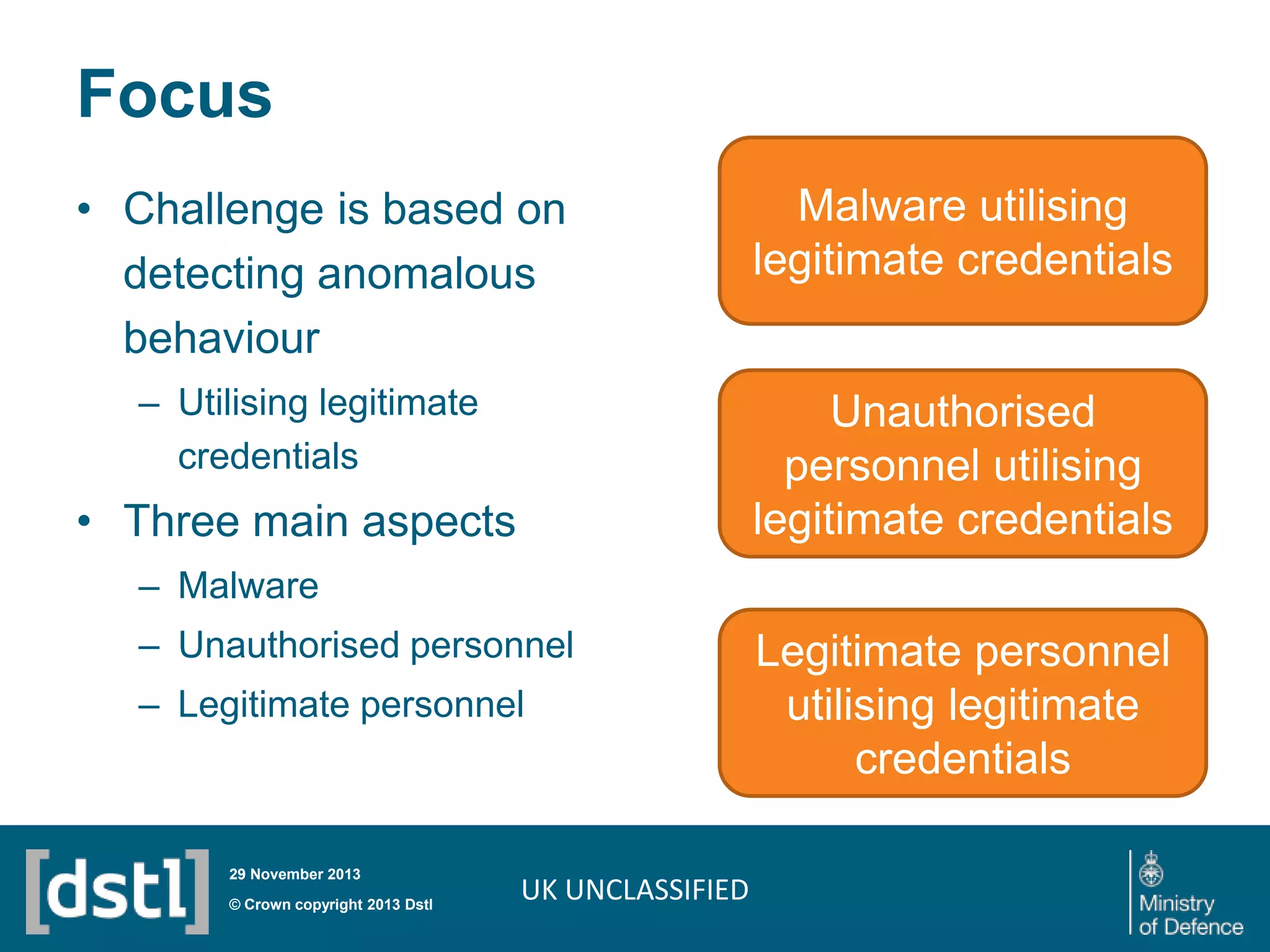
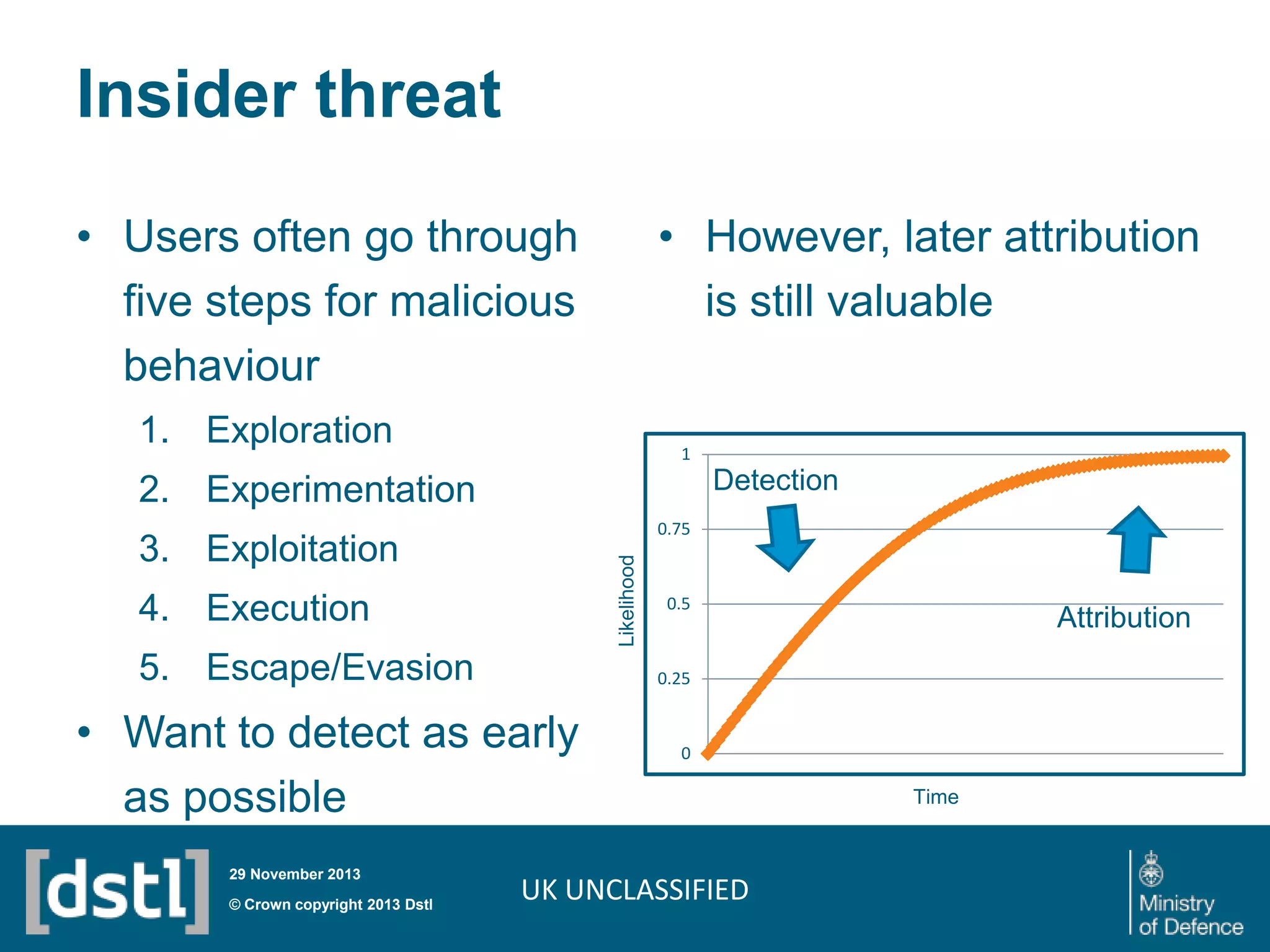
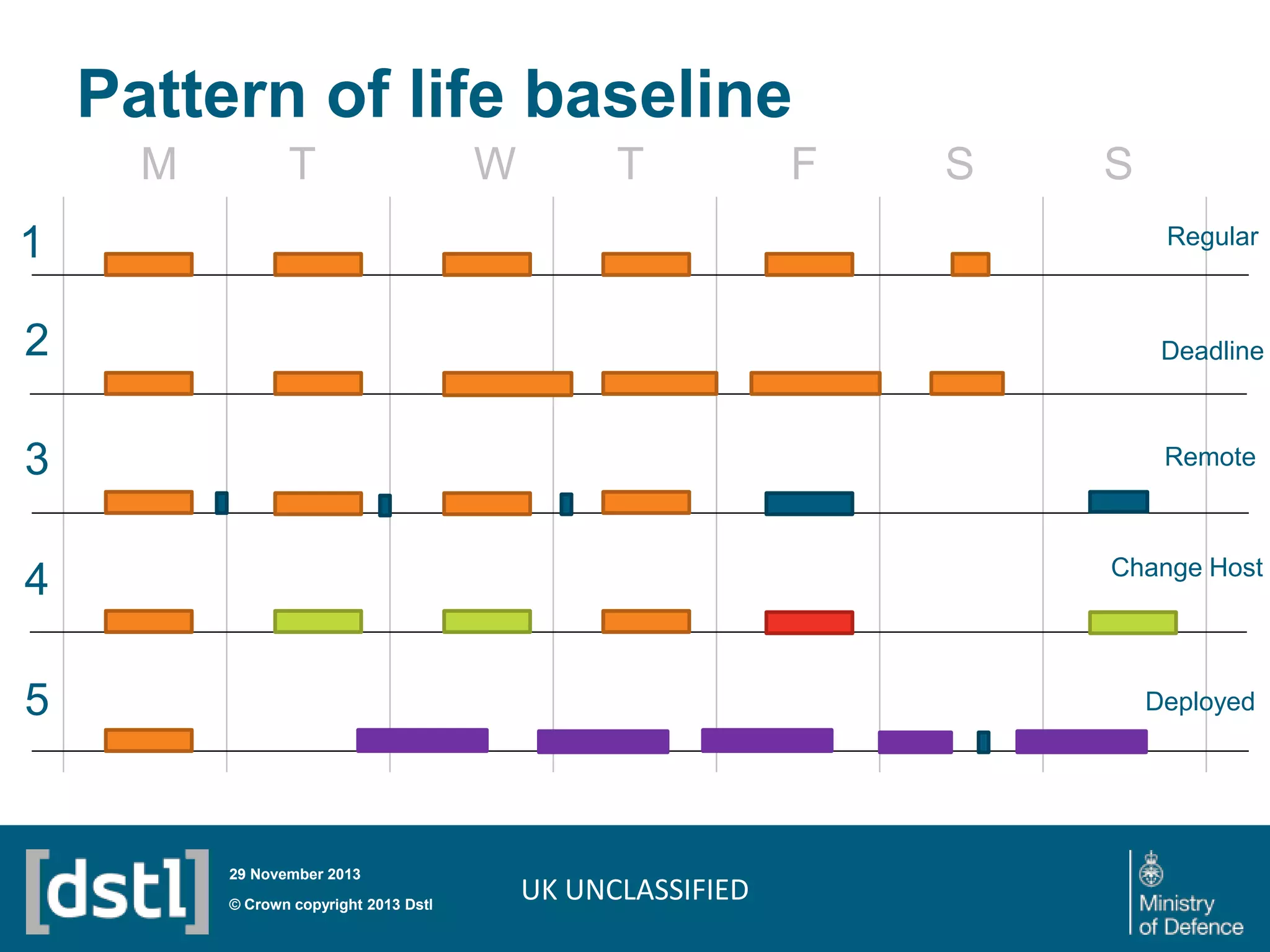
