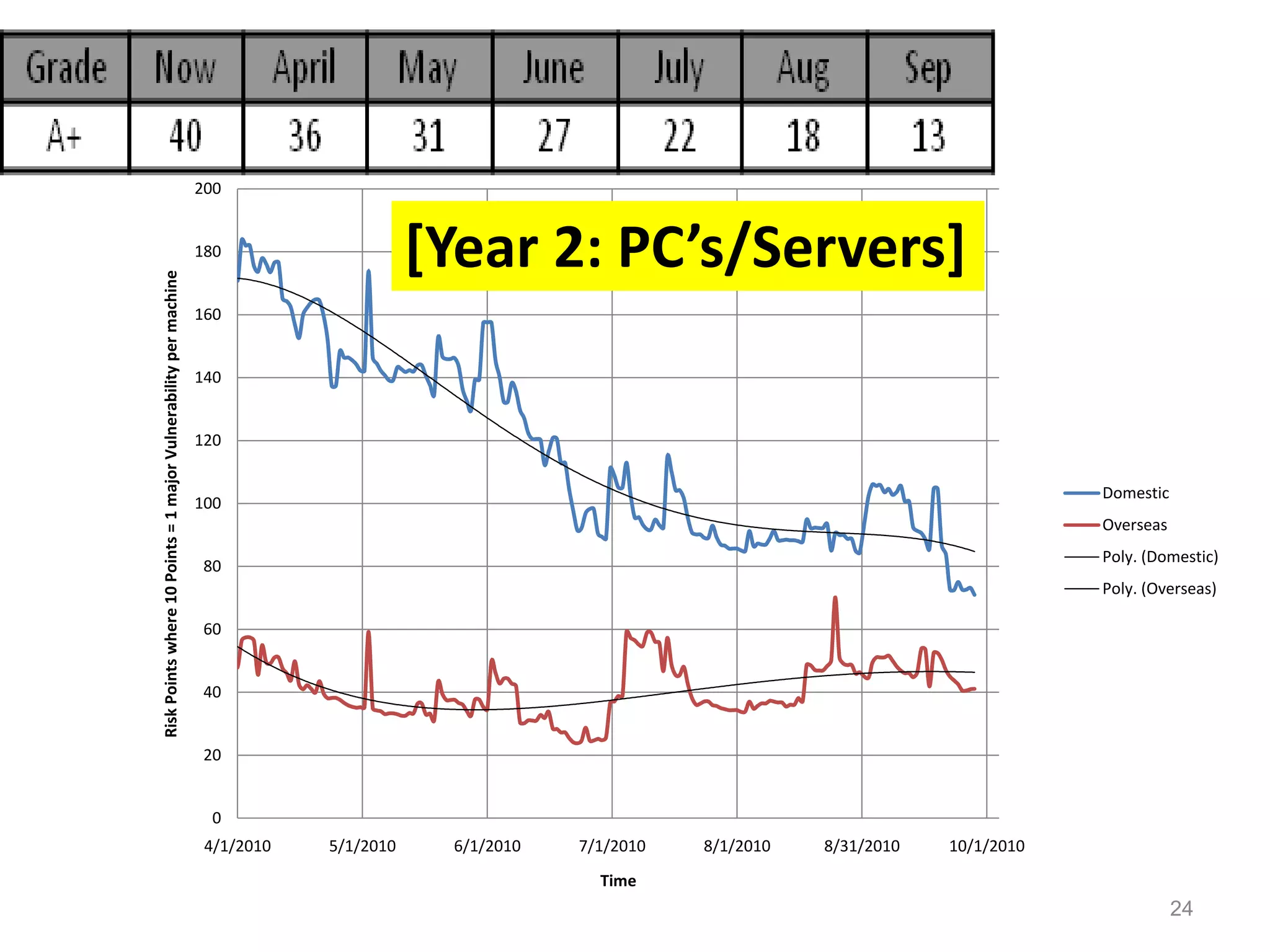
