Embed presentation
Download as PDF, PPTX







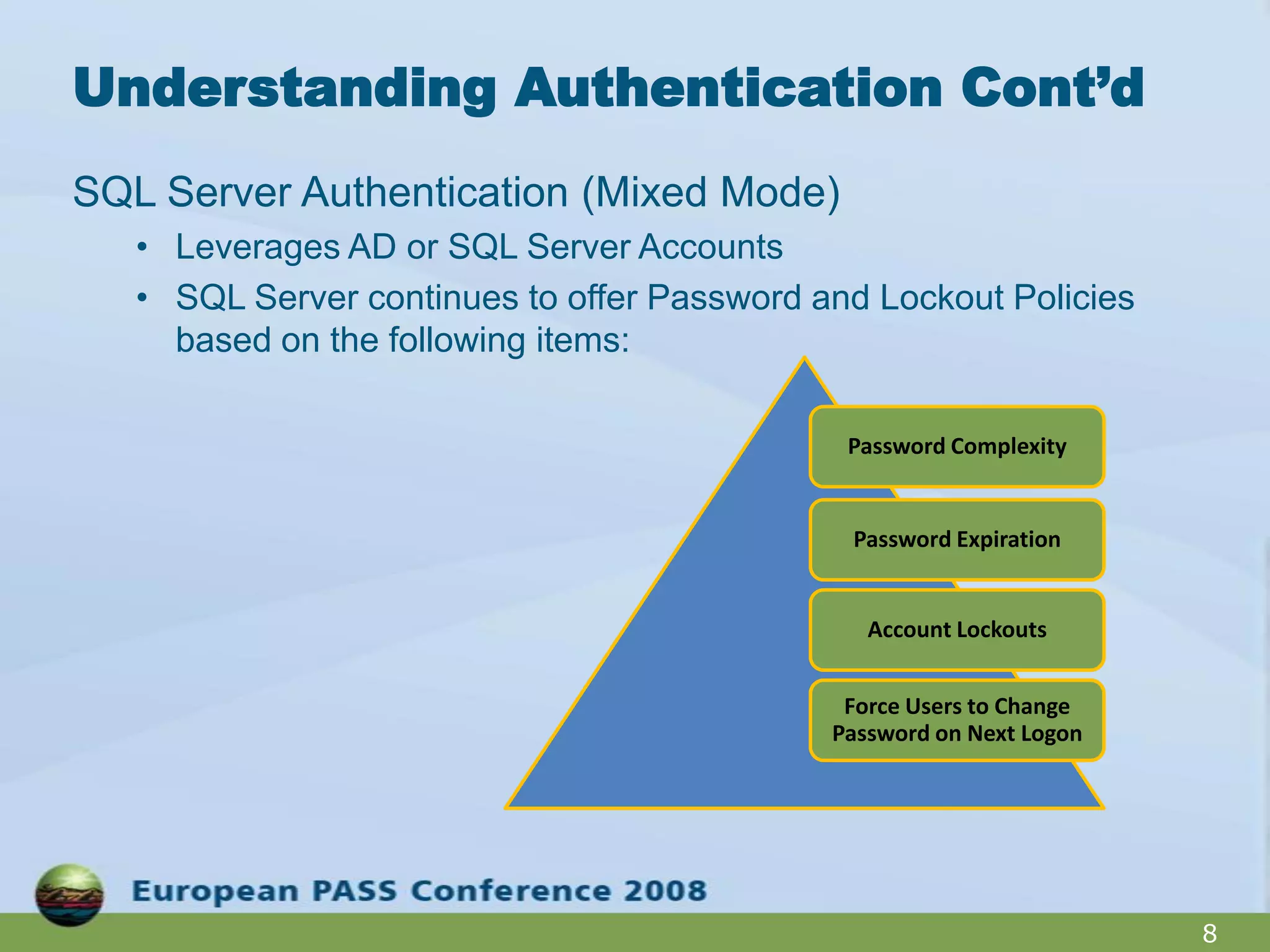

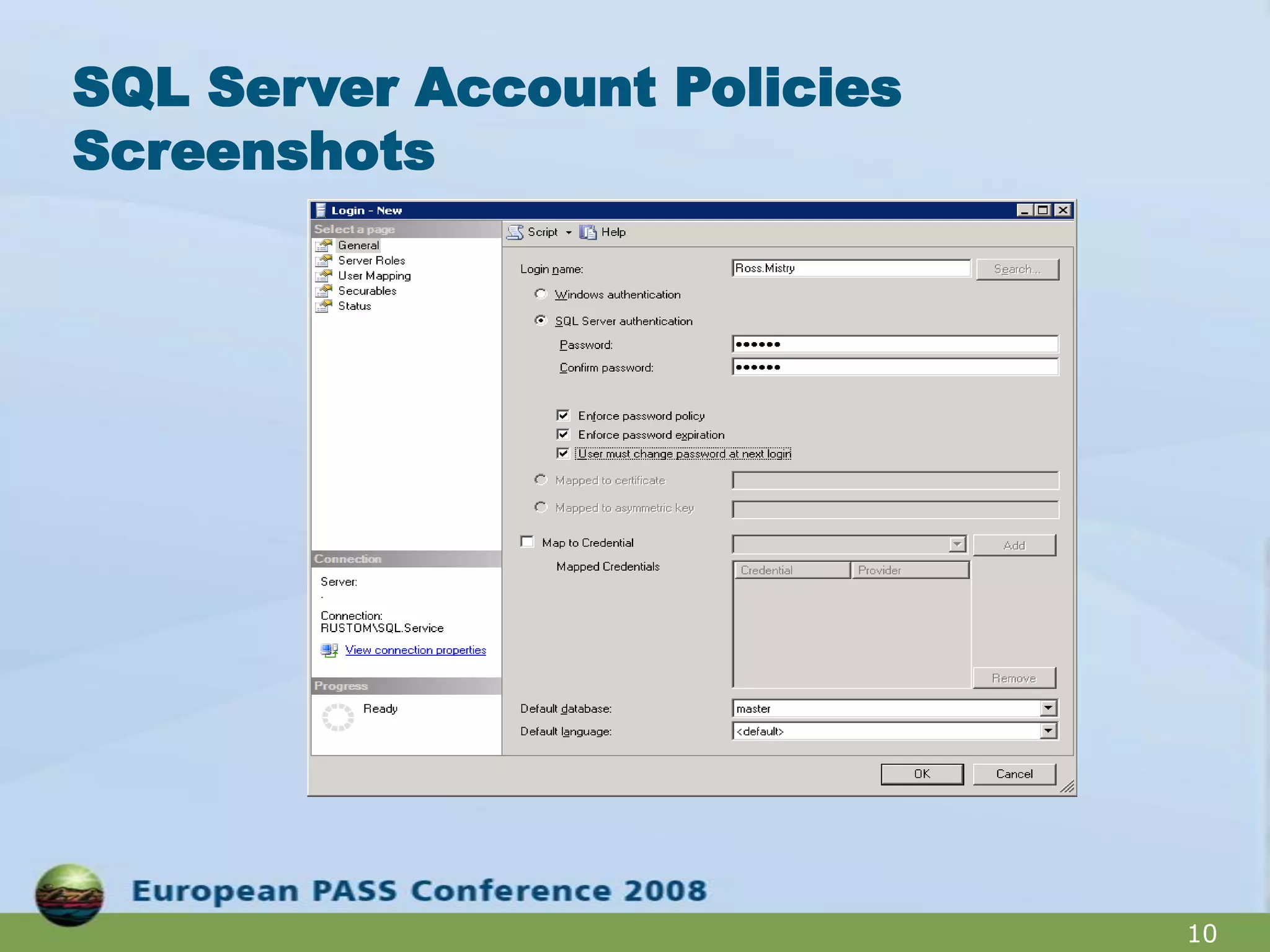




