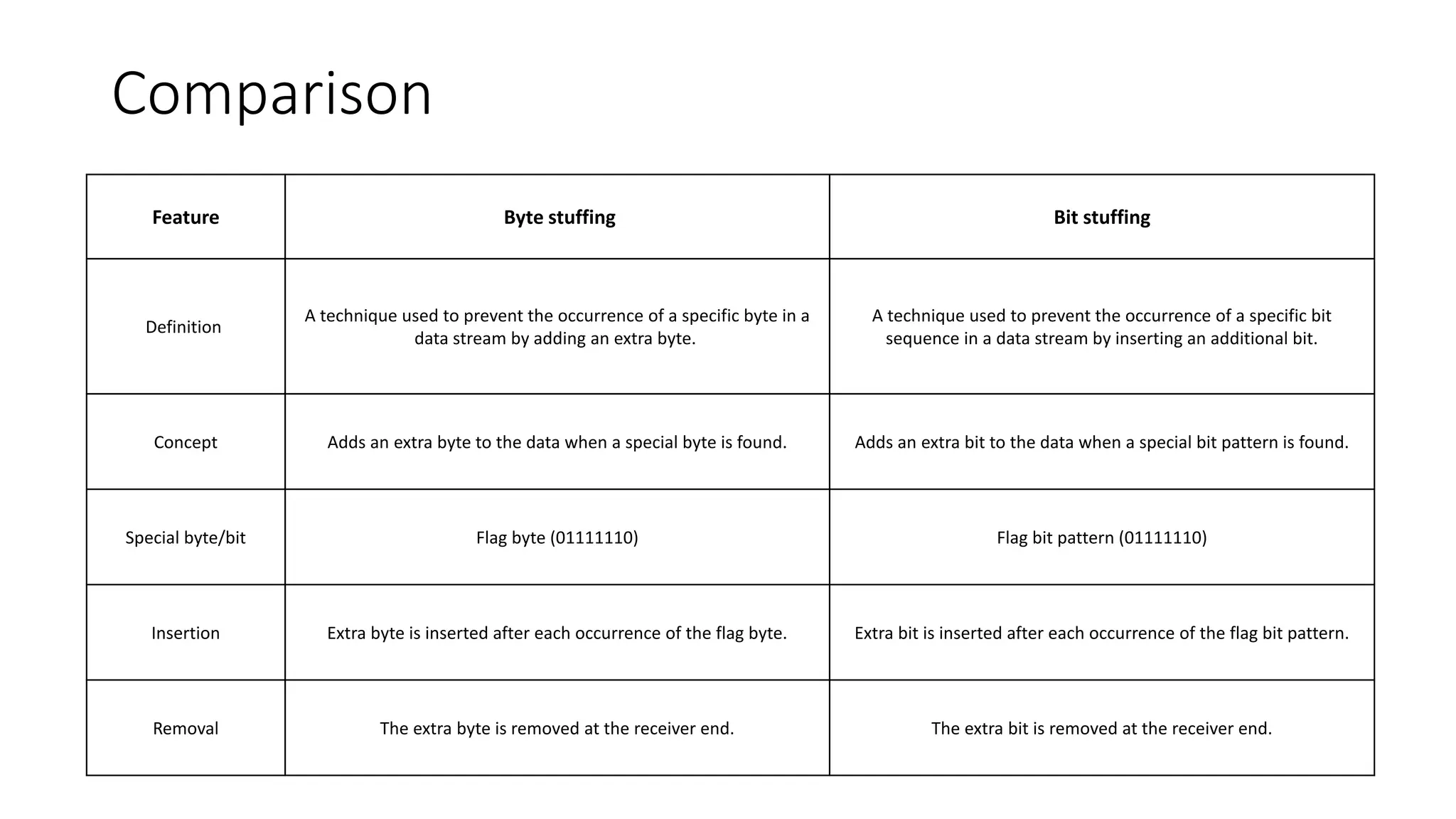
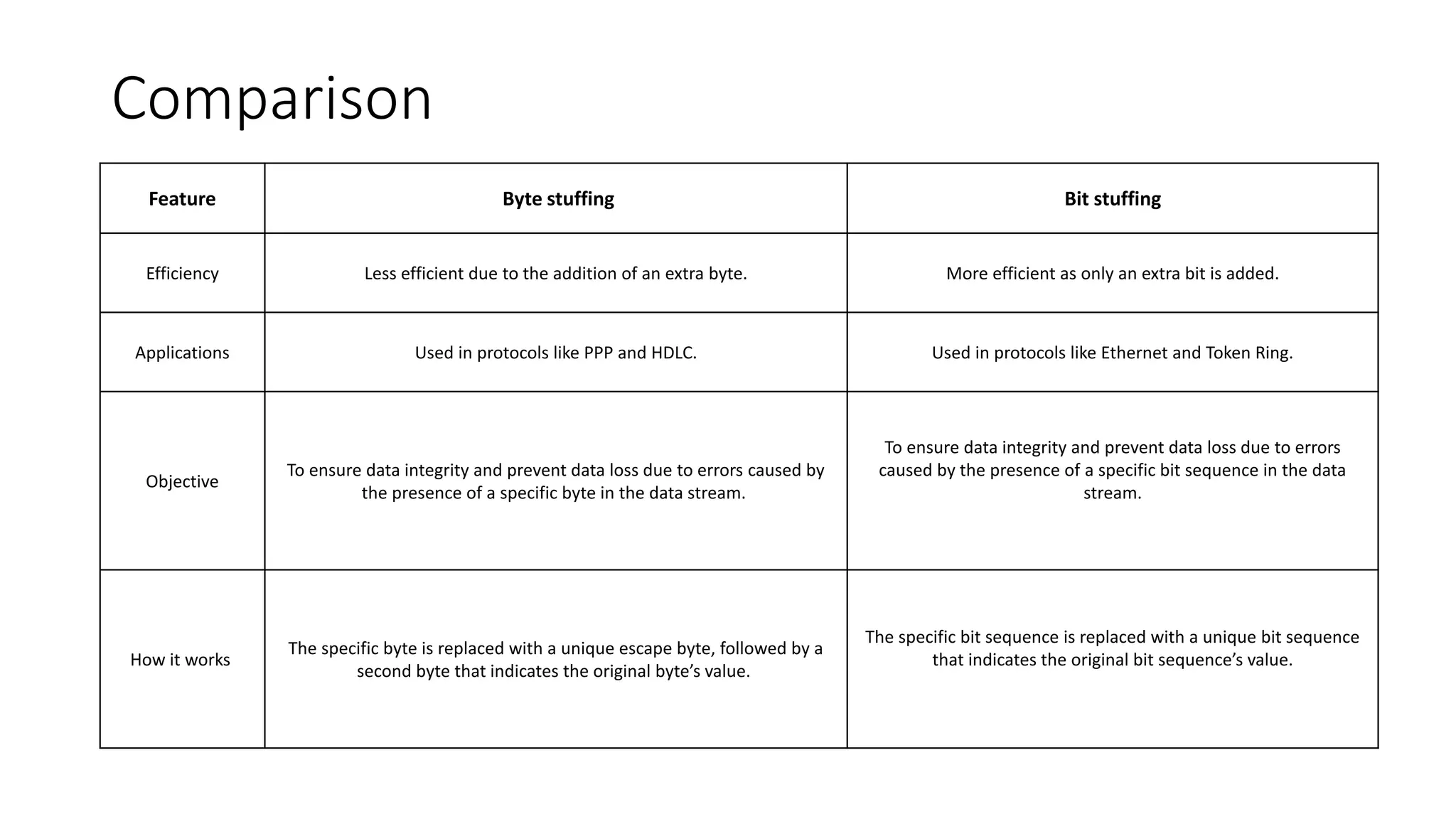
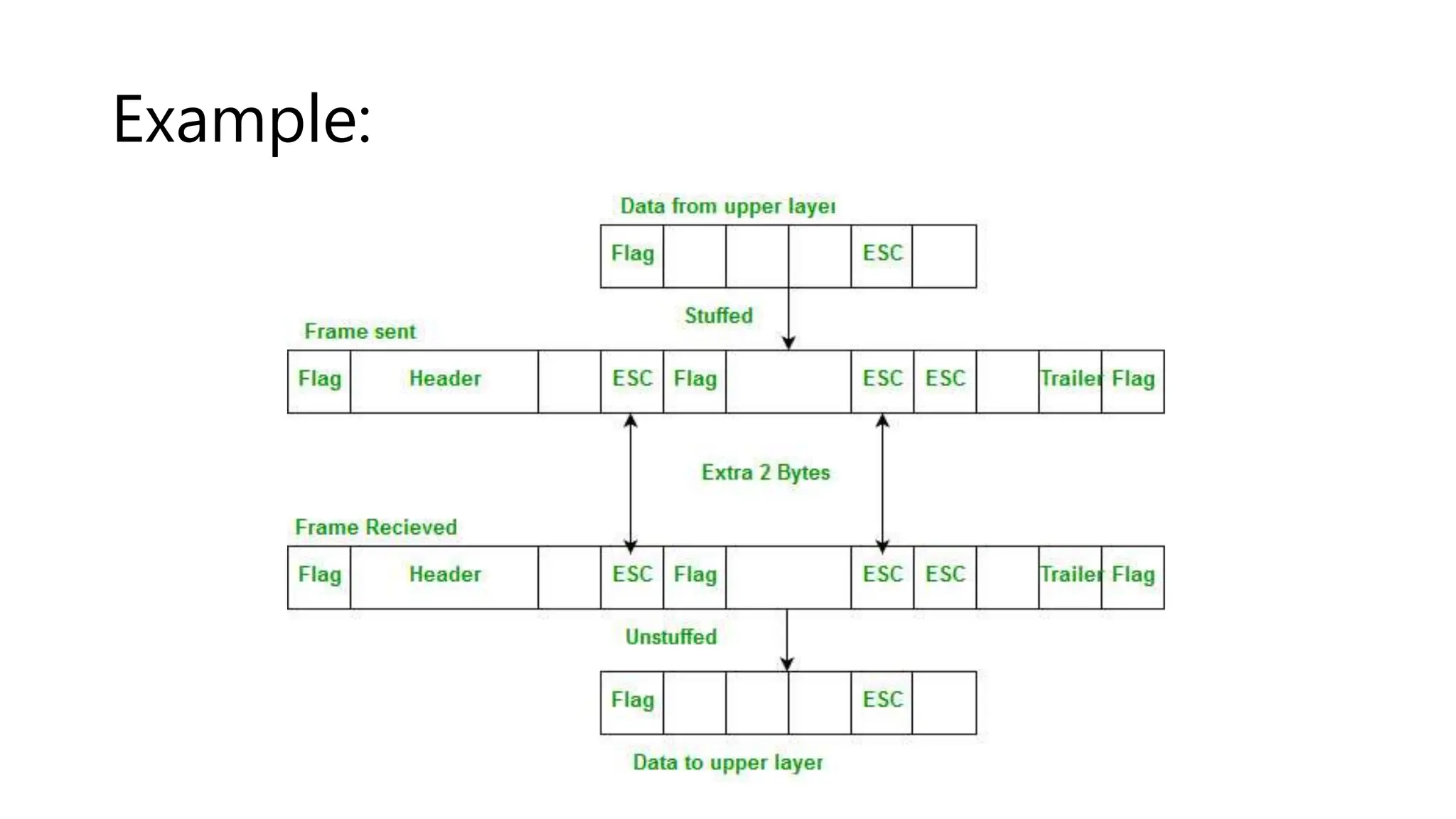
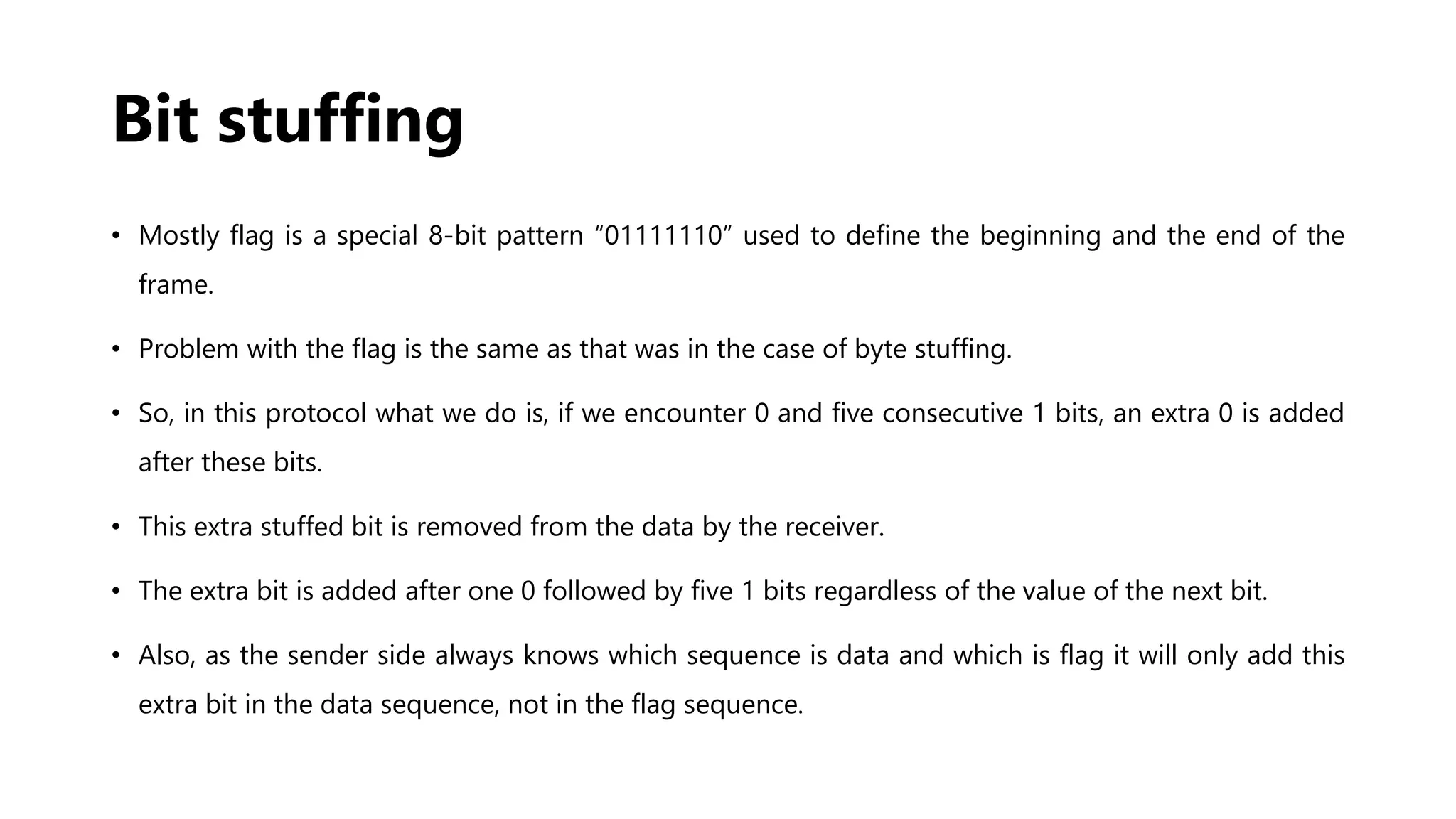
