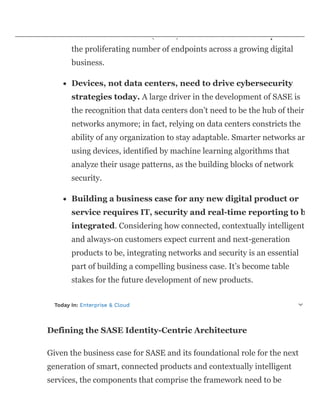
The document discusses the importance of integrating network technology and security, emphasizing that identities are now the new security perimeter. Gartner's emerging framework, Secure Access Service Edge (SASE), is highlighted as crucial for enabling real-time, flexible access for modern digital enterprises. The need for a robust identity-centric architecture that combines various network security components is essential for adapting to evolving business models and customer expectations.