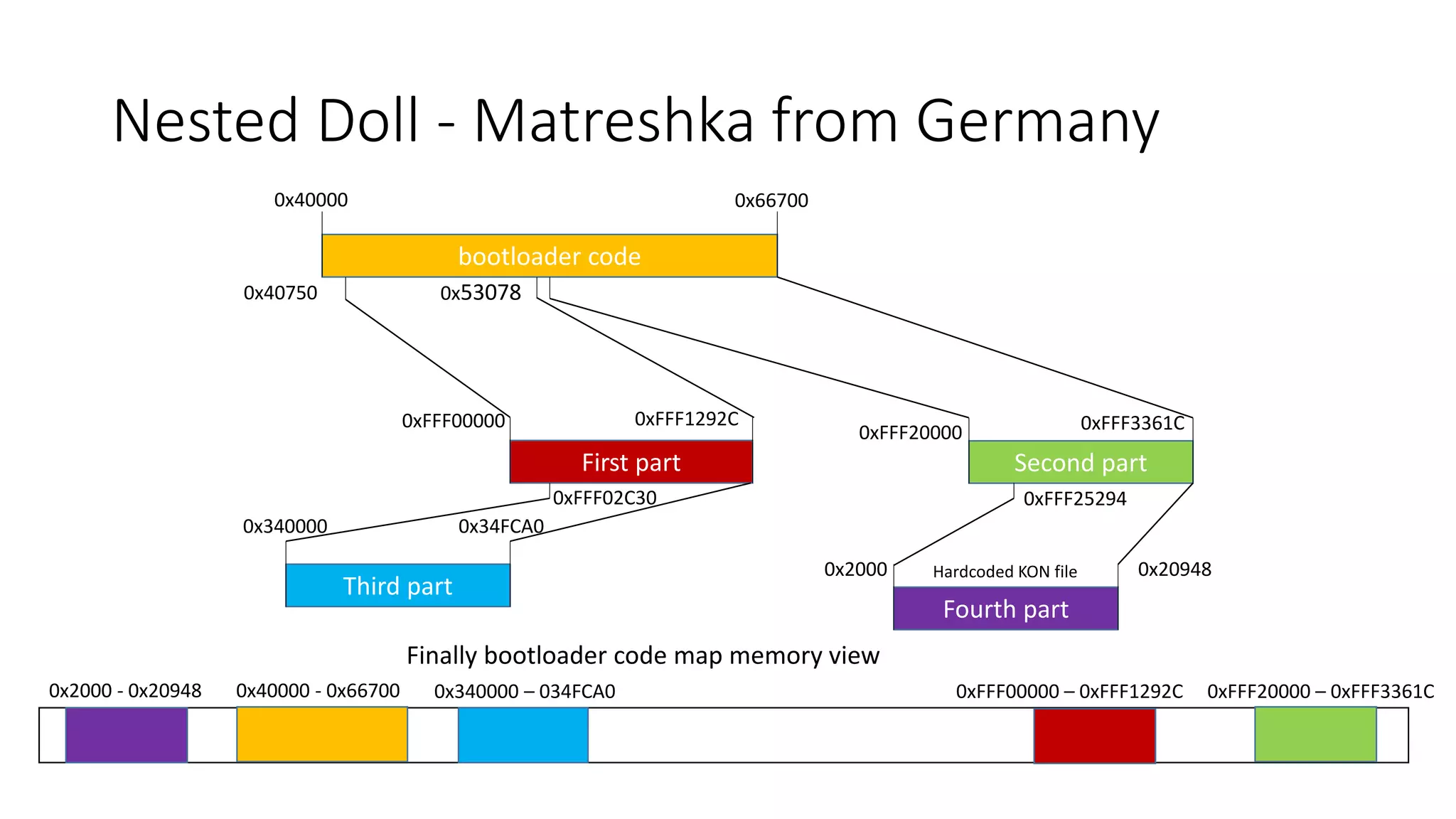
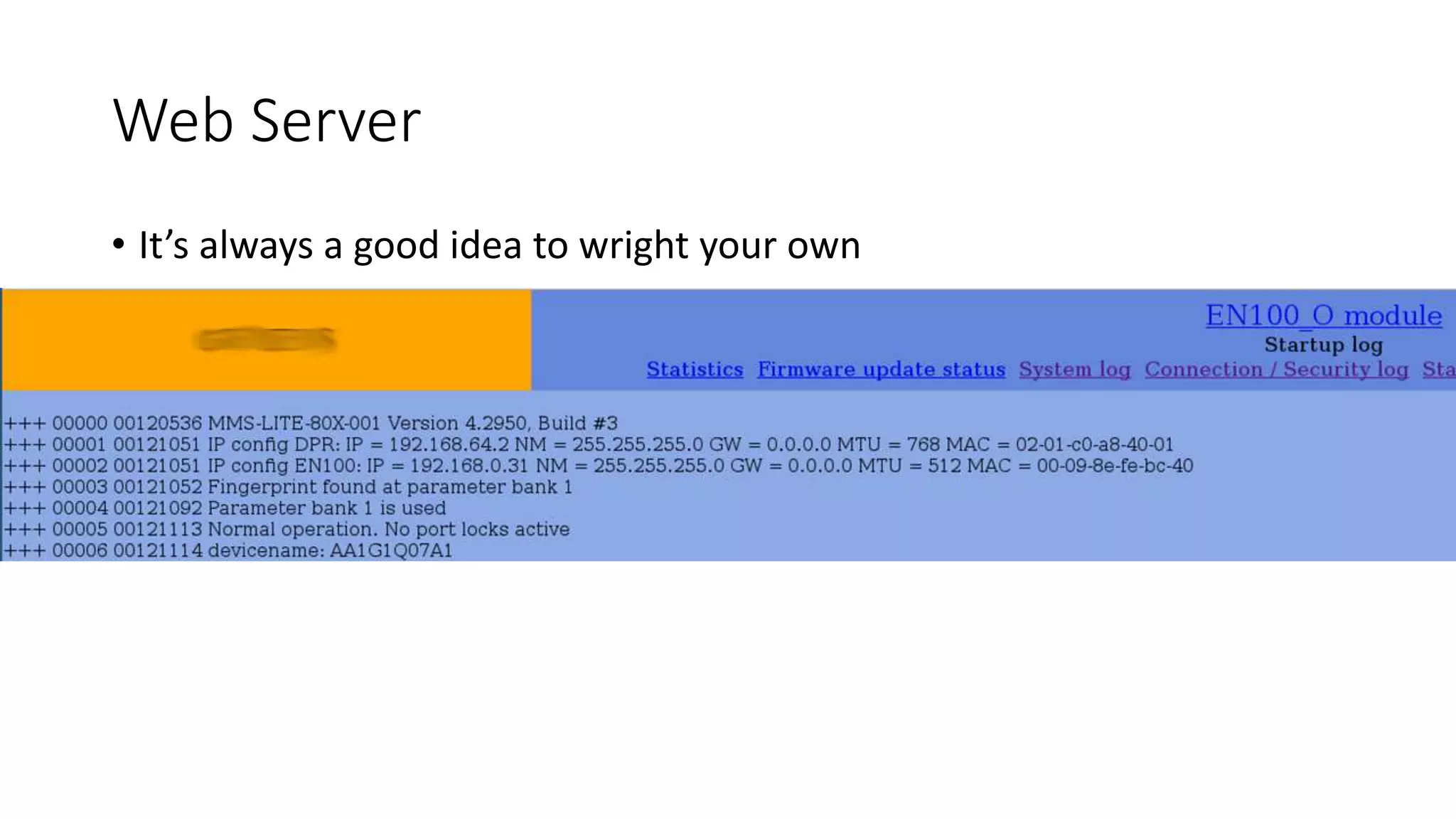
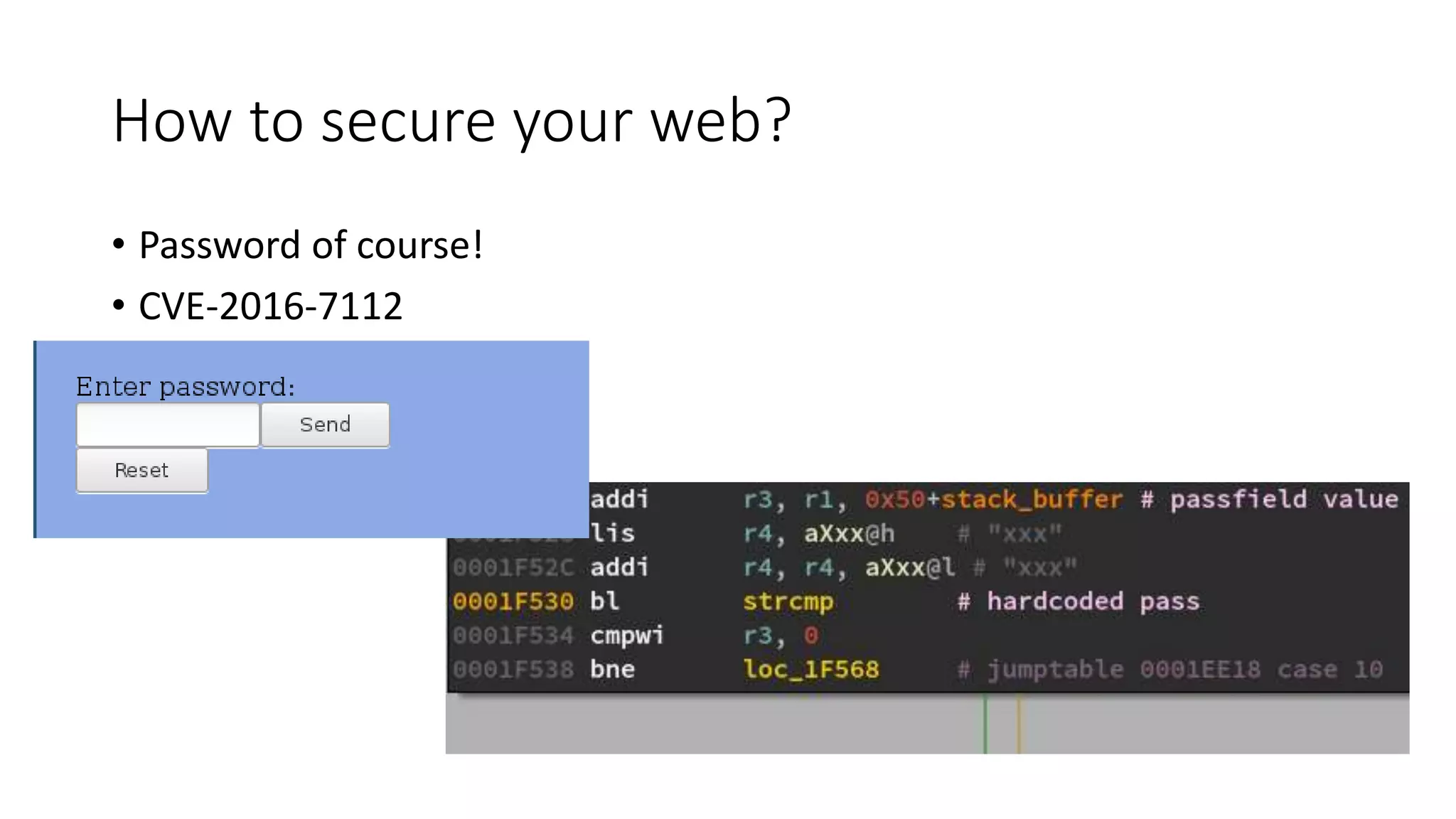
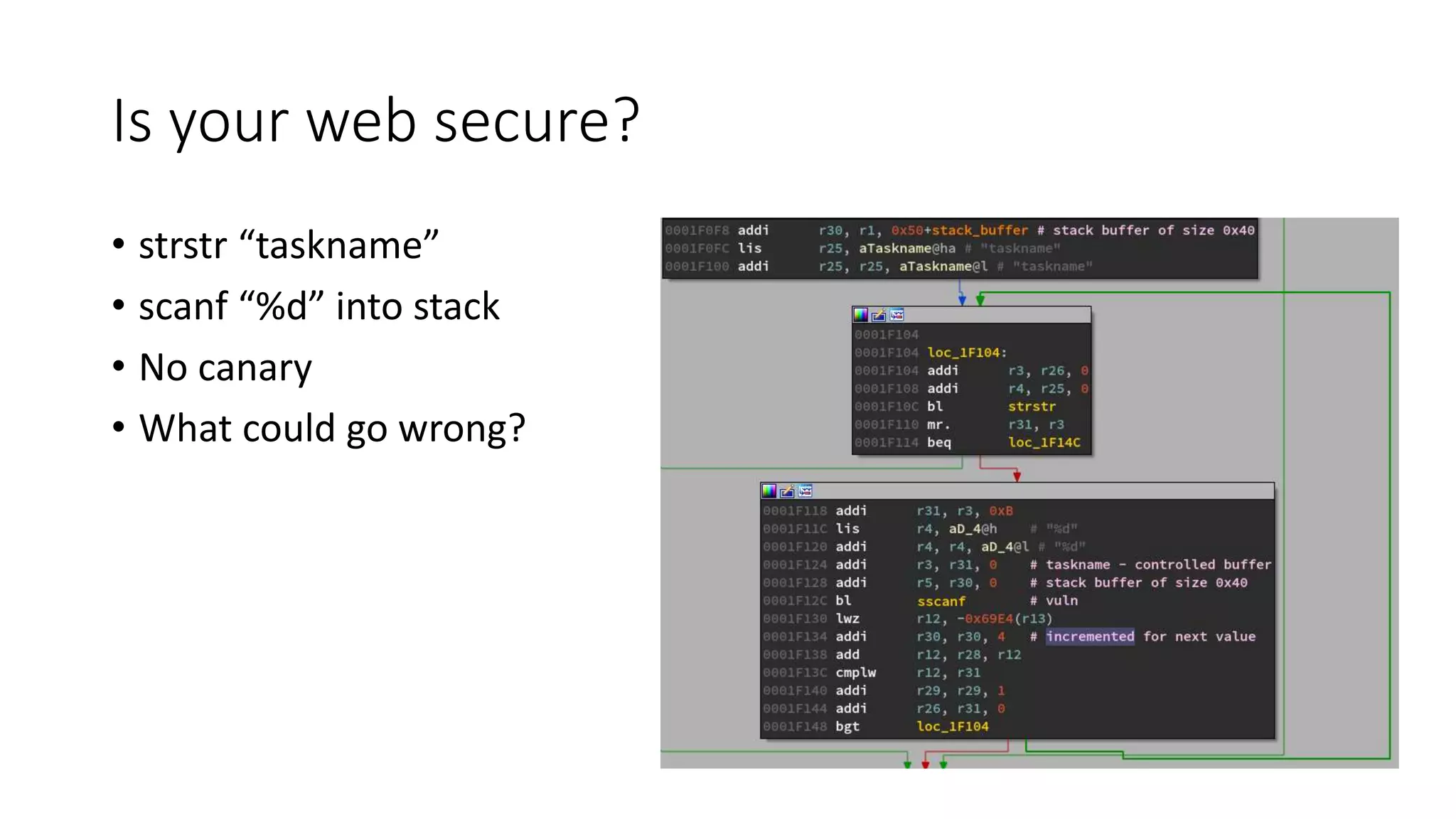
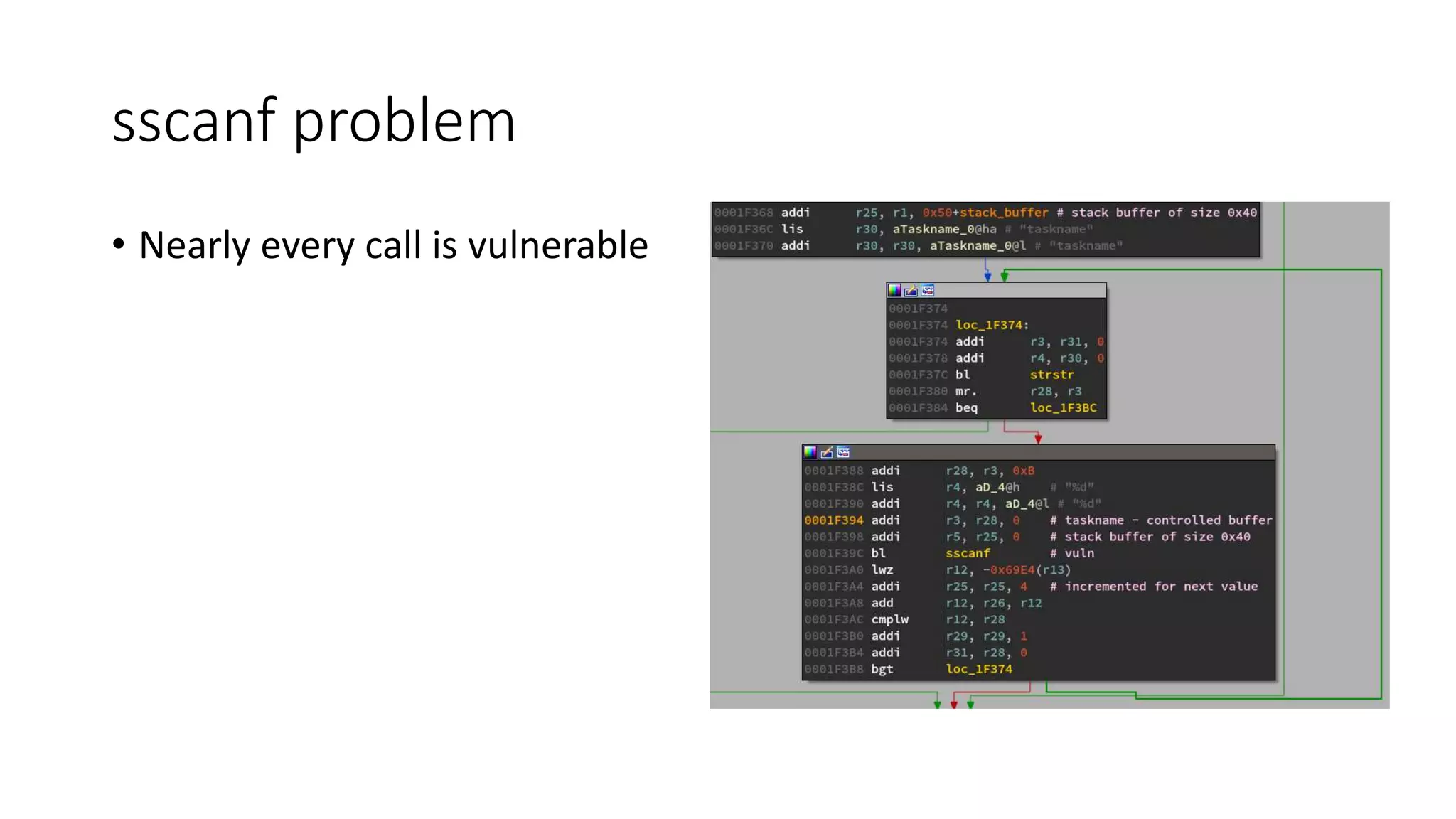
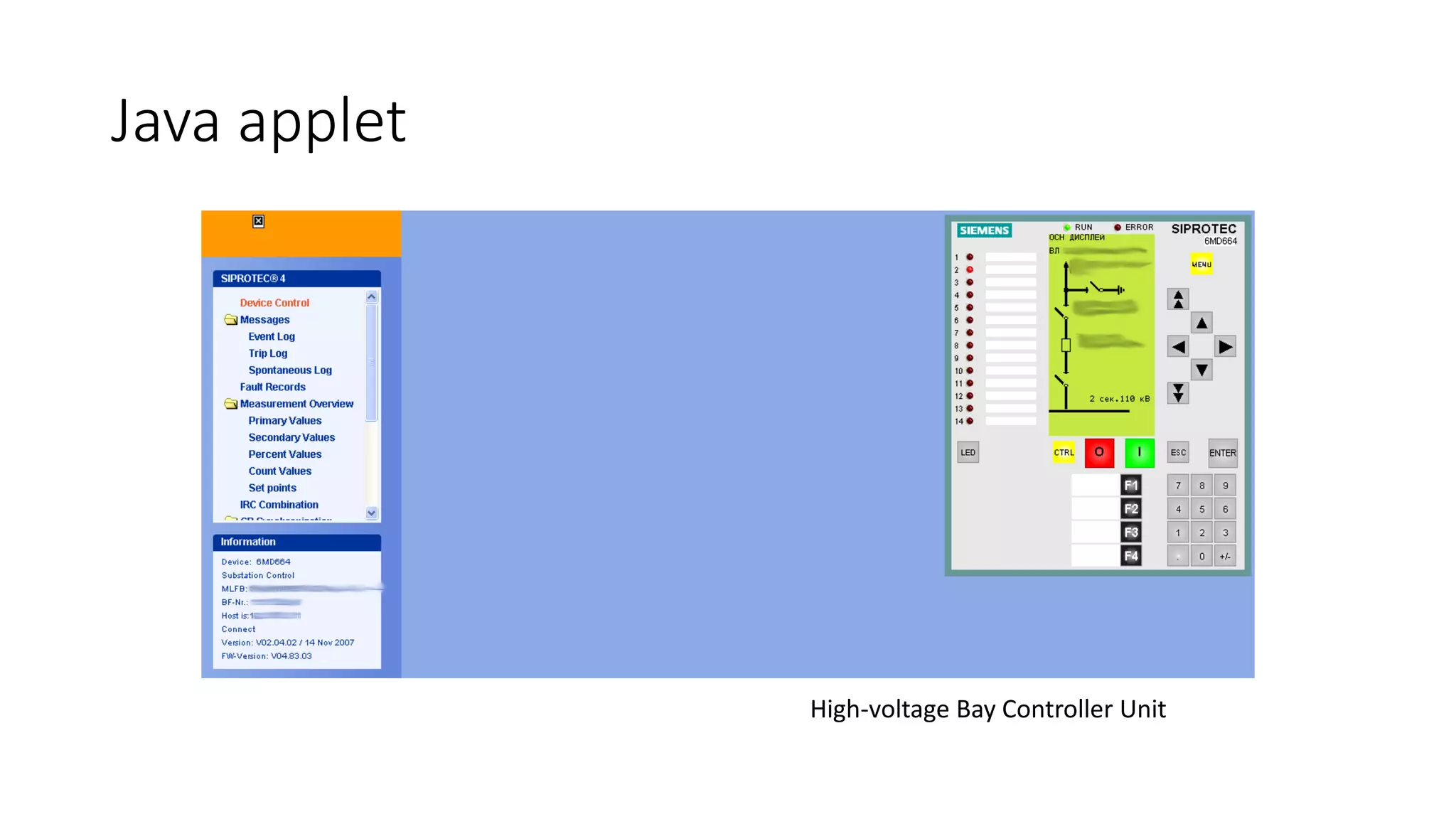
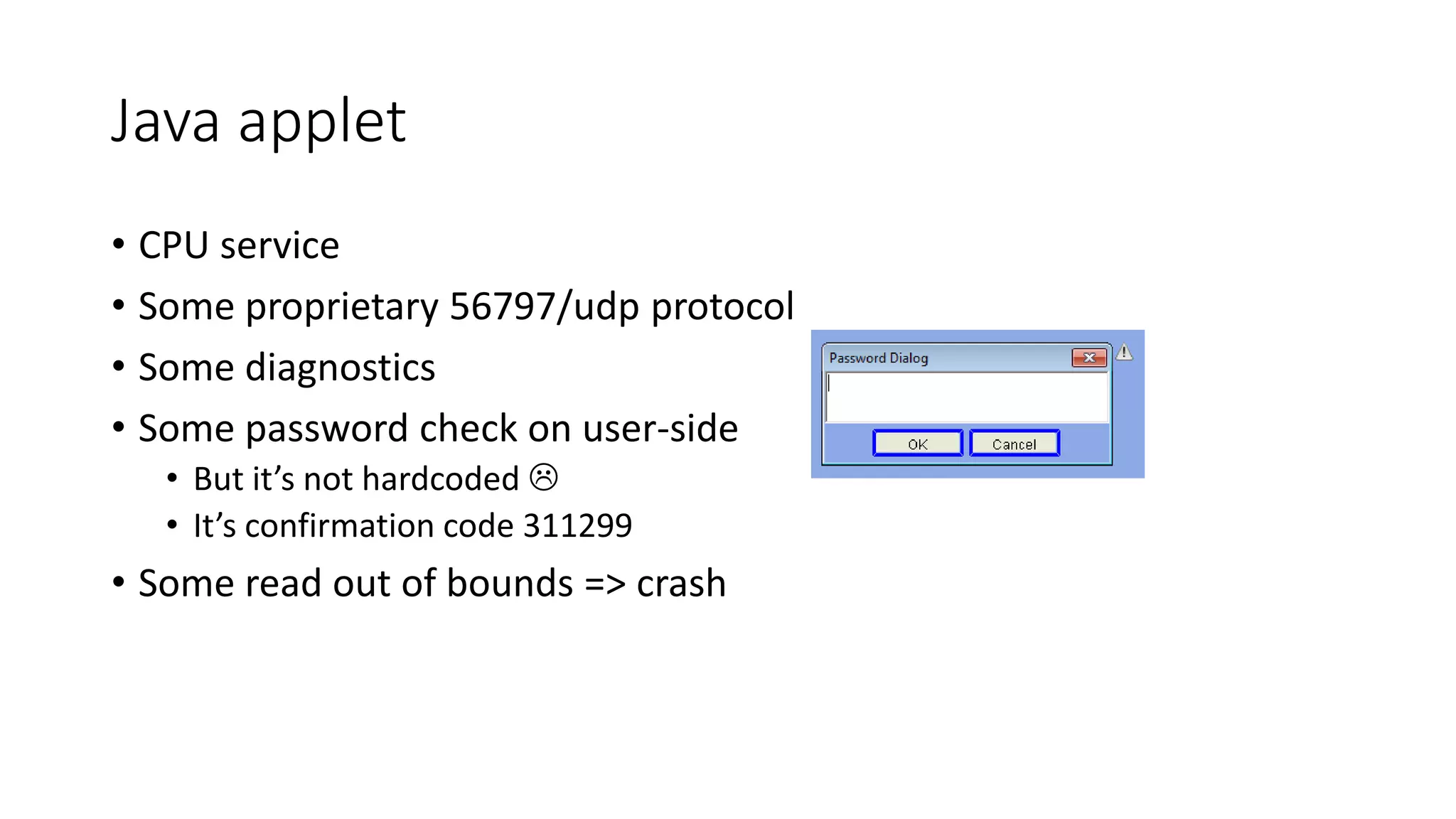
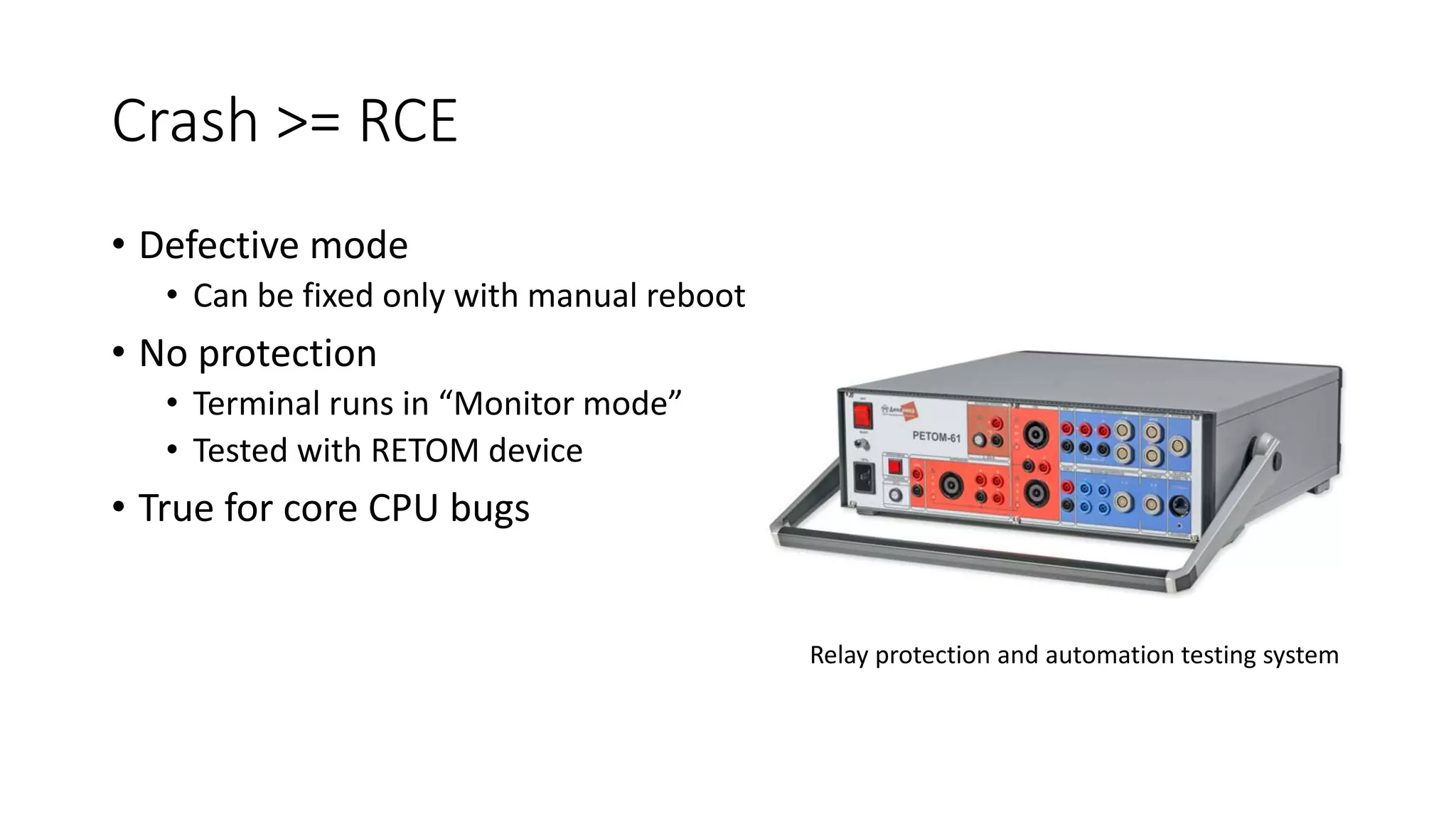
