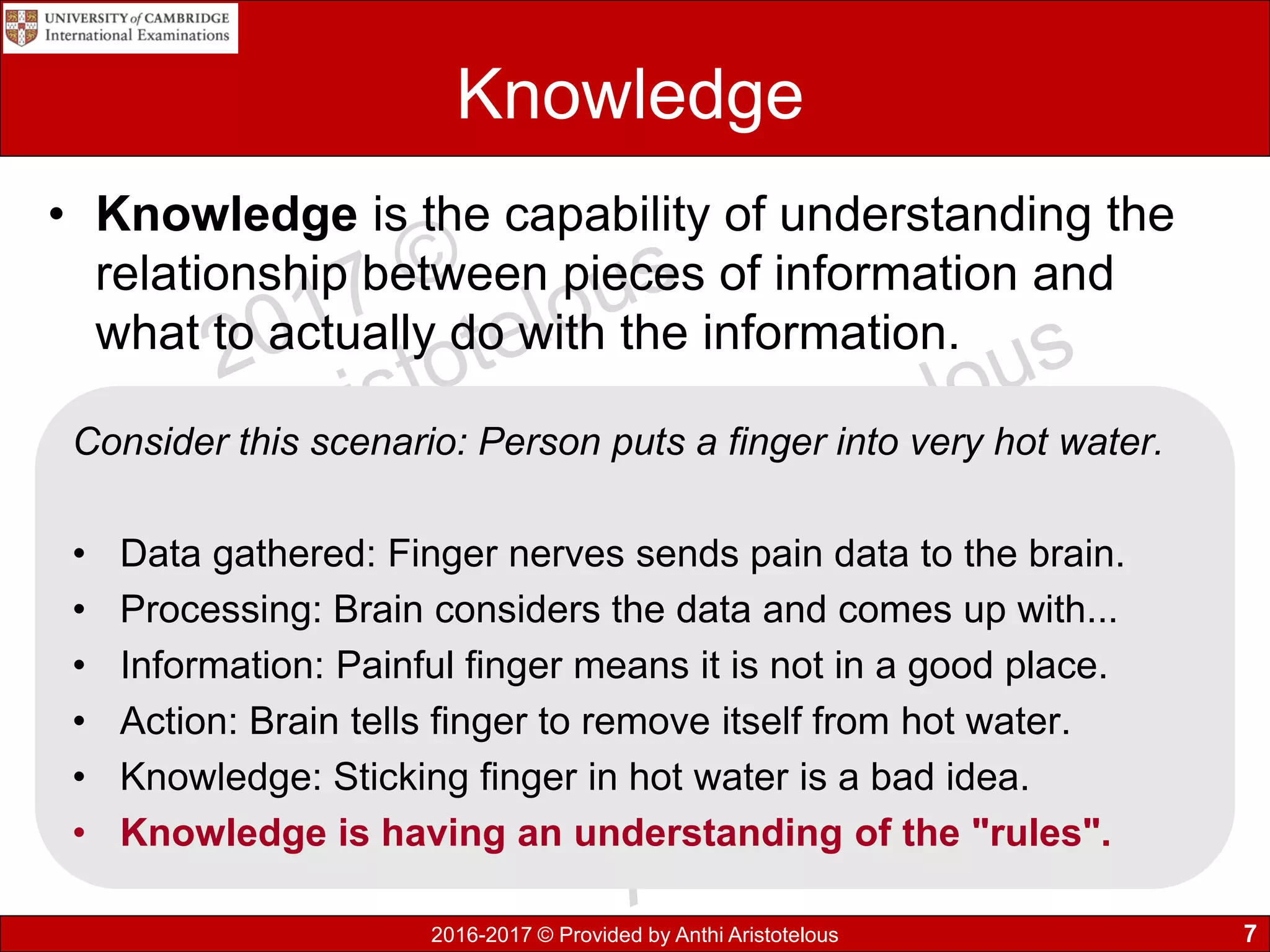
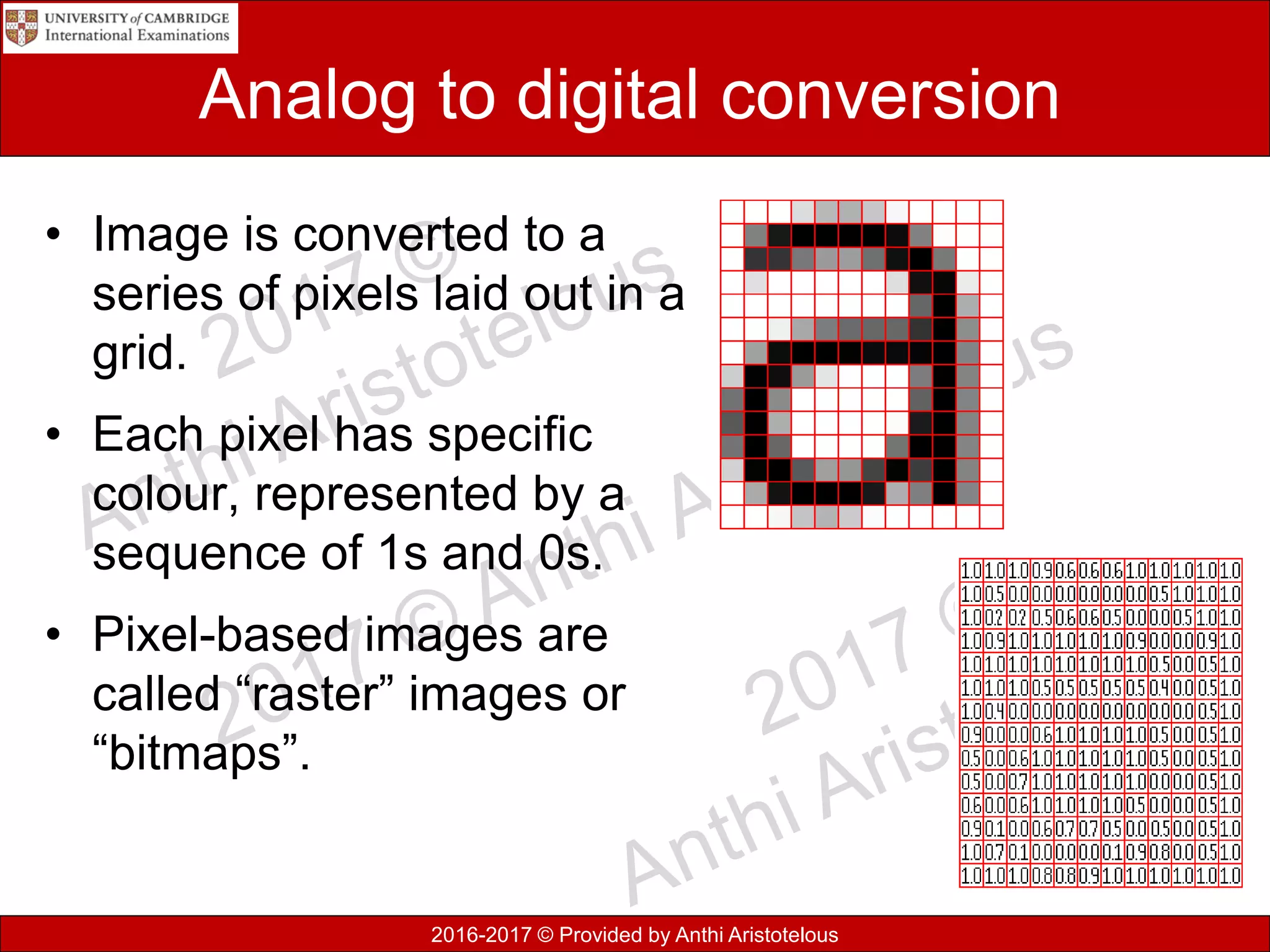
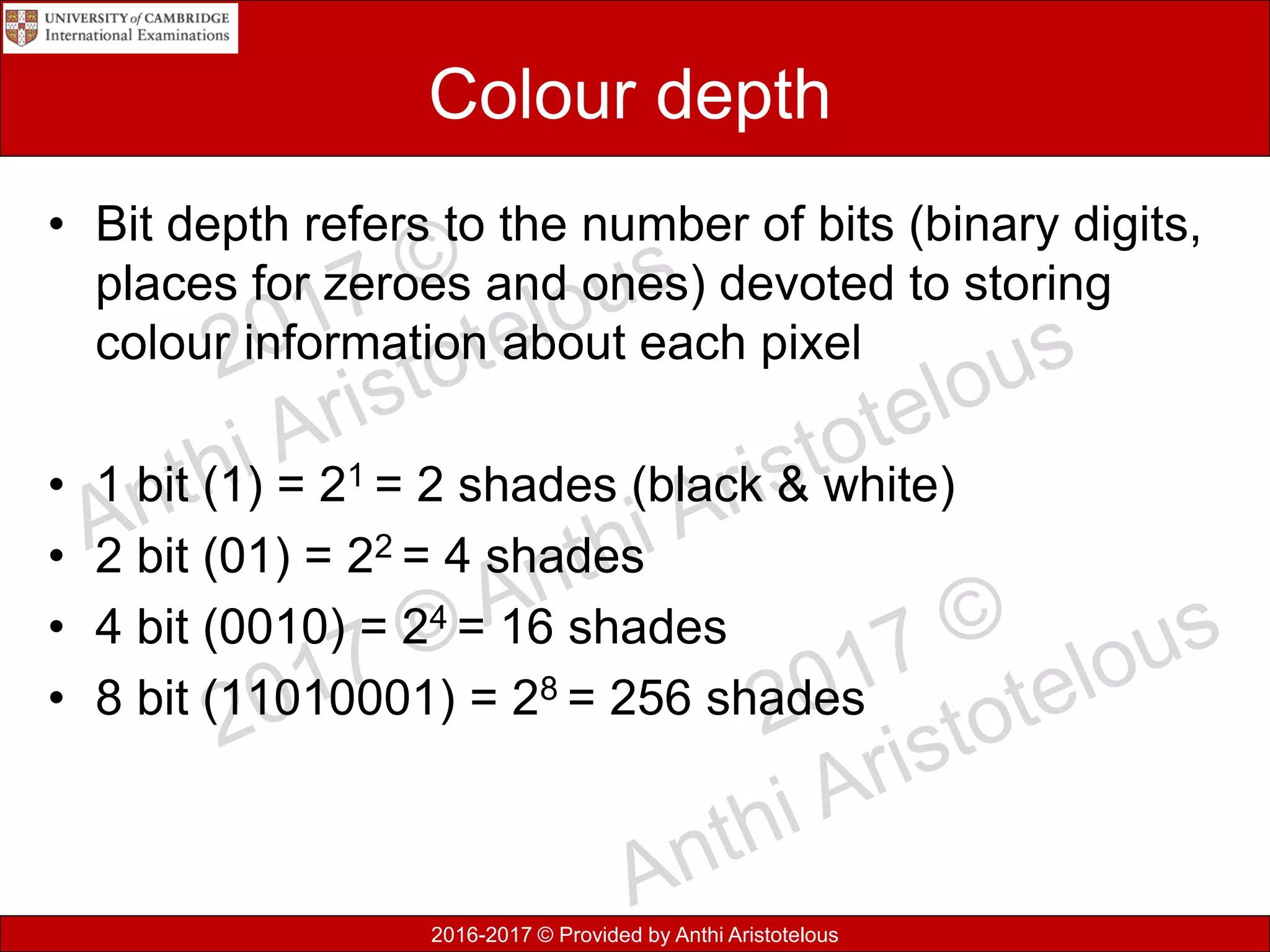
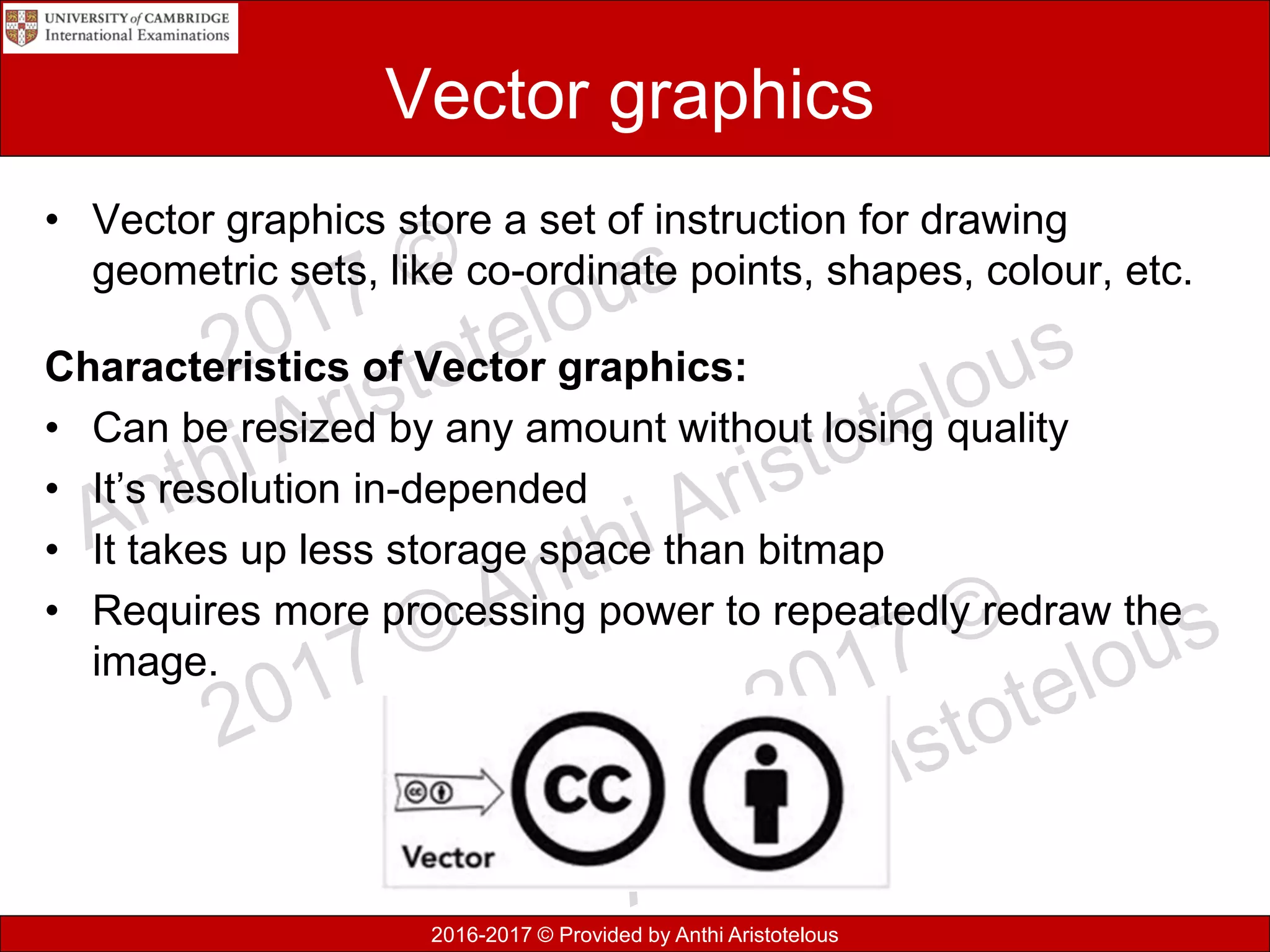
This document discusses data, information, and knowledge processing. It begins by defining key terms like data, information, knowledge, and how they relate. Data refers to raw unprocessed facts, while information adds context and meaning to data. Knowledge combines information with experience and insight.
