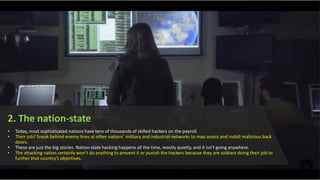
The document discusses the evolution of hackers from juvenile pranksters to sophisticated criminals with various motivations, including financial gain, corporate espionage, and political activism. It categorizes hackers into 10 types, including bank robbers, nation-state operatives, corporate spies, and hacktivists, outlining their methods and objectives. The document emphasizes the need for strong cybersecurity measures to combat these diverse threats.