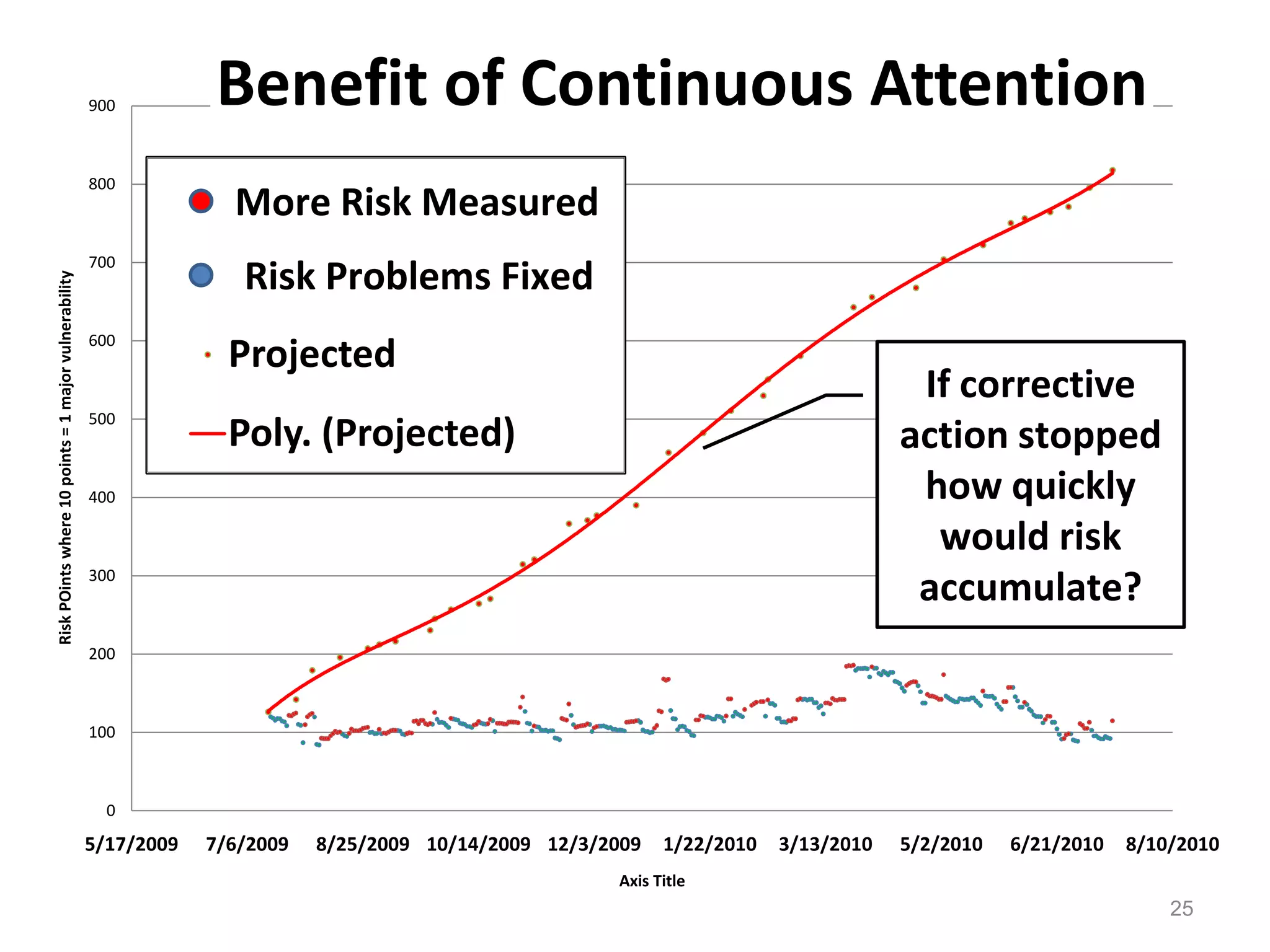