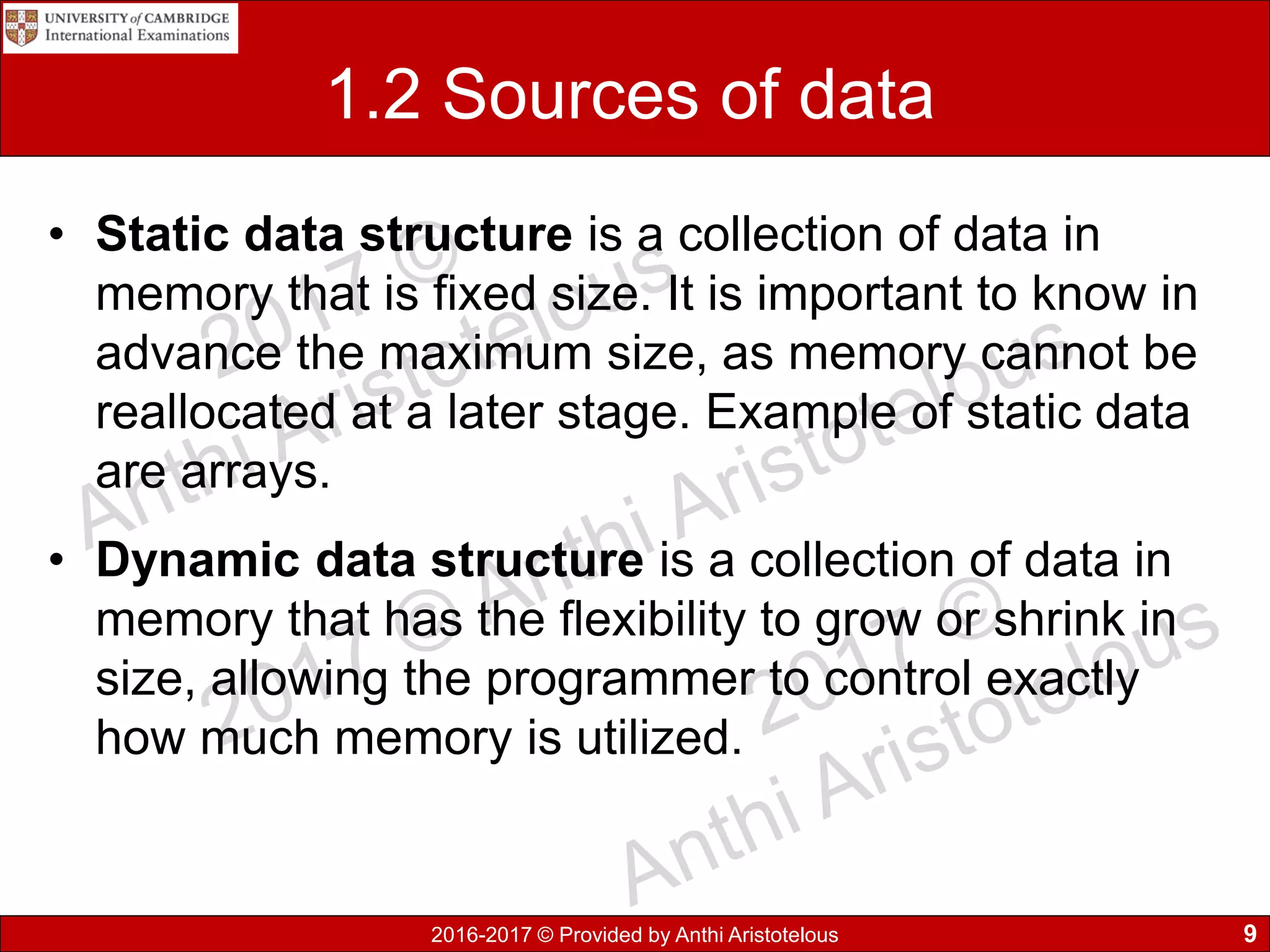
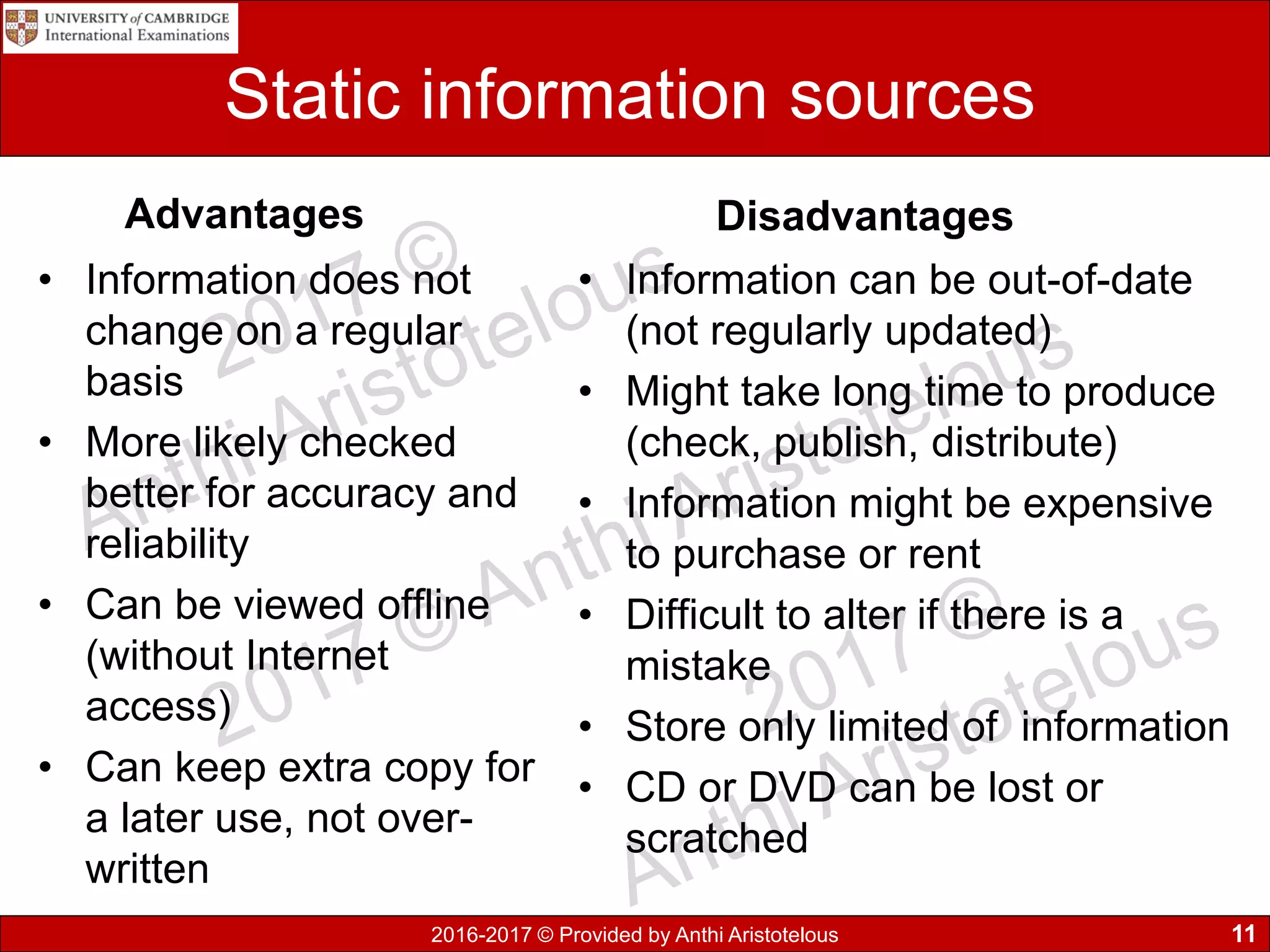
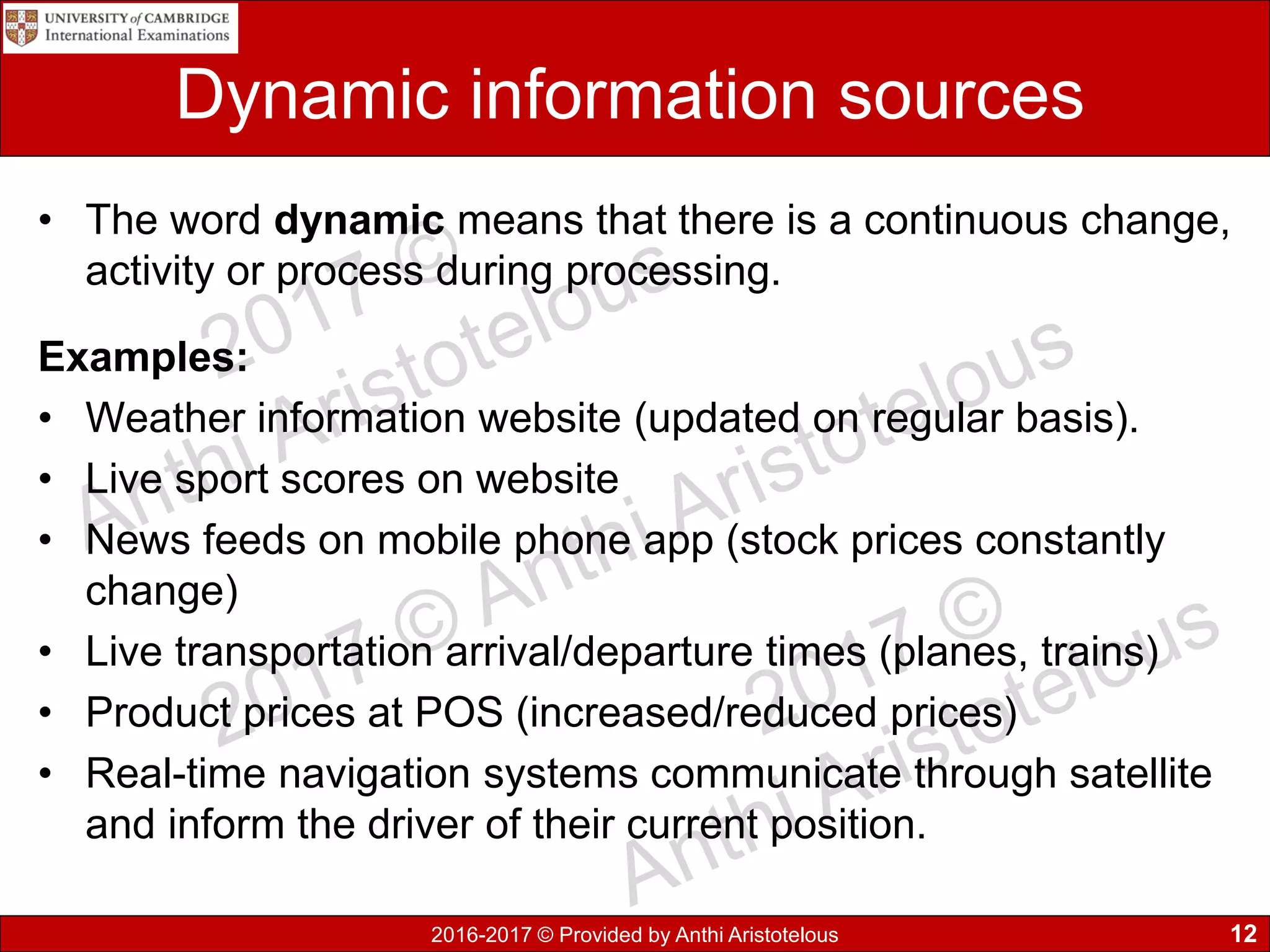
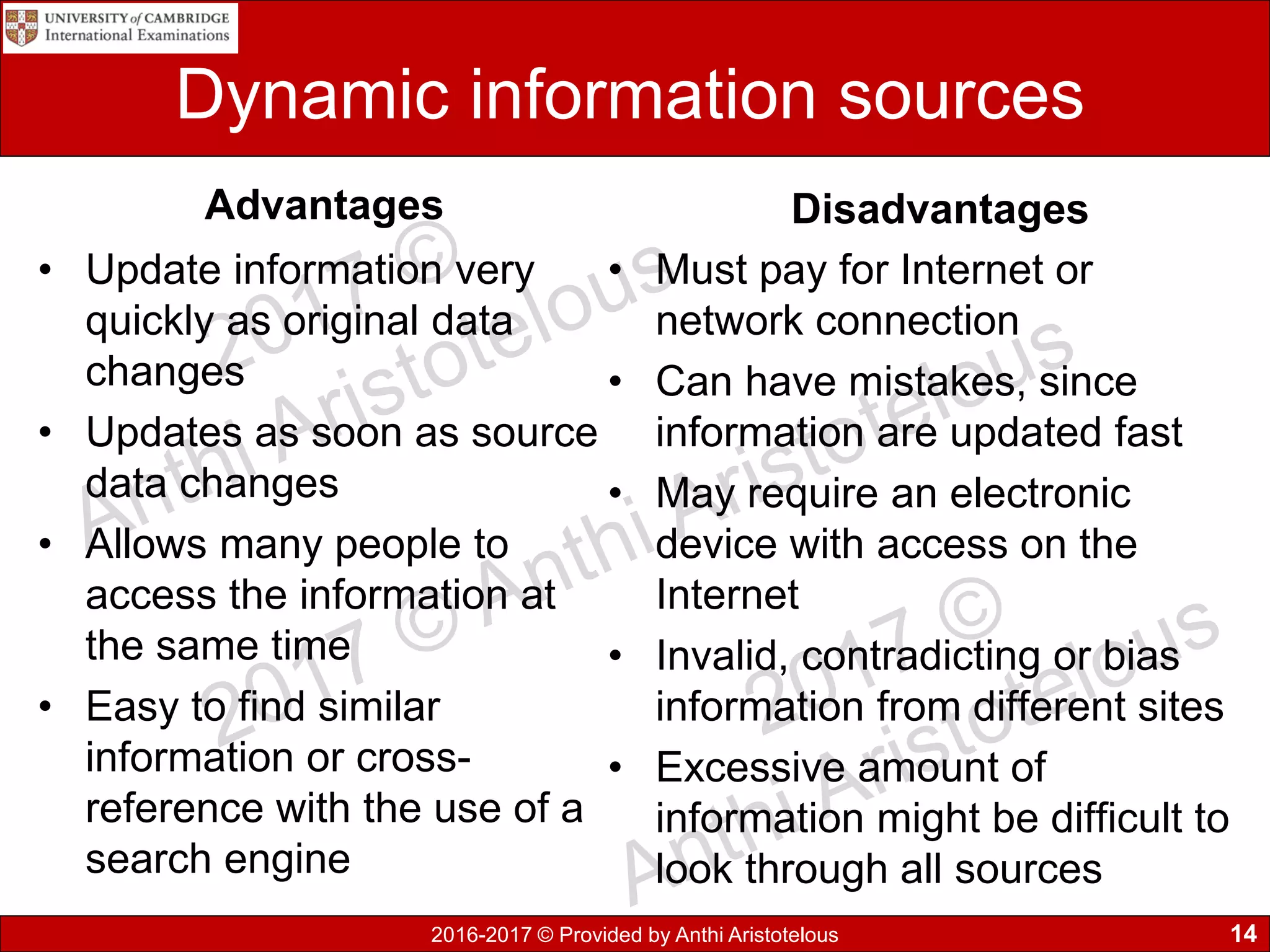
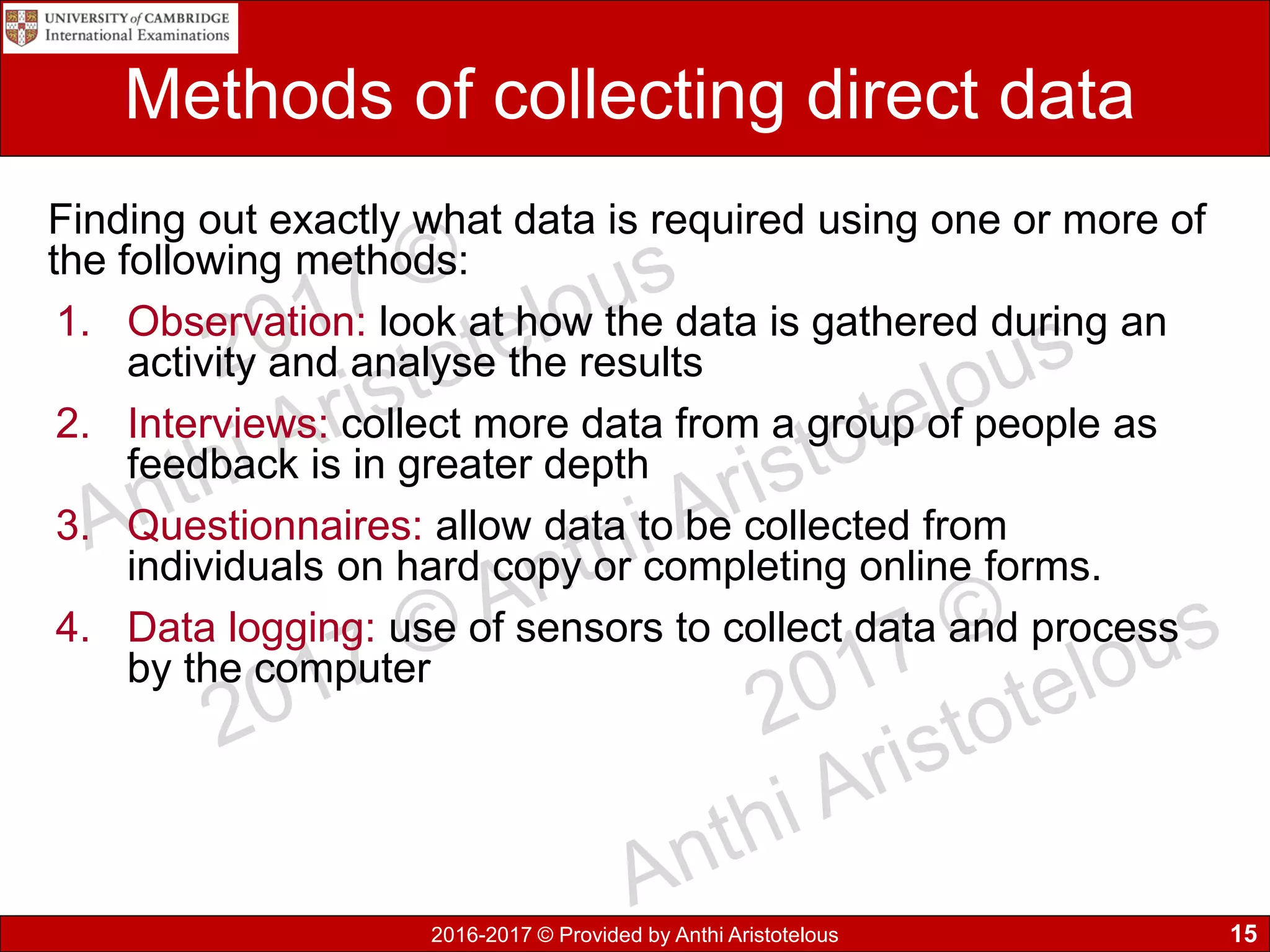
