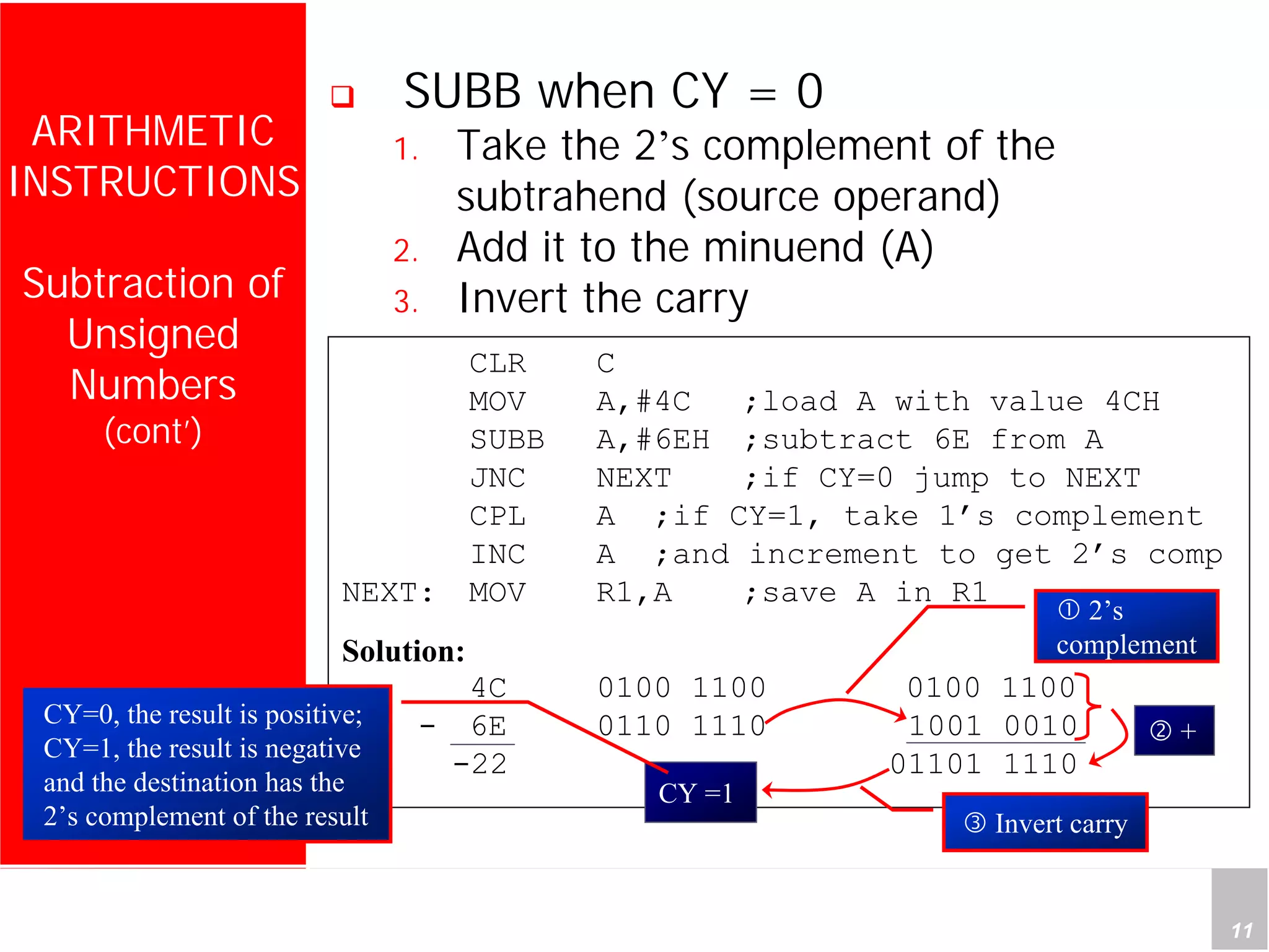
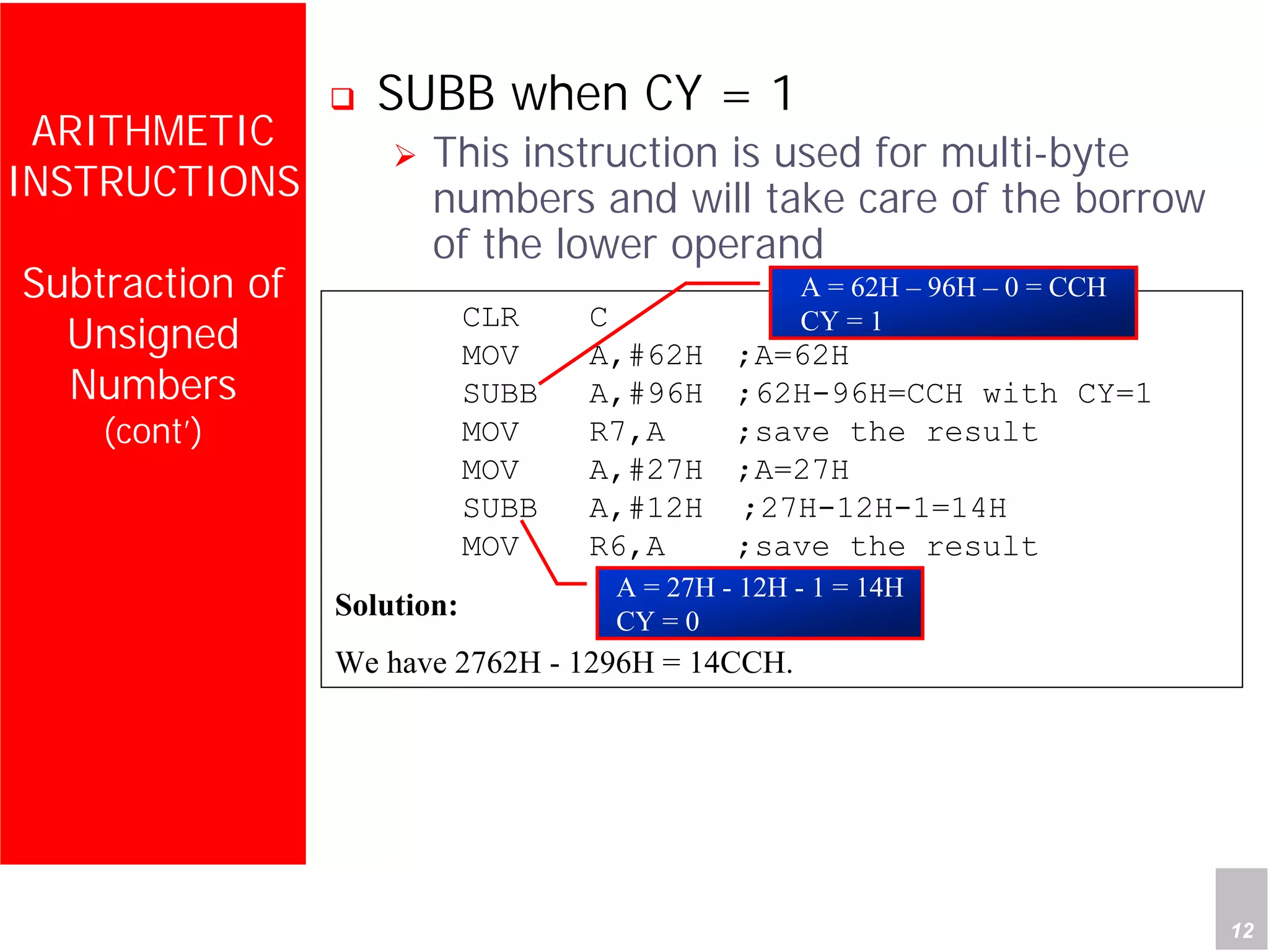
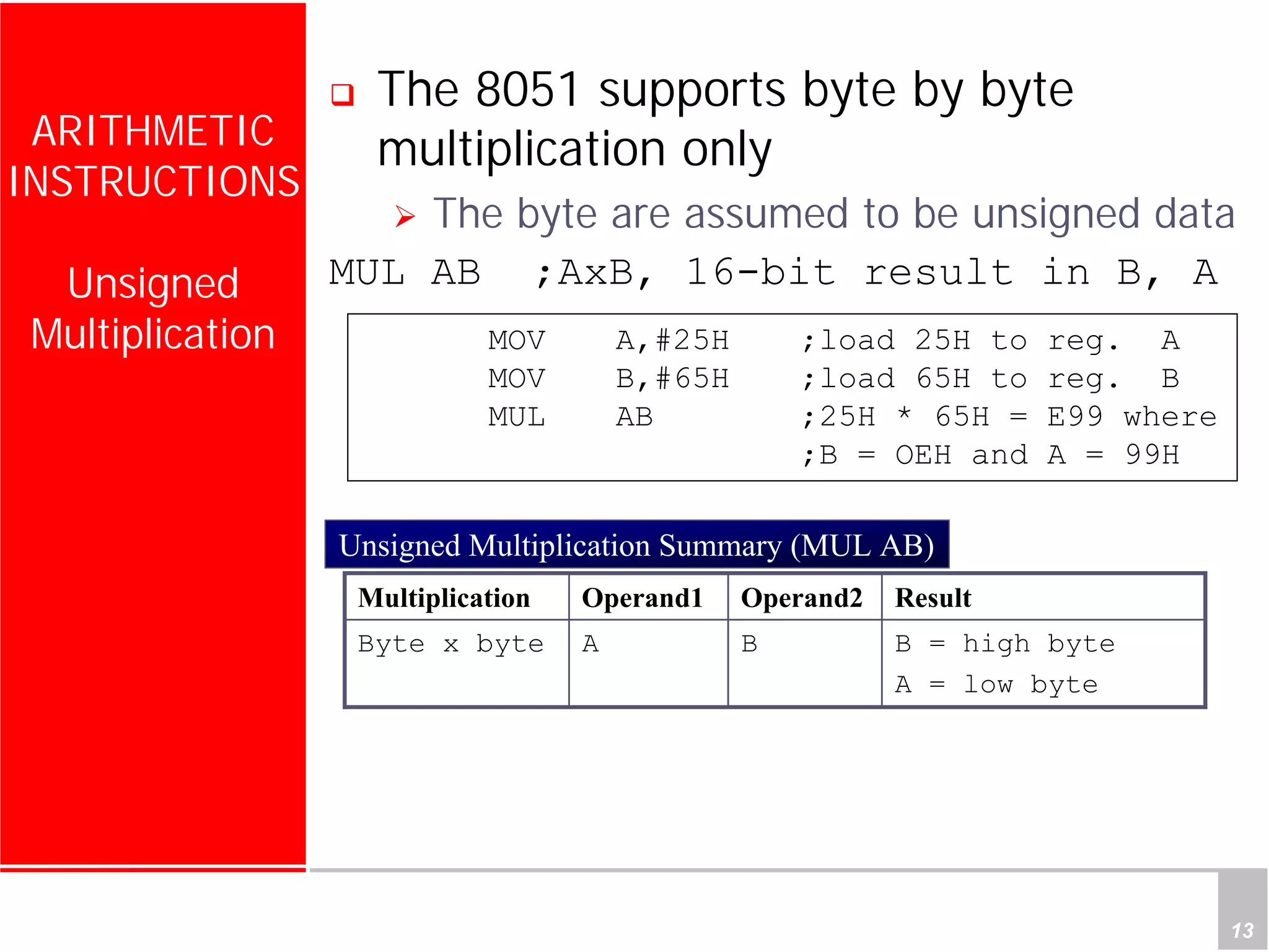
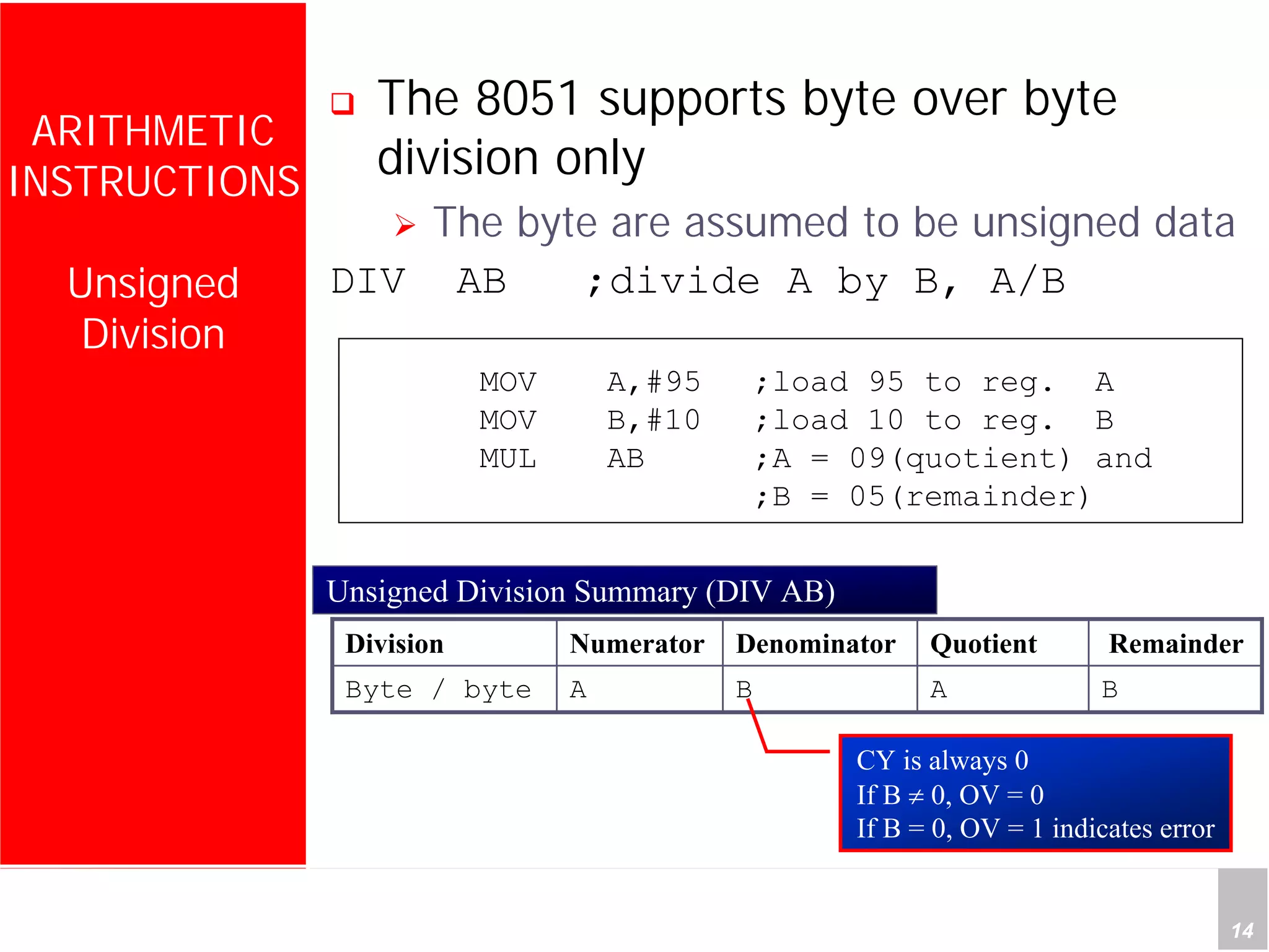
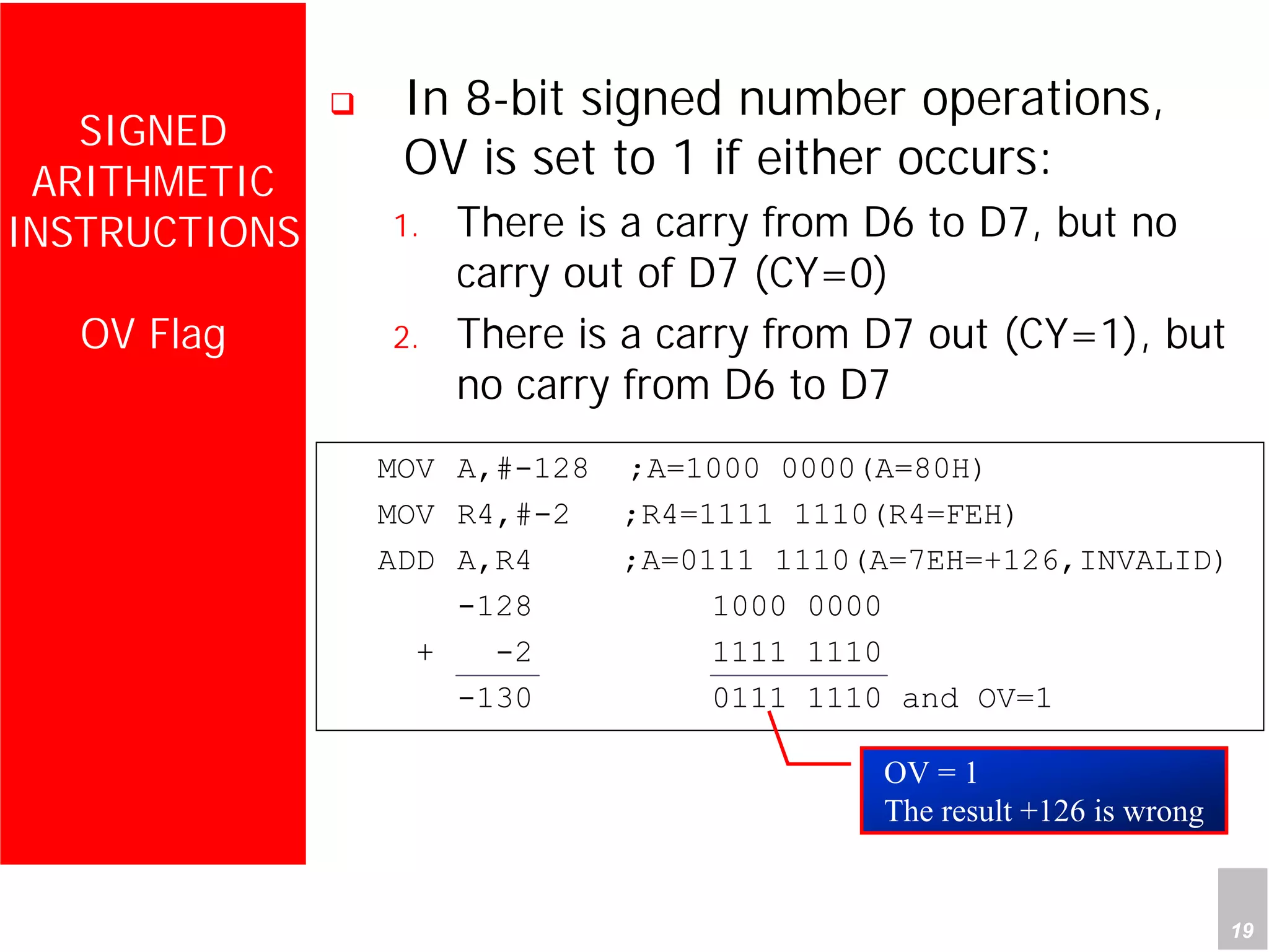
