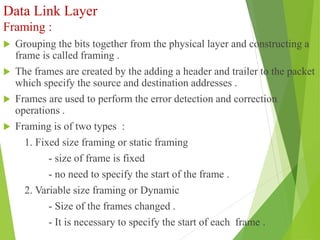
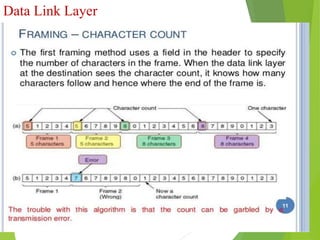
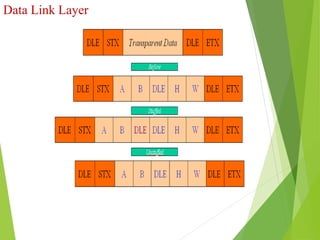
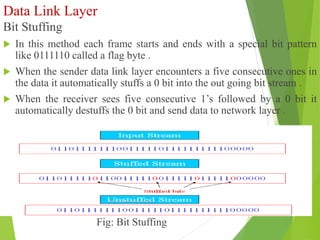
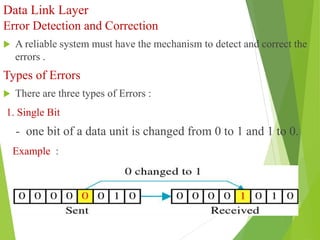
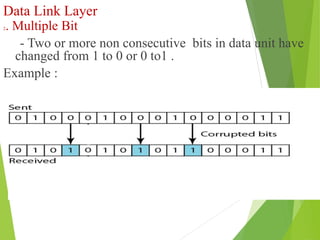
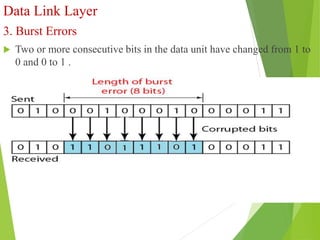
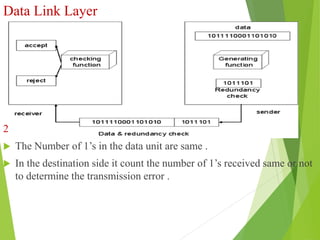
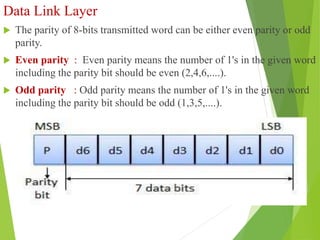
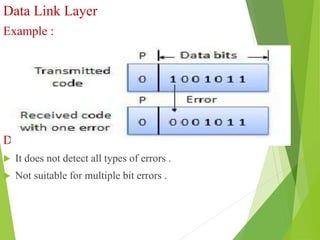
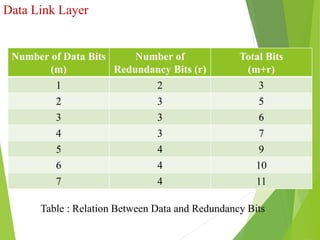
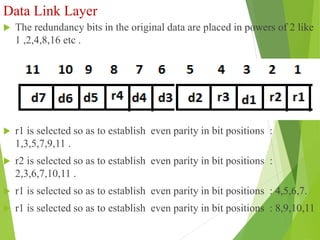
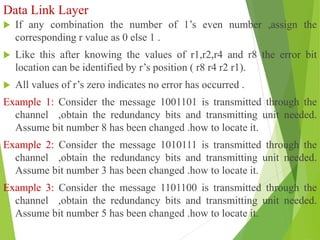
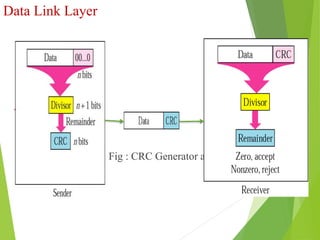
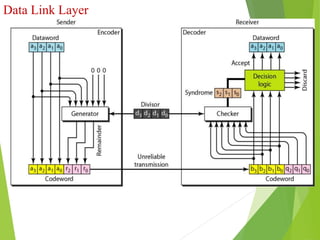
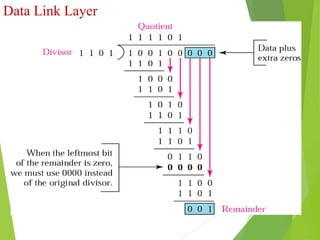
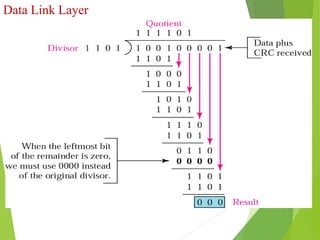
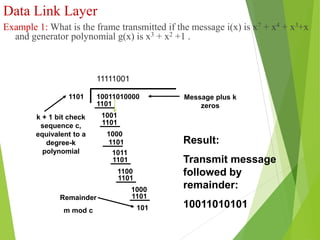
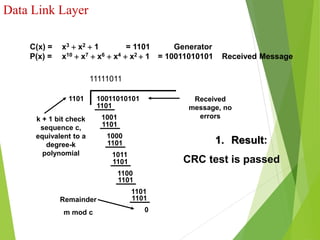
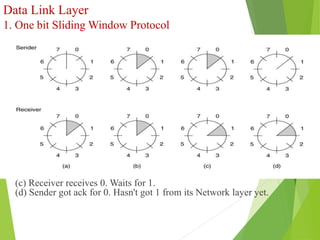
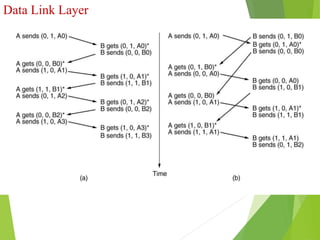
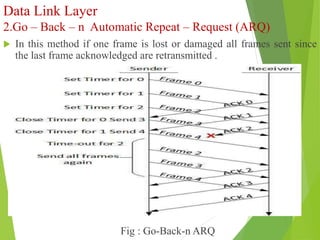