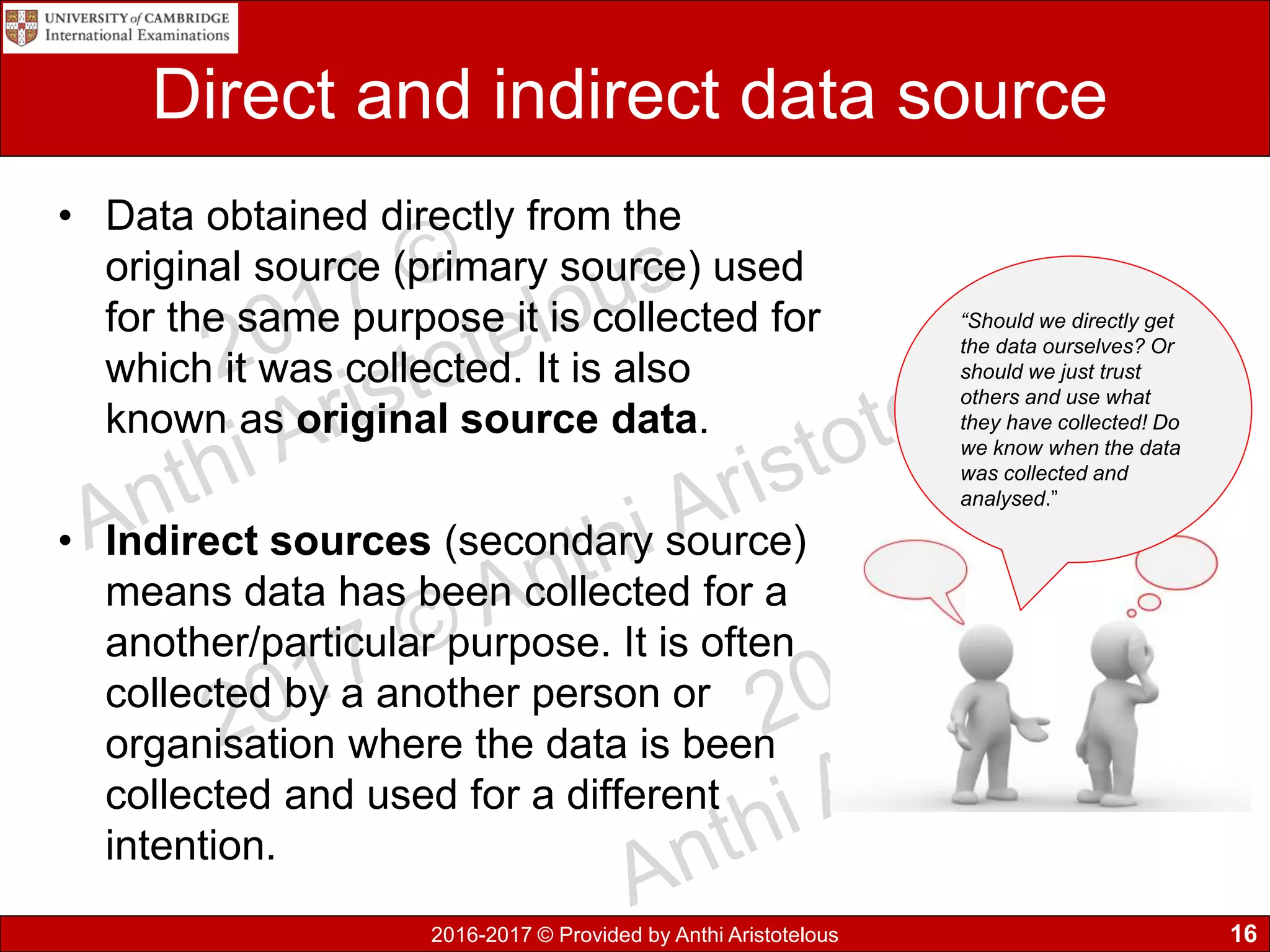
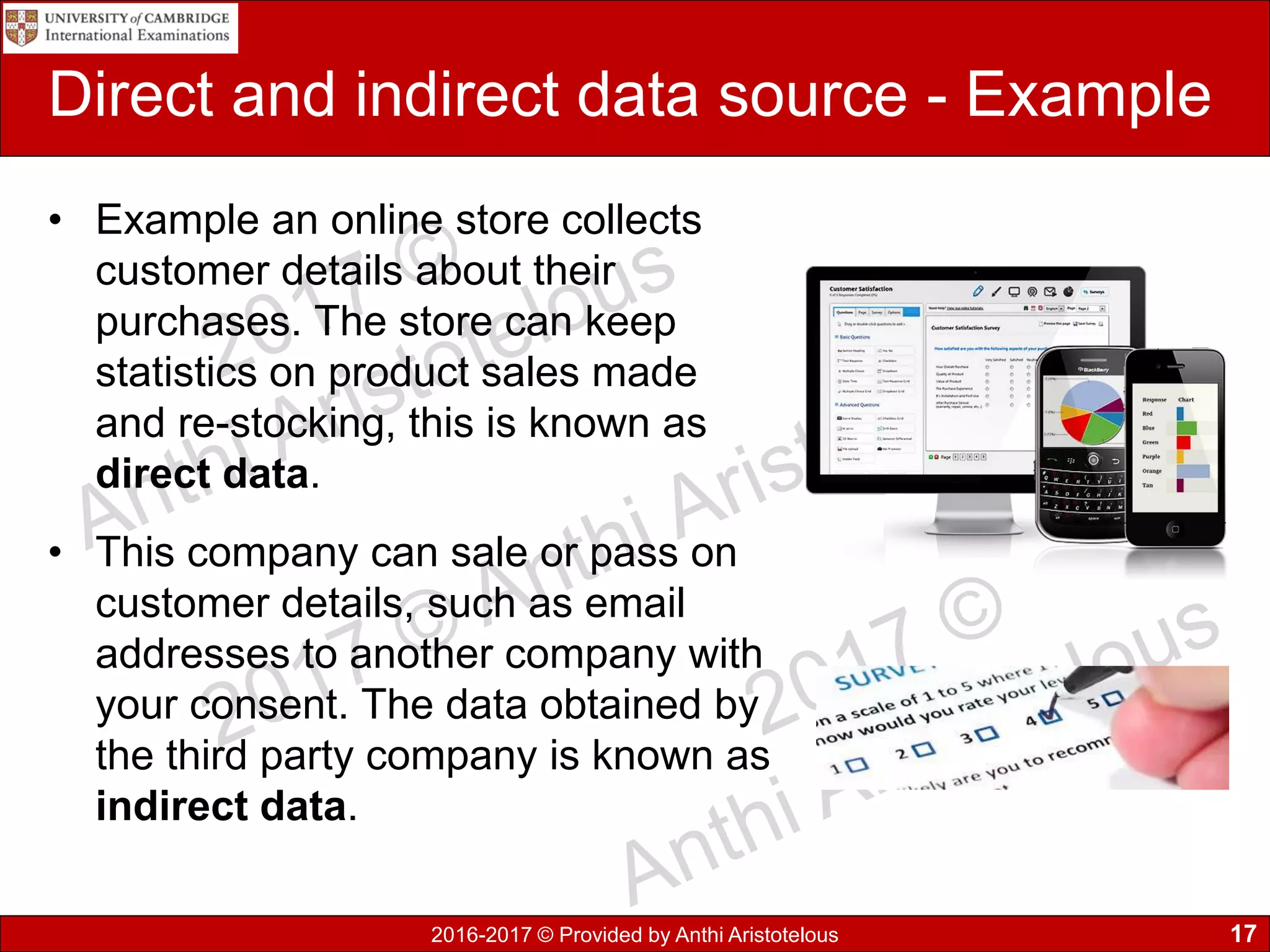
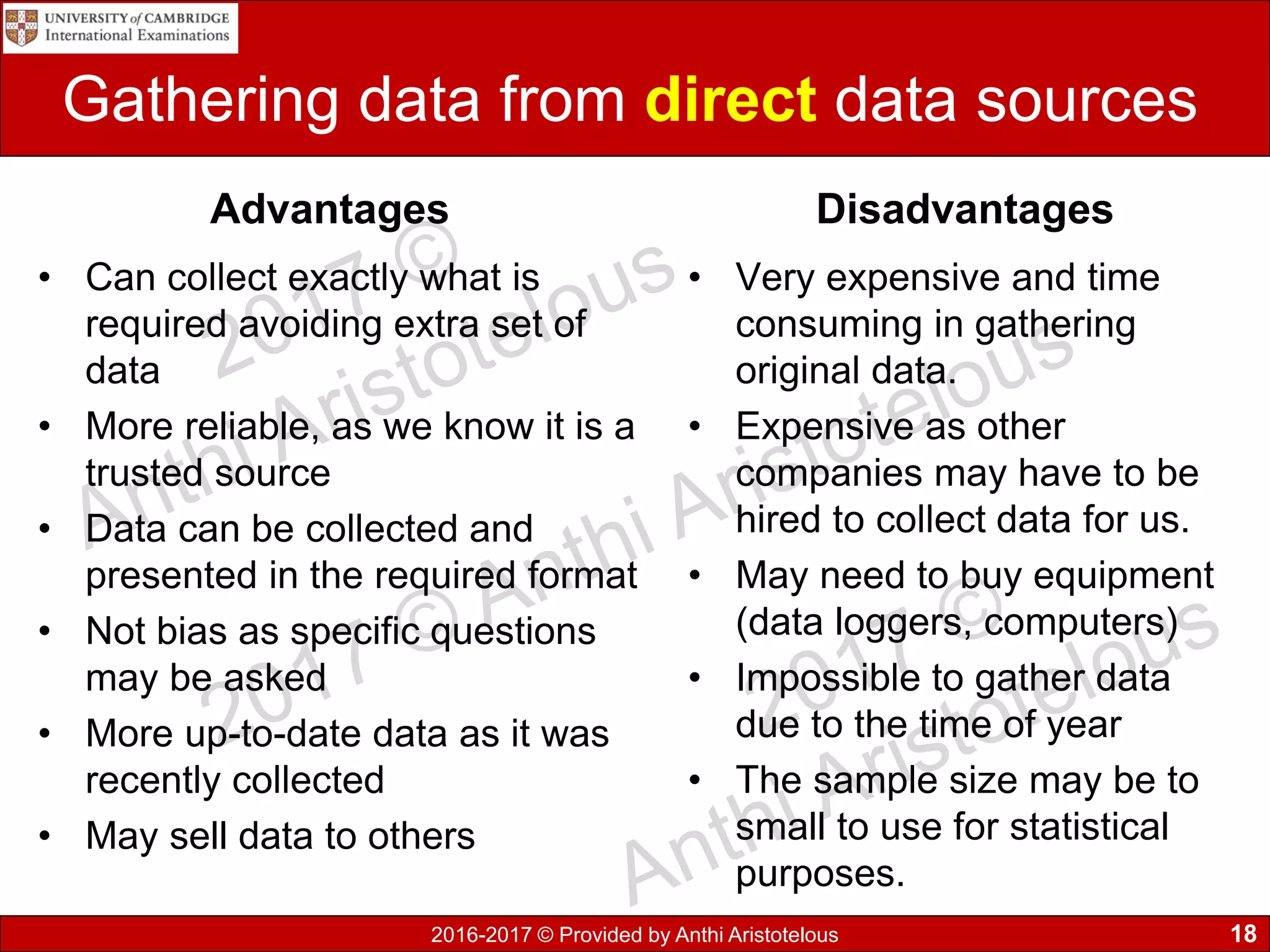
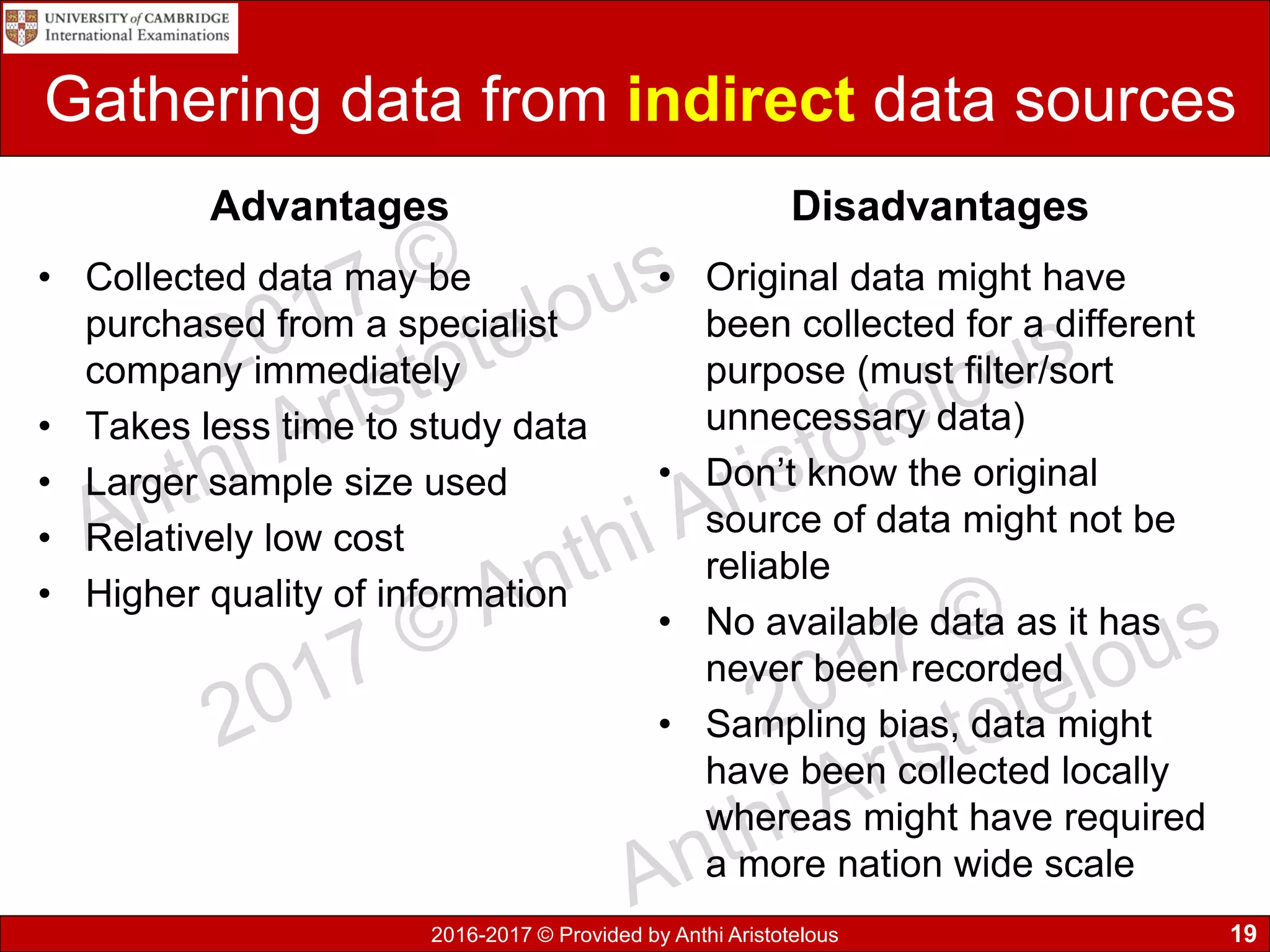
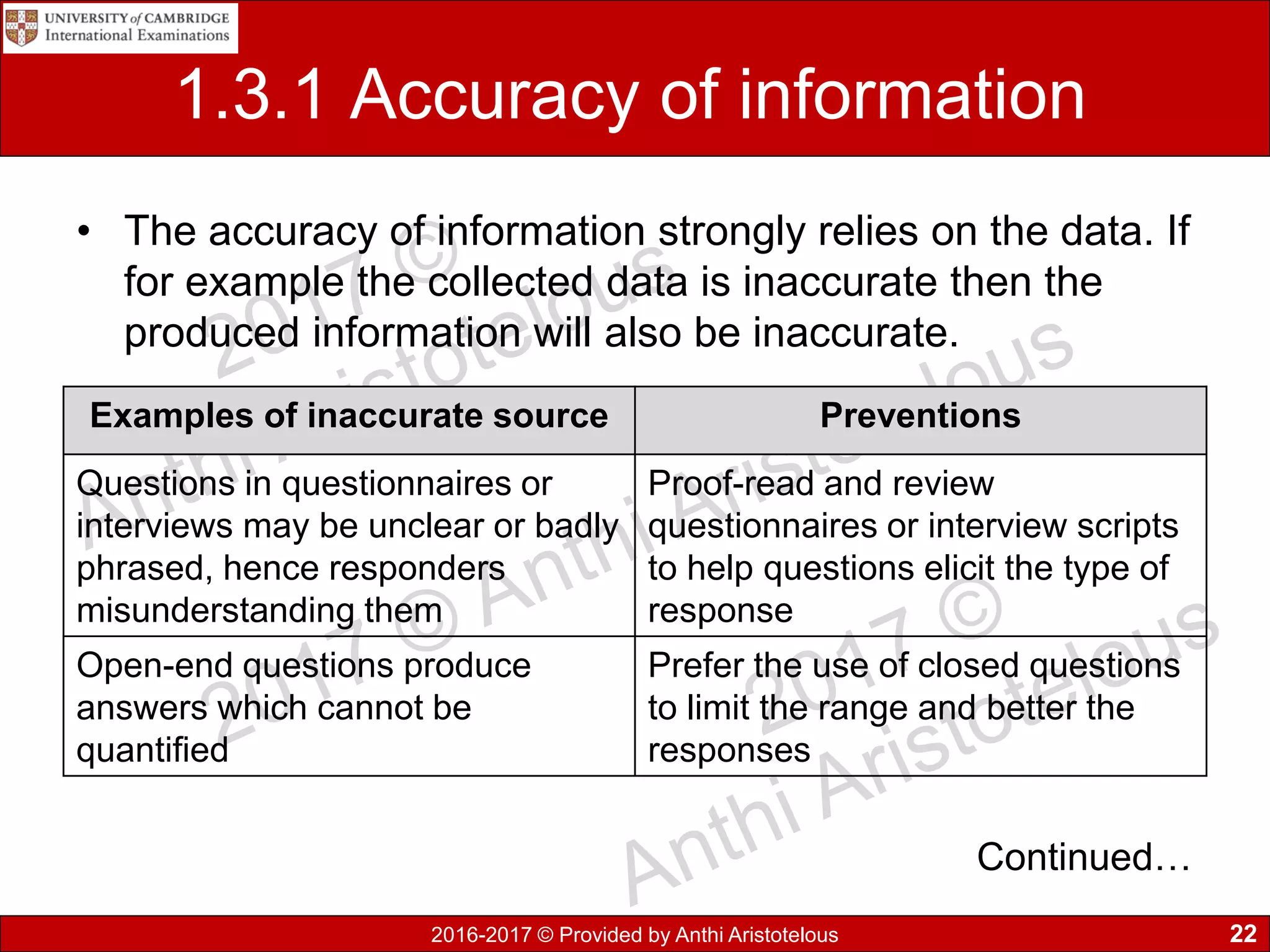