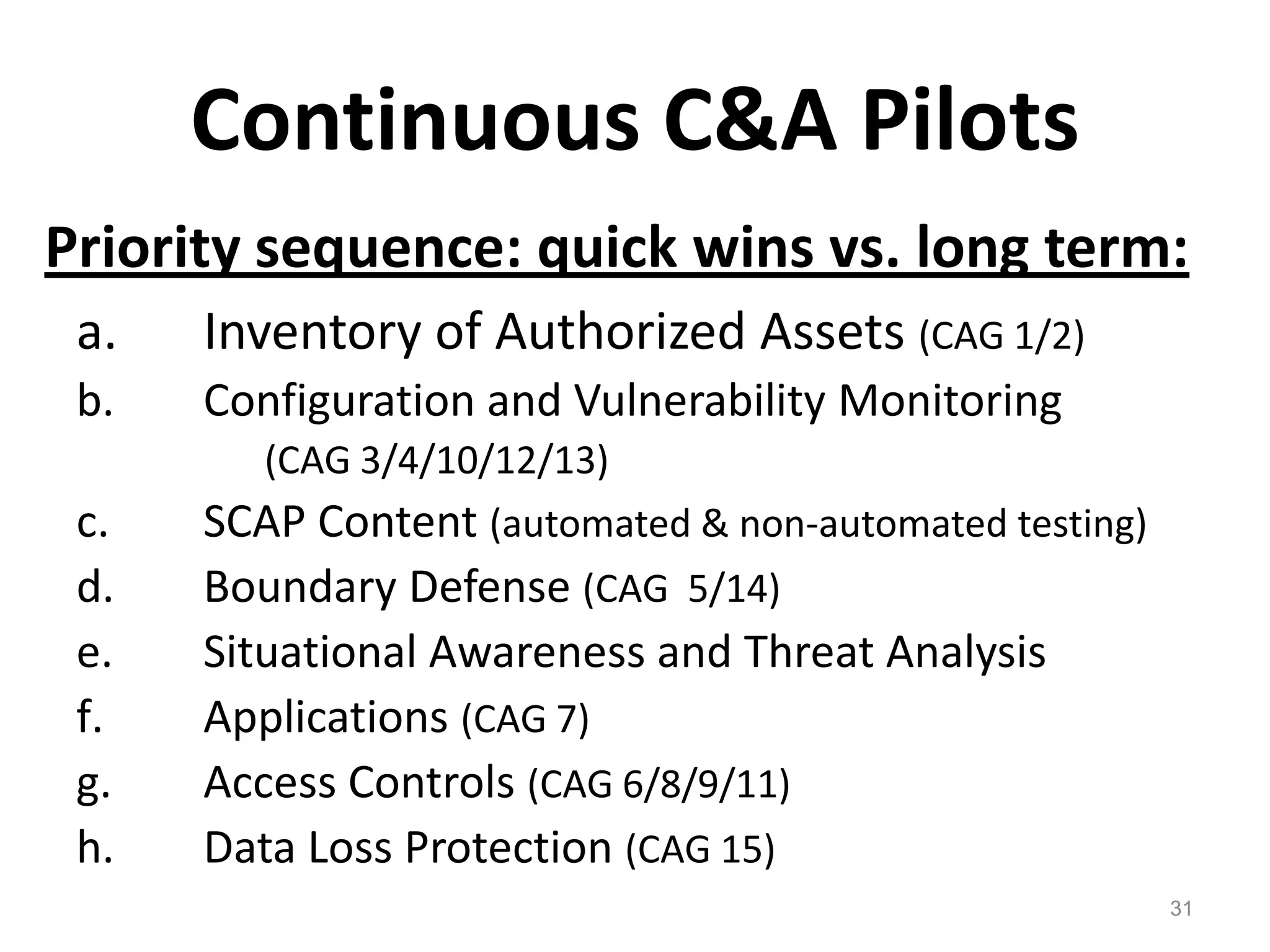