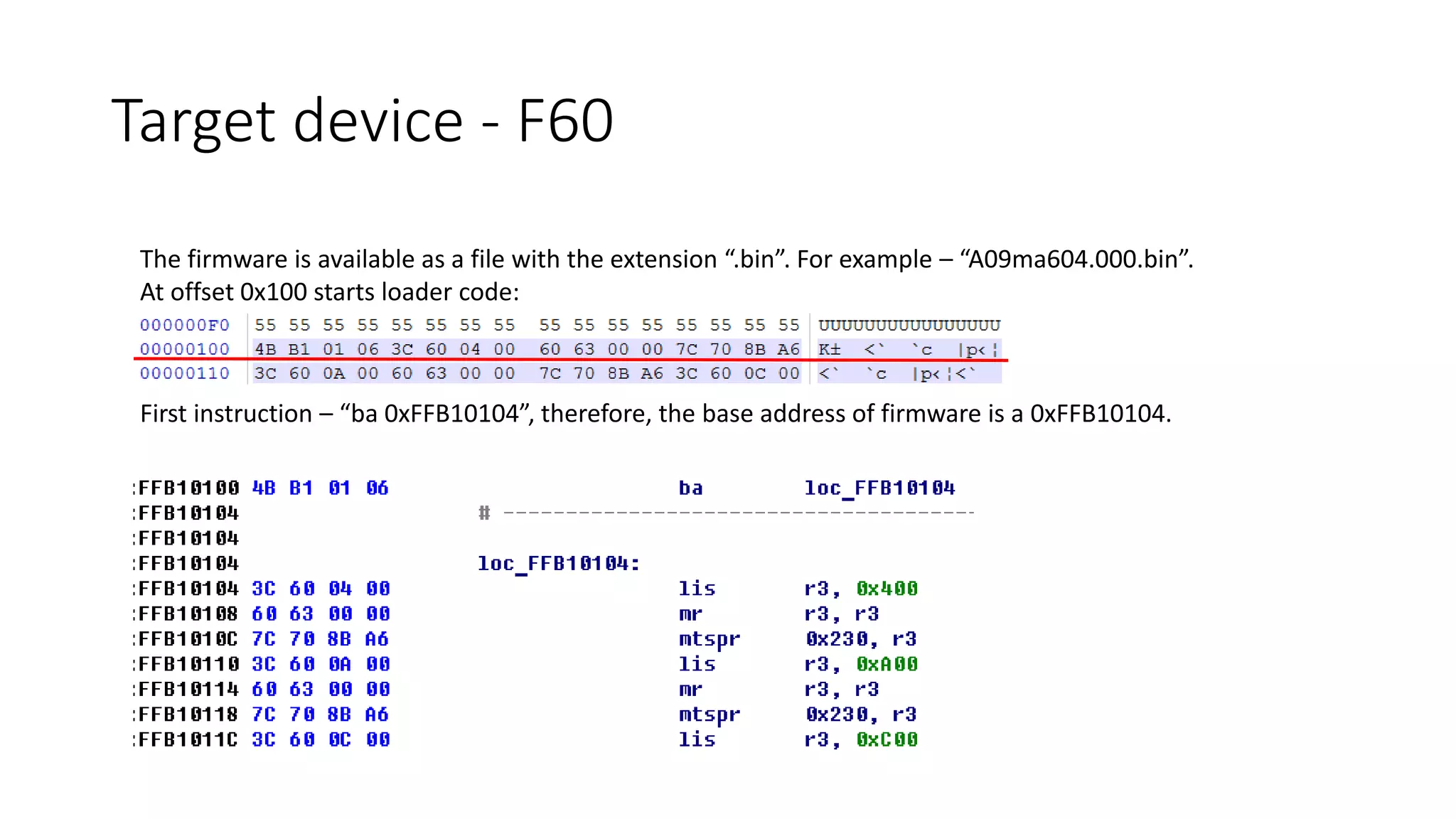
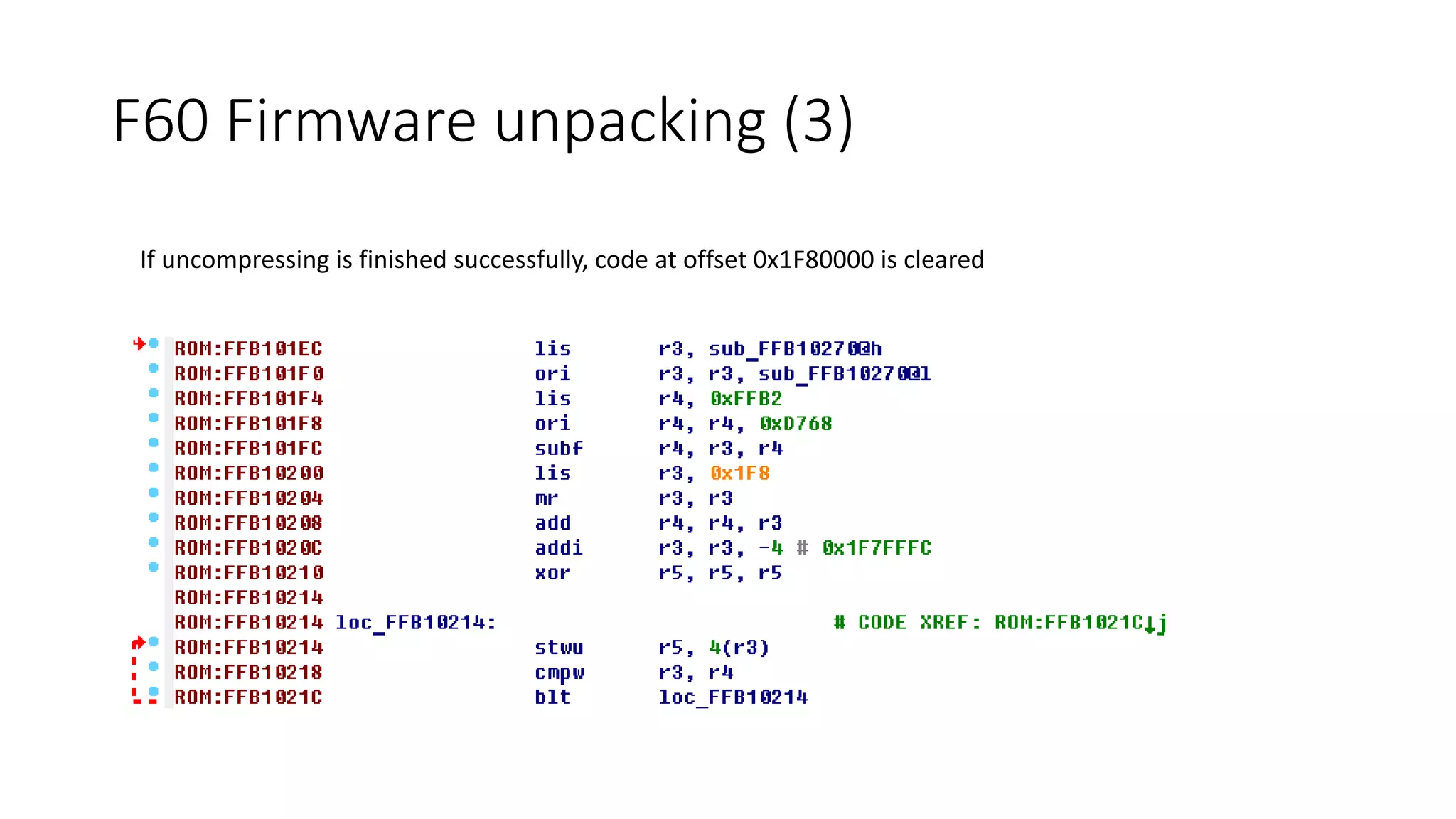
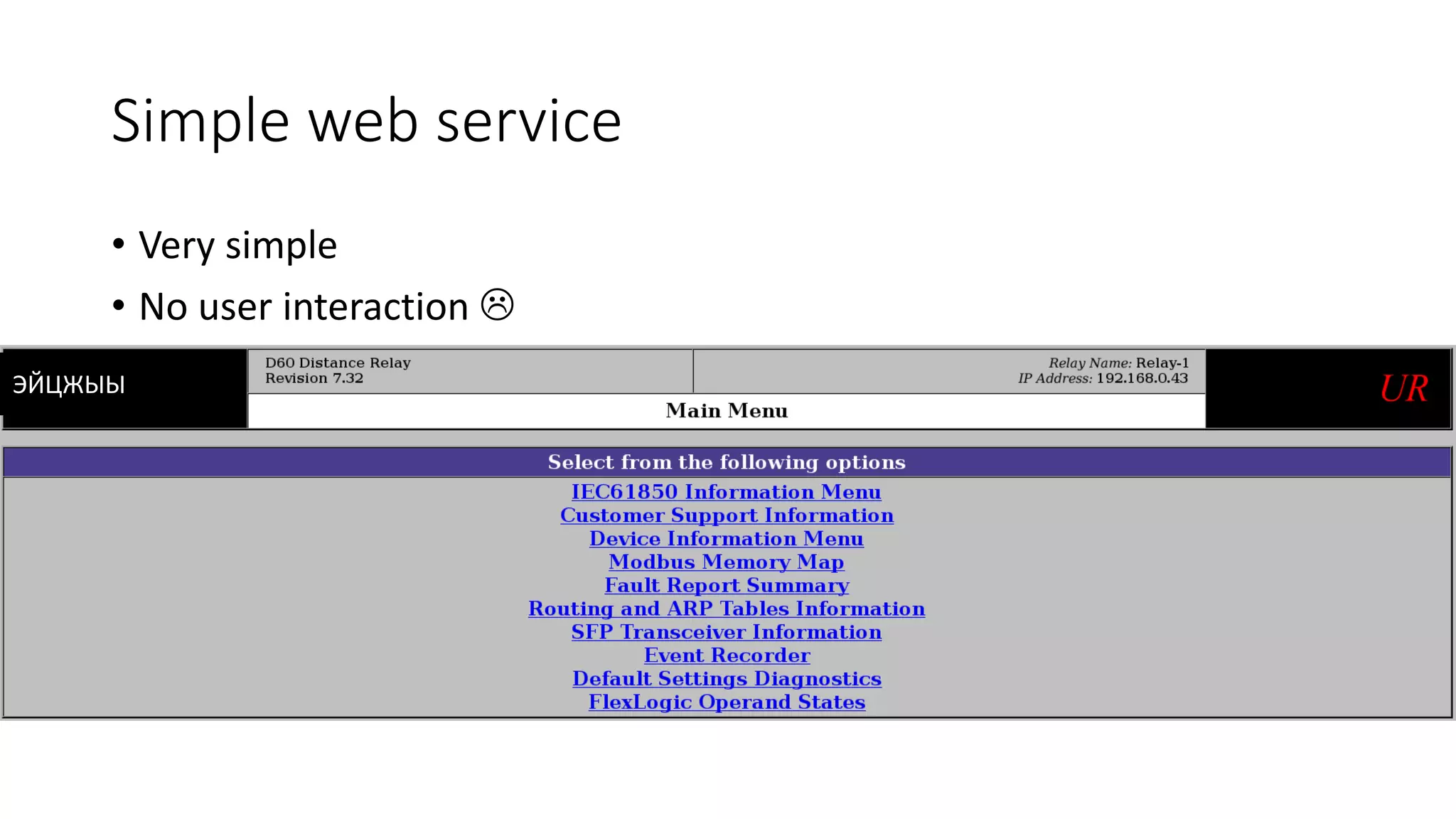
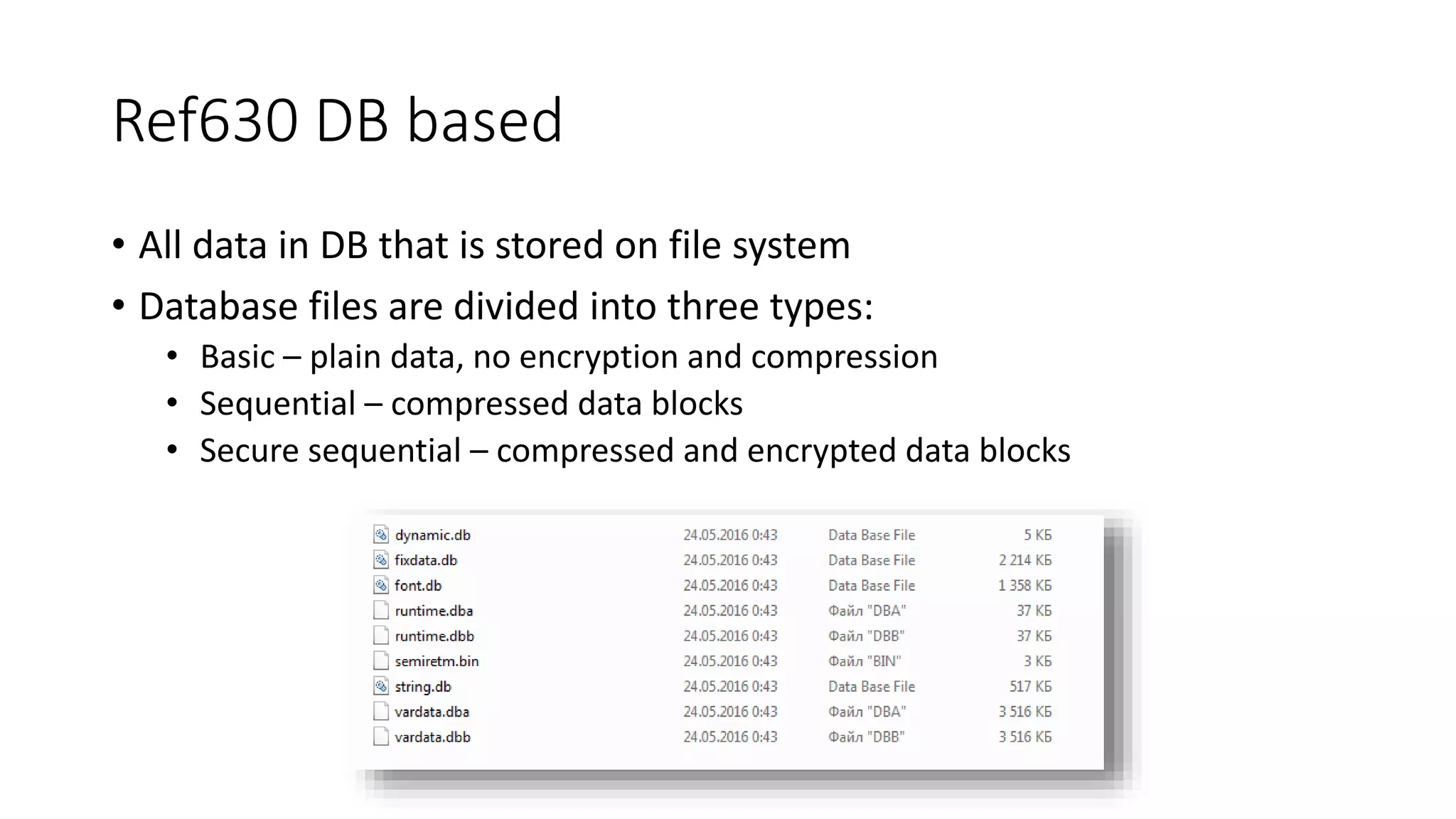
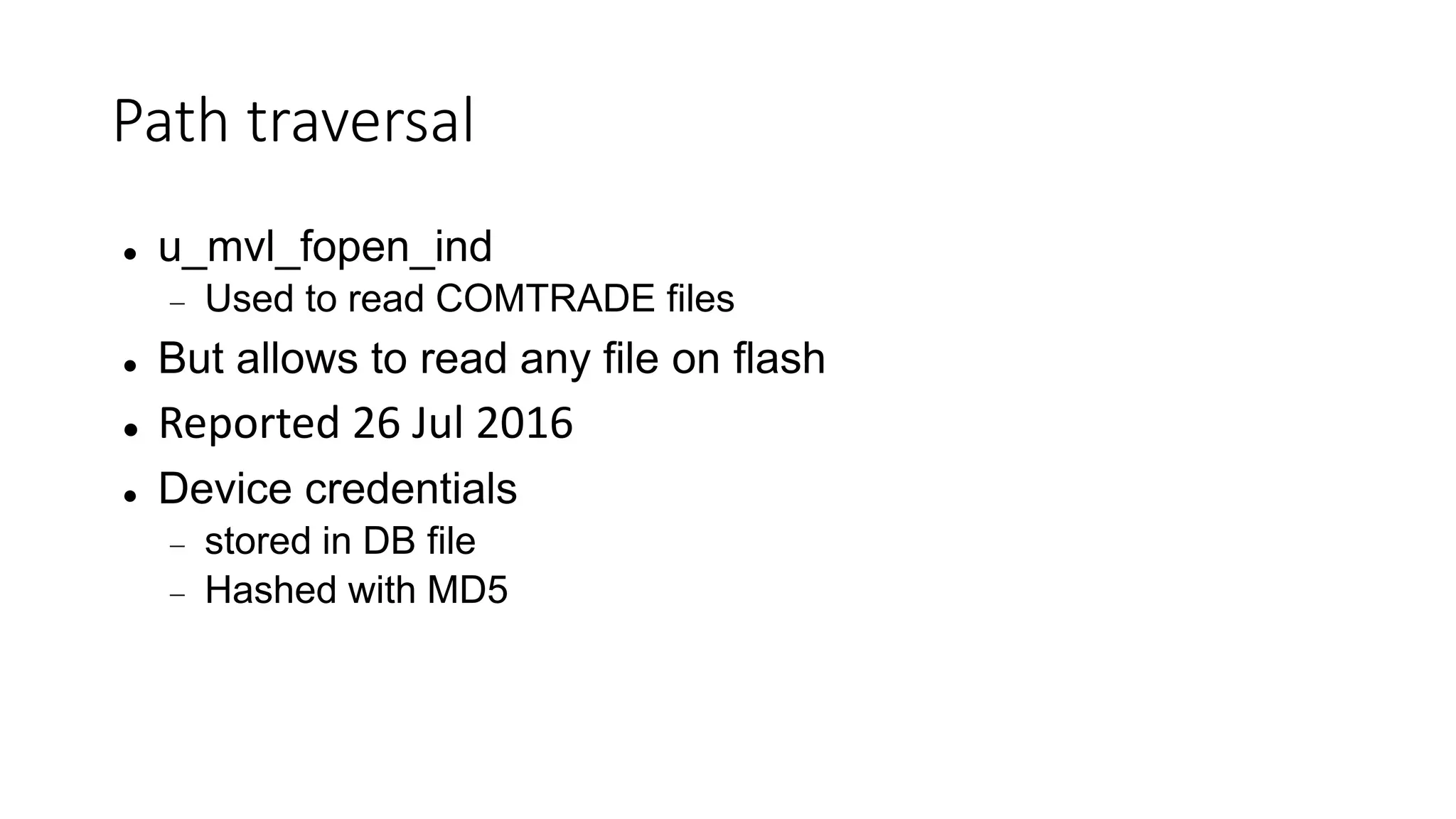
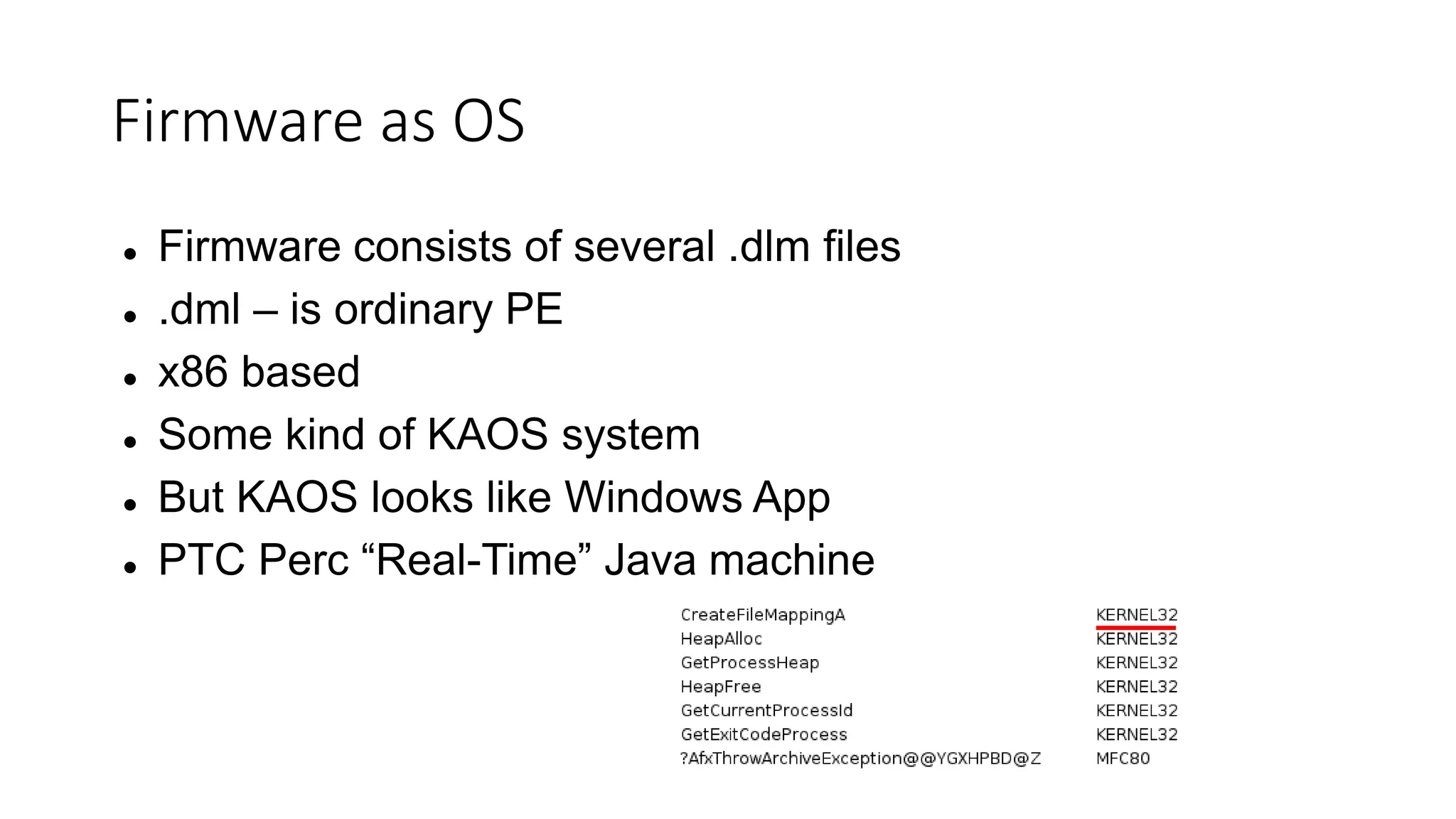
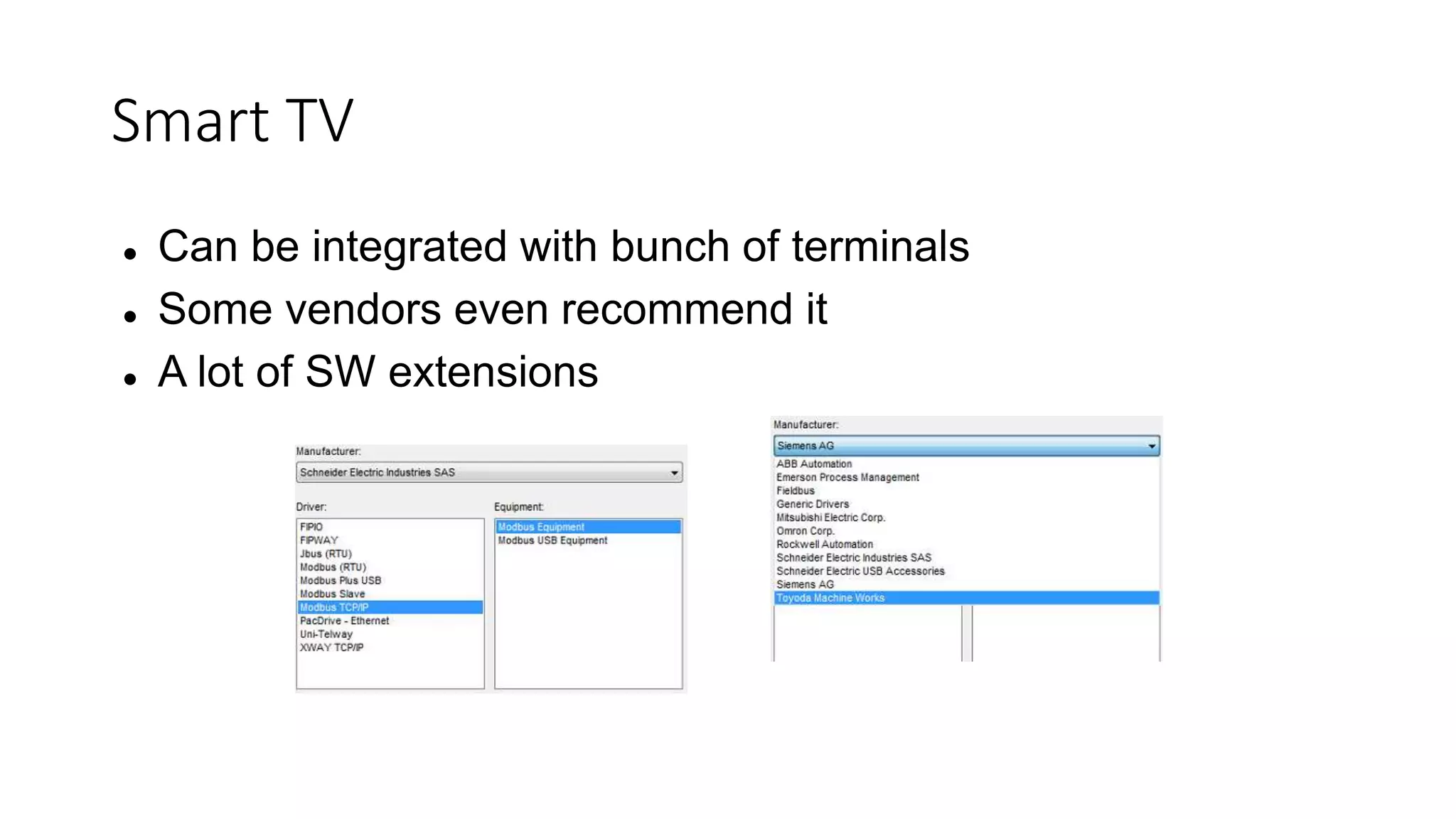
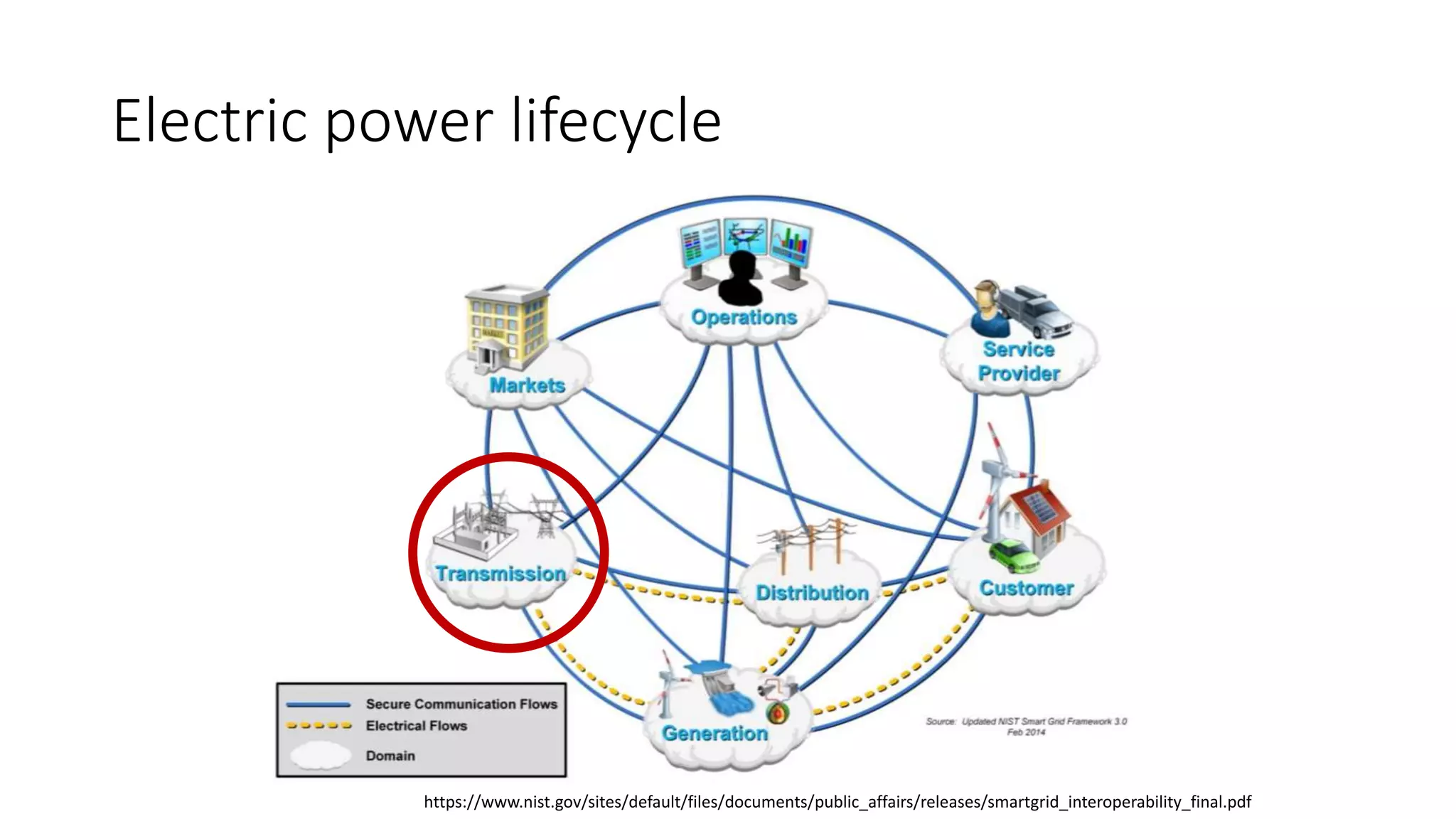