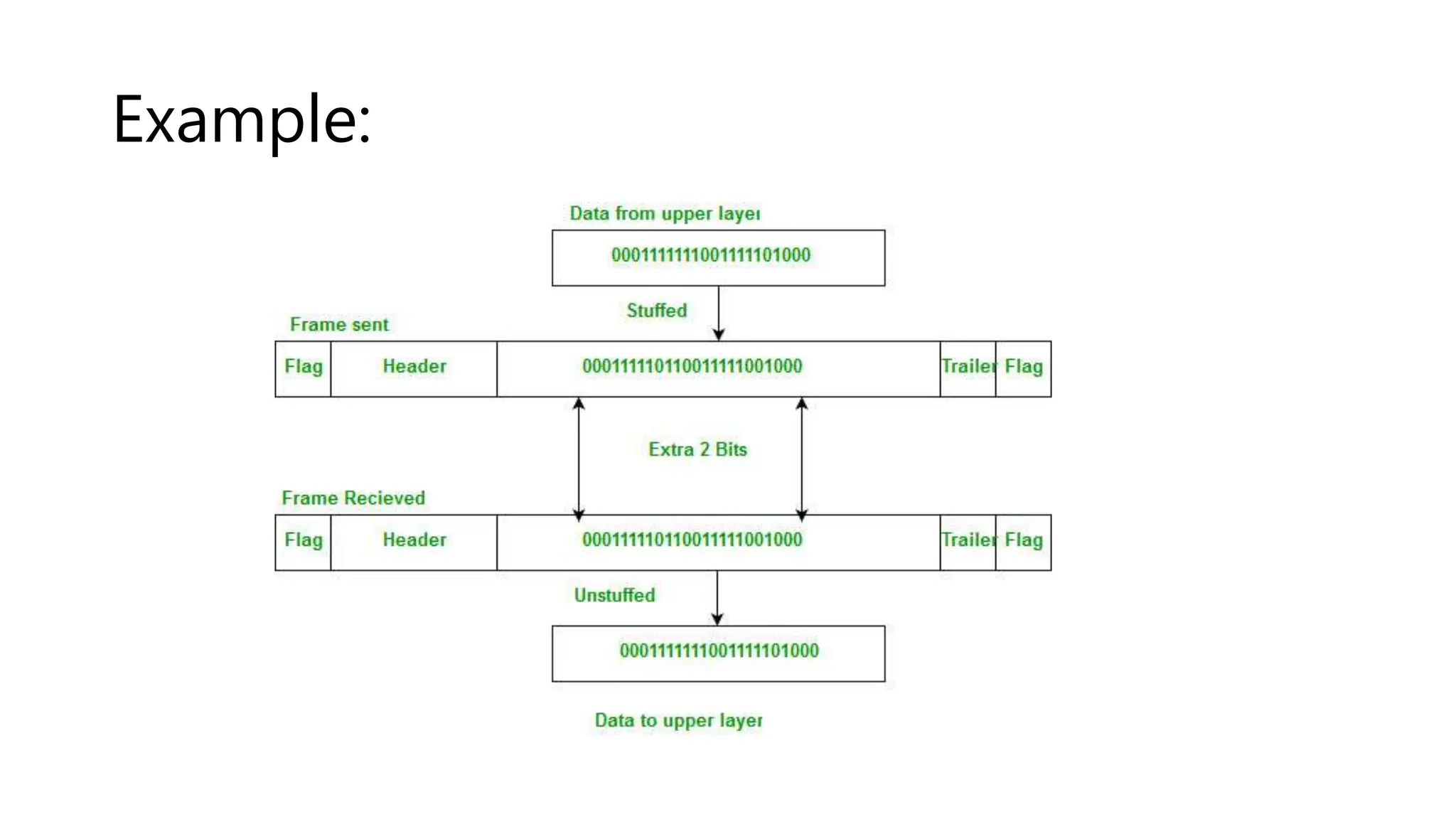
The document explains the concept of framing in the data link layer, specifically focusing on bit and byte stuffing techniques to handle variable-sized frames. Byte stuffing adds an extra byte to prevent specific byte patterns from interfering with frame delimitation, while bit stuffing inserts an extra bit to avoid similar issues with bit sequences. Both techniques are employed to ensure data integrity and prevent loss during transmission, each with its defined applications and methods for handling special patterns.