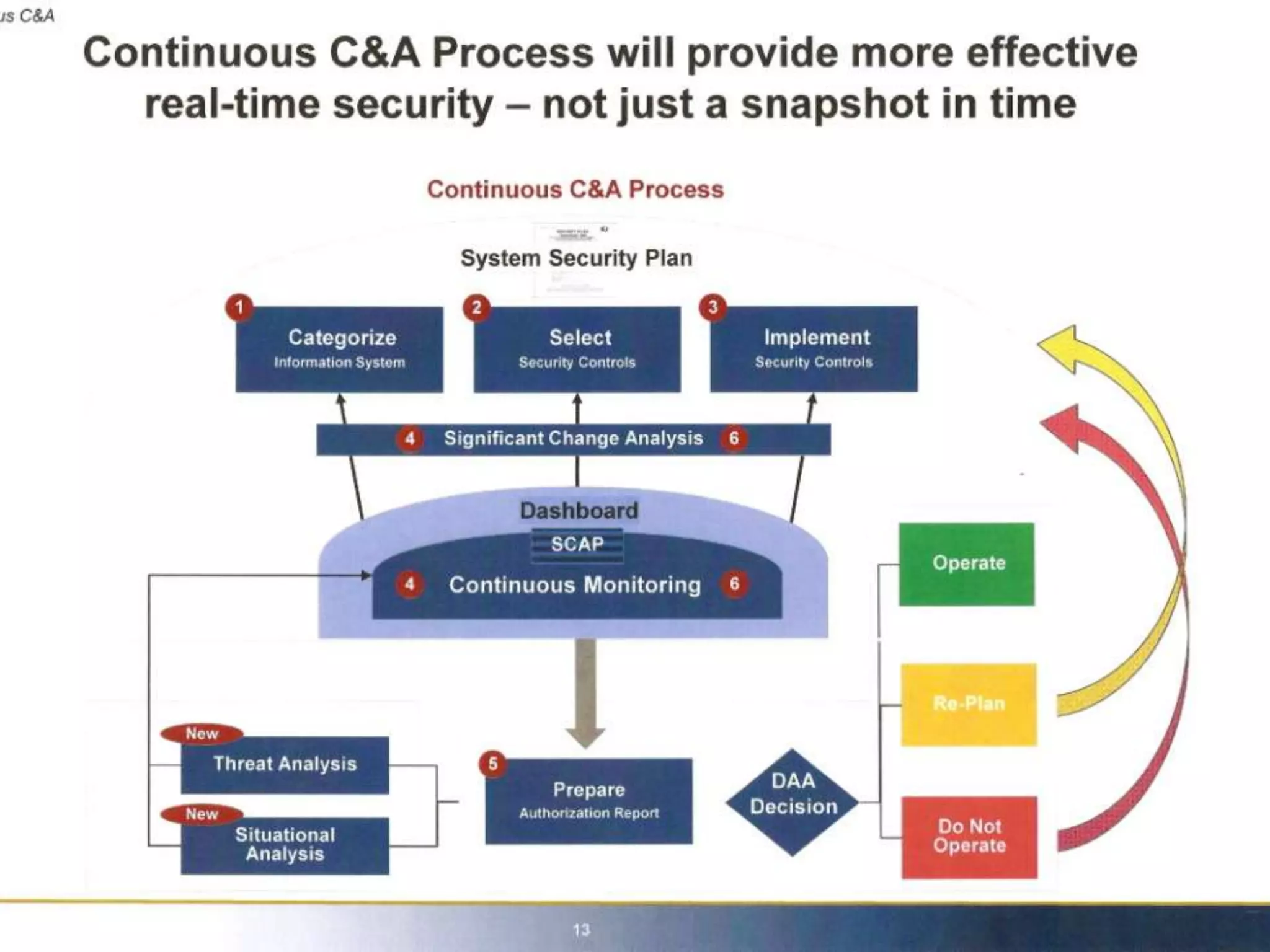