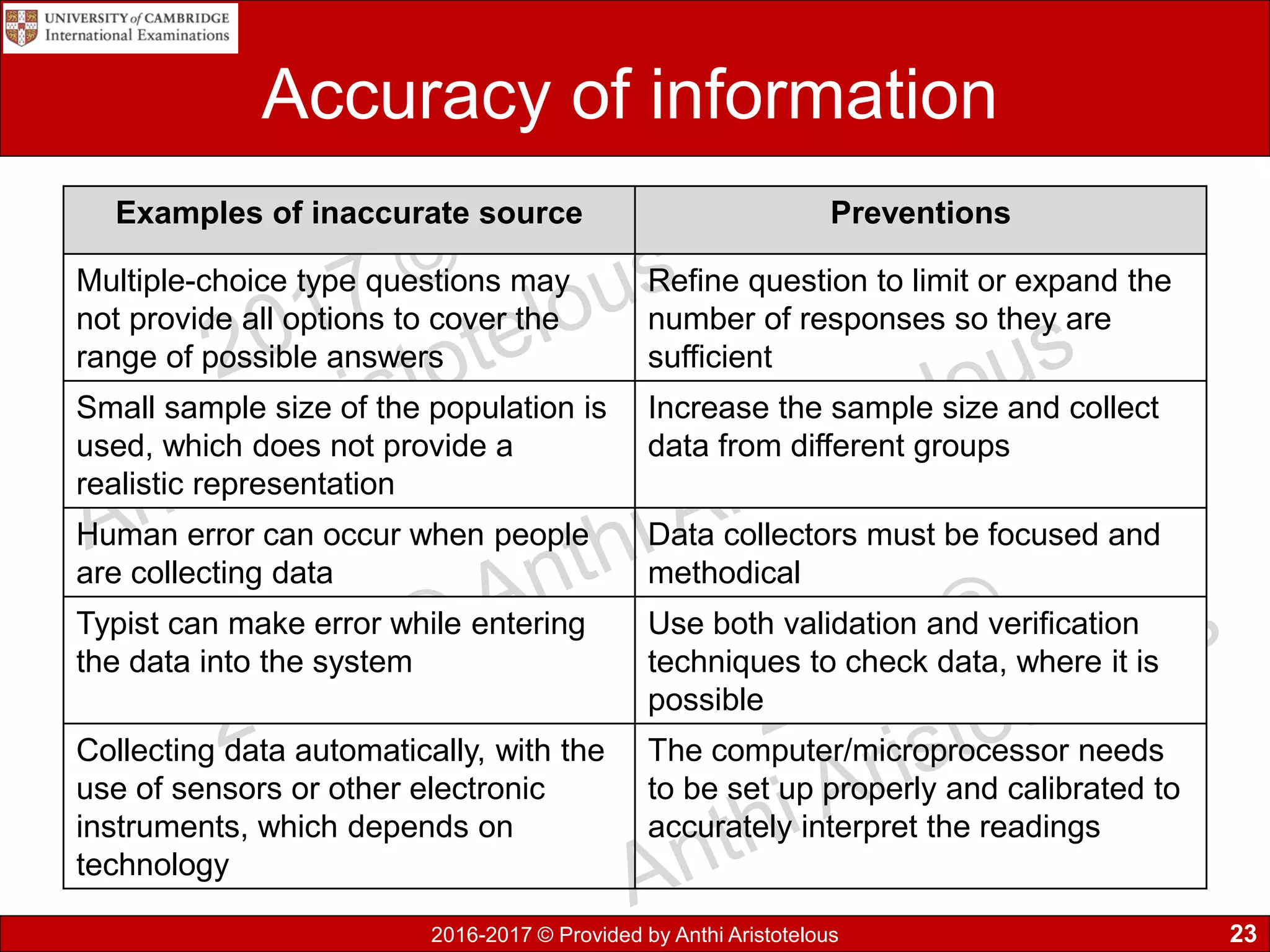
It then covers sources of data, distinguishing between static and dynamic sources. Static sources like printed materials change little over time, while dynamic online sources