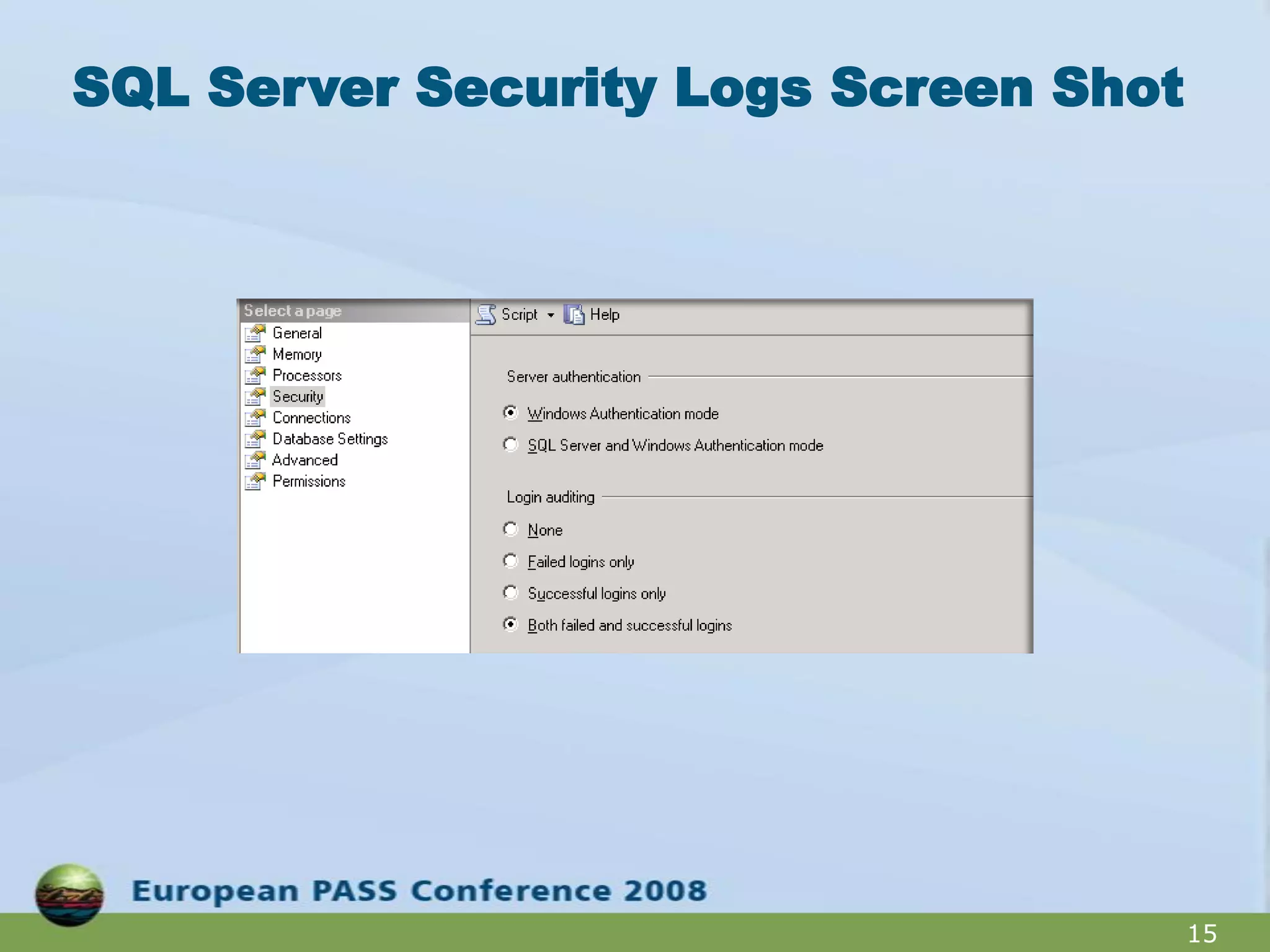








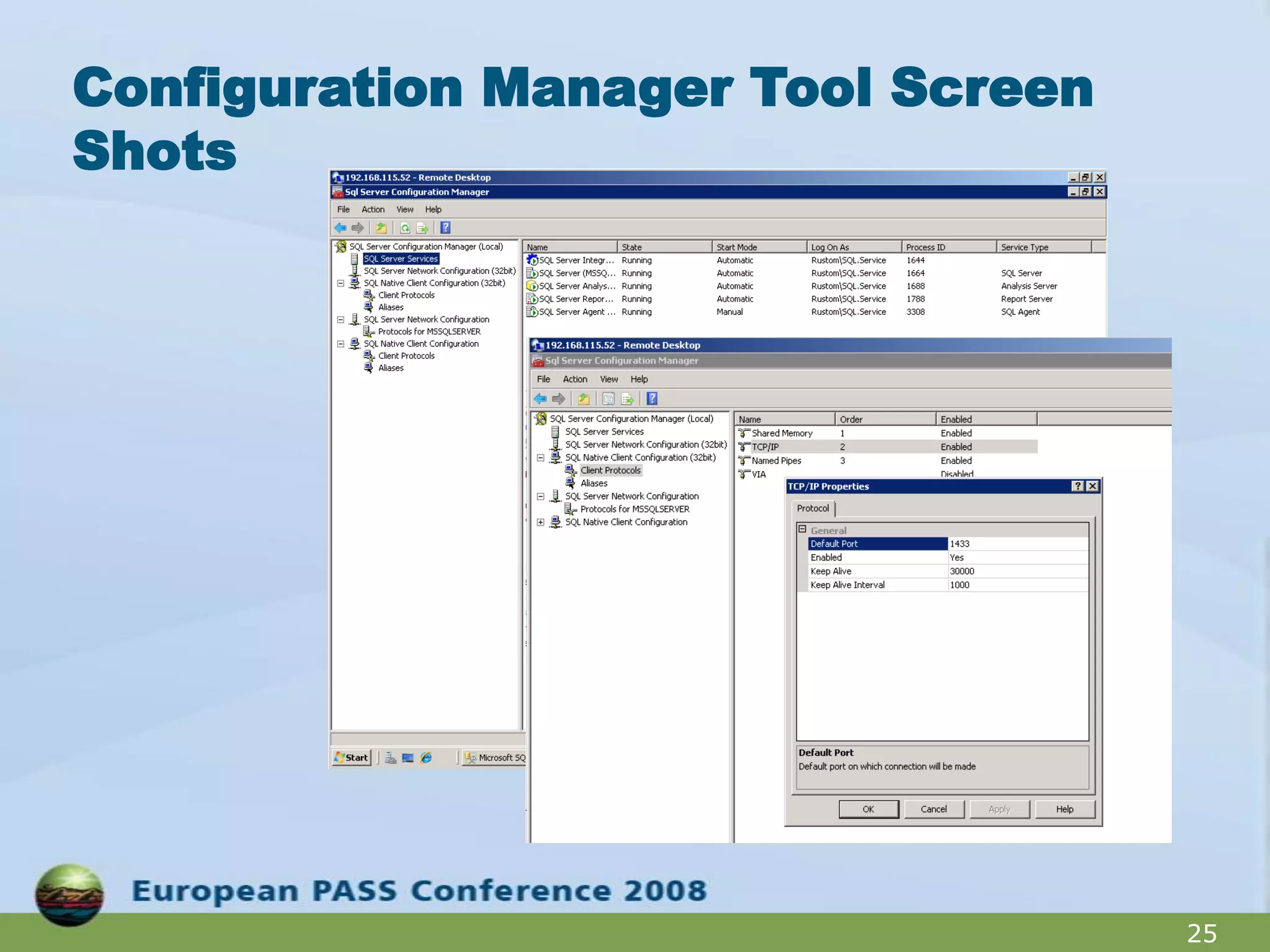






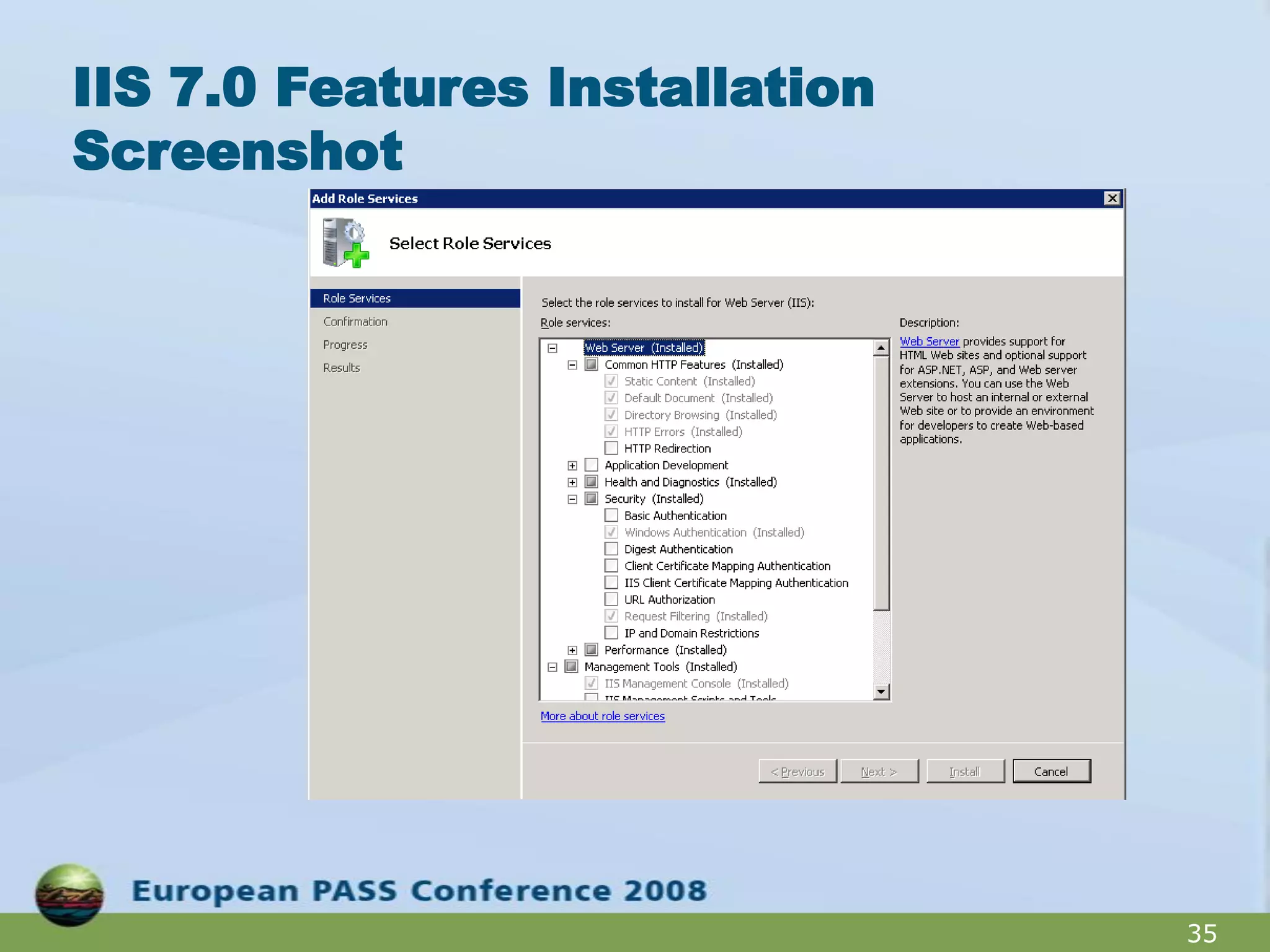



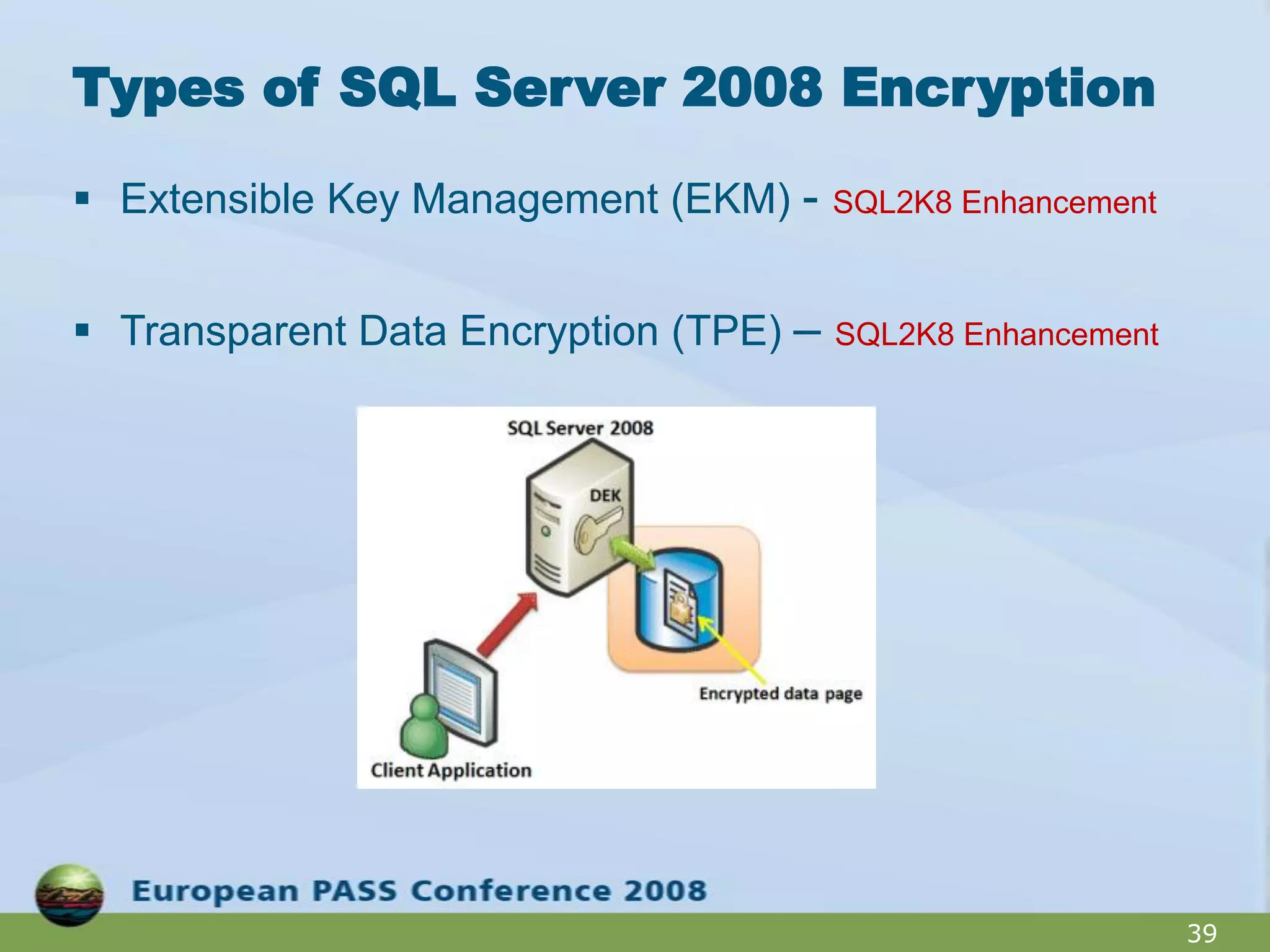






The document outlines best practices for hardening a SQL Server 2008 implementation, emphasizing the importance of security and data protection due to regulatory compliance and the increasing volume of sensitive data. It details technical recommendations on authentication methods, account management, patch management, and auditing, as well as the use of tools like the SQL Server Configuration Manager and the Microsoft Baseline Security Analyzer. It also discusses encryption options for data, both at rest and in transit, and provides resources for further learning.












