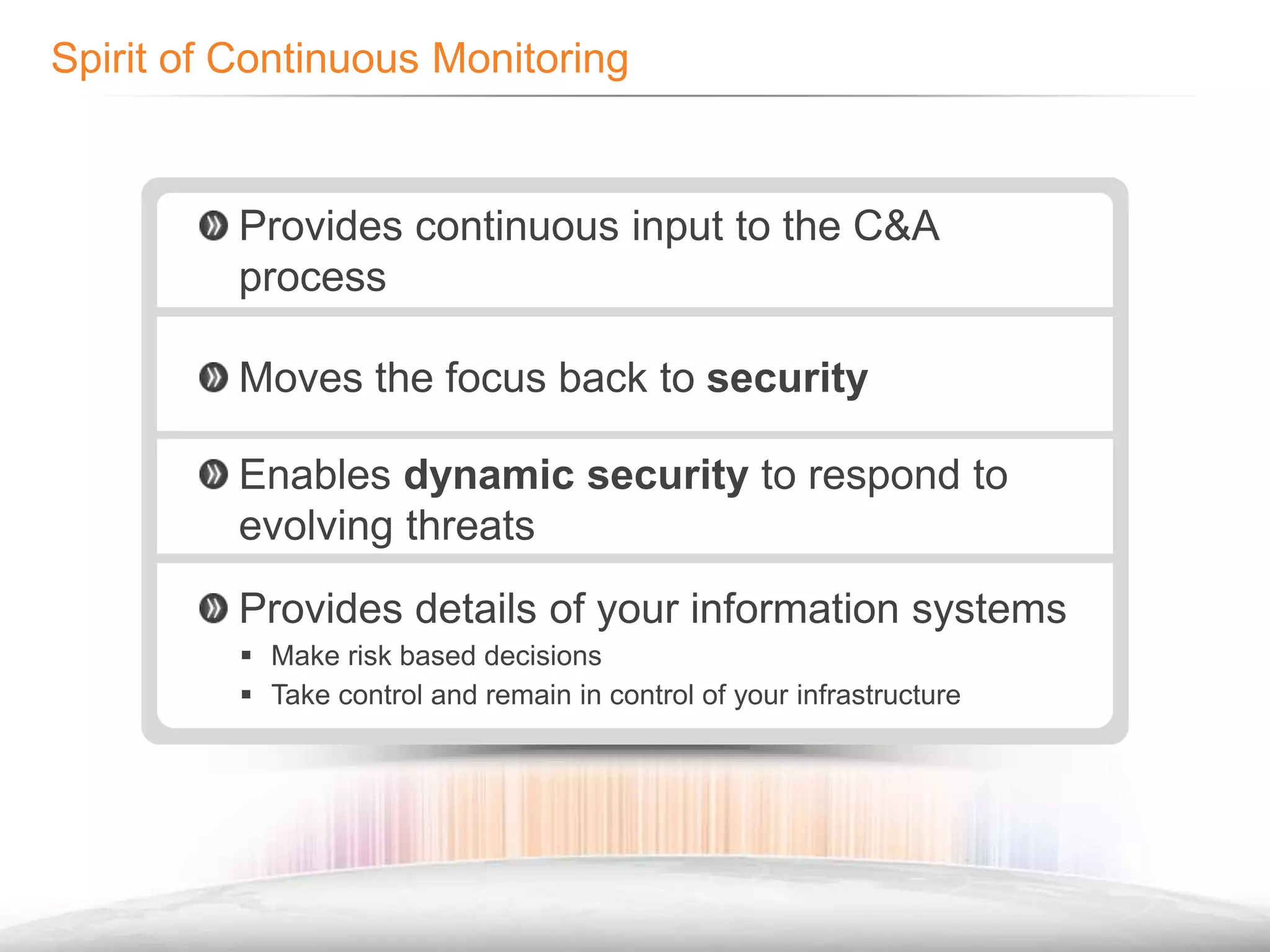