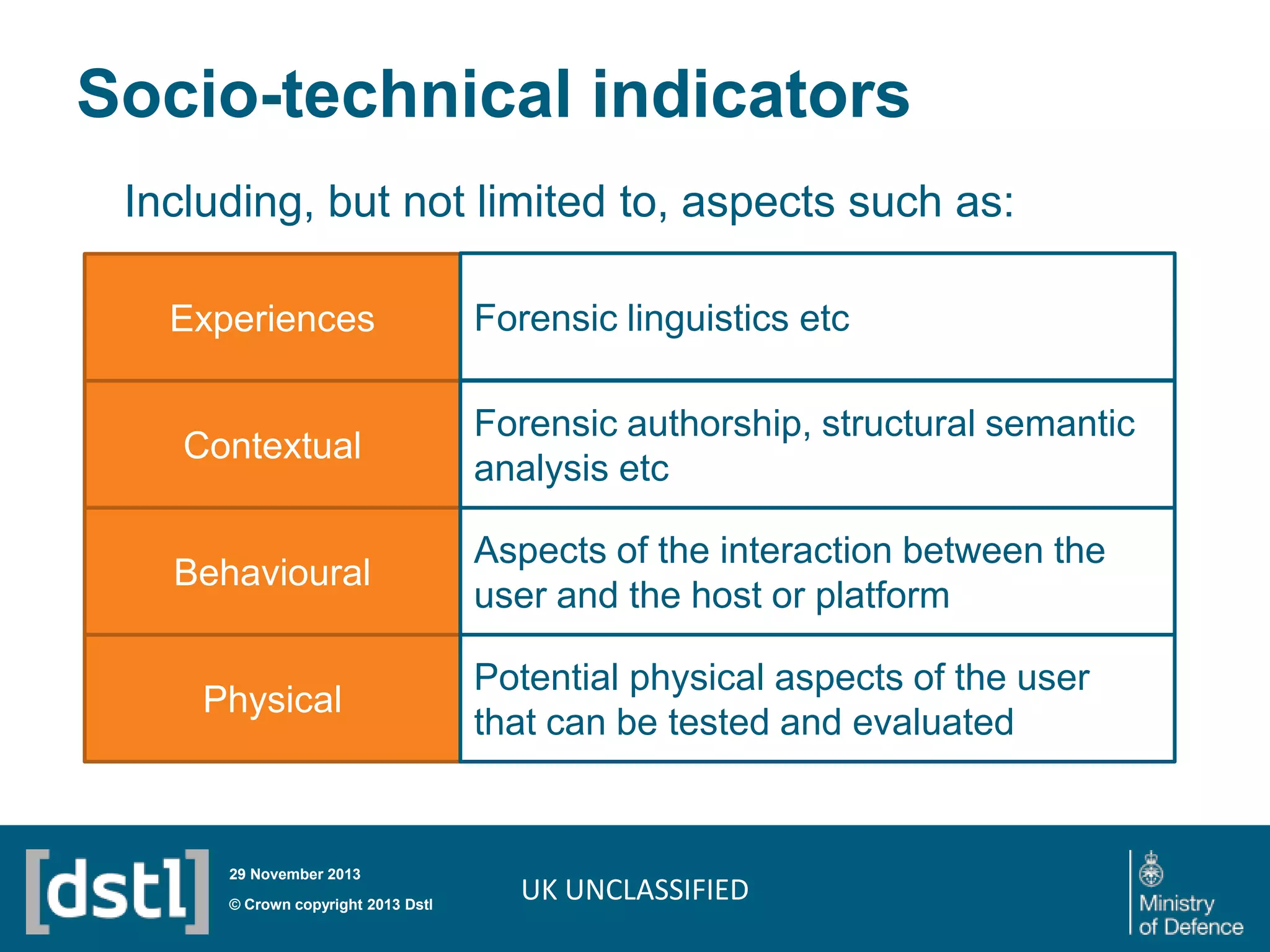
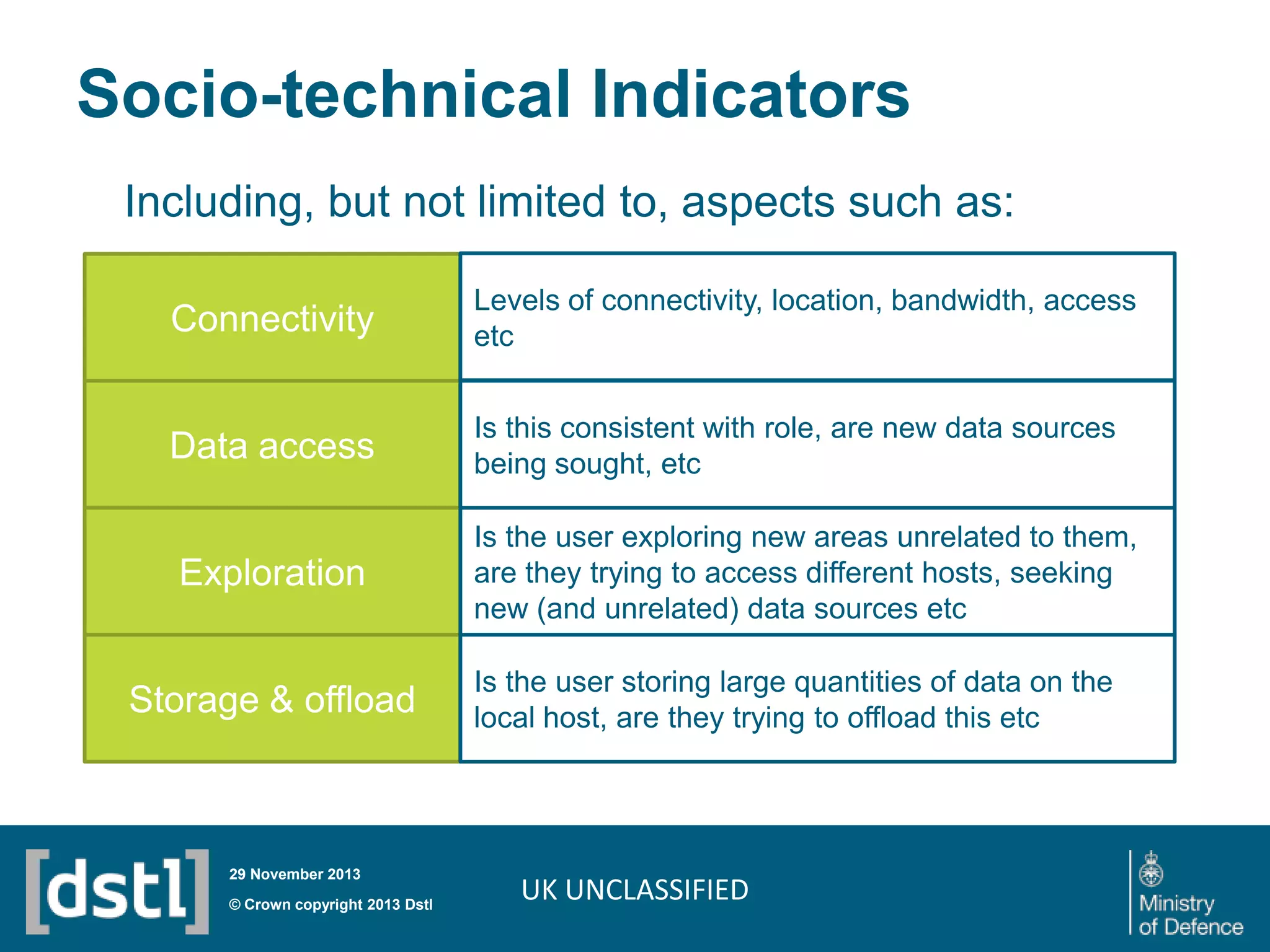
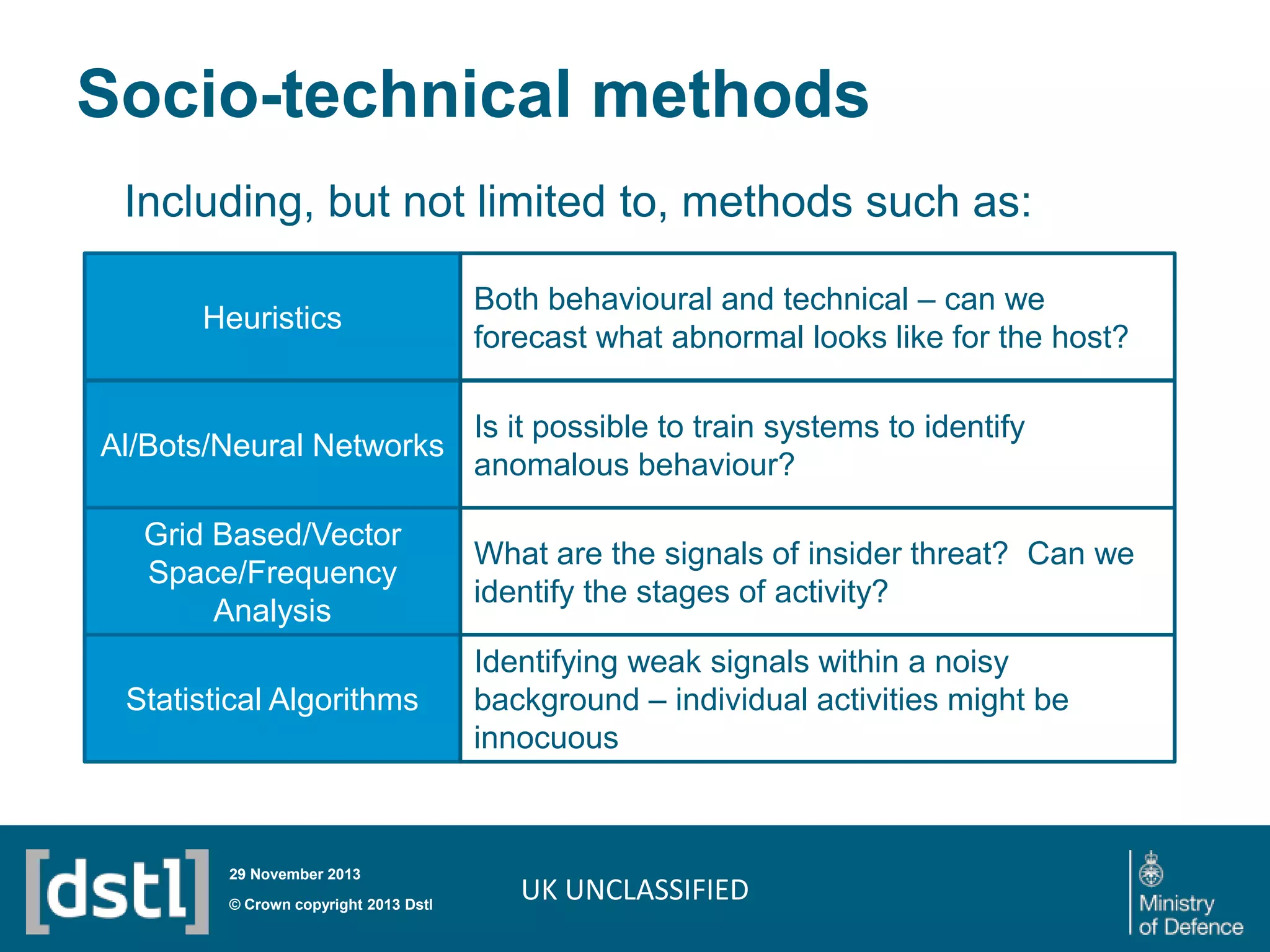