continuously update. Direct sources are from original data collection, while indirect sources use data collected by others. Quality of information is also discussed in terms accuracy, relevance, age, detail level, and completeness.
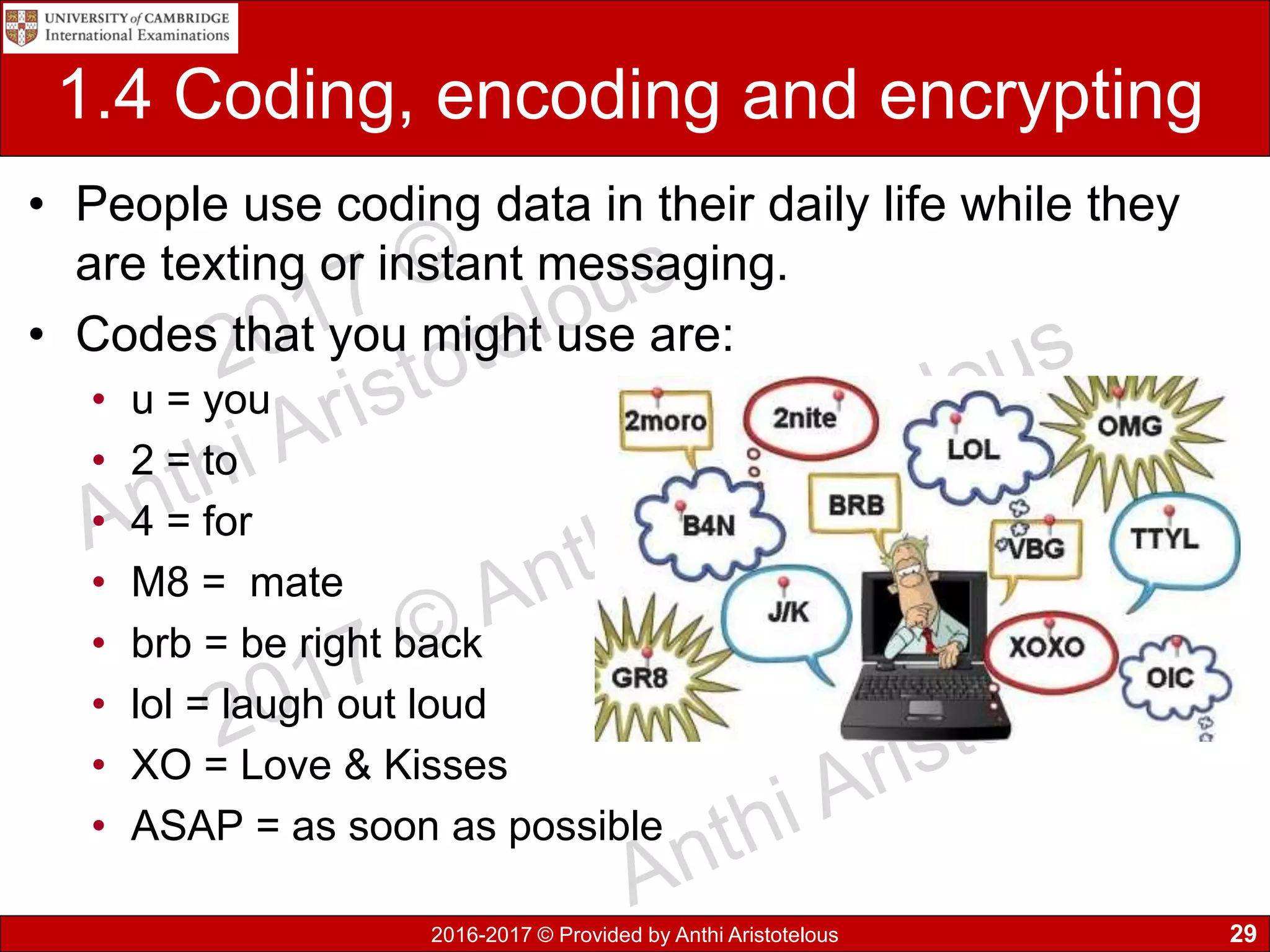
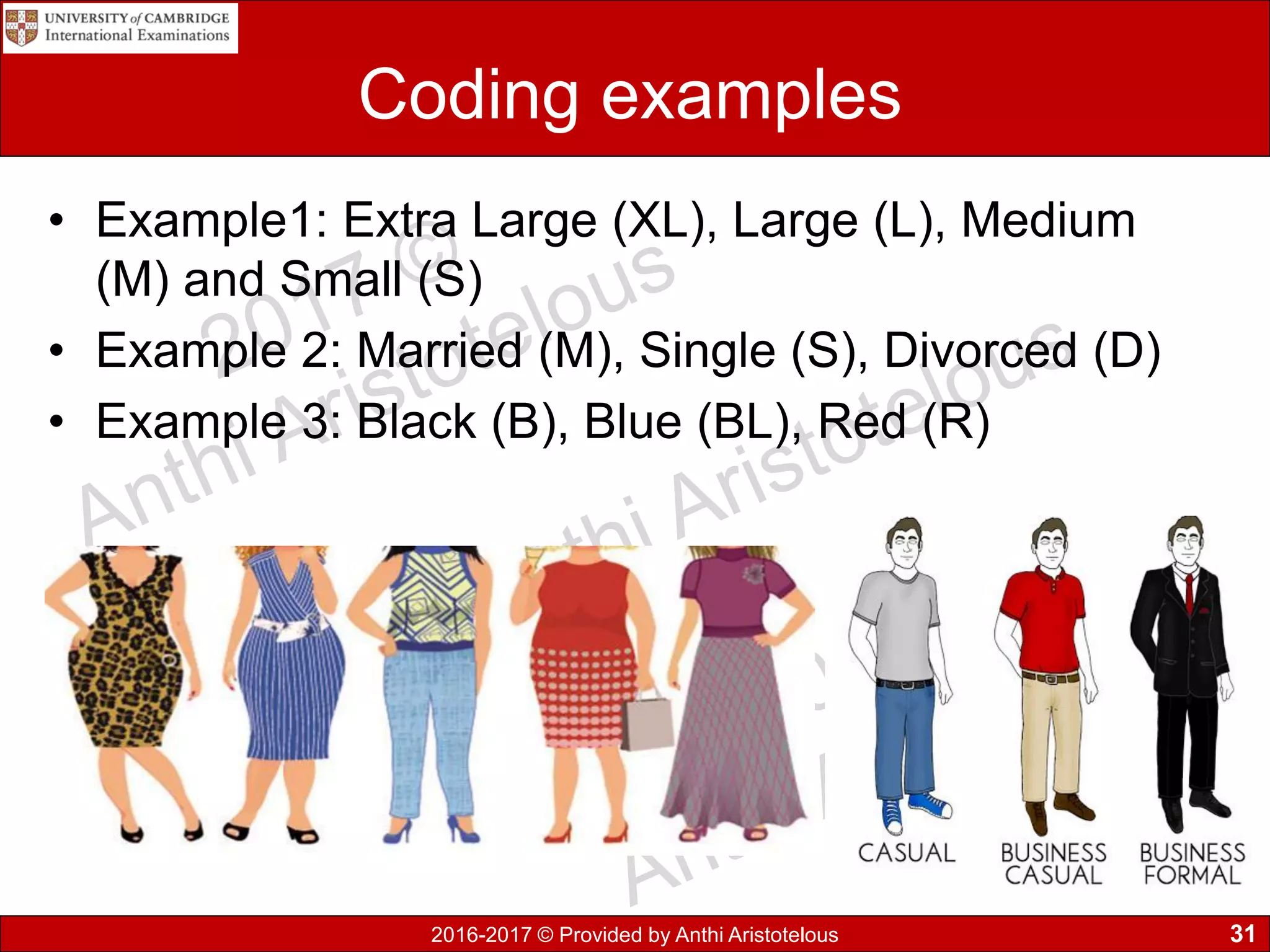
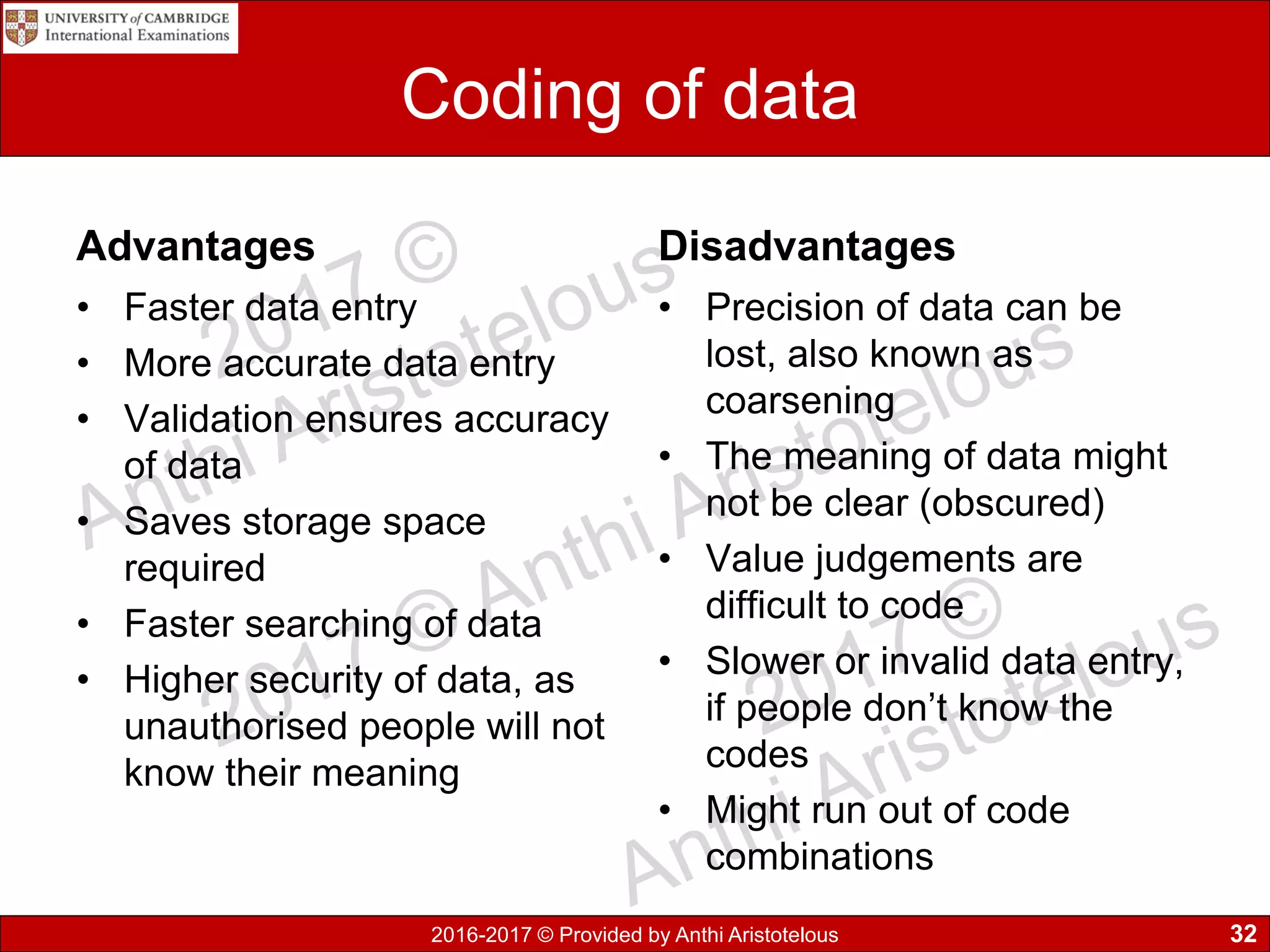
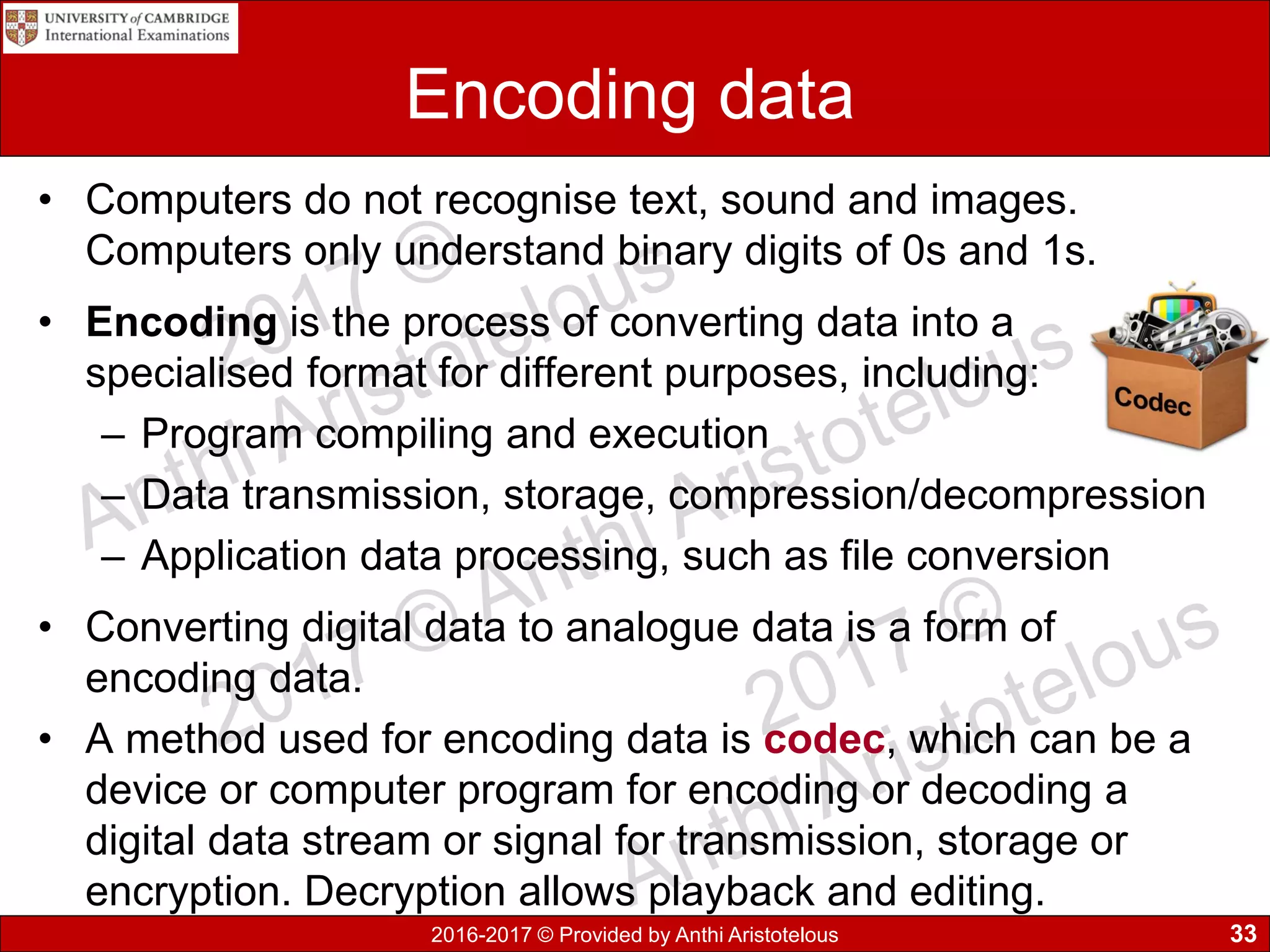