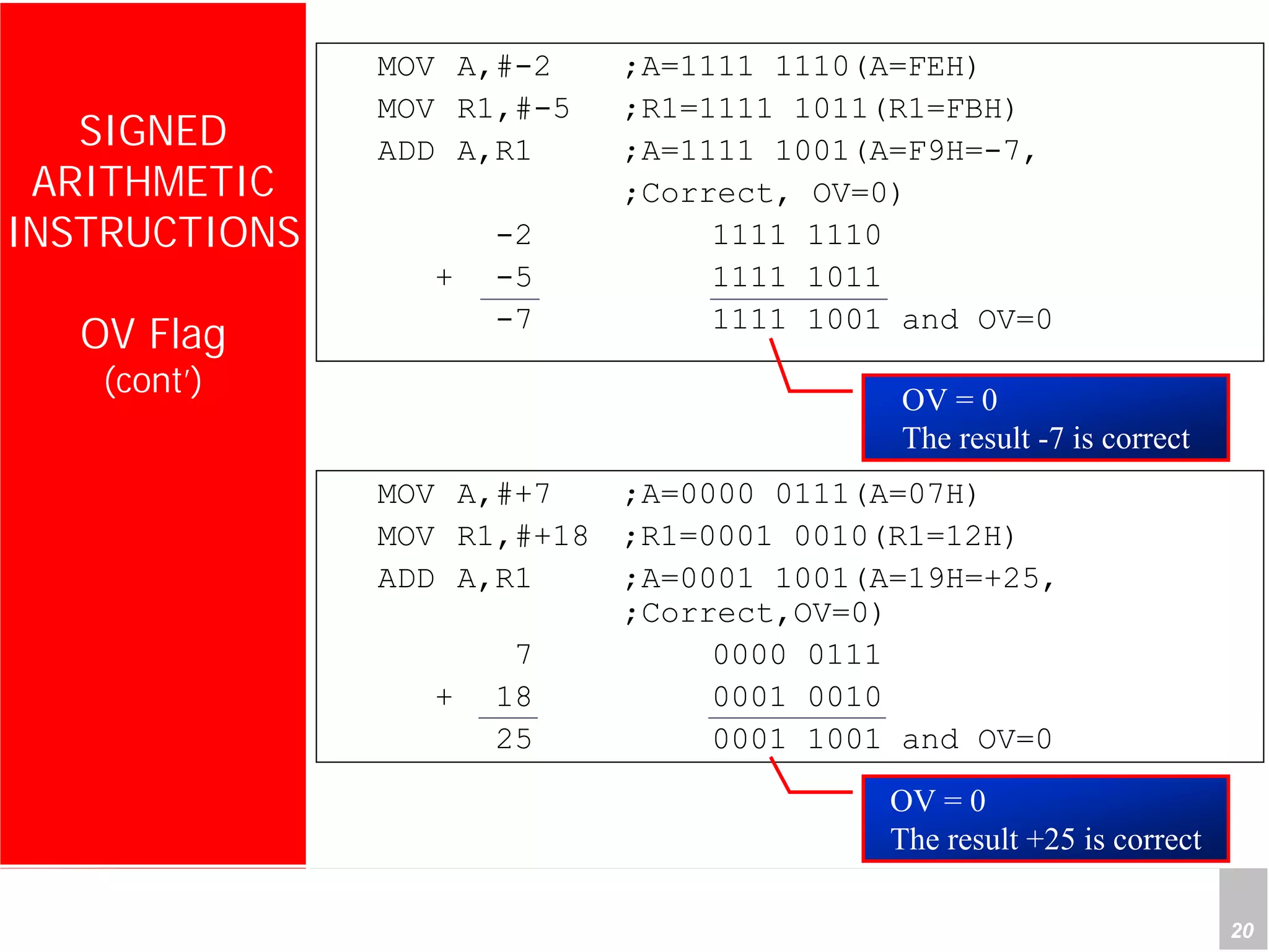
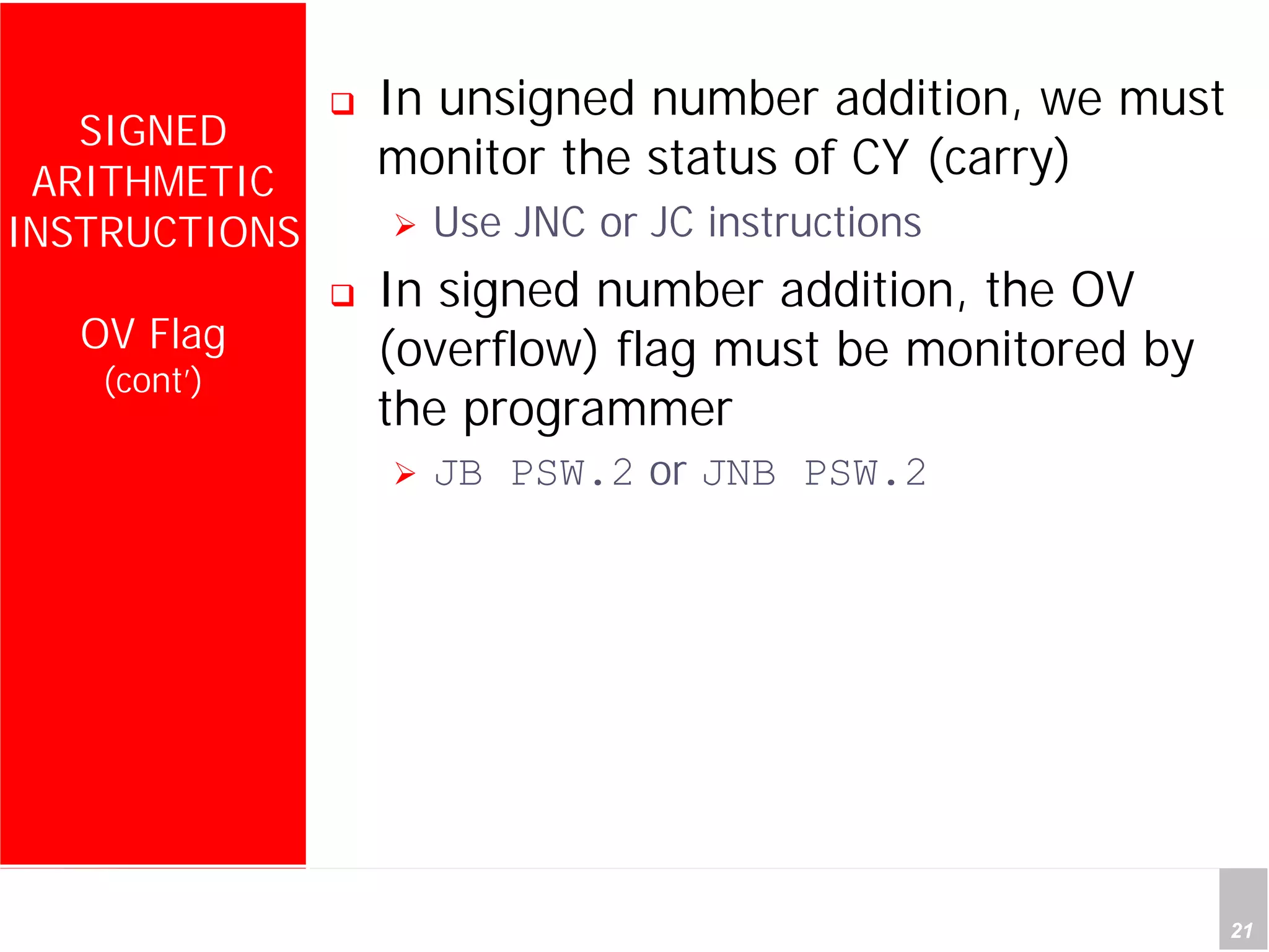
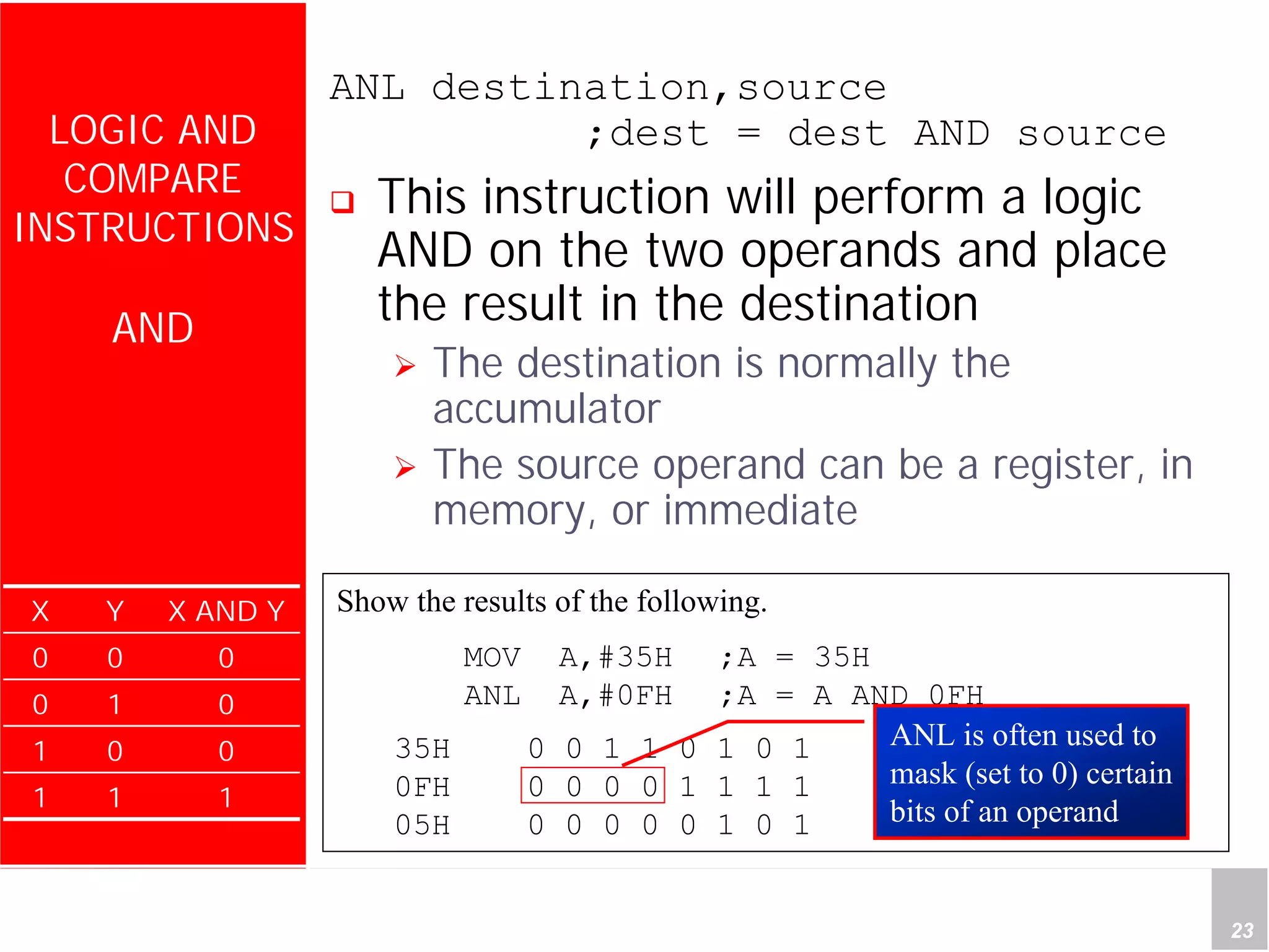
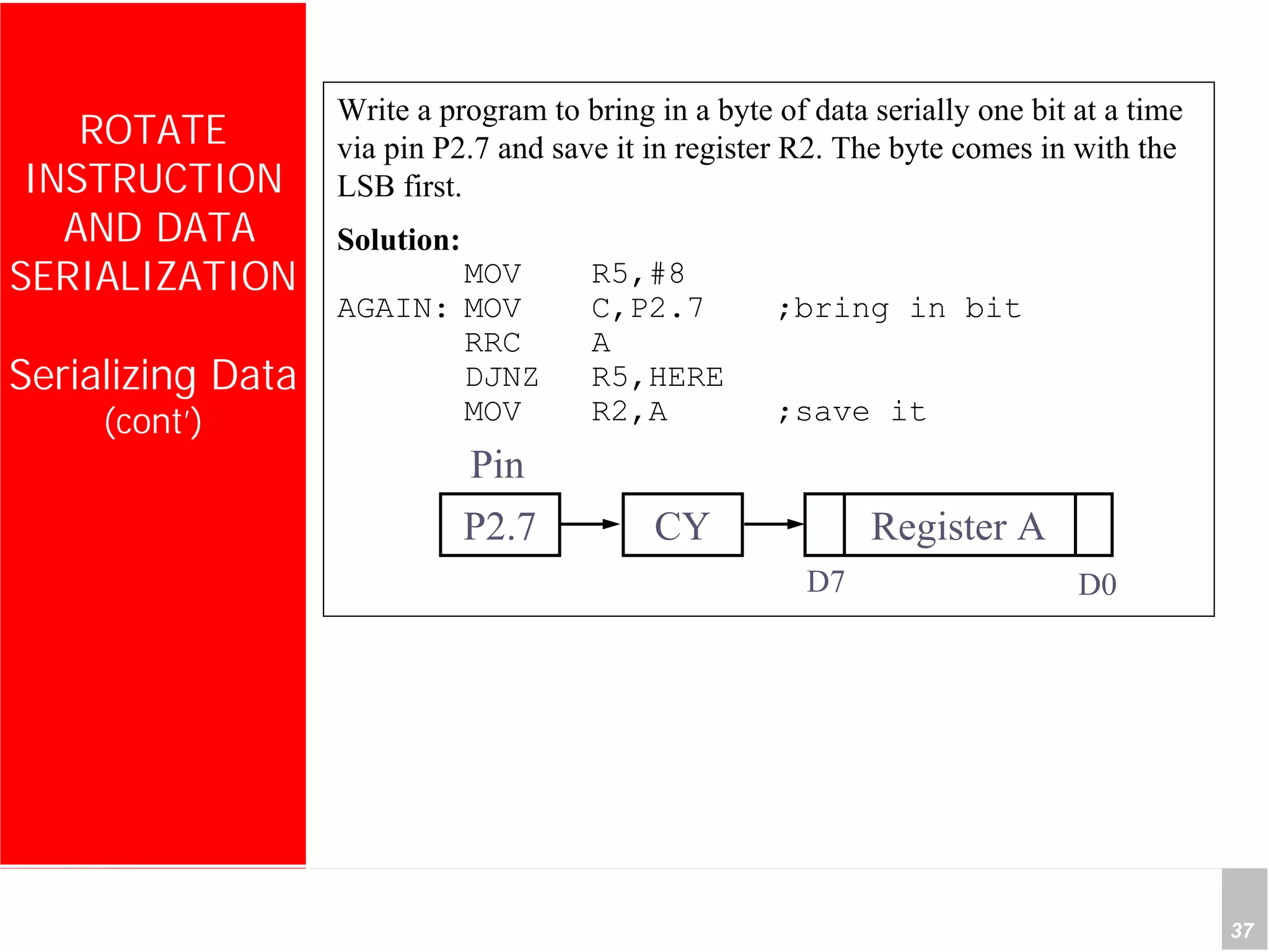
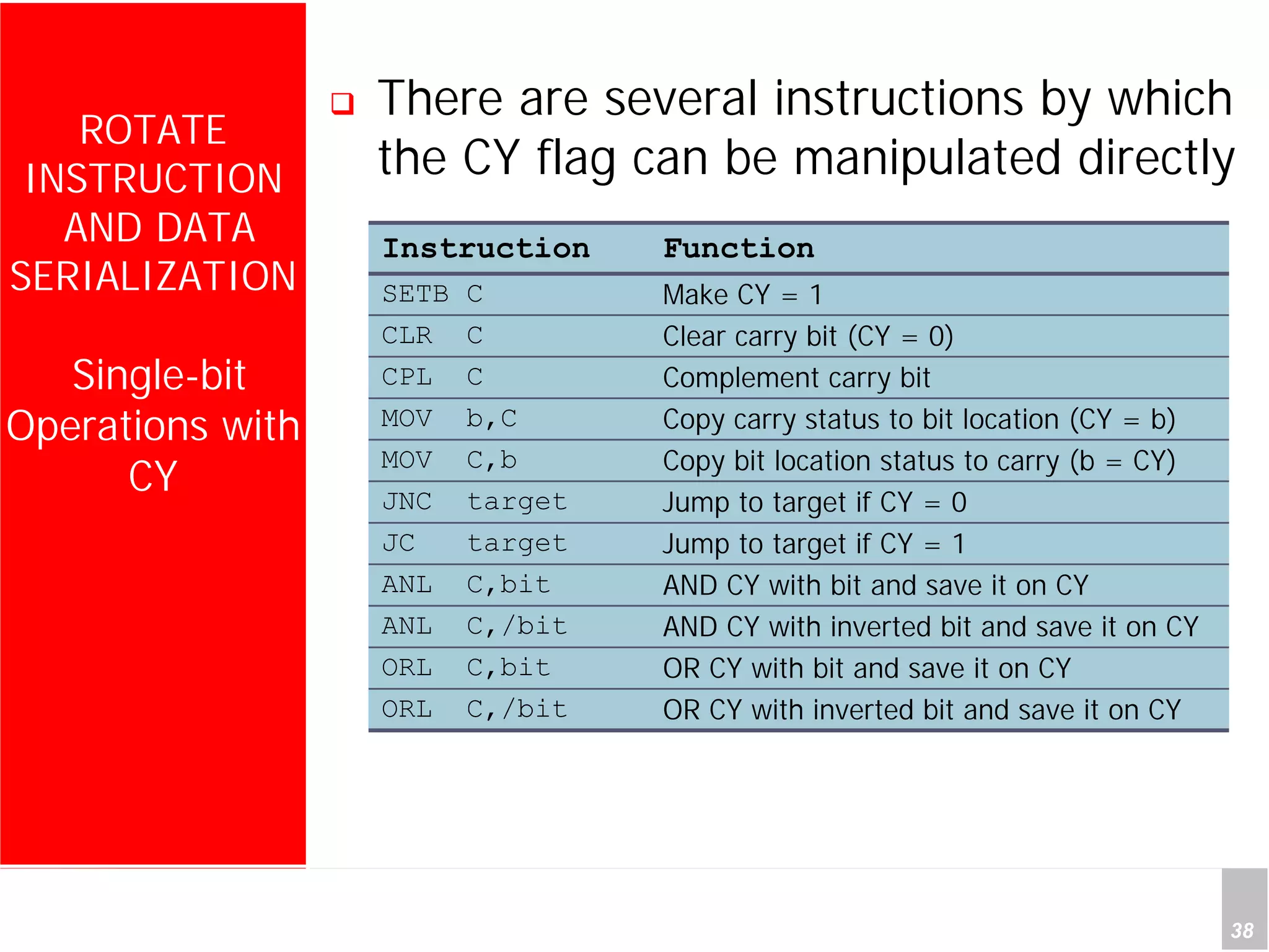
