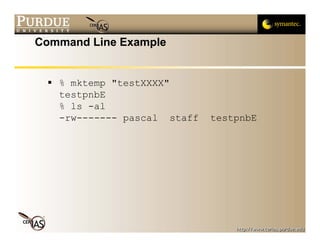
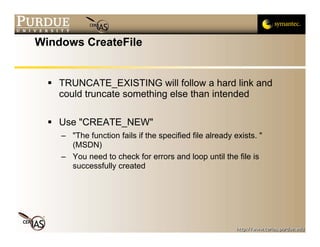
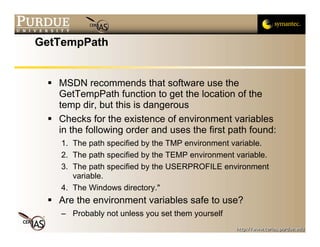
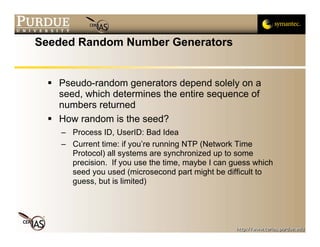
This document discusses temporary files and randomness. It outlines issues with creating temporary files in insecure directories like /tmp, including name collisions and race conditions. It recommends using OS functions like mktemp, mkstemp, and mkdtemp to generate unique, unpredictable temporary file names. It also discusses the need for cryptographically secure random numbers and recommends using OS devices like /dev/urandom as sources of randomness.