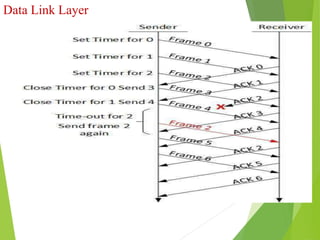
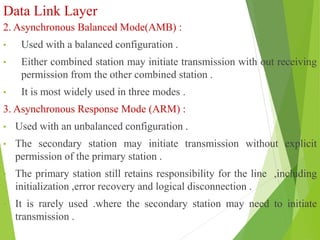
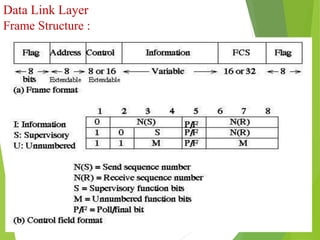
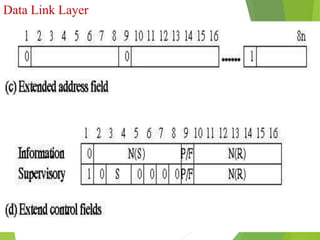
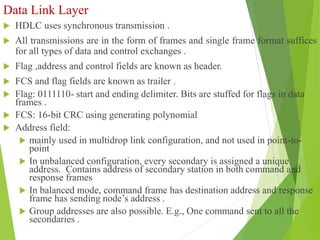
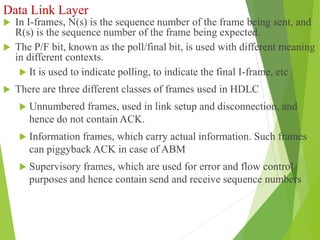
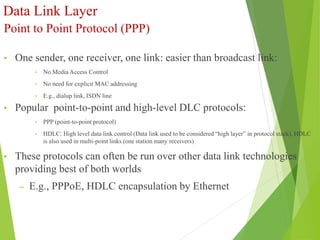
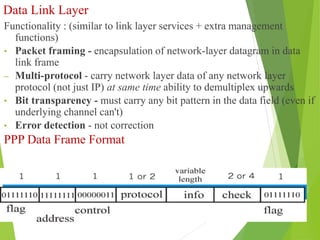
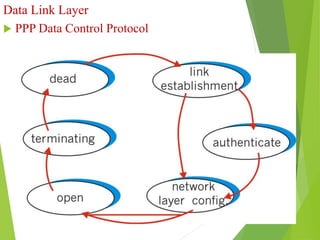
The document discusses several key topics in data link layer design including framing, error detection and correction, and flow control. It describes different framing techniques like character counting, stuffing, and physical layer coding violations. It also explains various error detection methods like parity checks, cyclic redundancy checks (CRC), and Hamming codes. Flow control mechanisms like sliding window protocols are also mentioned. Examples are provided to illustrate Hamming codes and CRC calculations.