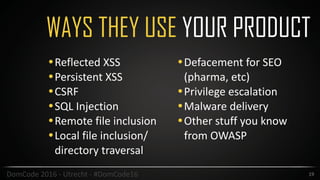
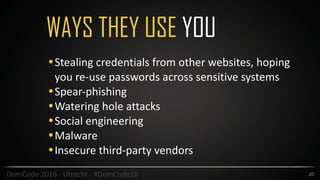
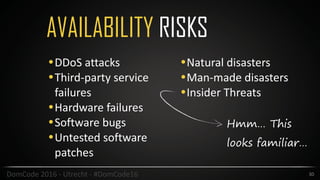
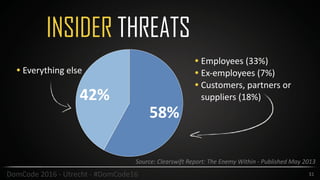
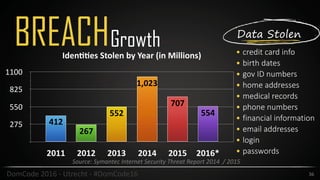
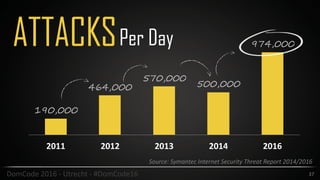
This document provides an overview of security best practices for startups and small businesses. It discusses the importance of security for protecting reputation, finances, and customer data. Key recommendations include implementing policies for least privilege, developing disaster recovery and incident response plans, enabling two-factor authentication, carefully managing third-party vendors, encrypting data, and conducting regular security testing. The document emphasizes that smaller companies can also be targets and should not assume they are immune from attacks.