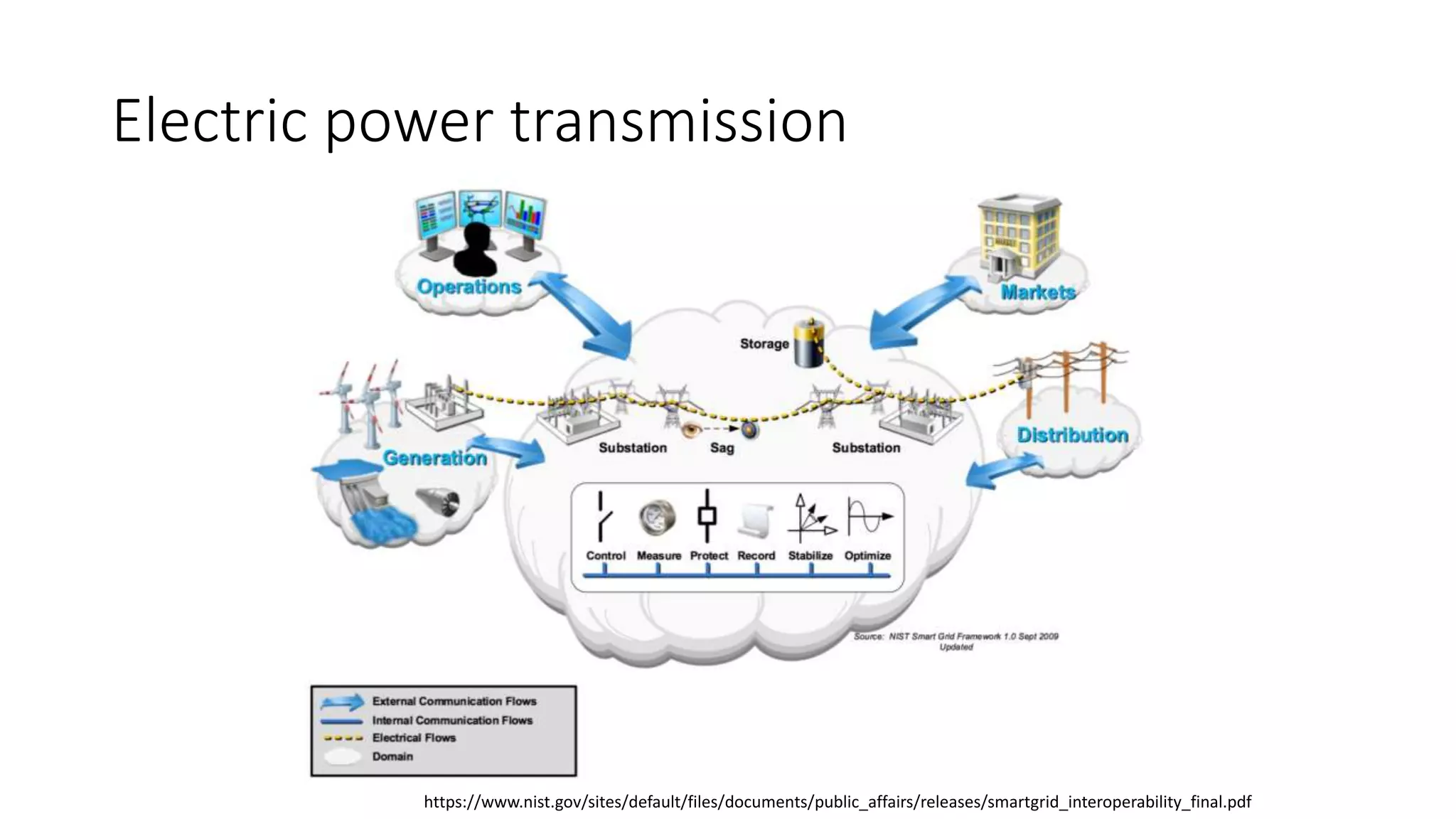
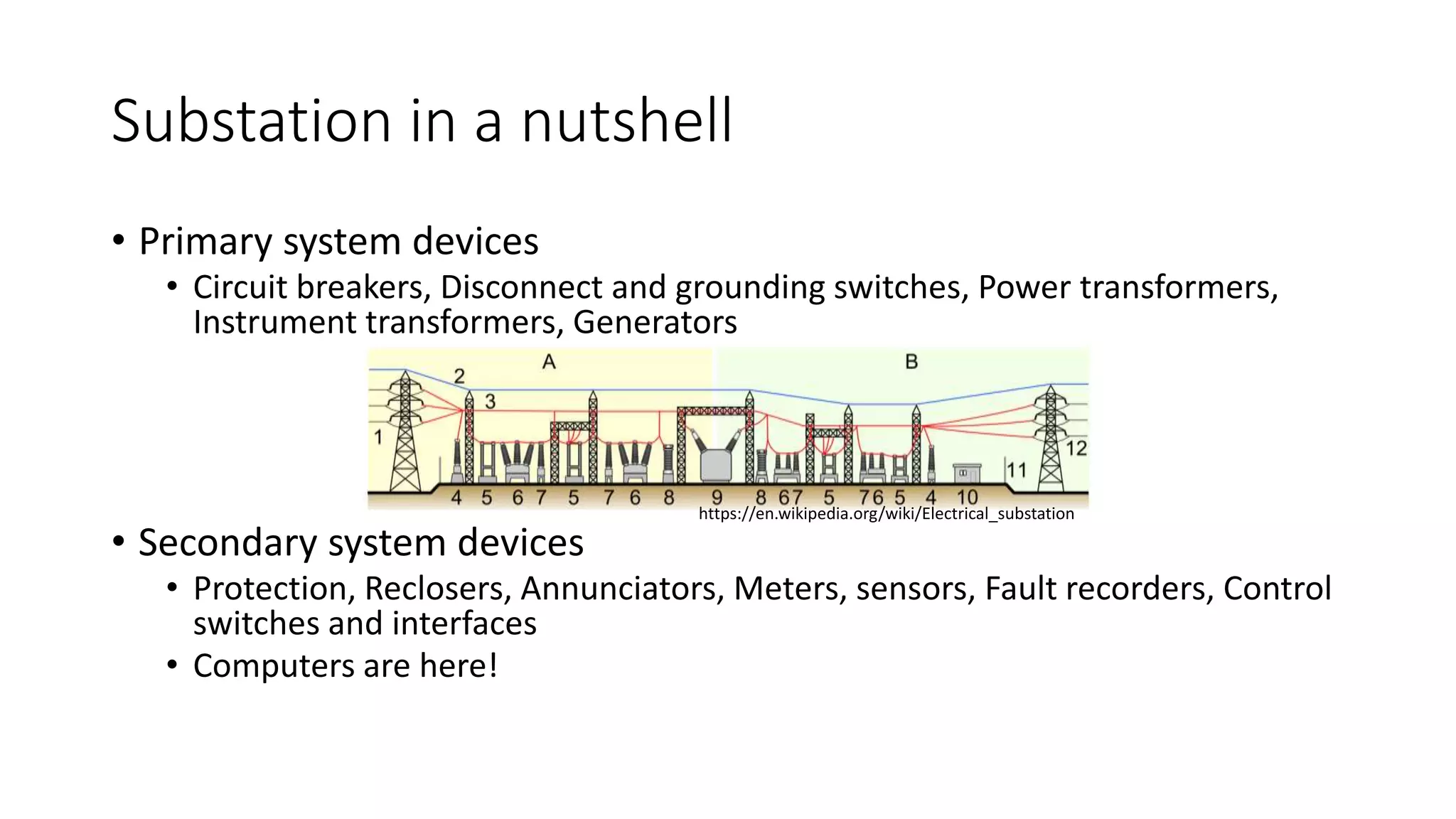
The document discusses the complexities and vulnerabilities associated with relay protection and automation systems in substations, including various devices and protocols used in their operation. It highlights security