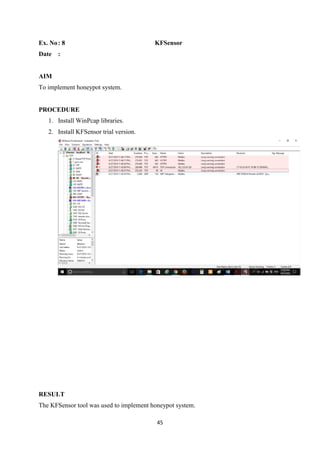
This document provides information about the Security Lab course conducted at R.M.K. College of Engineering and Technology. It lists the objectives of the course as exposing students to cipher techniques, encryption algorithms like DES, RSA, MD5 and SHA-1, and security tools like GnuPG, KF Sensor and NetStumbler. It provides details of 8 experiments to be performed in the lab related to substitution and transposition ciphers, encryption algorithms, digital signatures, secure data storage and transmission, honeypot setup, rootkit installation and intrusion detection. It also lists the expected outcomes, lab equipment requirements and software to be used for the course.




![2
/*Ceaser Cipher */
import java.util.Scanner;
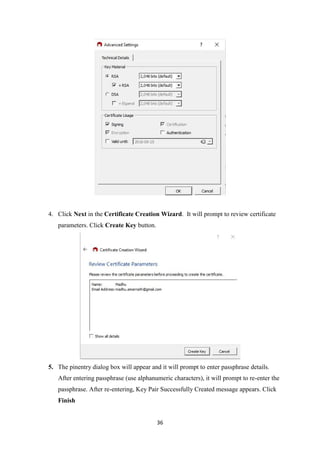
public class CaesarCipher {
public static void main(String[] args) {
Scanner in = new Scanner(System.in);
System.out.println("Enter the plaintext message without space:");
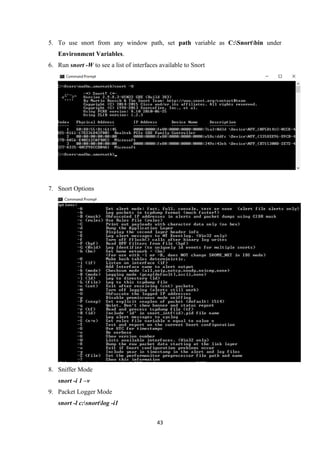
String plainText = in.nextLine();
int key = in.nextInt(); // key value should be from 0 to 25
plainText = plainText.toUpperCase();
char[] plainTextChar = plainText.toCharArray();
//Encryption
for (int i = 0; i < plainTextChar.length; i++) {
plainTextChar[i] = (char) (((int) plainTextChar[i] + key - 65) % 26 + 65);
}
System.out.println("The Ciphertext message:");
String cipherText = String.valueOf(plainTextChar);
System.out.println(cipherText);
plainTextChar = cipherText.toCharArray();
//Decryption
for (int i = 0; i < plainTextChar.length; i++) {
plainTextChar[i] = (char) (((int) plainTextChar[i] - key - 65) % 26 + 65);
}
String recoveredPlainText = String.valueOf(plainTextChar).toLowerCase();
System.out.println("Recovered Plaintext message:");
System.out.println(recoveredPlainText);
}
}](https://image.slidesharecdn.com/it6712labmanual-170818053823/85/IT6712-lab-manual-6-320.jpg)


![5
/*HILL CIPHER*/
import java.util.Scanner;
class HillCipher {
public String encrypt(String plainText, int key[][]) {
char[] text=plainText.toCharArray();
int c1,c2,c3,p1,p2,p3;
p1=(int)text[0] - 65;
p2=(int)text[1] - 65;
p3=(int)text[2] - 65;
c1 = (key[0][0]*p1+key[0][1]*p2+key[0][2]*p3) % 26;
c2 = (key[1][0]*p1+key[1][1]*p2+key[1][2]*p3) % 26;
c3 = (key[2][0]*p1+key[2][1]*p2+key[2][2]*p3) % 26;
char[] cipherText=new char[3];
cipherText[0]=(char)(c1+65);
cipherText[1]=(char)(c2+65);
cipherText[2]=(char)(c3+65);
return String.valueOf(cipherText);
}
}
public class HillCipherDemo {
public static void main(String[] args) {
Scanner sc = new Scanner(System.in);
HillCipher hillCipher = new HillCipher();
System.out.print("Enter the plaintext message:");
String plainText = sc.nextLine();](https://image.slidesharecdn.com/it6712labmanual-170818053823/85/IT6712-lab-manual-9-320.jpg)
![6
int[][] key=new int[3][3];
System.out.println("Enter the Key in 3 X 3 Matrix Format:");
for(int i=0;i<3;i++)
{
for(int j=0;j<3;j++){
key[i][j]= sc.nextInt();
}
}
String cipherText = hillCipher.encrypt(plainText.toUpperCase(), key);
System.out.println("Cipher Text="+cipherText);
}
}](https://image.slidesharecdn.com/it6712labmanual-170818053823/85/IT6712-lab-manual-10-320.jpg)