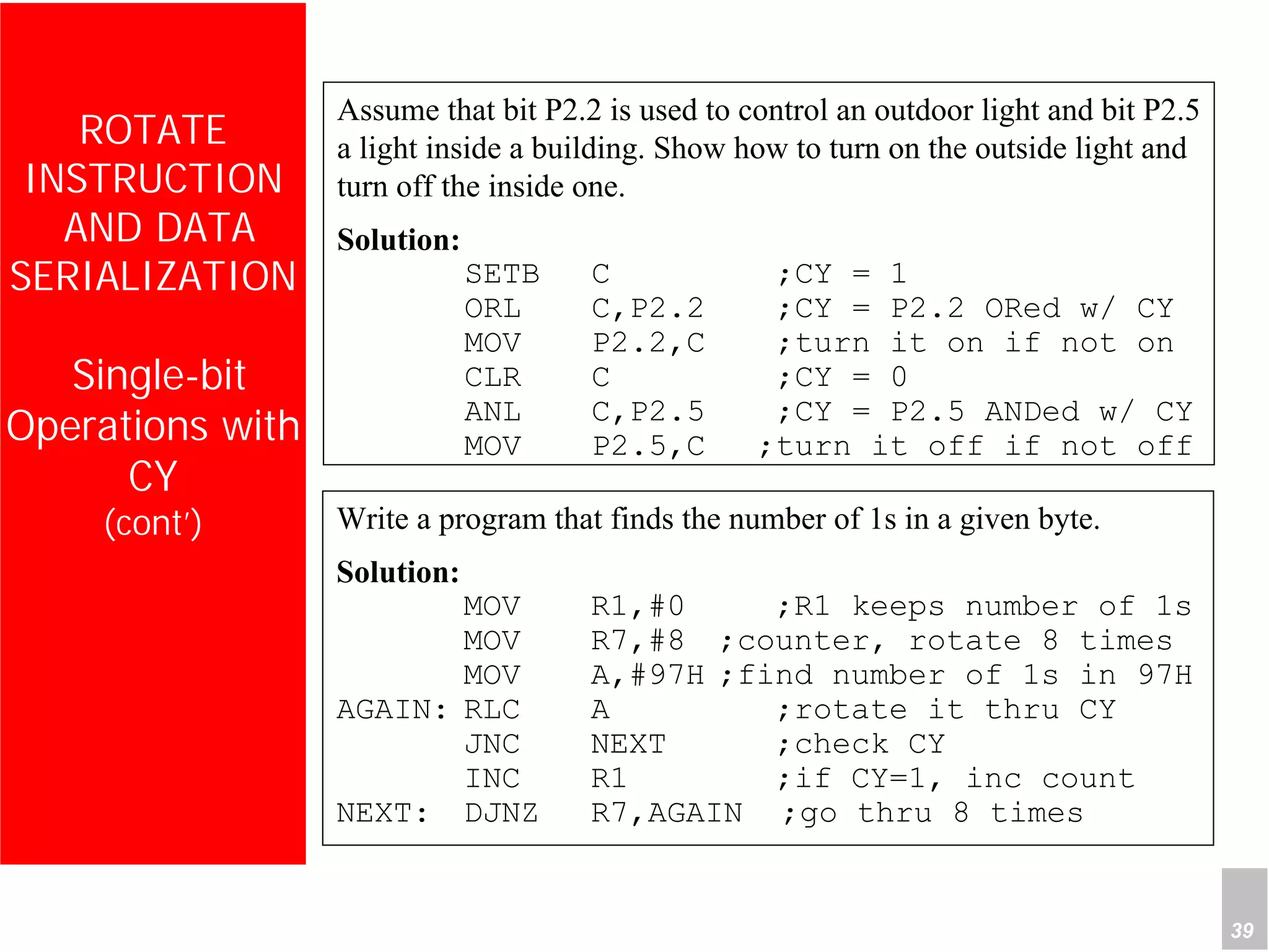
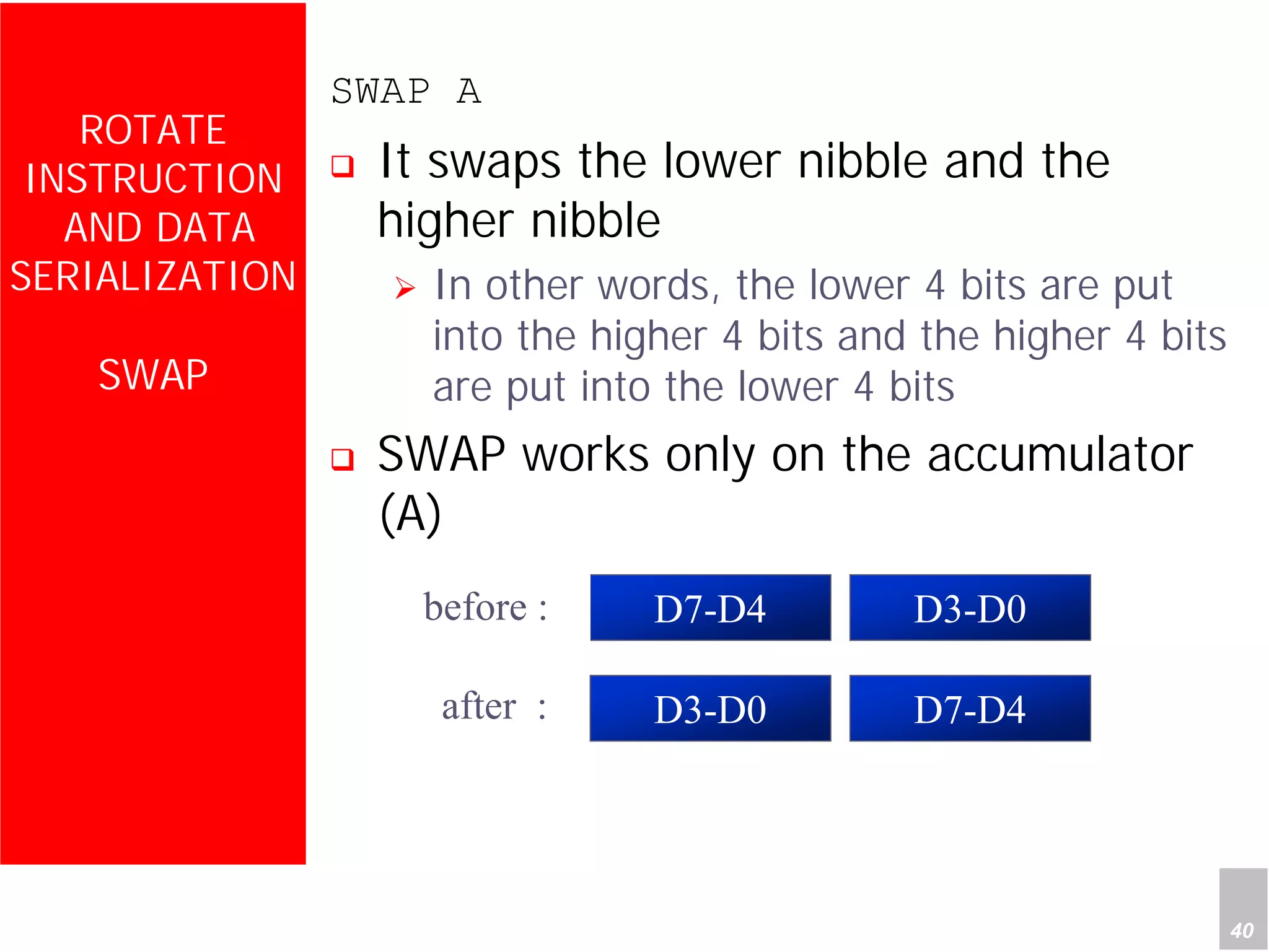
1) The document discusses arithmetic instructions for the 8051 microcontroller, including addition, subtraction, multiplication, and division.