concerns, particularly focusing on the IEC 61850 protocol, and outlines potential cyber-attacks on substation infrastructure. Additionally, it mentions the importance of firmware updates and the challenges faced in securing these systems against various vulnerabilities.








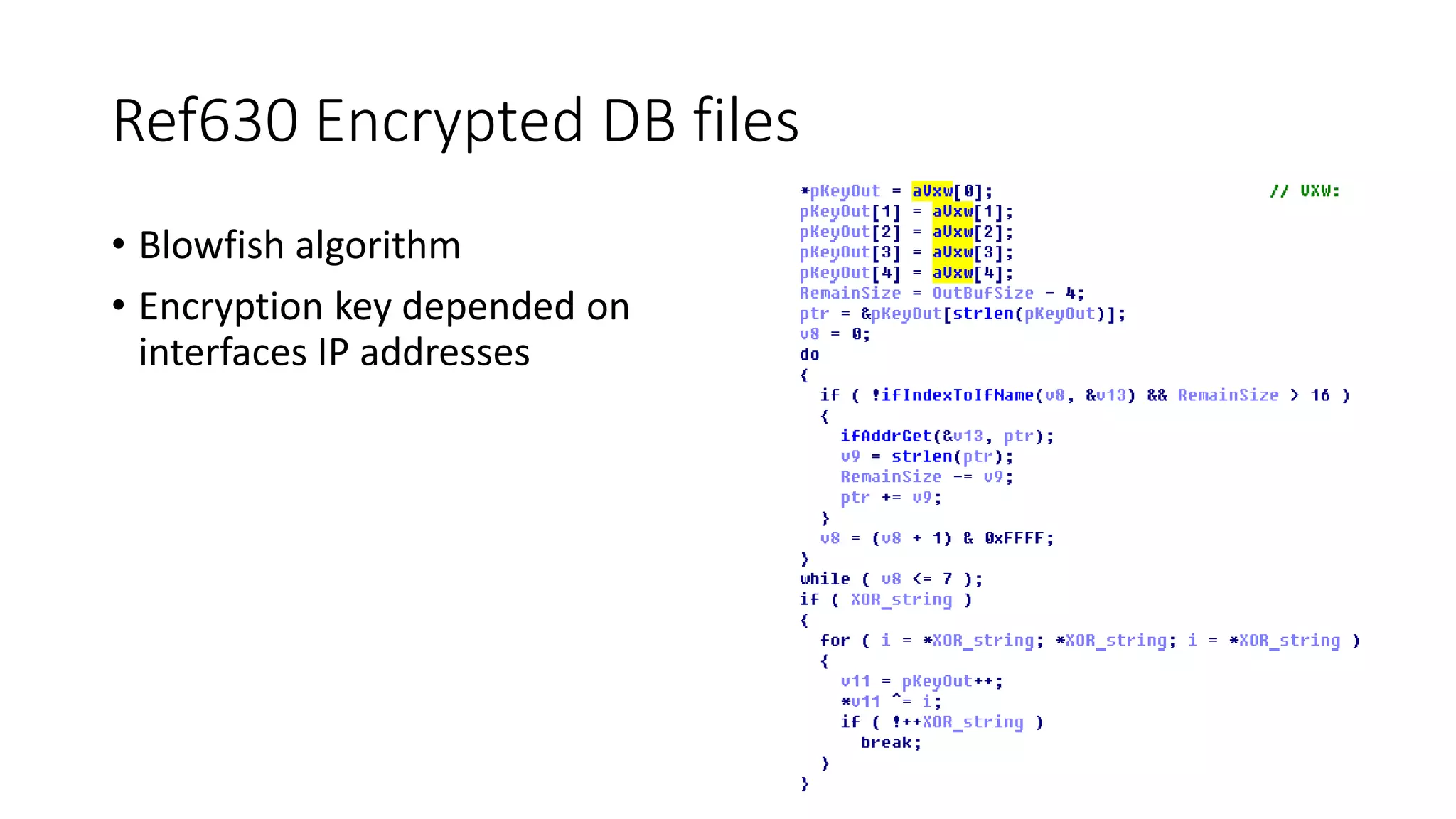