![9
/*VIGENERE CIPHER*/
import java.util.Arrays;
import java.util.Scanner;
public class VigenereCipherDemo {
public static void main(String[] args) {
Scanner sc = new Scanner(System.in);
String plainText = sc.nextLine();
String key=sc.nextLine();
char[] plainTextChar = plainText.toUpperCase().toCharArray();
char[] keyChar =
Arrays.copyOf(key.toUpperCase().toCharArray(),plainTextChar.length);
int i=0;
//Making length of Key same as length of Plain Text message
for(int j=key.toCharArray().length;j<keyChar.length;j++){
keyChar[j]=keyChar[i];
i++;
}
char[] cipherTextChar = new char[keyChar.length];
//Encryption
for(i=0;i<cipherTextChar.length;i++){
cipherTextChar[i]=(char)(int) ((plainTextChar[i]+keyChar[i]-130)%26+65);
}
System.out.println("Cipher Text="+String.valueOf(cipherTextChar));
char[] recoveredPlainTextChar = new char[cipherTextChar.length];
//Decryption
for(i=0;i<recoveredPlainTextChar.length;i++)](https://image.slidesharecdn.com/it6712labmanual-170818053823/85/IT6712-lab-manual-13-320.jpg)
![10
{
recoveredPlainTextChar[i] = (char)(int) ((cipherTextChar[i]-keyChar[i]+26)%26+65)
;
}
System.out.println("Recovered Plain
Text="+String.valueOf(recoveredPlainTextChar).toLowerCase());
}
}](https://image.slidesharecdn.com/it6712labmanual-170818053823/85/IT6712-lab-manual-14-320.jpg)


![13
/*RAIL FENCE */
import java.util.Scanner;
public class RailFenceDemo {
public static void main(String[] args) {
Scanner sc = new Scanner(System.in);
System.out.println("Enter the plaintext(Even Number of characters):");
String plainText = sc.nextLine();
char[] plainTextChar = plainText.toCharArray();
char[] cipherTextChar = new char[plainTextChar.length];
int i, j = 0;
for (i = 0; i < (cipherTextChar.length / 2); i++) {
cipherTextChar[i] = plainTextChar[j];
cipherTextChar[i + plainTextChar.length / 2] = plainTextChar[j + 1];
j = j + 2;
}
System.out.println("CipherText=" + String.valueOf(cipherTextChar));
char[] recoveredPlainTextChar = new char[cipherTextChar.length];
j = 0;
for (i = 0; i < recoveredPlainTextChar.length; i = i + 2) {
recoveredPlainTextChar[i] = cipherTextChar[j];
recoveredPlainTextChar[i + 1] = cipherTextChar[j + (plainTextChar.length / 2)];
j++;
}
System.out.println("Recovered Plain Text=" +
String.valueOf(recoveredPlainTextChar));
}
}](https://image.slidesharecdn.com/it6712labmanual-170818053823/85/IT6712-lab-manual-17-320.jpg)