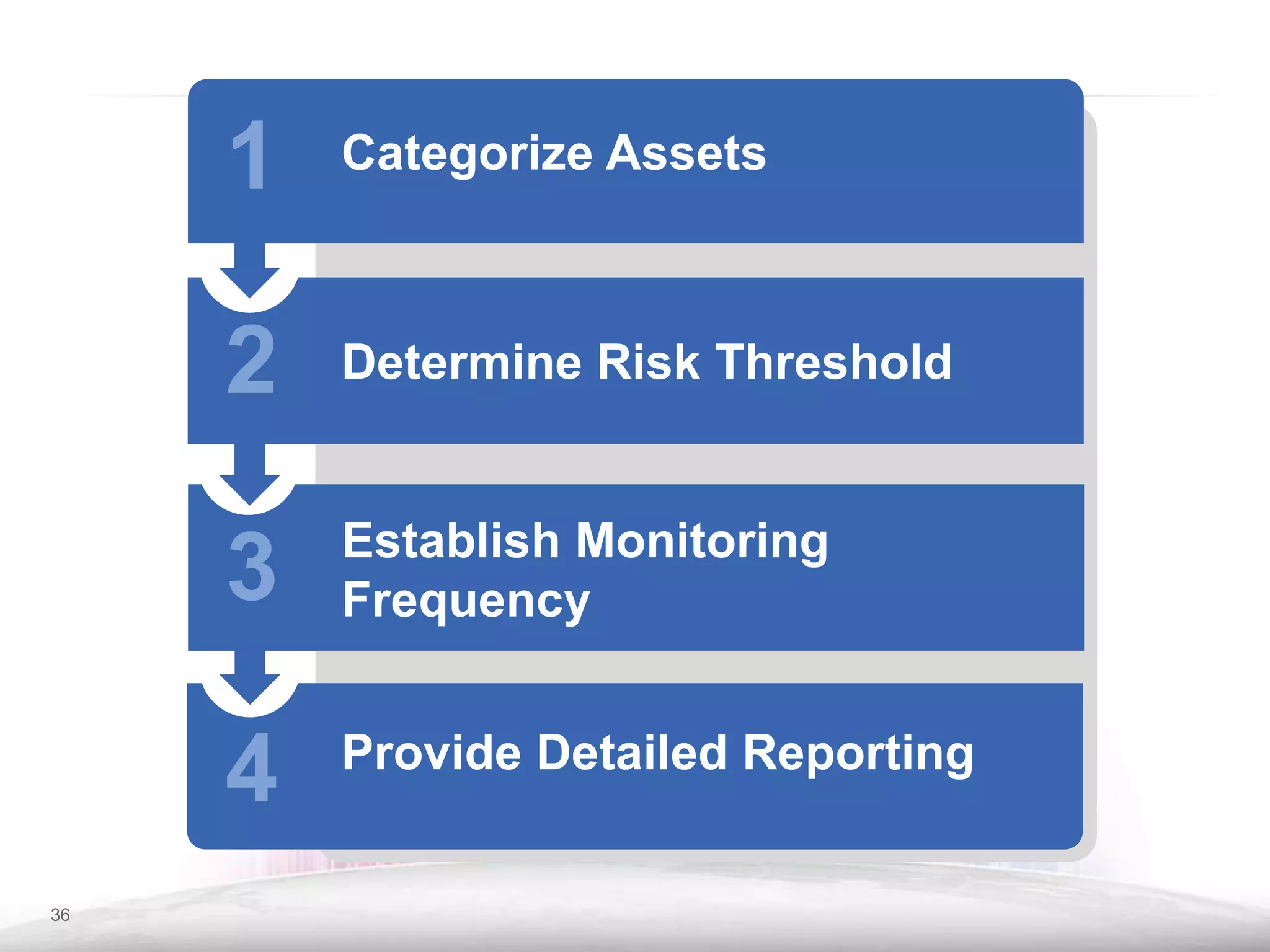