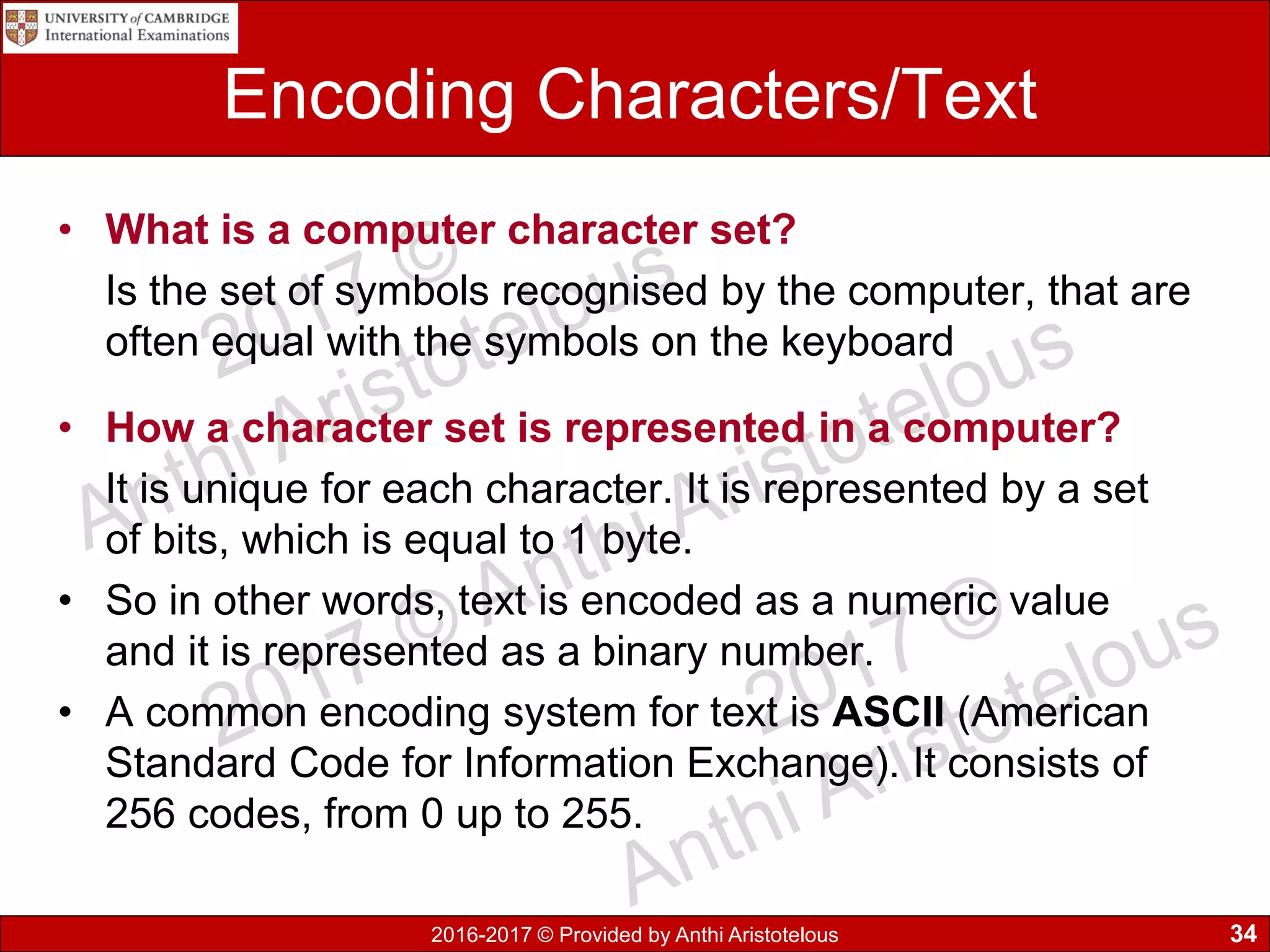
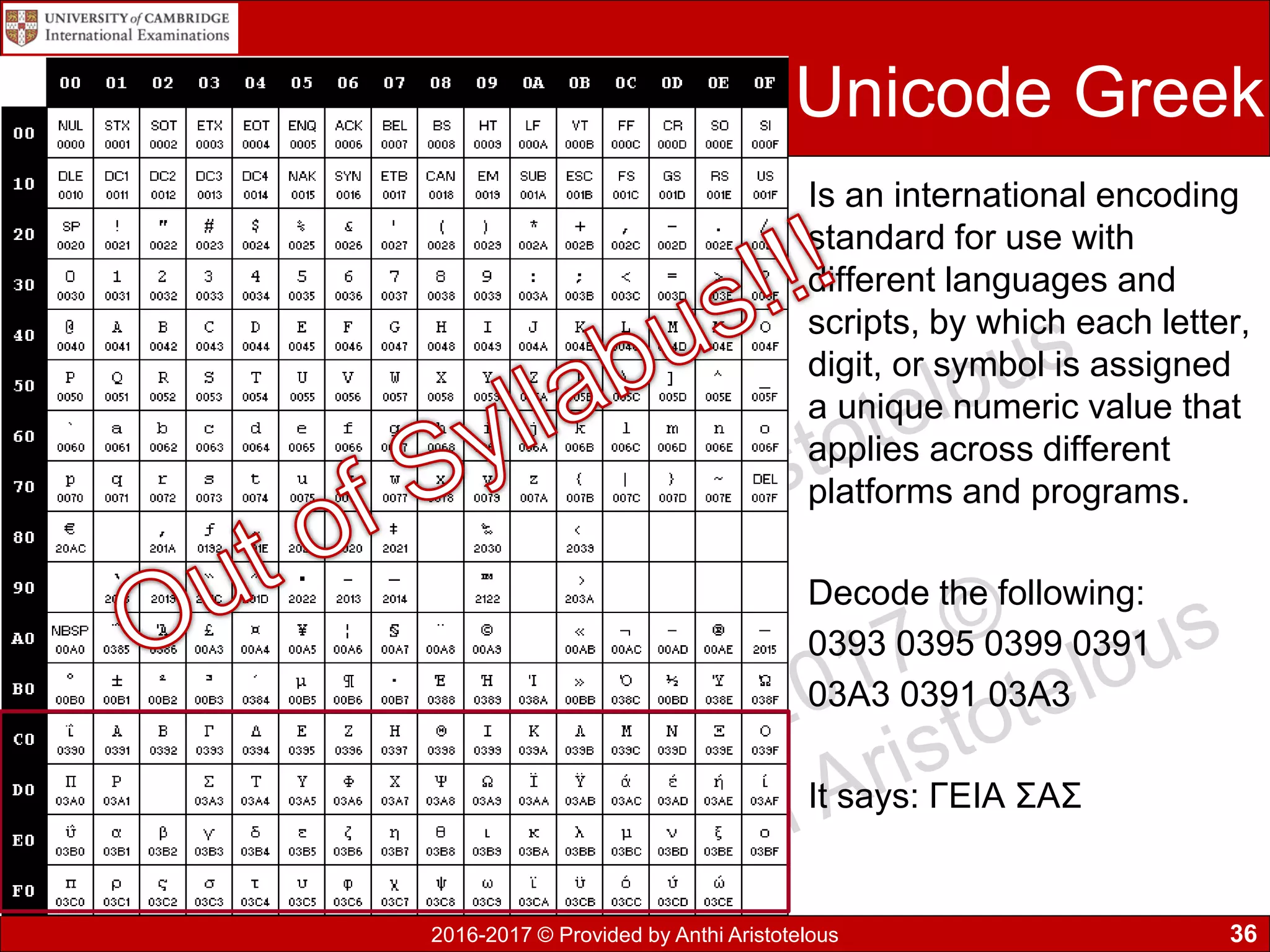
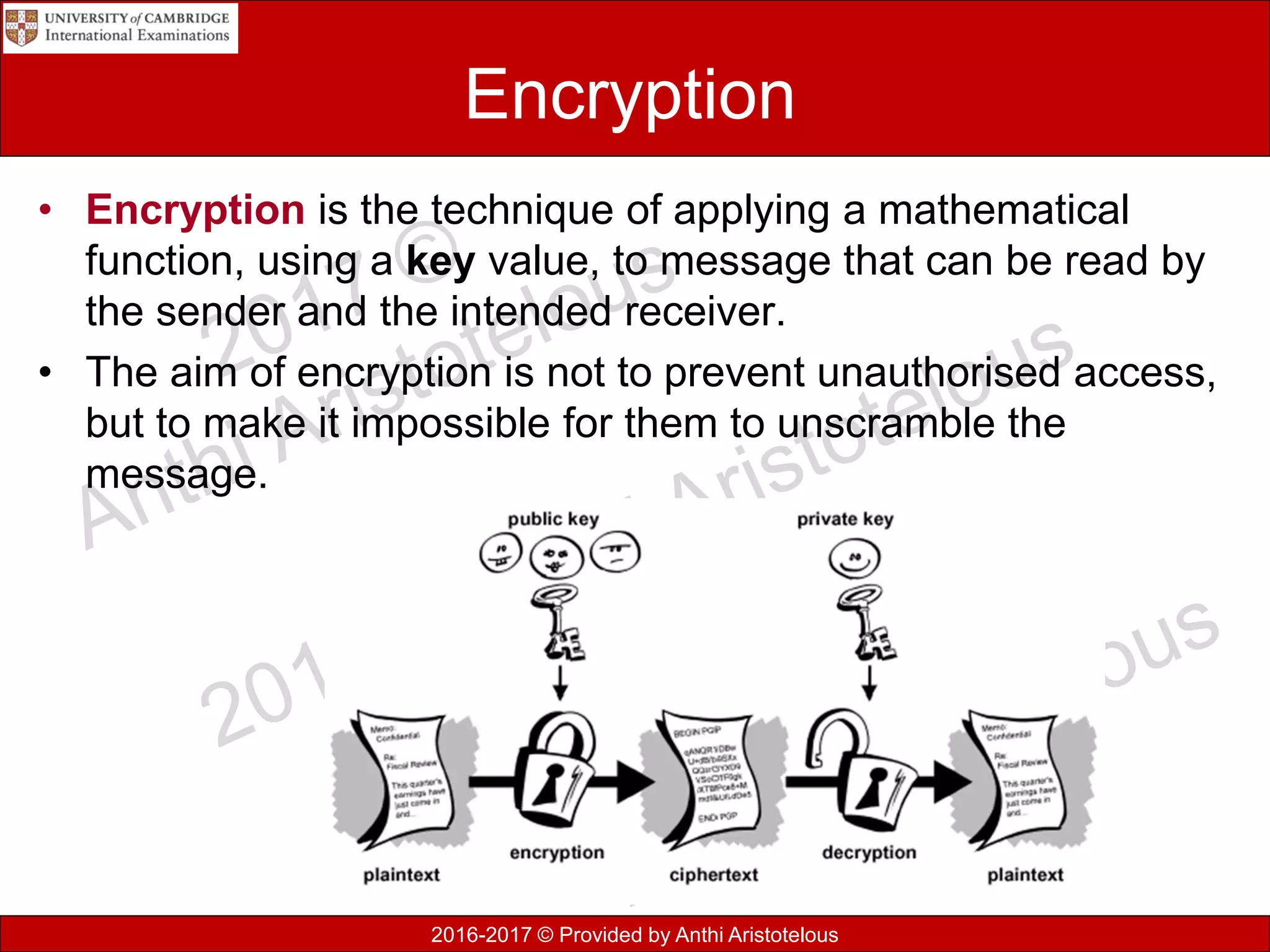
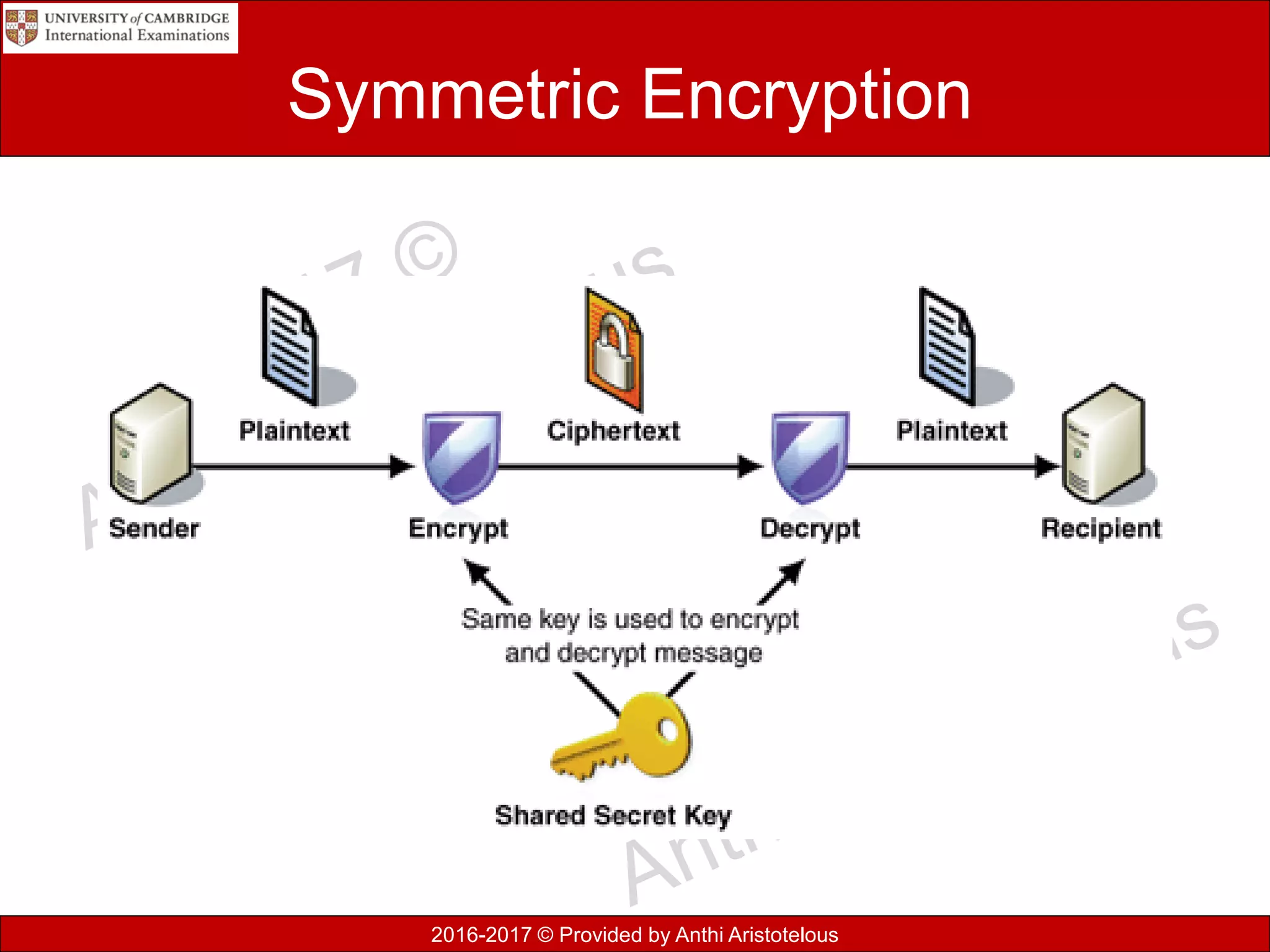
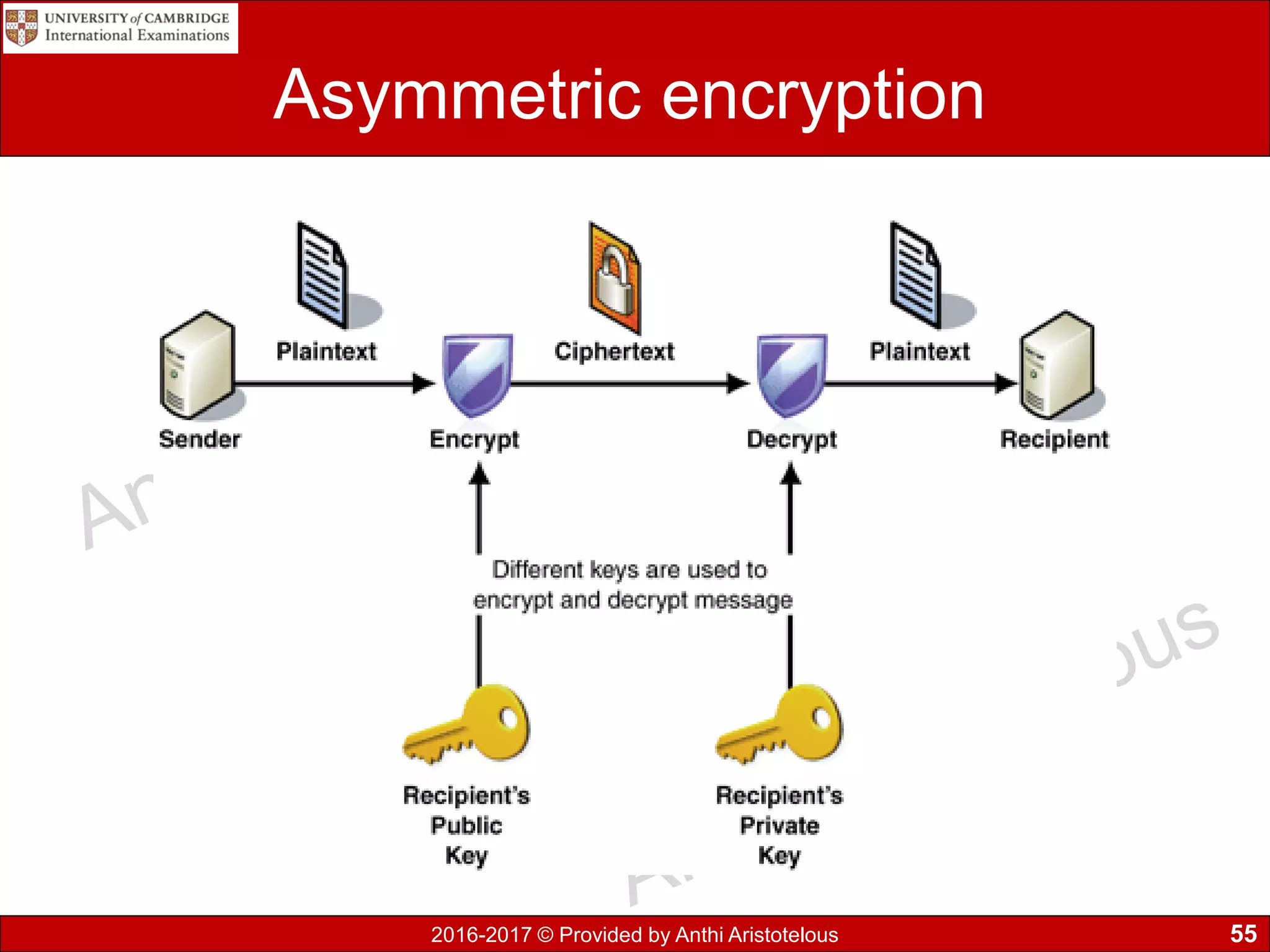
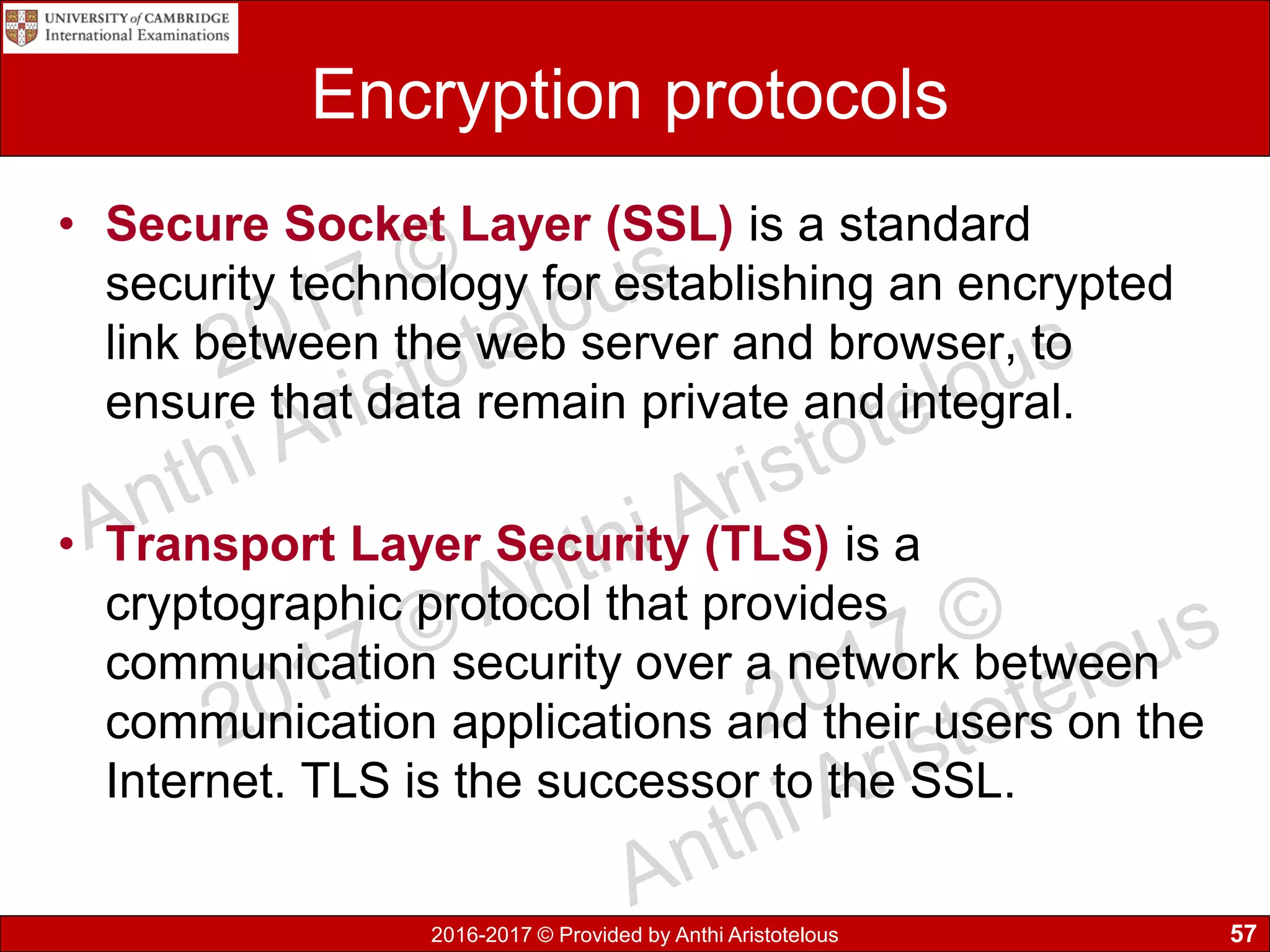
