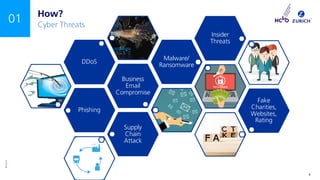
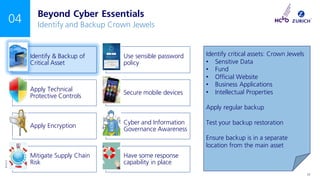
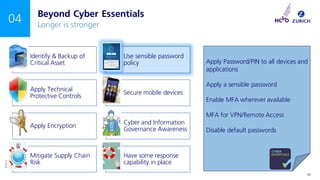
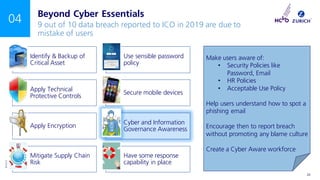
The document outlines a NCVO risk webinar focused on cyber risk awareness and mitigation for charities, emphasizing the importance of recognizing cyber threats and implementing protective measures. Key topics include the prevalence of cyber attacks on charities, the necessity of cyber essentials certification, and the role of senior management in overseeing cyber governance. The event encourages attendees to engage in Q&A and emphasizes the critical need for charities to prioritize cyber security.