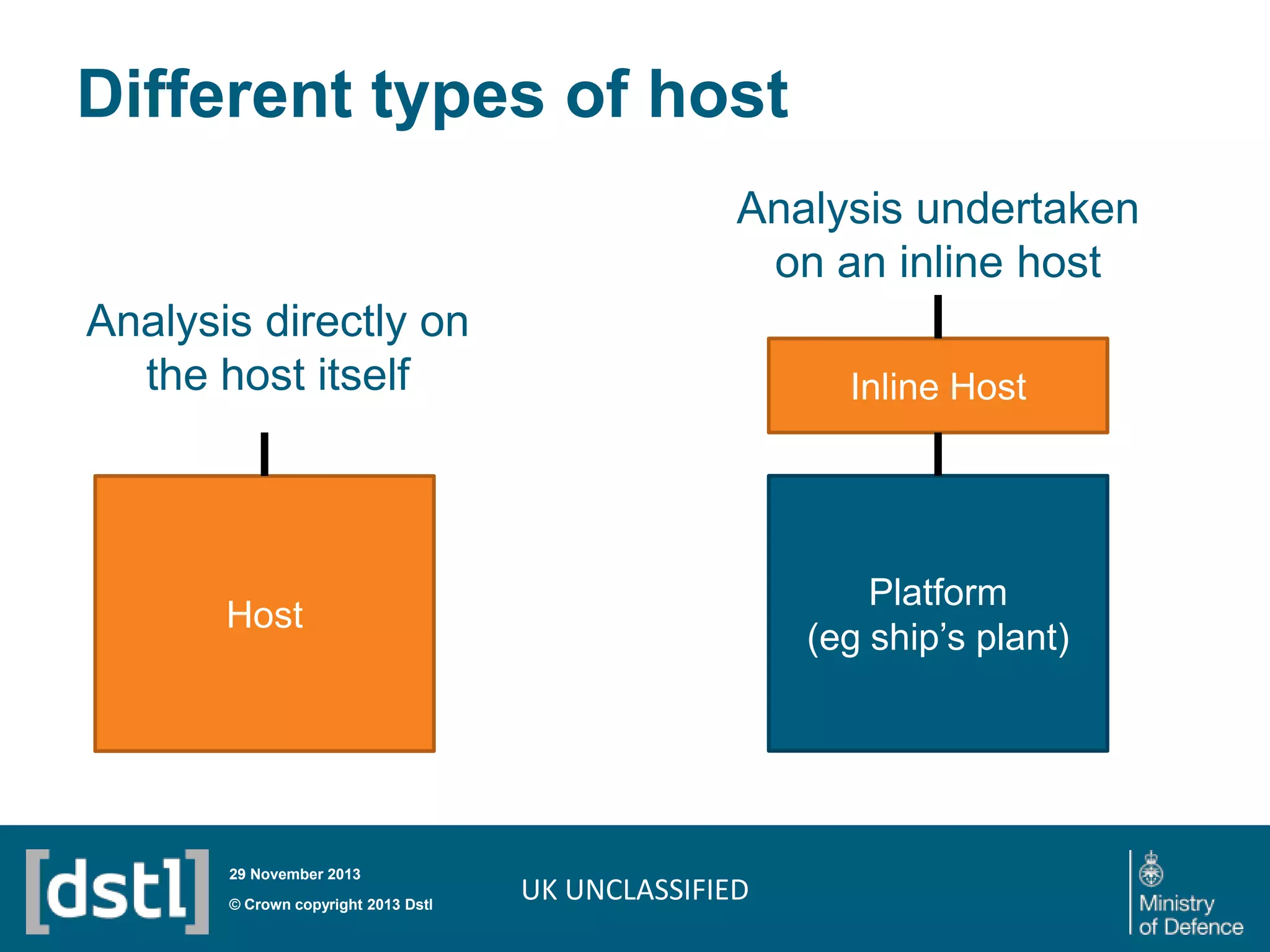
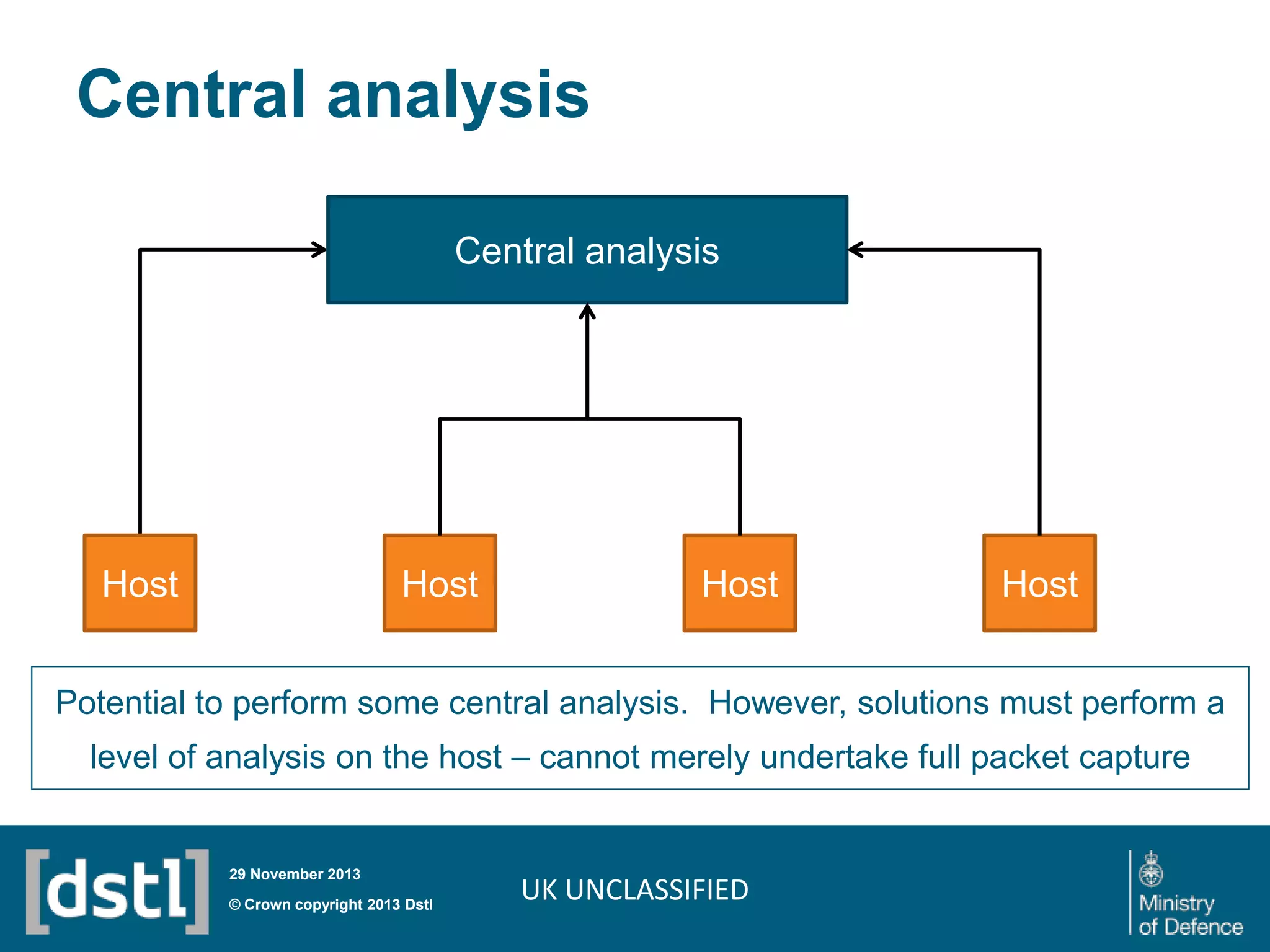