![16
/*DES Demo*/
import com.sun.crypto.provider.SunJCE;
import java.util.Base64;
importjava.io.BufferedReader;
importjava.io.InputStreamReader;
importjava.math.BigInteger;
importjava.security.Security;
importjavax.crypto.Cipher;
importjavax.crypto.KeyGenerator;
importjavax.crypto.SecretKey;
public class DesDemo {
public static void main(String[] args) throws Exception{
// TODO code application logic here
BufferedReaderbr = new BufferedReader(new InputStreamReader(System.in));
Security.addProvider(new SunJCE());
//Getting PlainText Message From User
System.out.println("Enter the plaintext message");
String plainMessage = br.readLine();
byte[] input = plainMessage.getBytes();
BigInteger b = new BigInteger(1, input);
System.out.println("PlainText in the binary form: " + b.toString(2));
//System.out.println("Entered PlainText is: " + new String(input));
Cipher cipher = Cipher.getInstance("DES");
KeyGeneratorkeyGen = KeyGenerator.getInstance("DES");
SecretKey key=keyGen.generateKey();](https://image.slidesharecdn.com/it6712labmanual-170818053823/85/IT6712-lab-manual-20-320.jpg)
![17
//Base64 works in Java 8 only
System.out.println("The Key is:"+ Base64.getEncoder().encodeToString(key.getEncoded()));
//Encryption
cipher.init(Cipher.ENCRYPT_MODE, key);
byte[] cipherText = cipher.doFinal(input);
BigInteger b2 = new BigInteger(1, cipherText);
System.out.println("CipherText in the binary form: " + b2.toString(2));
//System.out.println("CipherText: " + new String(cipherText));
//Decryption
cipher.init(Cipher.DECRYPT_MODE, key);
byte[] plainText = cipher.doFinal(cipherText);
System.out.println();
System.out.println("Recovered PlainText : " + new String(plainText));
}
}](https://image.slidesharecdn.com/it6712labmanual-170818053823/85/IT6712-lab-manual-21-320.jpg)


![20
/*RSA Demo */
import java.io.*;
importjava.math.BigInteger;
importjava.security.Security;
importjava.security.KeyPairGenerator;
importjava.security.Key;
importjava.security.KeyPair;
importjavax.crypto.Cipher;
importcom.sun.crypto.provider.SunJCE;
public class RsaDemo {
public static void main(String[] args) throws Exception {
BufferedReaderbr = new BufferedReader(new InputStreamReader(System.in));
Security.addProvider(new SunJCE());
//Getting PlainText Message From User
System.out.println("Enter the plaintext message");
String plainMessage = br.readLine();
byte[] input = plainMessage.getBytes();
BigInteger b = new BigInteger(1, input);
System.out.println("PlainText in the binary form: " + b.toString(2));
//System.out.println("Entered PlainText is: " + new String(input));
Cipher cipher = Cipher.getInstance("RSA");
// Get an instance of the RSA key generator](https://image.slidesharecdn.com/it6712labmanual-170818053823/85/IT6712-lab-manual-24-320.jpg)
![21
KeyPairGeneratorkpg = KeyPairGenerator.getInstance("RSA");
kpg.initialize(2048);
// Generate the keys
KeyPairkp = kpg.genKeyPair();
Key publicKey = kp.getPublic();
Key privateKey = kp.getPrivate();
//Encryption
cipher.init(Cipher.ENCRYPT_MODE, publicKey);
byte[] cipherText = cipher.doFinal(input);
BigInteger b2 = new BigInteger(1, cipherText);
System.out.println("CipherText in the binary form: " + b2.toString(2));
//System.out.println("CipherText: " + new String(cipherText));
//Decryption
cipher.init(Cipher.DECRYPT_MODE, privateKey);
byte[] plainText = cipher.doFinal(cipherText);
System.out.println();
System.out.println("Recovered PlainText : " + new String(plainText));
}
}](https://image.slidesharecdn.com/it6712labmanual-170818053823/85/IT6712-lab-manual-25-320.jpg)
![22
/*RSA Version 2 */
import java.math.BigInteger;
import java.io.BufferedReader;
import java.io.InputStreamReader;
public class RSAAlgorithm {
public static void main(String[] args) throws Exception {
// TODO code application logic here
BufferedReader br = new BufferedReader(new InputStreamReader(System.in));
System.out.println("Enter Encryption Constant:");
BigInteger e = new BigInteger(br.readLine());
System.out.println("Enter Prime Number 1:");
BigInteger p = new BigInteger(br.readLine());
System.out.println("Enter Prime Number 2:");
BigInteger q = new BigInteger(br.readLine());
BigInteger n = p.multiply(q);
BigInteger phi = p.subtract(BigInteger.ONE).multiply(q.subtract(BigInteger.ONE));
BigInteger d = e.modInverse(phi);
System.out.println("Enter PlainText Message:");
BigInteger plainText = new BigInteger(br.readLine());
BigInteger cipherText = plainText.modPow(e, n);
System.out.println("CipherText:" + cipherText);
BigInteger recoveredPlainText = cipherText.modPow(d, n);
System.out.println("Recovered PlainText:" + recoveredPlainText);
}
}](https://image.slidesharecdn.com/it6712labmanual-170818053823/85/IT6712-lab-manual-26-320.jpg)