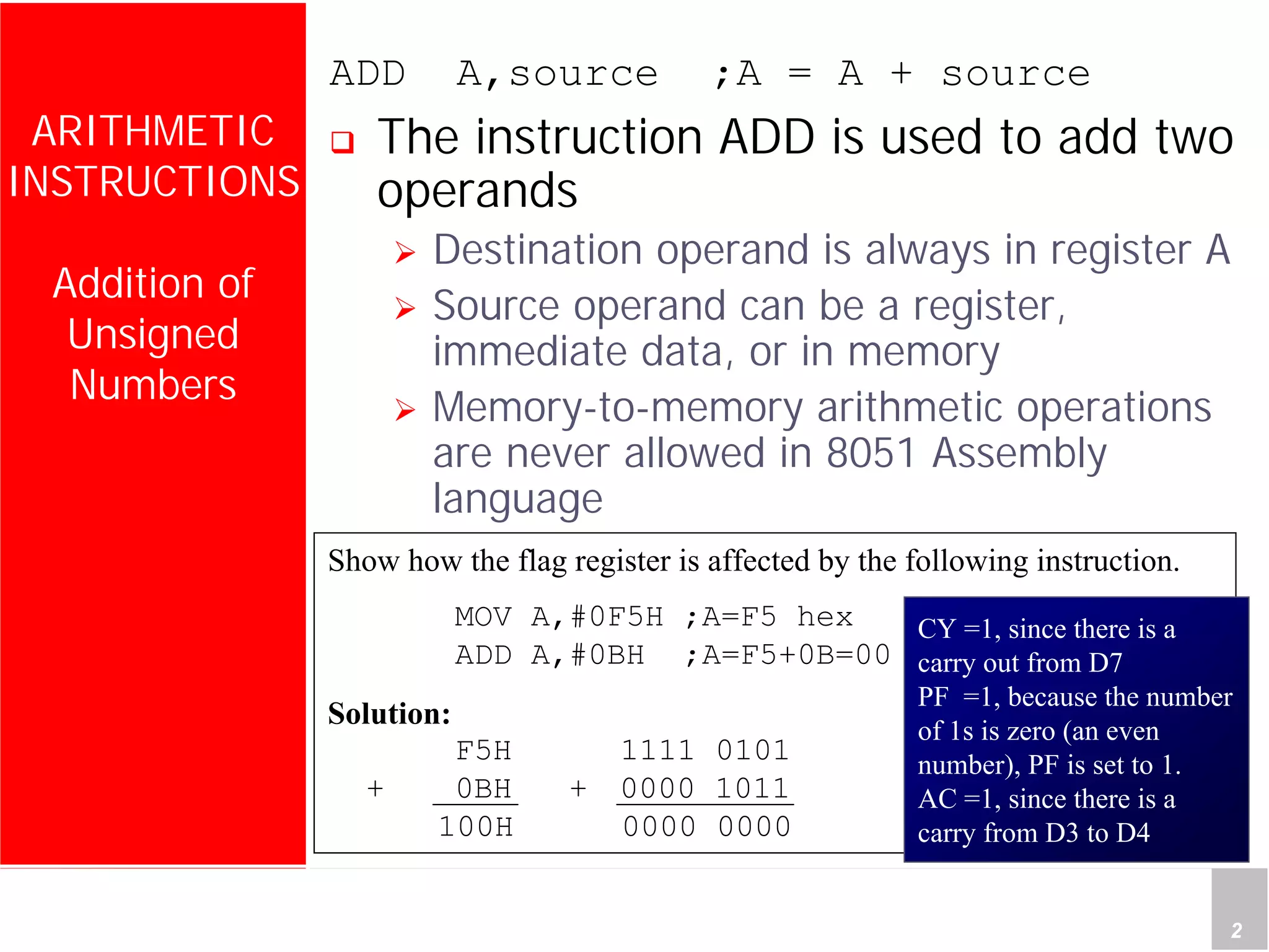
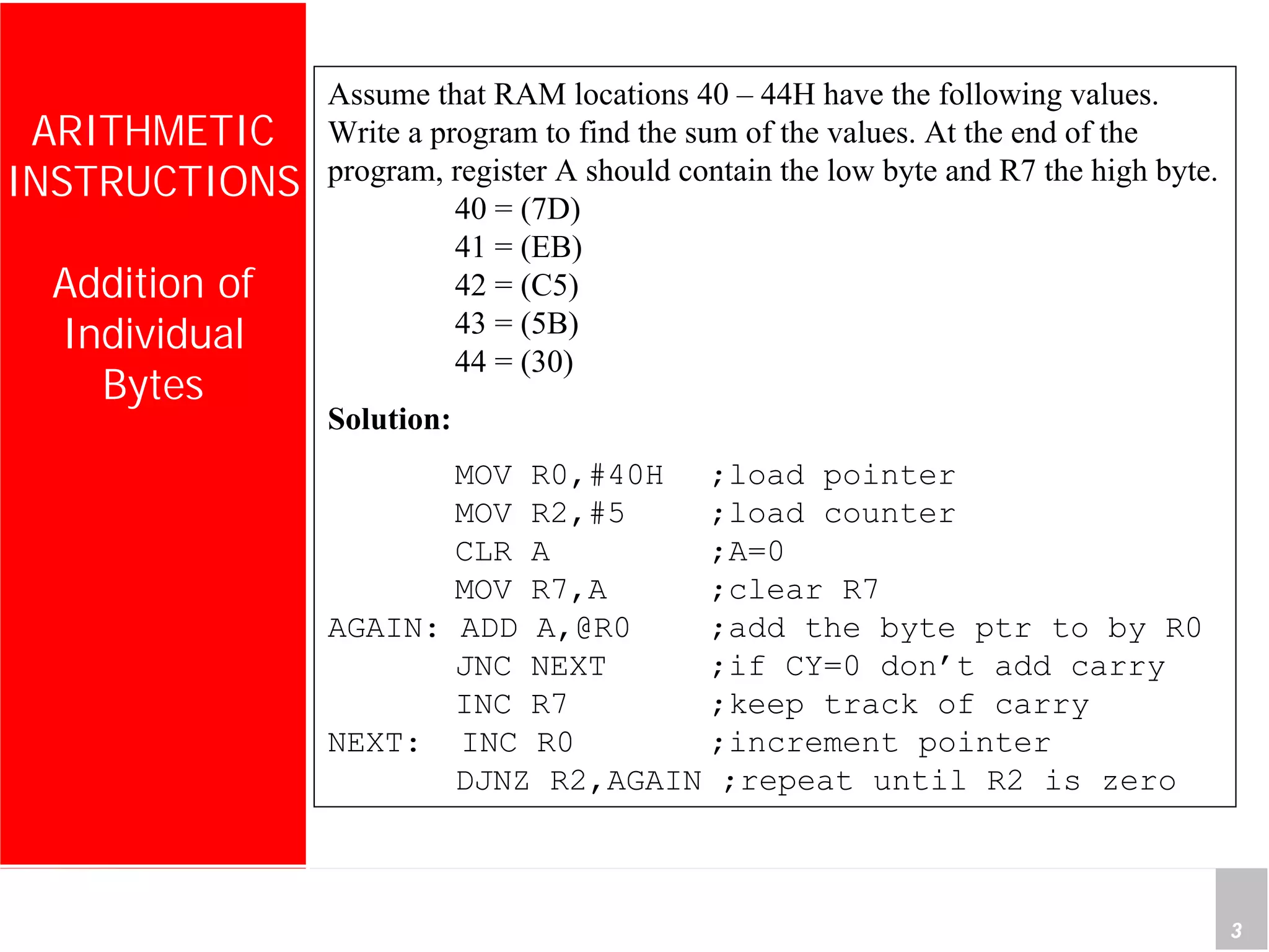
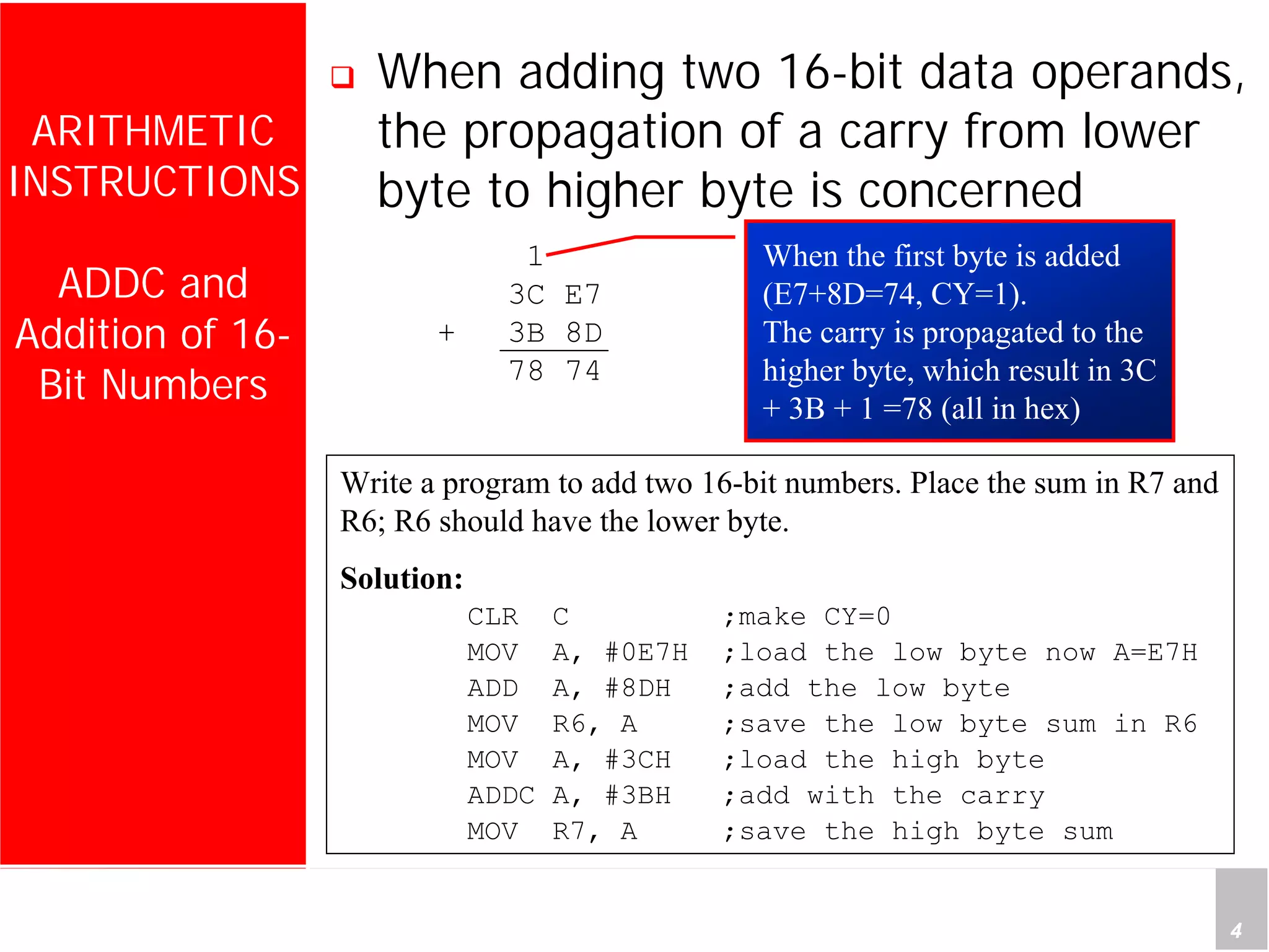
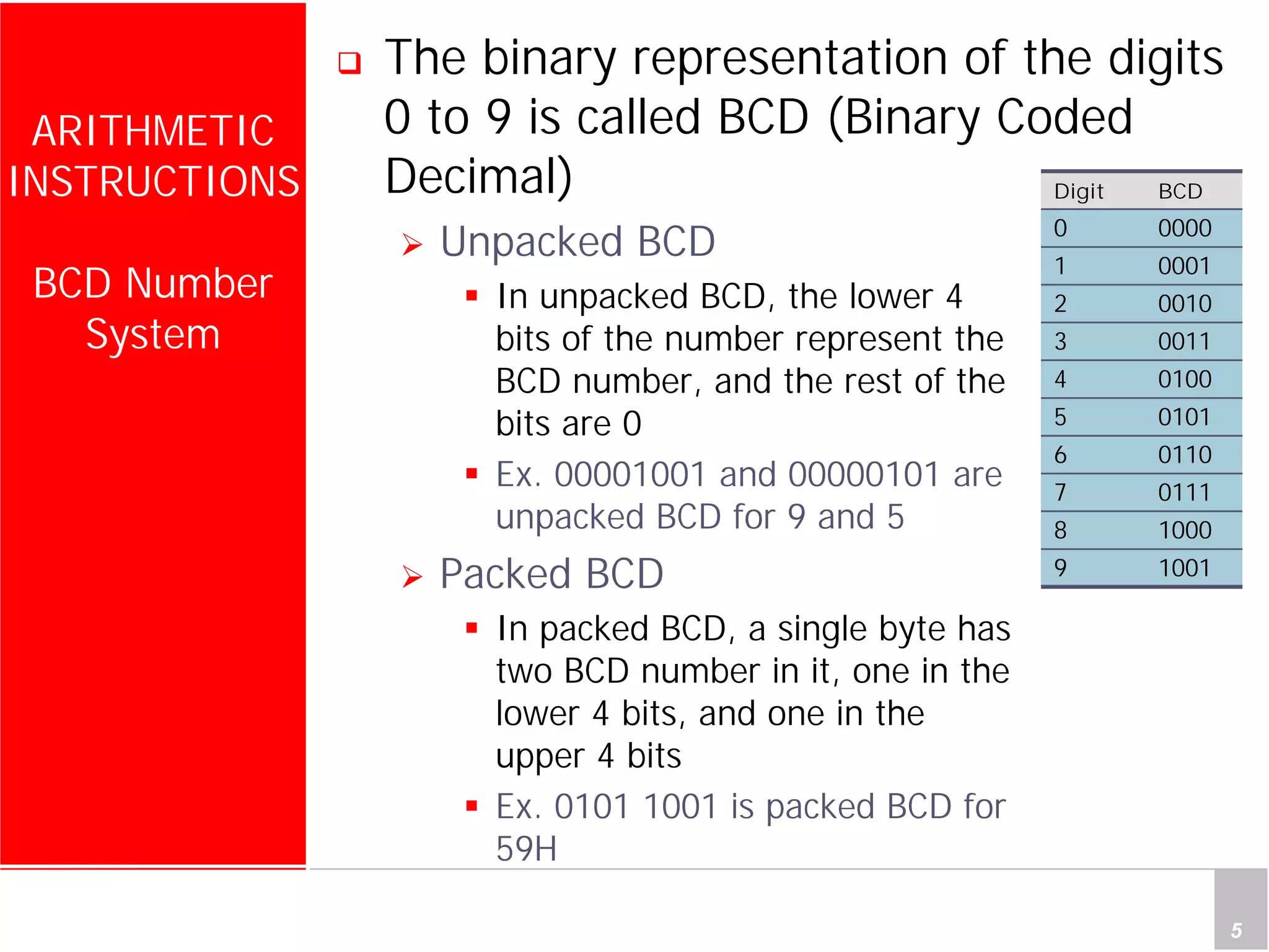
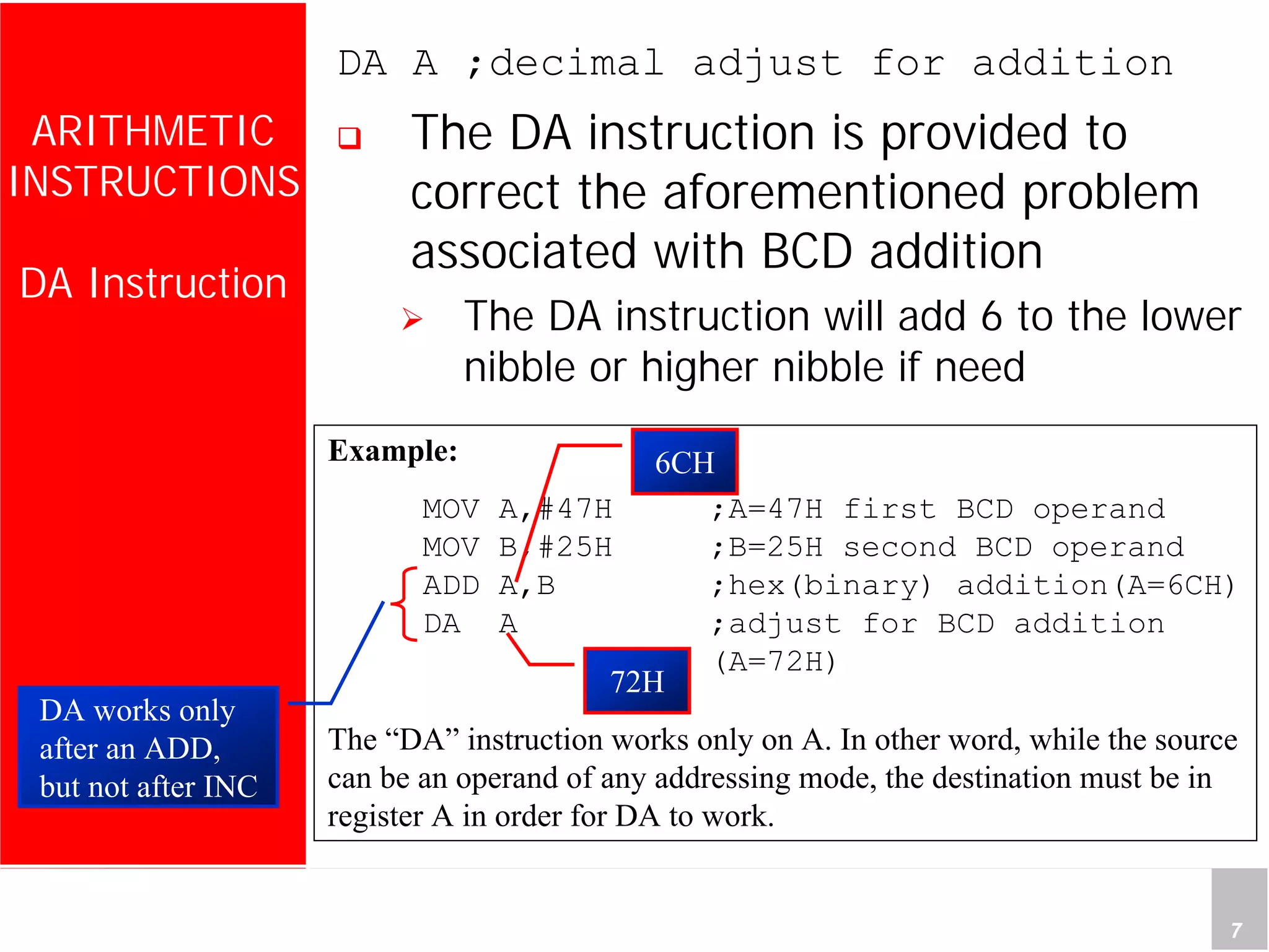