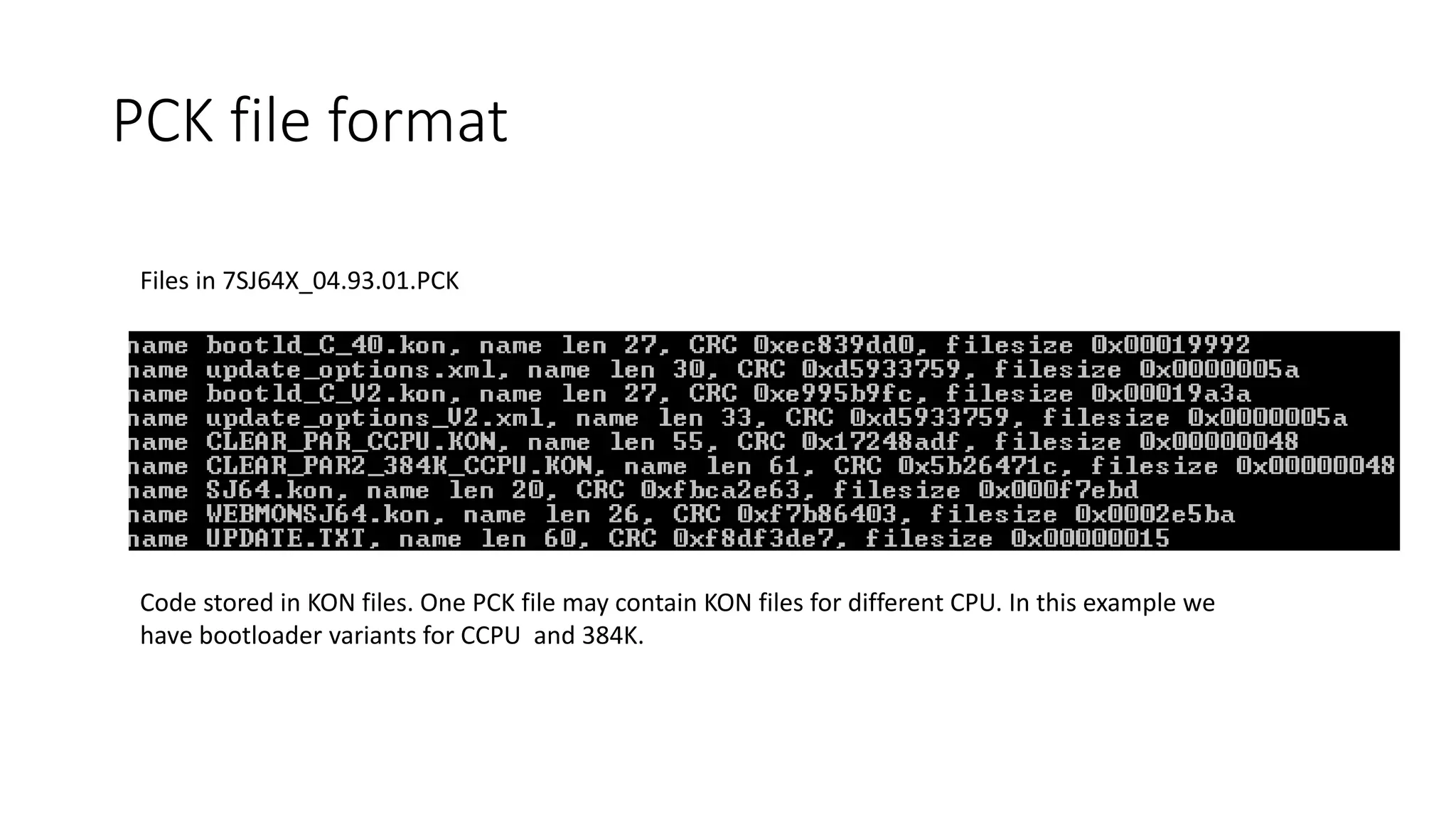
![Contains records with file description
struct PCK_file_record
{
char Name[252];
DWORD CRC;
DWORD Size;
}
PCK file format](https://image.slidesharecdn.com/hopelessrelayprotectionforsubstationautomationfin-171015042634/75/Recon-Hopeless-relay-protection-for-substation-automation-14-2048.jpg)
