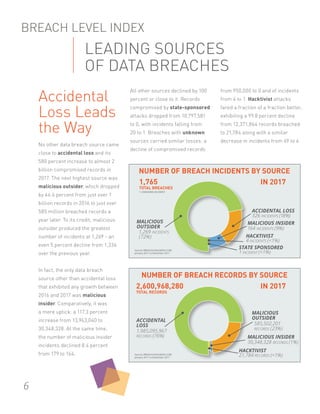
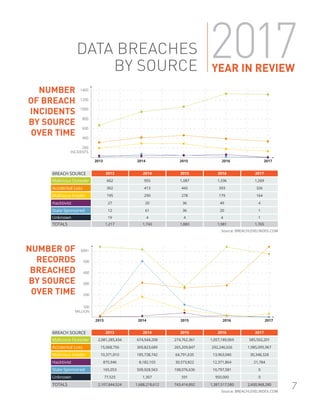
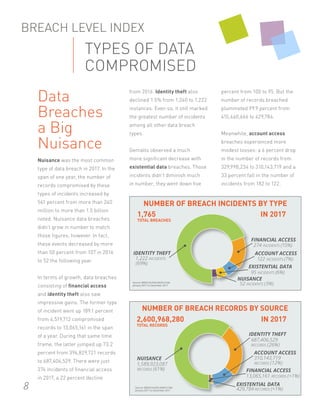
In 2017, there were over 1,765 data breach incidents compromising over 2.6 billion records. The largest breaches stemmed from poor security practices and accidental data exposures, rather than external hacking attacks. Notable breaches included the Equifax breach of 147 million Americans' personal data due to unpatched vulnerabilities, and accidental exposures of personal data by Deep Root Analytics, River City Media, and Alteryx due to misconfigured cloud storage settings. Looking ahead, new regulations like the EU's GDPR have the potential to increase transparency around data breaches.