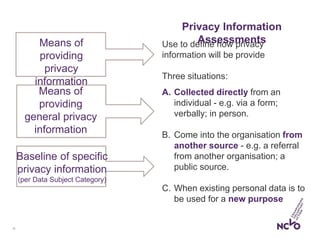
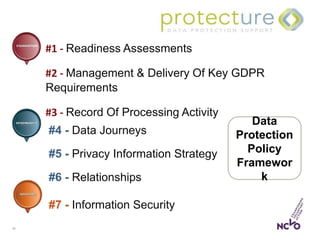
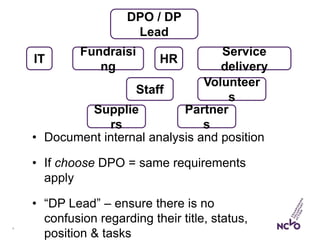
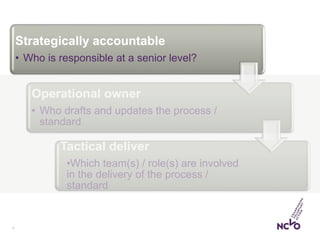
This document outlines the steps organizations need to take to prepare for the General Data Protection Regulation (GDPR), emphasizing the principles of accountability, transparency, and risk management. It details the requirements for data protection officers, the importance of maintaining a record of processing activities (ROPA), and strategies for achieving transparency in privacy notices. Additionally, it identifies the necessary actions for compliance, including establishing strategic accountability, assessing current procedures, and ensuring appropriate security measures are in place.


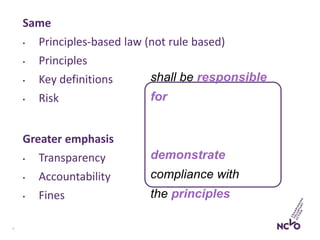

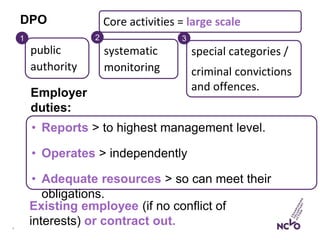





![14
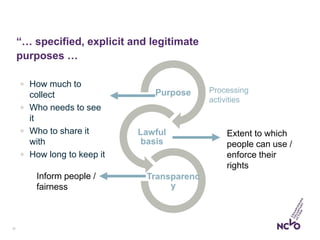
‘Privacy notice’ to describe all the privacy
information you need to make available to
people. It must:
• Be more detailed and specific
• Make notices understandable and accessible
• Be audience specific
• Use house-style language
…still discretion for [you] to
consider where the information…
should be displayed in different
layers of a notice.](https://image.slidesharecdn.com/2018-03-15gdprwebinar-slideshare-180316111241/85/GDPR-Day-1-and-beyond-14-320.jpg)