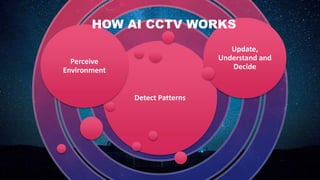
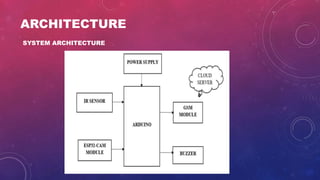
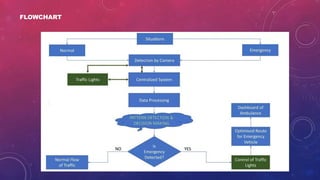
The document discusses using artificial intelligence to enhance closed-circuit television (CCTV) surveillance systems. It describes how integrating AI algorithms allows CCTV systems to detect objects, recognize faces, and analyze behavior in real-time, providing capabilities beyond traditional passive monitoring. The proposed AI-enhanced CCTV system aims to overcome limitations of existing CCTV by leveraging technologies like real-time object detection, predictive analytics, and automated alerts to facilitate quick security responses. The system architecture incorporates components like Arduino, high-end cameras, storage, and AI algorithms to intelligently analyze footage while acknowledging ethical considerations around privacy and compliance.