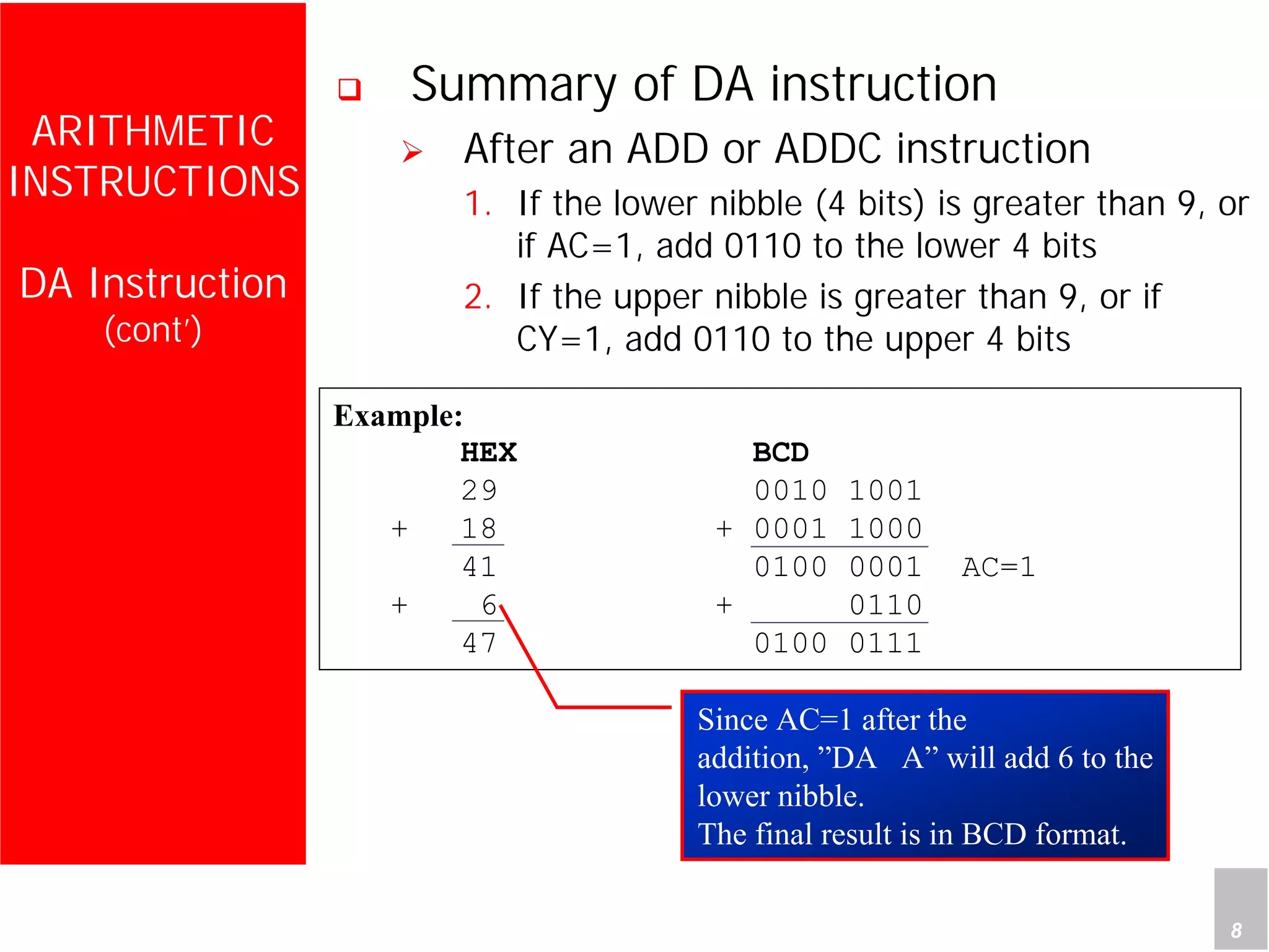
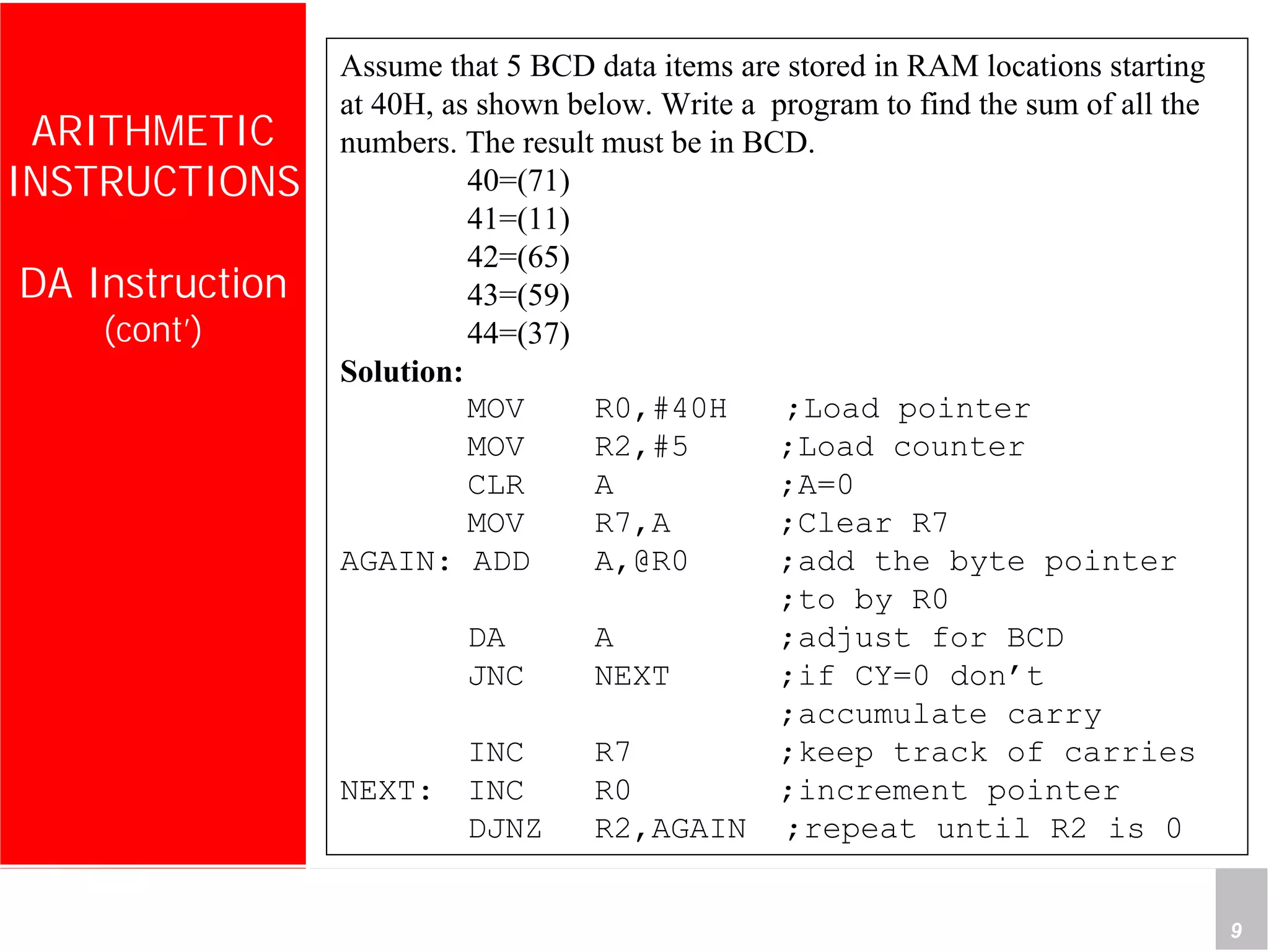
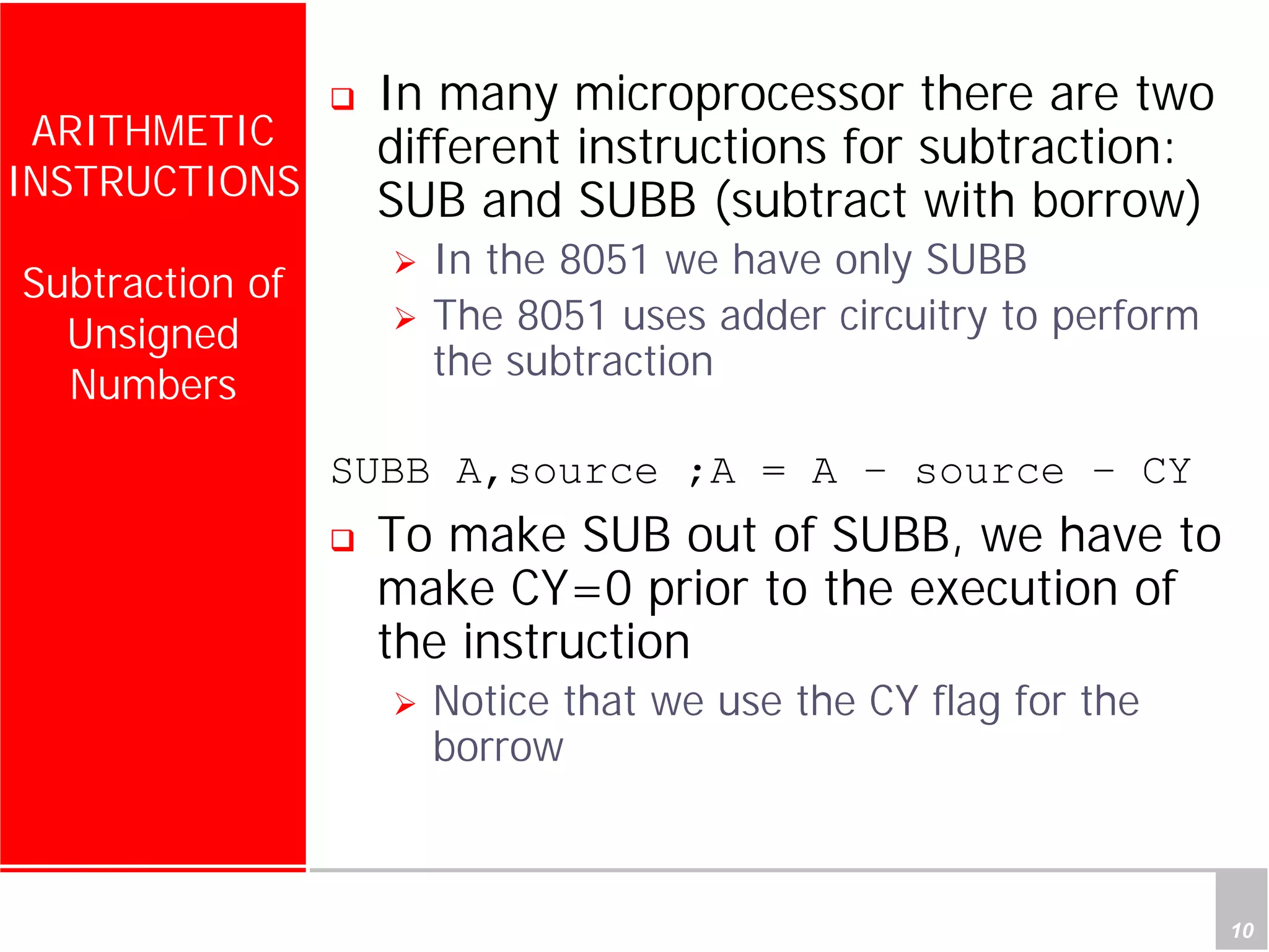
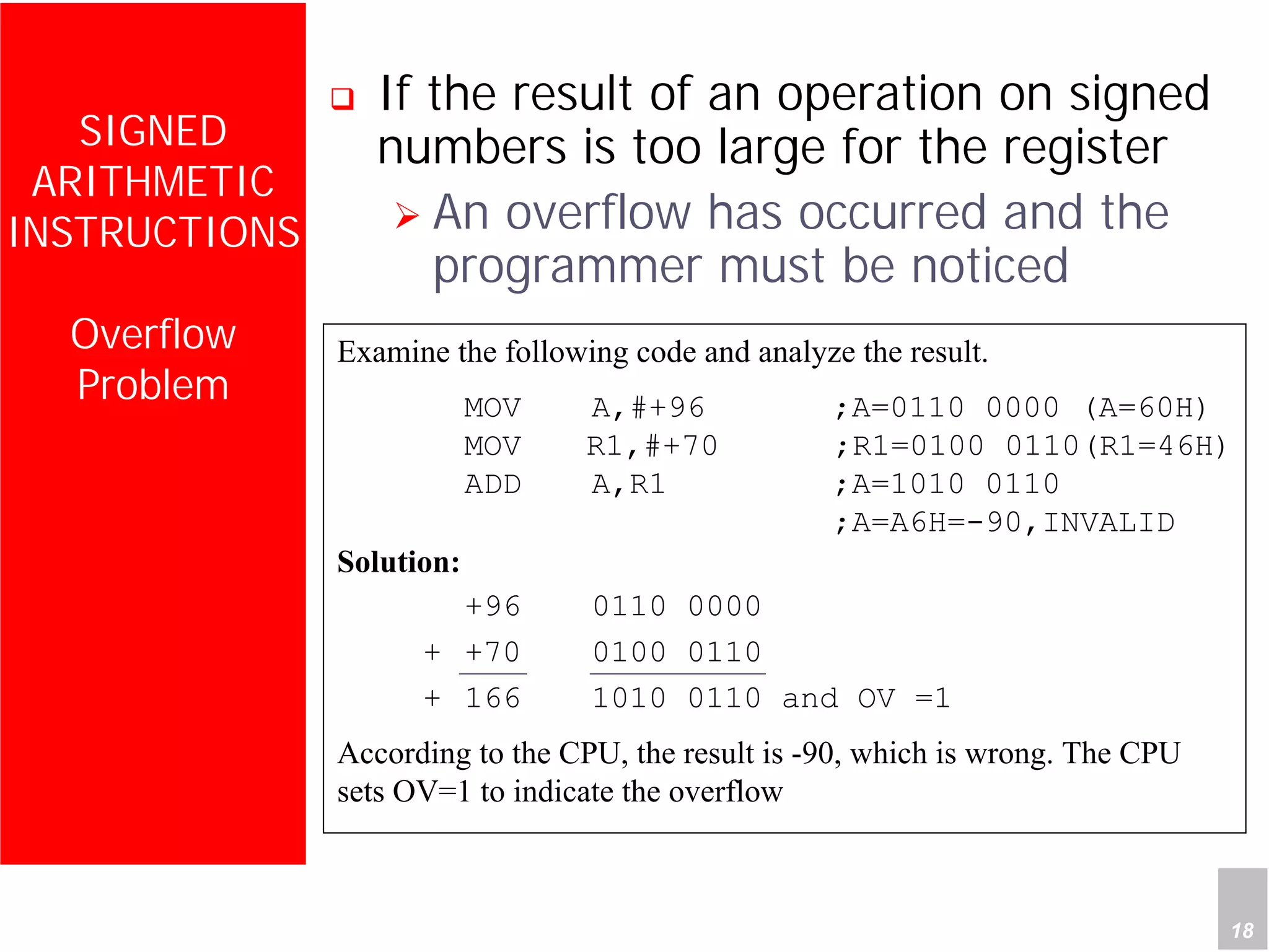