![25
/*Message Digest Demo – MD5 and SHA-1*/
import java.io.*;
importjava.math.BigInteger;
importjava.security.Security;
importjava.security.MessageDigest;
importcom.sun.crypto.provider.SunJCE;
public class MessageDigestDemo {
public static void main(String[] args) throws Exception {
BufferedReaderbr=new BufferedReader(new InputStreamReader(System.in));
Security.addProvider(new SunJCE());
System.out.println("Enter the message");
String message=br.readLine();
byte[] input = message.getBytes();
System.out.println("Message: " + new String(input));
MessageDigest md = MessageDigest.getInstance("MD5");
//MessageDigest md = MessageDigest.getInstance("SHA-1");
md.update(input);
byte[] hash = md.digest();
BigInteger b=new BigInteger(1,hash);
String hashValue=b.toString(16);
System.out.println("MessageDigest in HexaDecimal Format: " + hashValue);
}
}](https://image.slidesharecdn.com/it6712labmanual-170818053823/85/IT6712-lab-manual-29-320.jpg)


![28
/*Diffie-Hellman Key Exchange*/
import java.io.BufferedReader;
import java.io.InputStreamReader;
import java.math.BigInteger;
import java.io.IOException;
public class DiffieHellman {
public static void main(String[] args) {
// TODO code application logic here
try {
BufferedReader br = new BufferedReader(new InputStreamReader(System.in));
System.out.println("Enter the prime number:");
BigInteger primeNumber = new BigInteger(br.readLine());
System.out.println("Enter the primitive root of prime number:");
BigInteger primitiveRoot = new BigInteger(br.readLine());
System.out.println("Enter the private key of A:");
BigInteger privateKeyA = new BigInteger(br.readLine());
System.out.println("Enter the private key of B:");
BigInteger privateKeyB = new BigInteger(br.readLine());
BigInteger publicKeyA = primitiveRoot.modPow(privateKeyA, primeNumber);
BigInteger publicKeyB = primitiveRoot.modPow(privateKeyB, primeNumber);
System.out.println("Public Key of A:" + publicKeyA);
System.out.println("Public Key of B:" + publicKeyB);
BigInteger sharedSecretKeyB = publicKeyA.modPow(privateKeyB, primeNumber);
BigInteger sharedSecretKeyA = publicKeyB.modPow(privateKeyA, primeNumber);
System.out.println("Shared Secret Key Computed By A:" + sharedSecretKeyA);
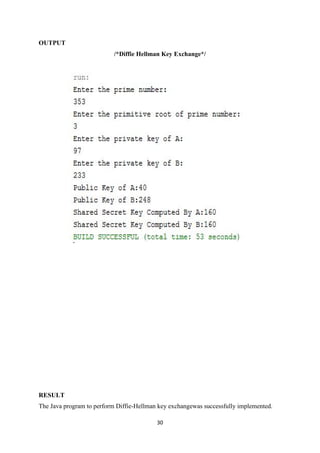
System.out.println("Shared Secret Key Computed By B:" + sharedSecretKeyB);](https://image.slidesharecdn.com/it6712labmanual-170818053823/85/IT6712-lab-manual-32-320.jpg)


![32
/*DSS*/
import com.sun.crypto.provider.SunJCE;
import java.io.BufferedReader;
import java.io.FileOutputStream;
import java.io.InputStreamReader;
import java.math.BigInteger;
import java.security.KeyPair;
import java.security.KeyPairGenerator;
import java.security.SecureRandom;
import java.security.Security;
import java.security.Signature;
public class DSSDemo {
public static void main(String[] args) throws Exception {
BufferedReader br = new BufferedReader(new InputStreamReader(System.in));
Security.addProvider(new SunJCE());
KeyPairGenerator keyGen = KeyPairGenerator.getInstance("DSA", "SUN");
keyGen.initialize(512, new SecureRandom());
KeyPair keyPair = keyGen.generateKeyPair();
Signature signature = Signature.getInstance("SHA1withDSA", "SUN");
signature.initSign(keyPair.getPrivate(), new SecureRandom());
String inputMessage = br.readLine();
byte[] message = inputMessage.getBytes();
signature.update(message);
byte[] sigBytes = signature.sign();
BigInteger signedMessage = new BigInteger(1, sigBytes);](https://image.slidesharecdn.com/it6712labmanual-170818053823/85/IT6712-lab-manual-36-320.jpg)