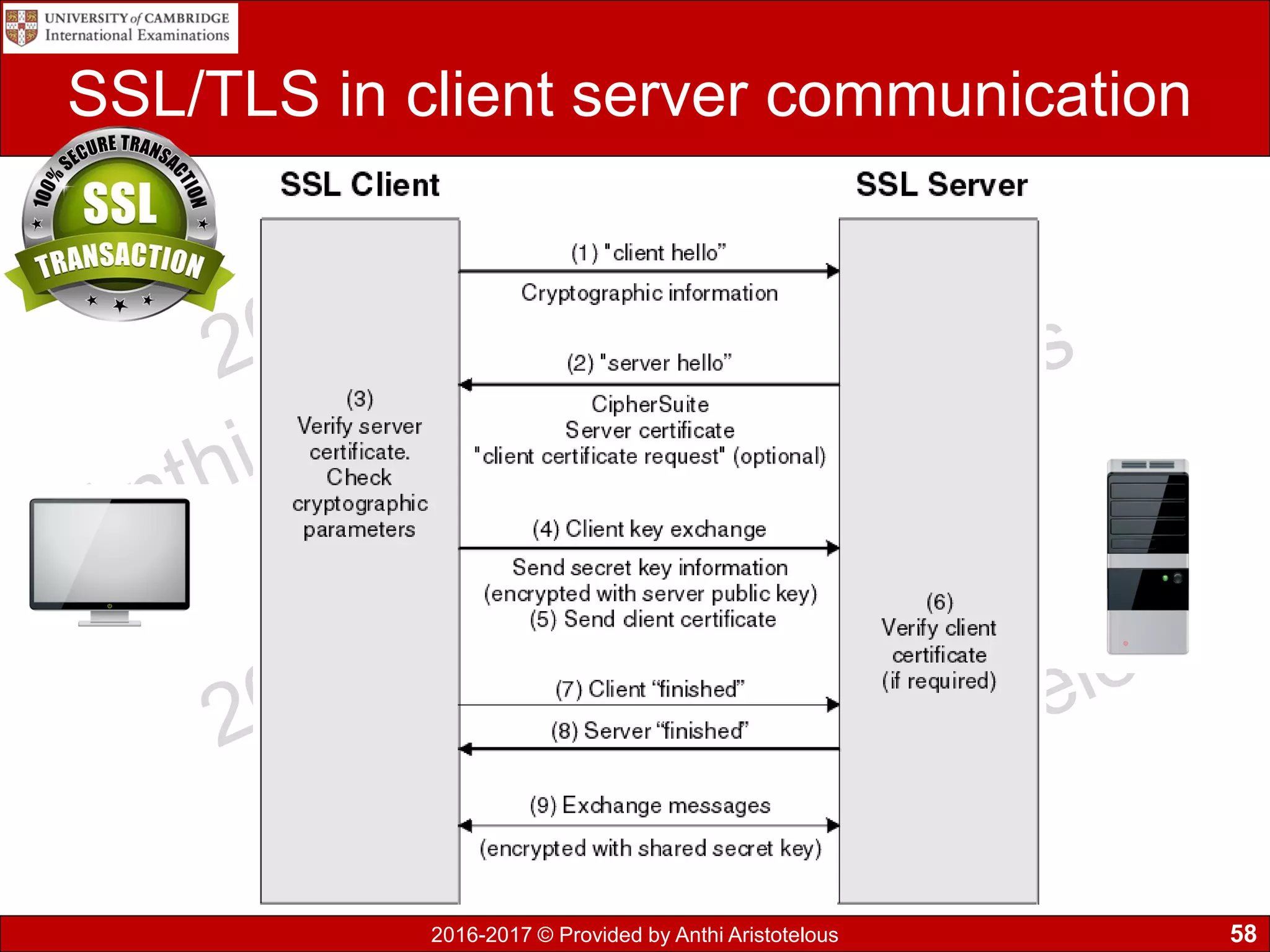
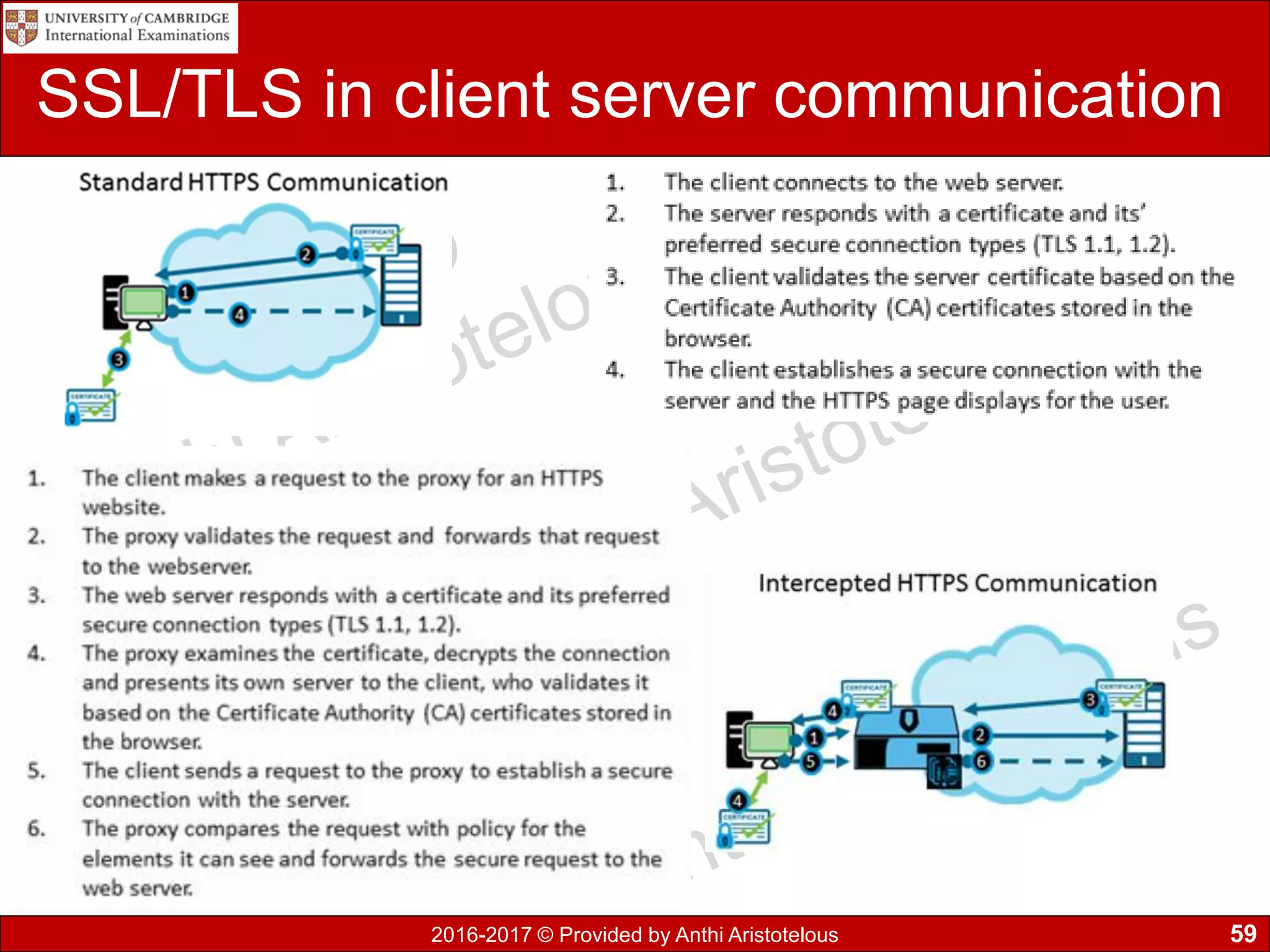
The document concludes by explaining coding, encoding, and encrypting of data. Coding assigns abbreviations