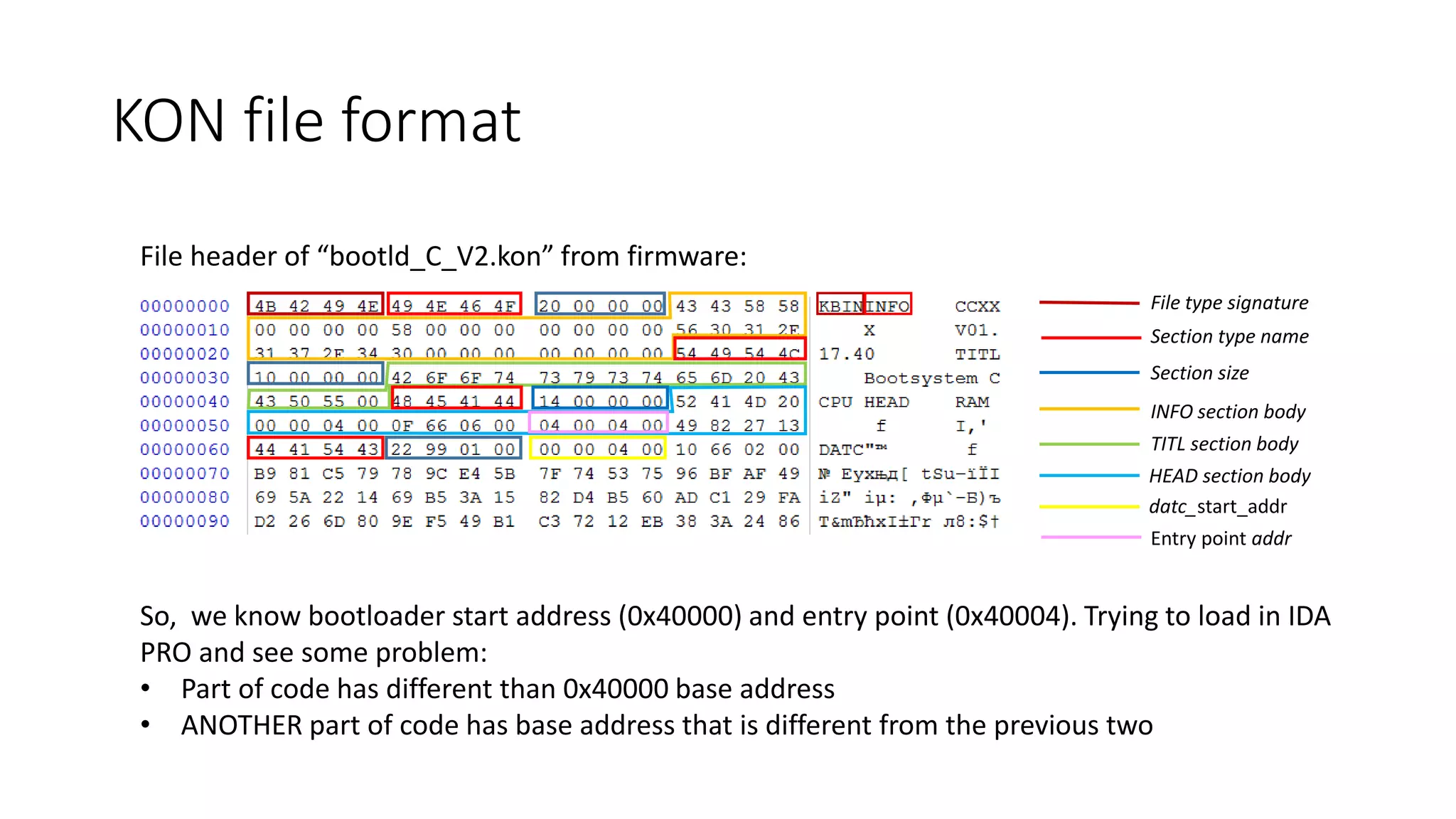
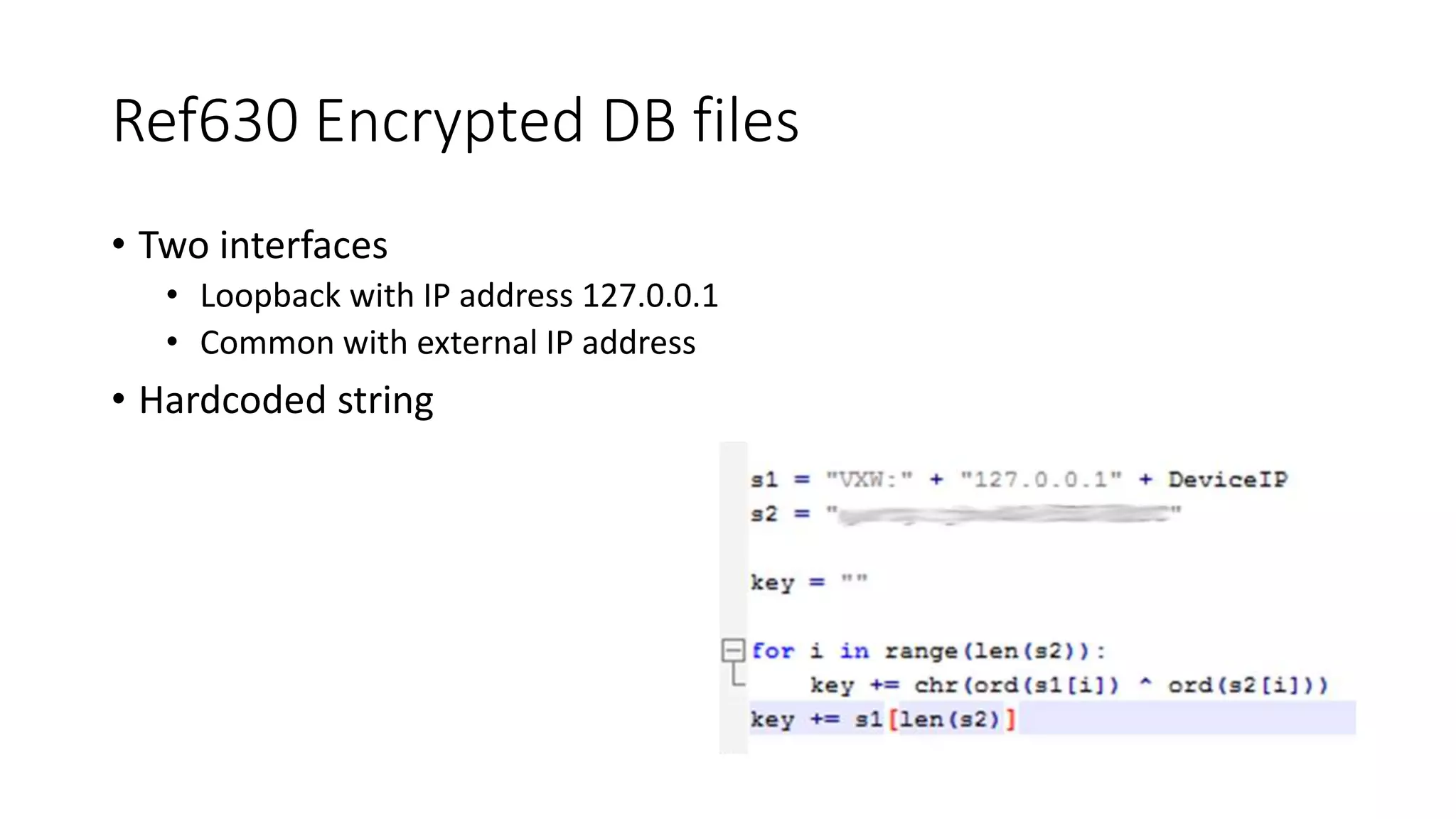
![KON file is set of tagged records with different types. Structure of the record header:
struct KON_section_header
{
char SectionTypeName[4];
DWORD size;
}
struct KON_file_header
{
char Signature[4];
KON_section_header Sections[];
}
In the present case we had the following types of records:
• “HEAD” (char code_type[4]; DWORD minaddr; DWORD maxaddr; DWORD entry_point ; DWORD xorcks)
• “INFO” (char unit[8]; char device[8]; char version[15]; BYTE number)
• "TITL“ (char title[] )
• "DATC“ (DWORD datc_start_addr; DWORD datc_size; DWORD crc)
• "DATA“ (DWORD start_addr; DWORD datca_size; DWORD crc)
• "ENDE“
• https://github.com/rigmar/Recon2017/tree/master/SIPROTEC
KON file format](https://image.slidesharecdn.com/hopelessrelayprotectionforsubstationautomationfin-171015042634/75/Recon-Hopeless-relay-protection-for-substation-automation-16-2048.jpg)