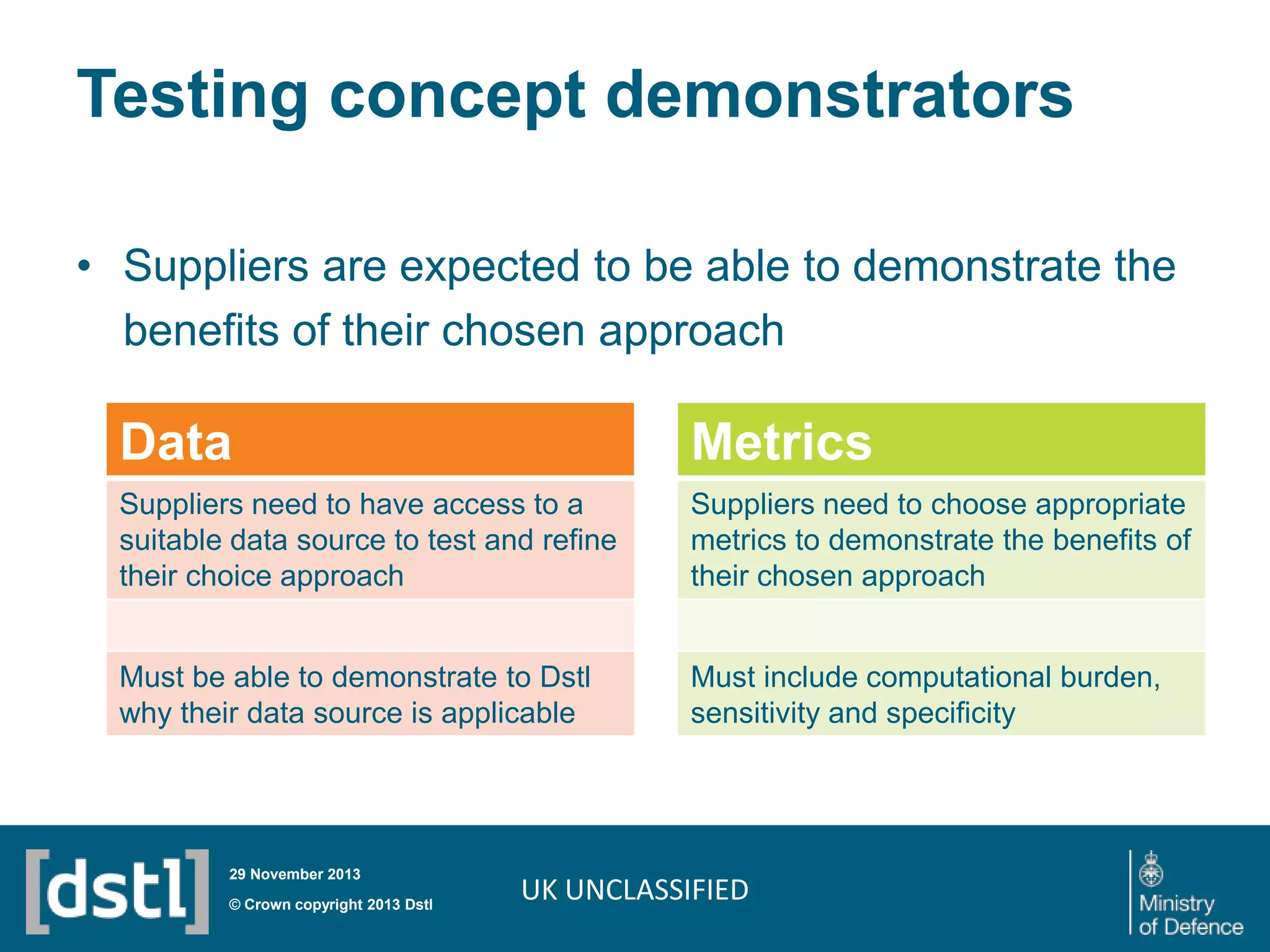
The document outlines a competition launched by the Centre for Defence Enterprise to develop innovative proof-of-concept tools for detecting insider threats and the abuse of legitimate user credentials in cyber defense. It emphasizes the complexity of the threat environment and seeks solutions that can differentiate anomalous behavior related to legitimate credentials. The competition encourages collaborations, aiming for demonstrable results within a tight timeframe, with significant funding available for successful proposals.