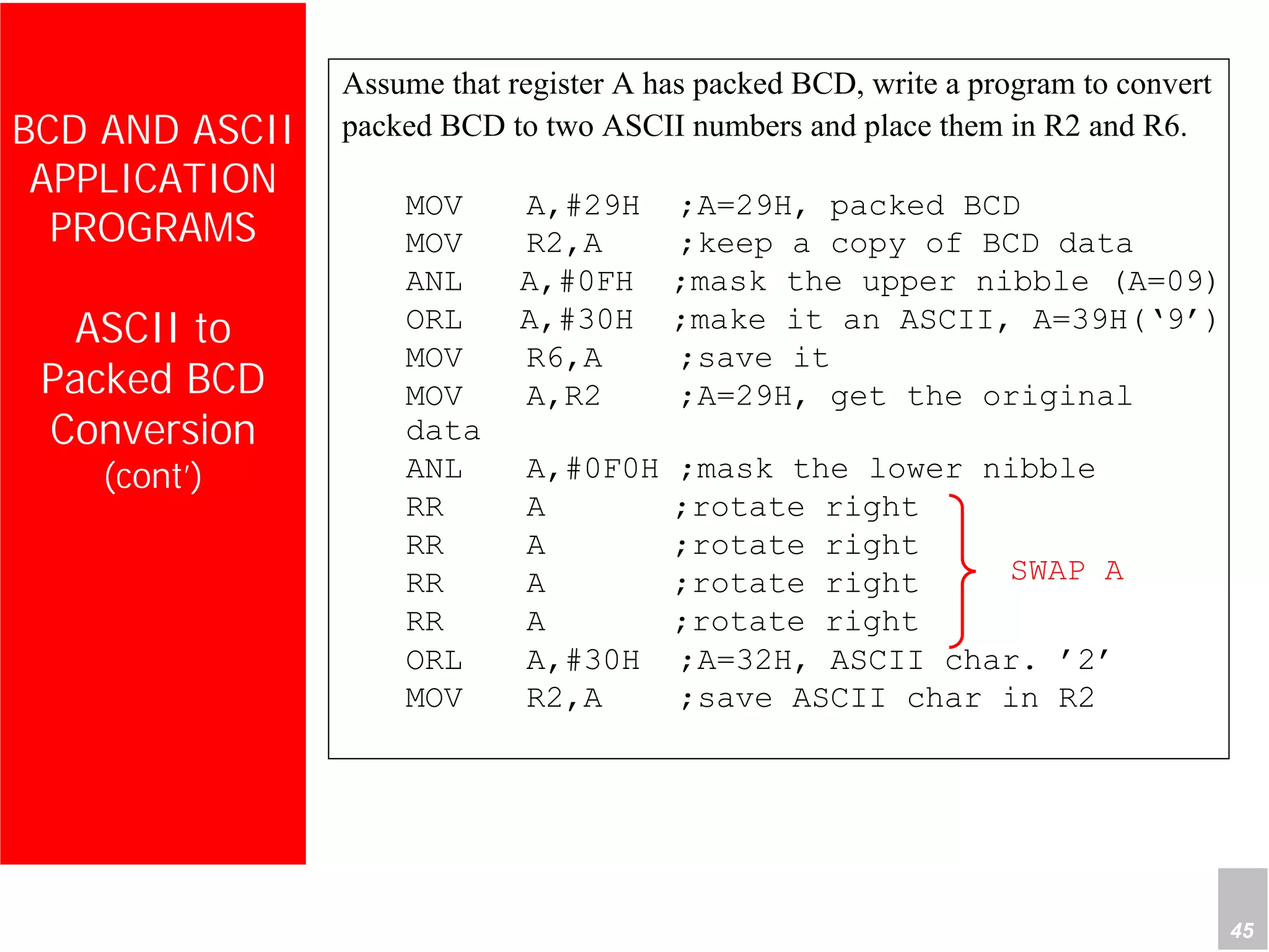
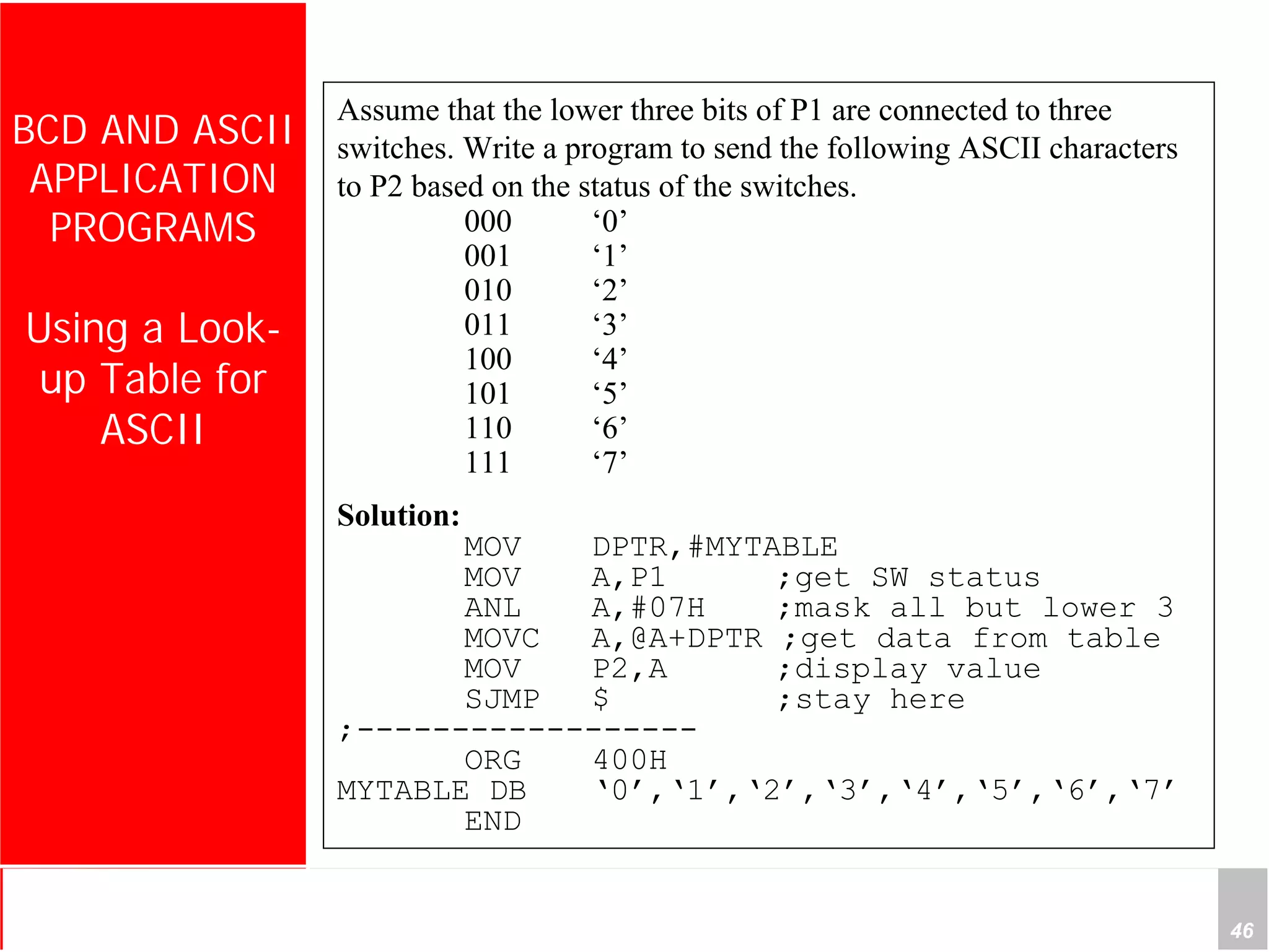
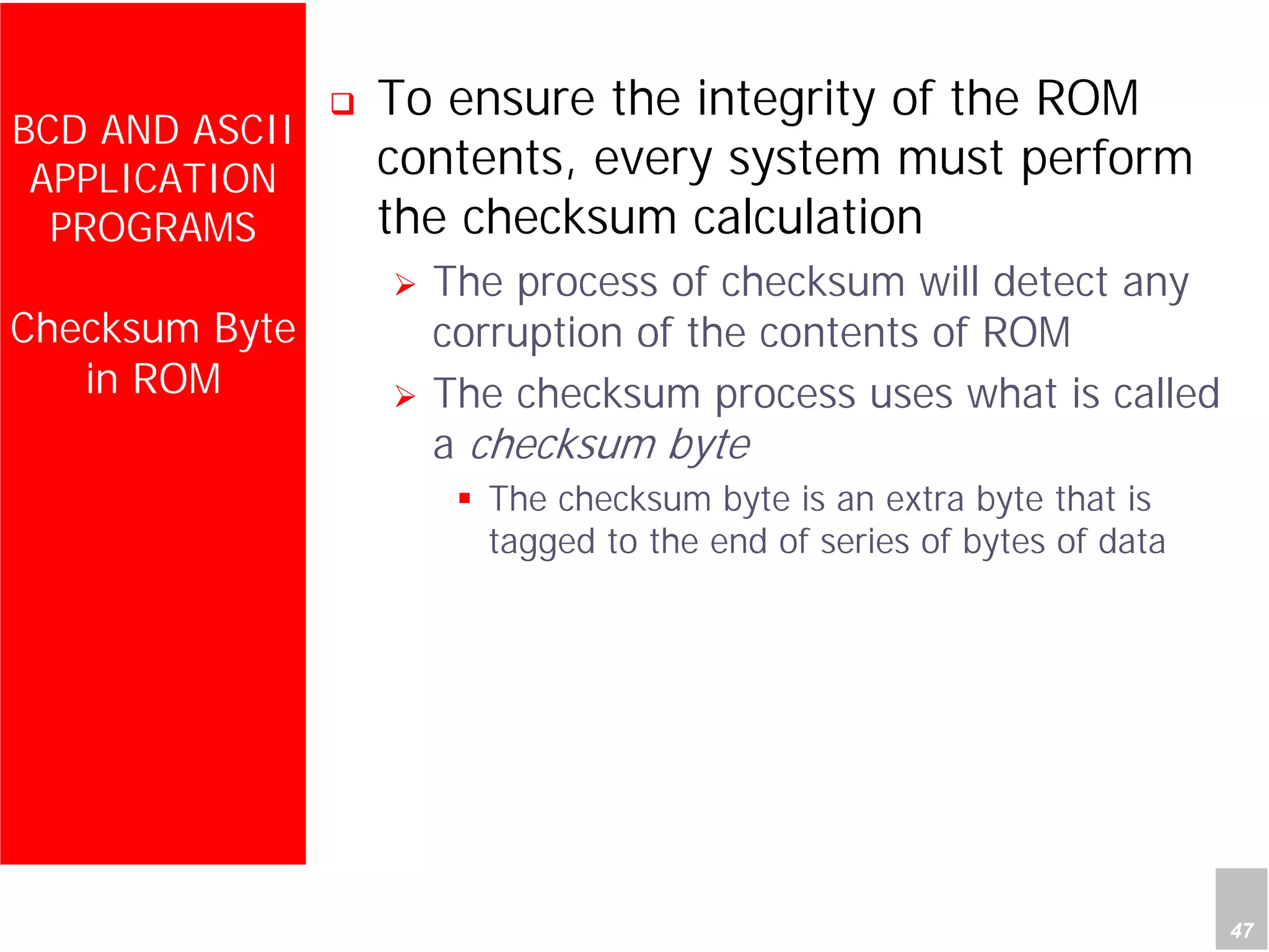
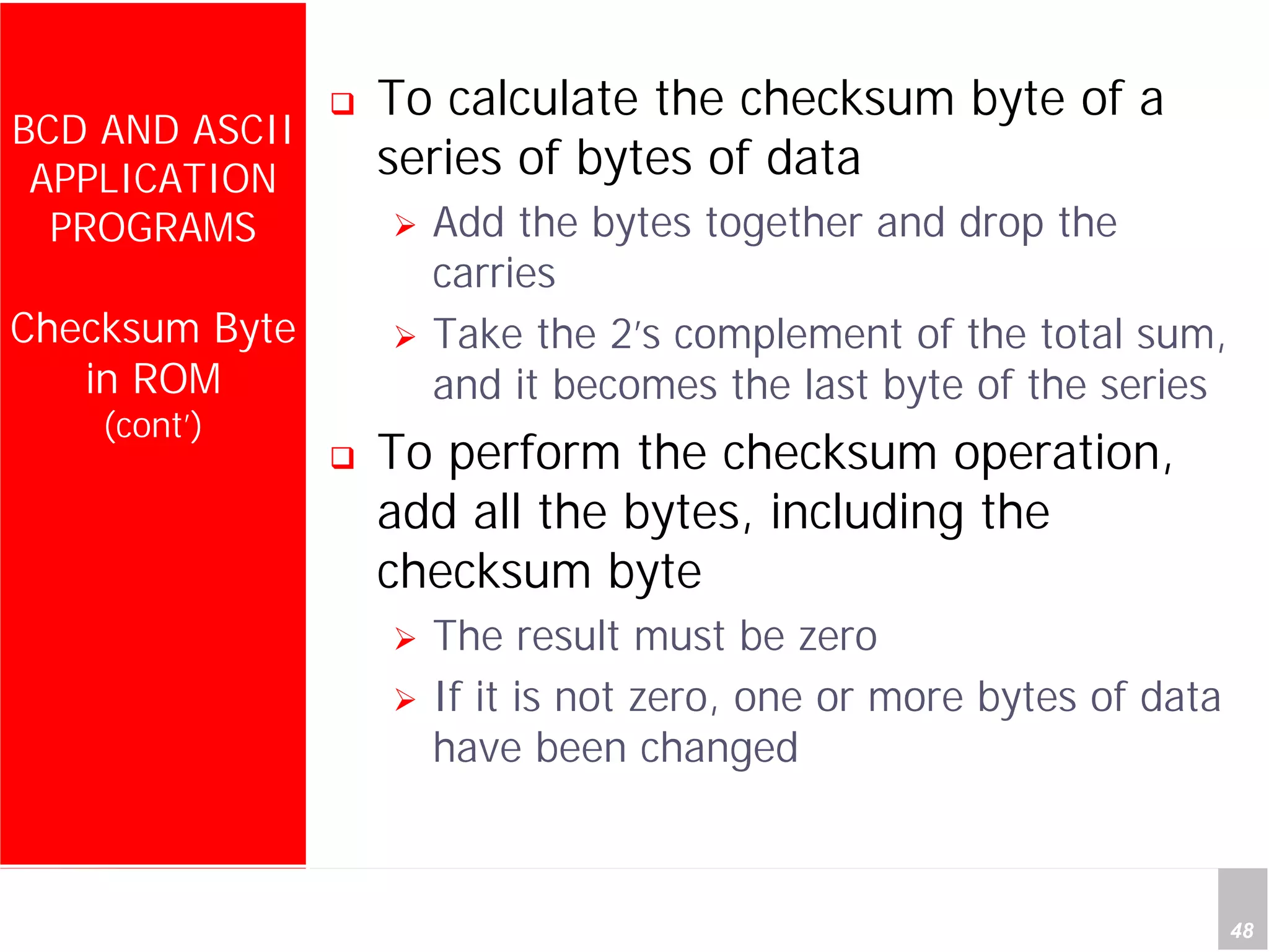
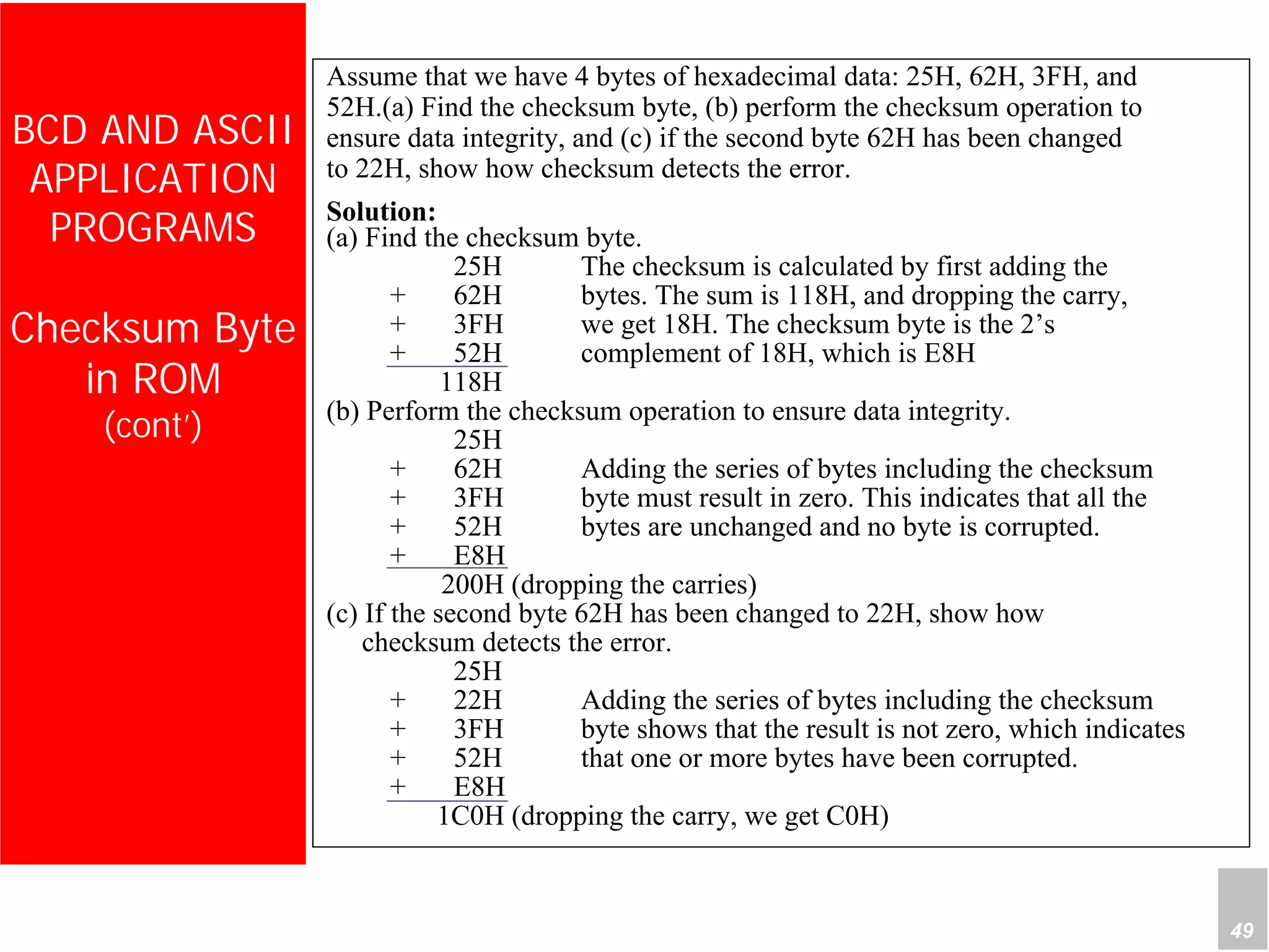
2) It provides examples of adding signed and unsigned numbers, as well as performing binary-coded decimal arithmetic. Special instructions like DA are used to handle carries for BCD.
