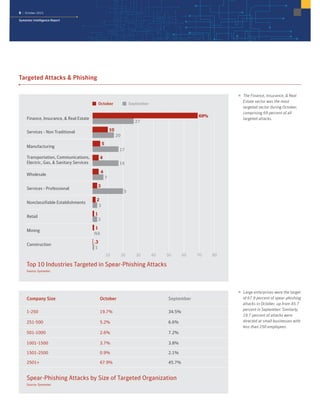
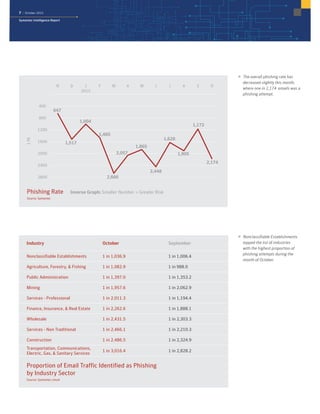
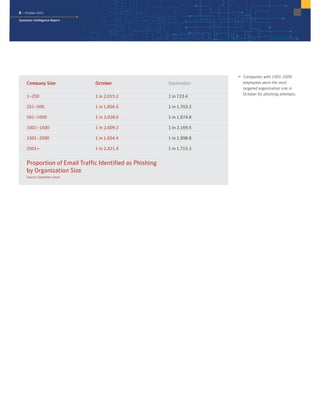
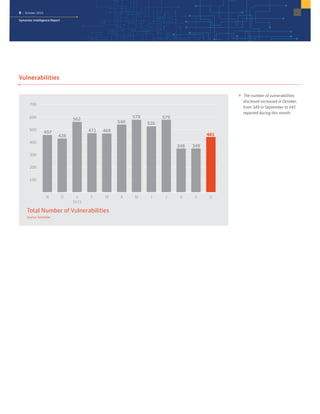
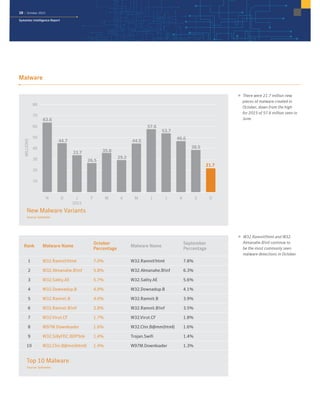
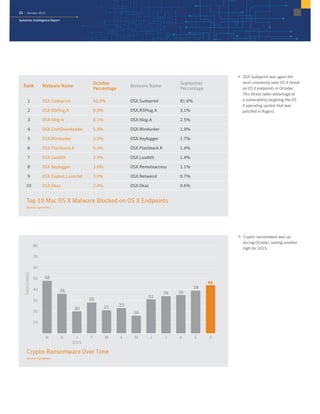
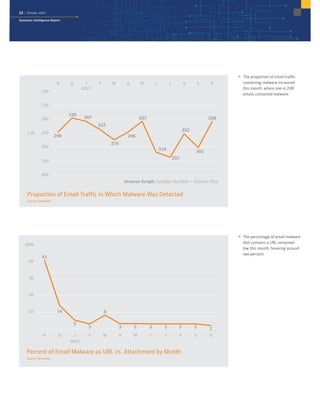
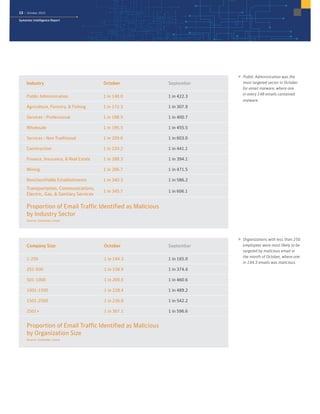
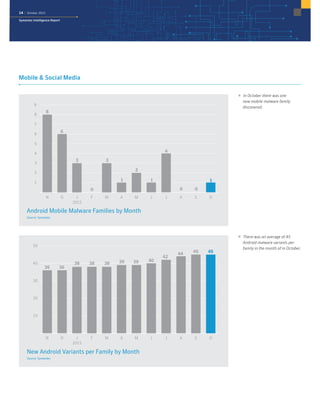
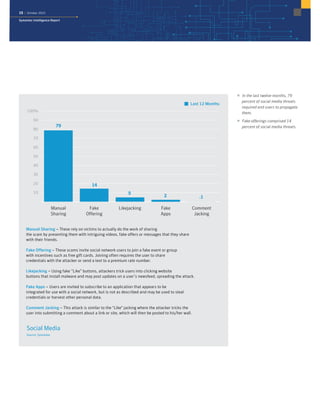
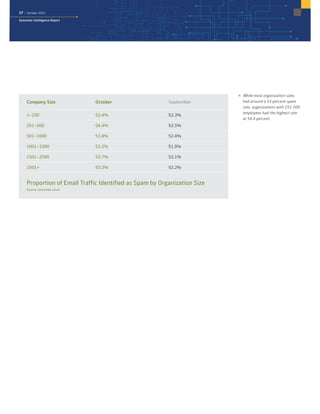
The October 2015 Symantec Intelligence Report highlights a rise in disclosed vulnerabilities, totaling 441, while the creation of new malware variants decreased to 21.7 million. Crypto-ransomware attacks reached an all-time high for 2015, and spam rates increased to 53.5 percent. The finance, insurance, and real estate sectors were the most targeted, with large enterprises experiencing a significant rise in spear-phishing attempts.