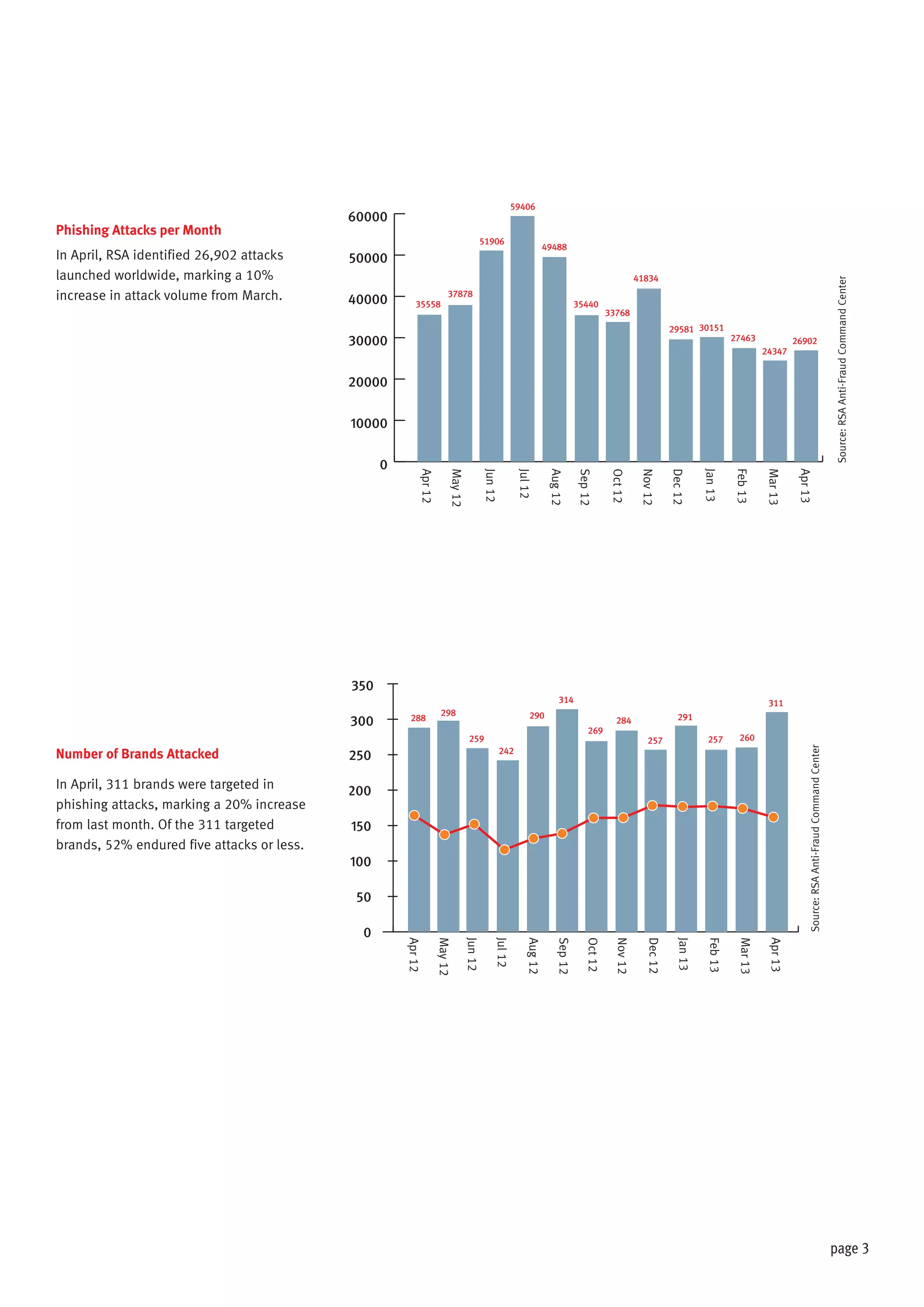
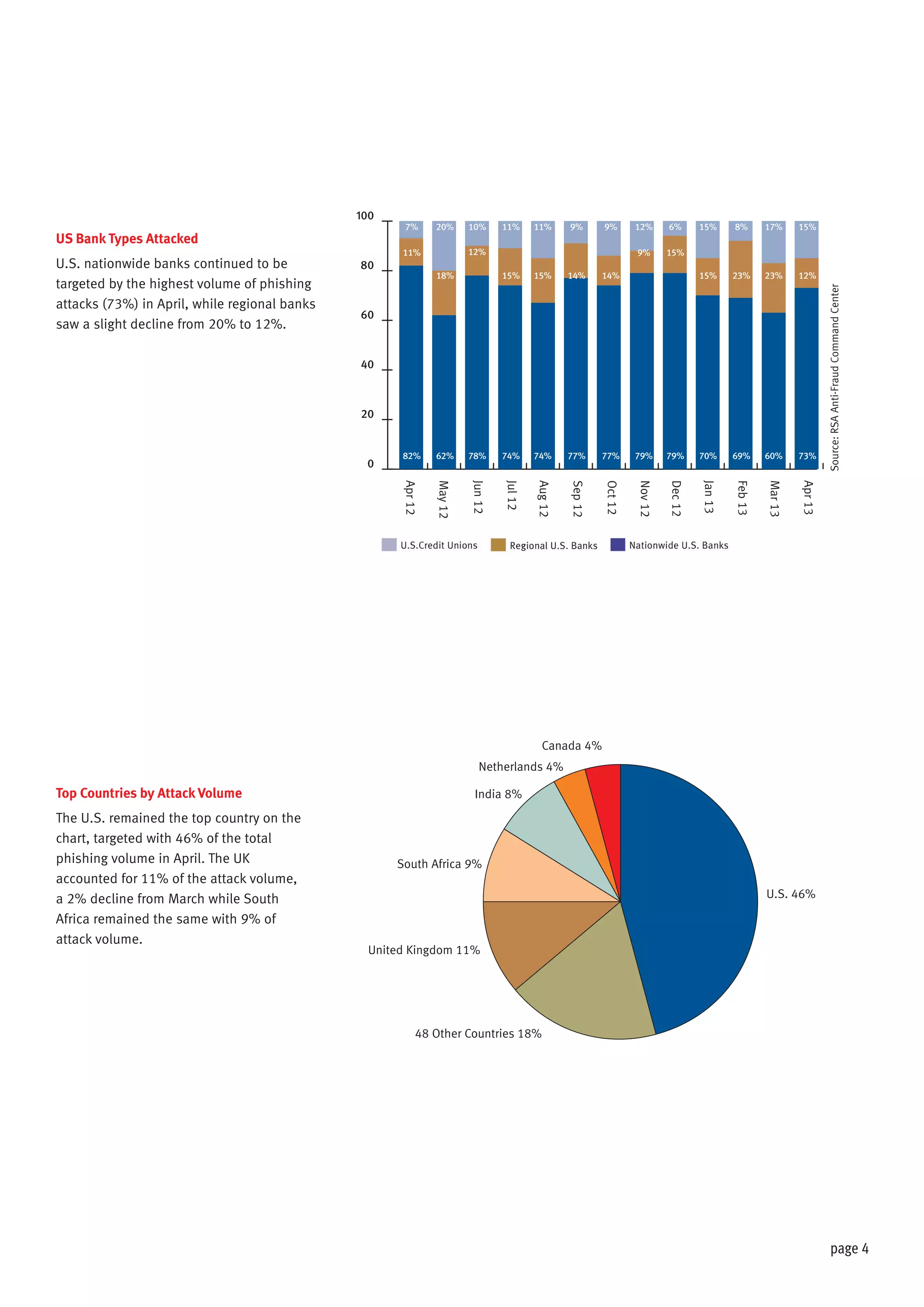
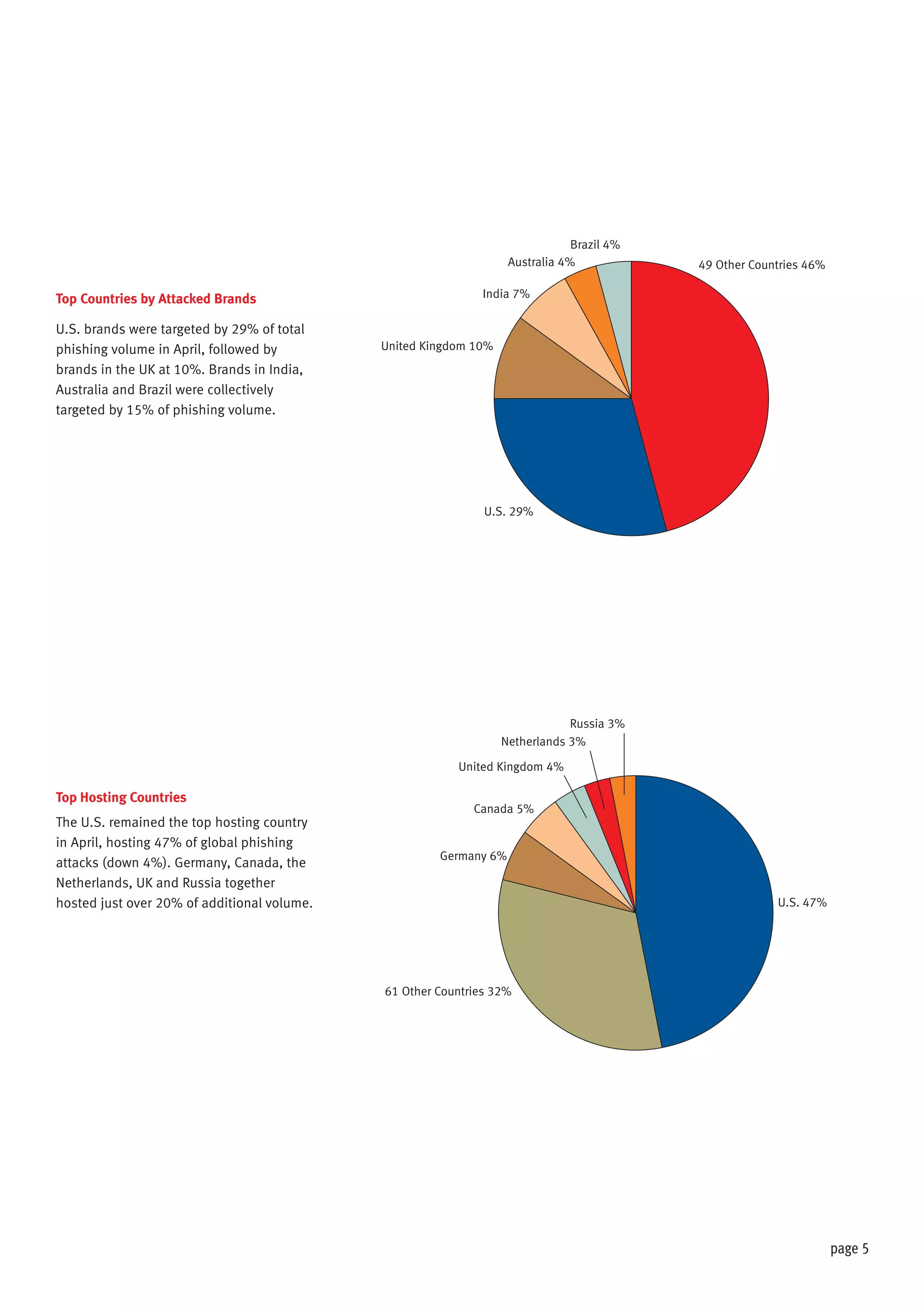
The document discusses the impact of hacktivism on cybersecurity, highlighting how attacks aimed at large entities often result in the exposure of sensitive user data that can be exploited by fraudsters. It outlines the increasing trend of phishing attacks, particularly following substantial data breaches, and identifies the United States as the primary target for such attacks. The report presents statistical data on phishing incidents and the demographics of affected brands and countries in 2013.