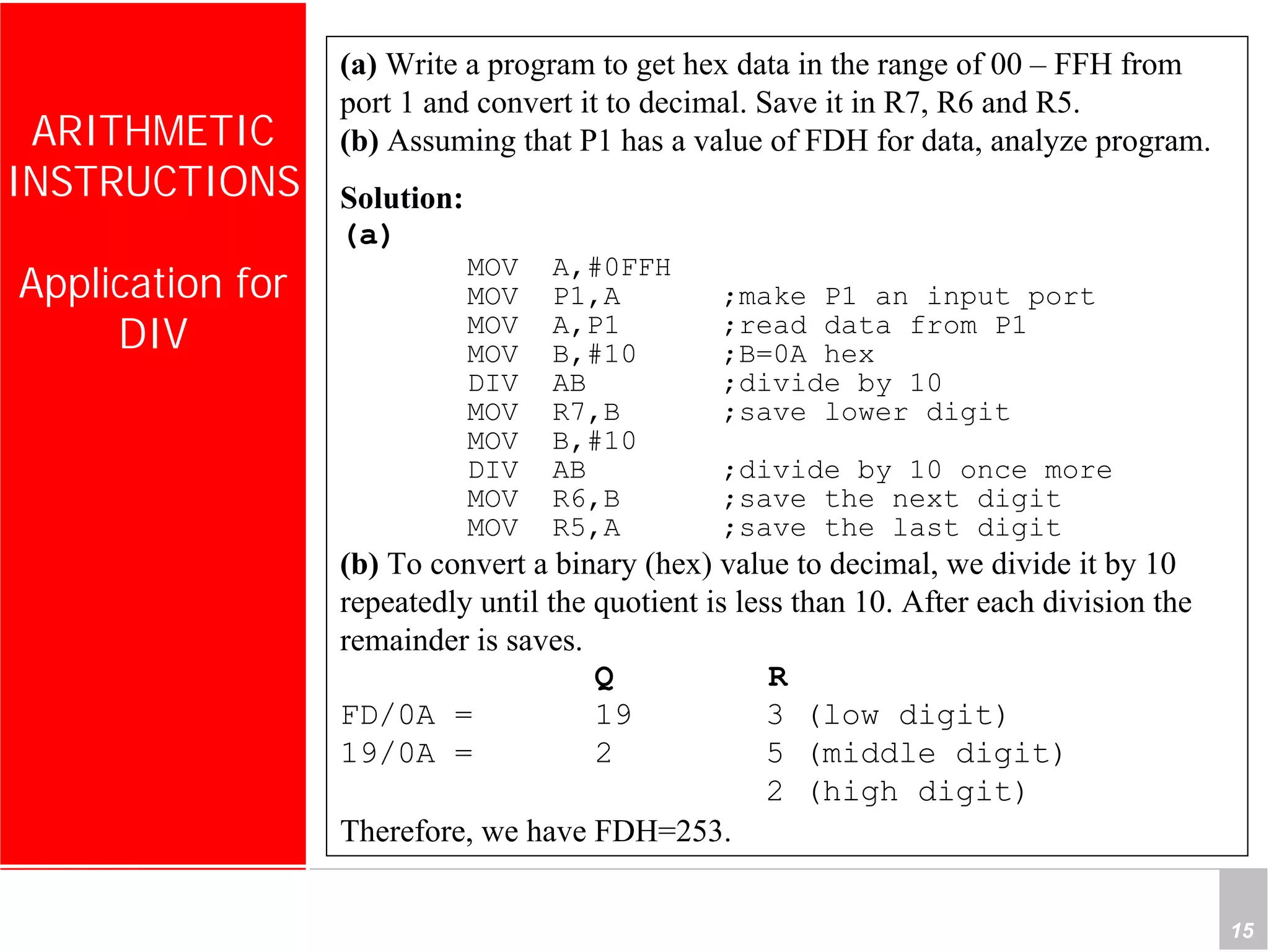
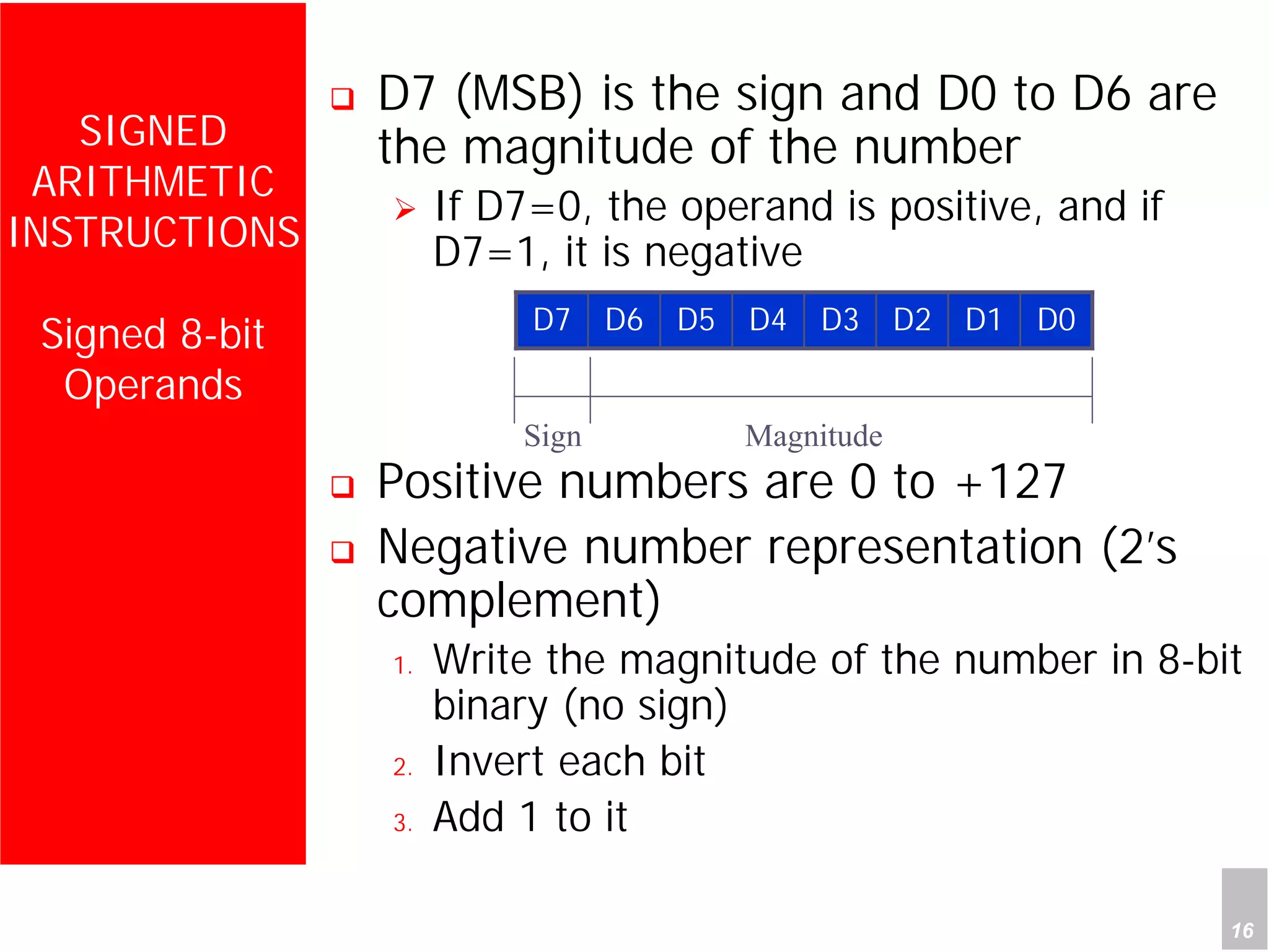
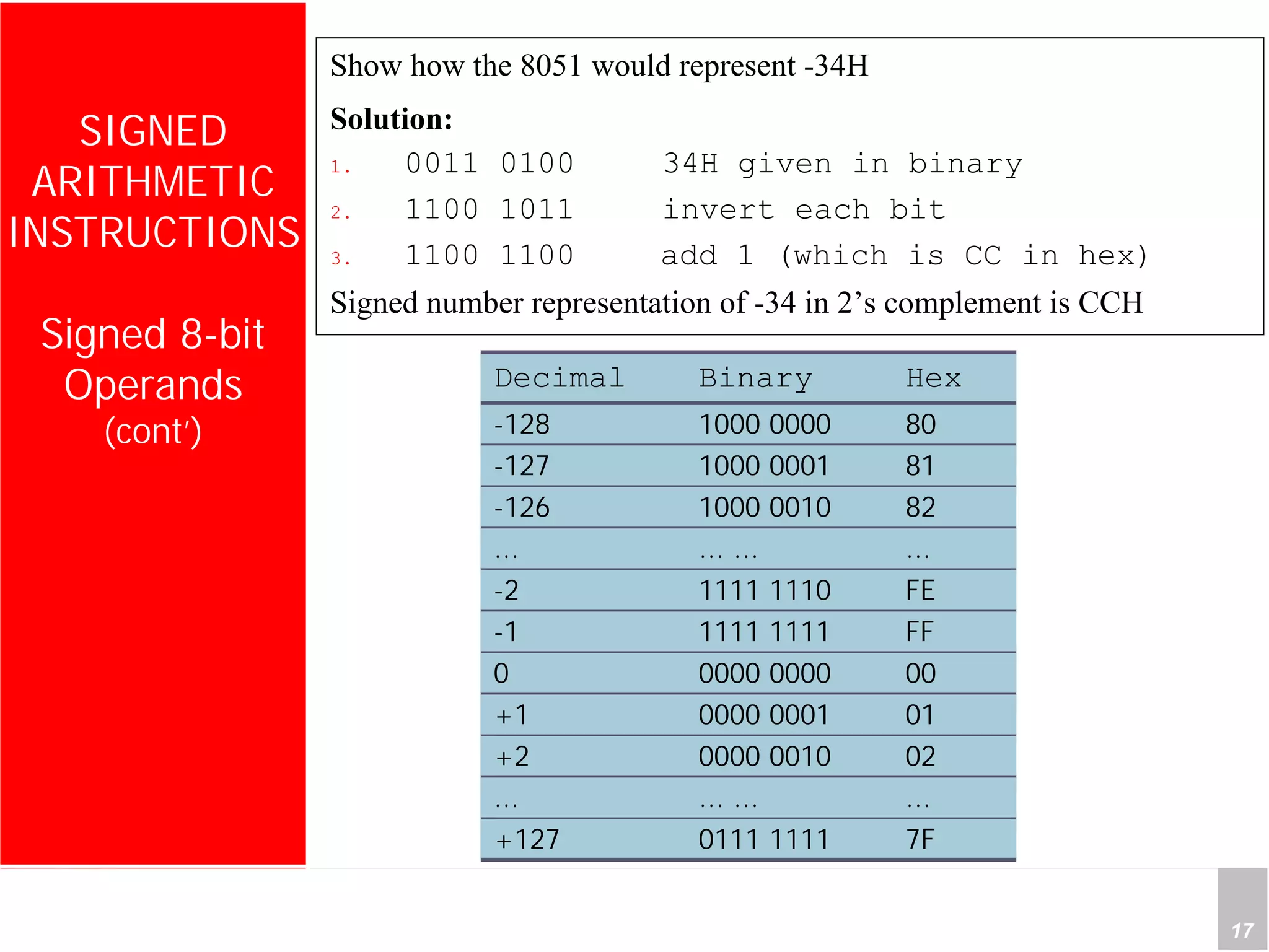
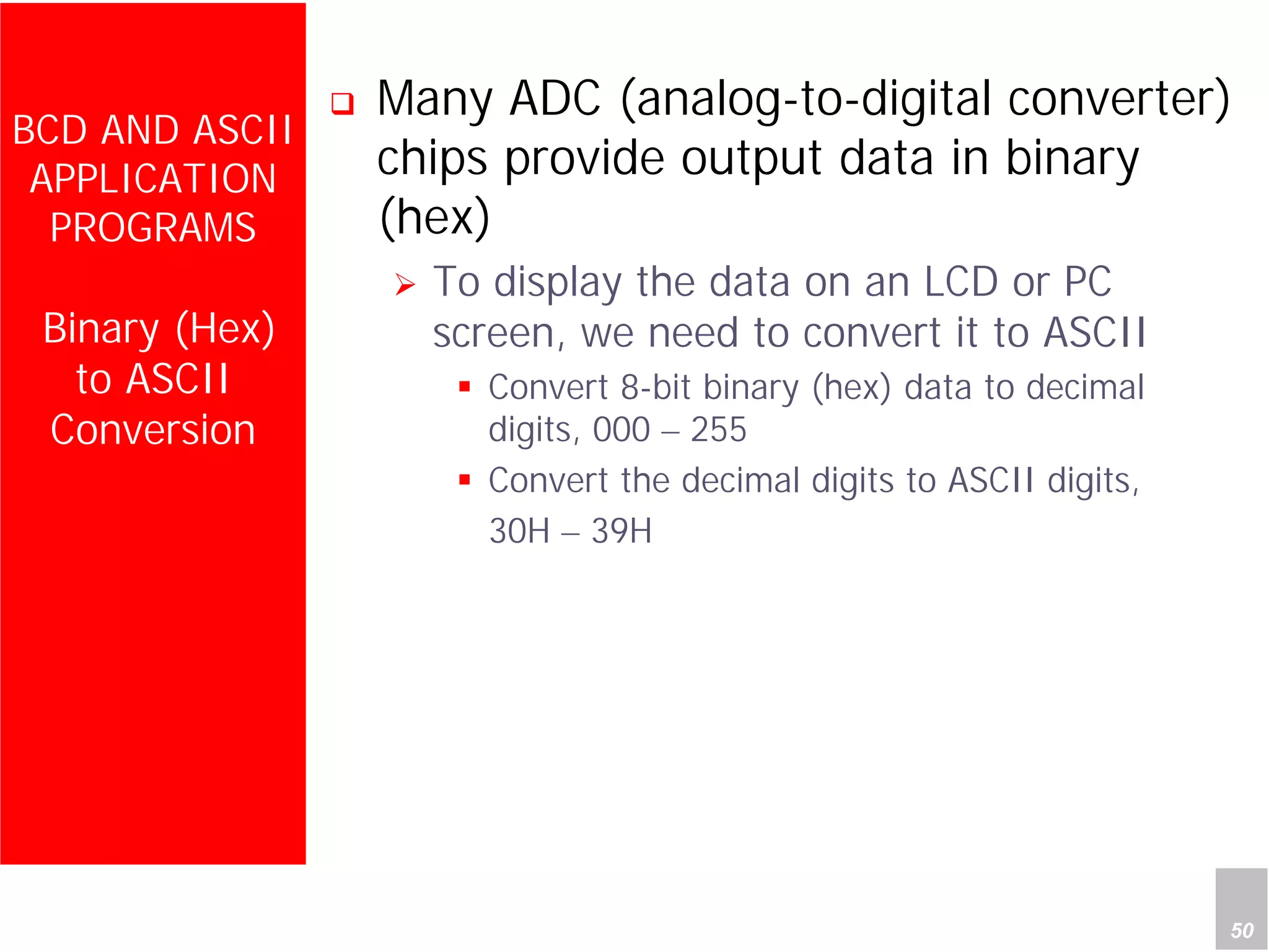
3) Applications described include converting hexadecimal values from an input port to decimal numbers by repeated division, and representing signed 8-bit two's complement numbers.