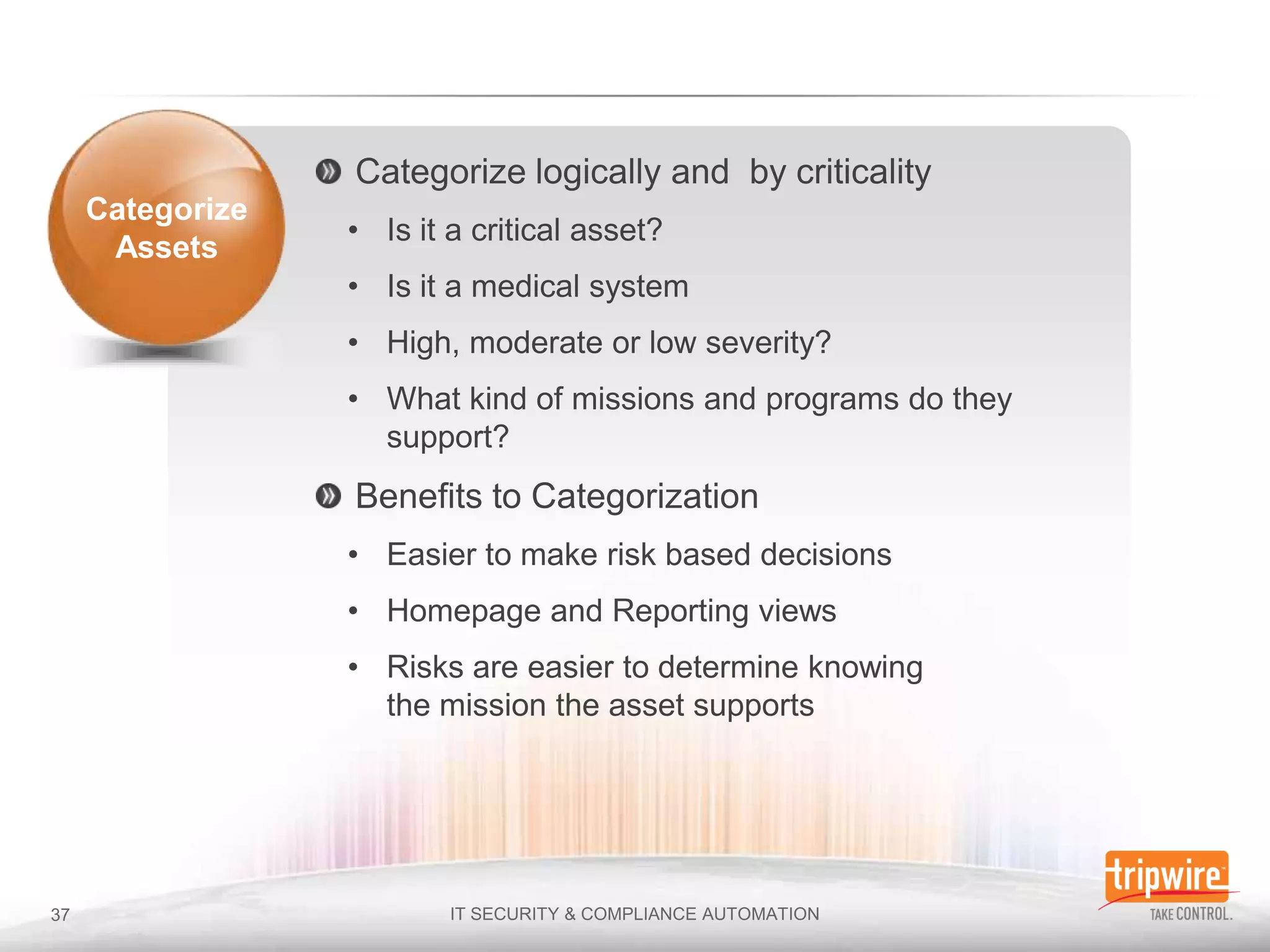
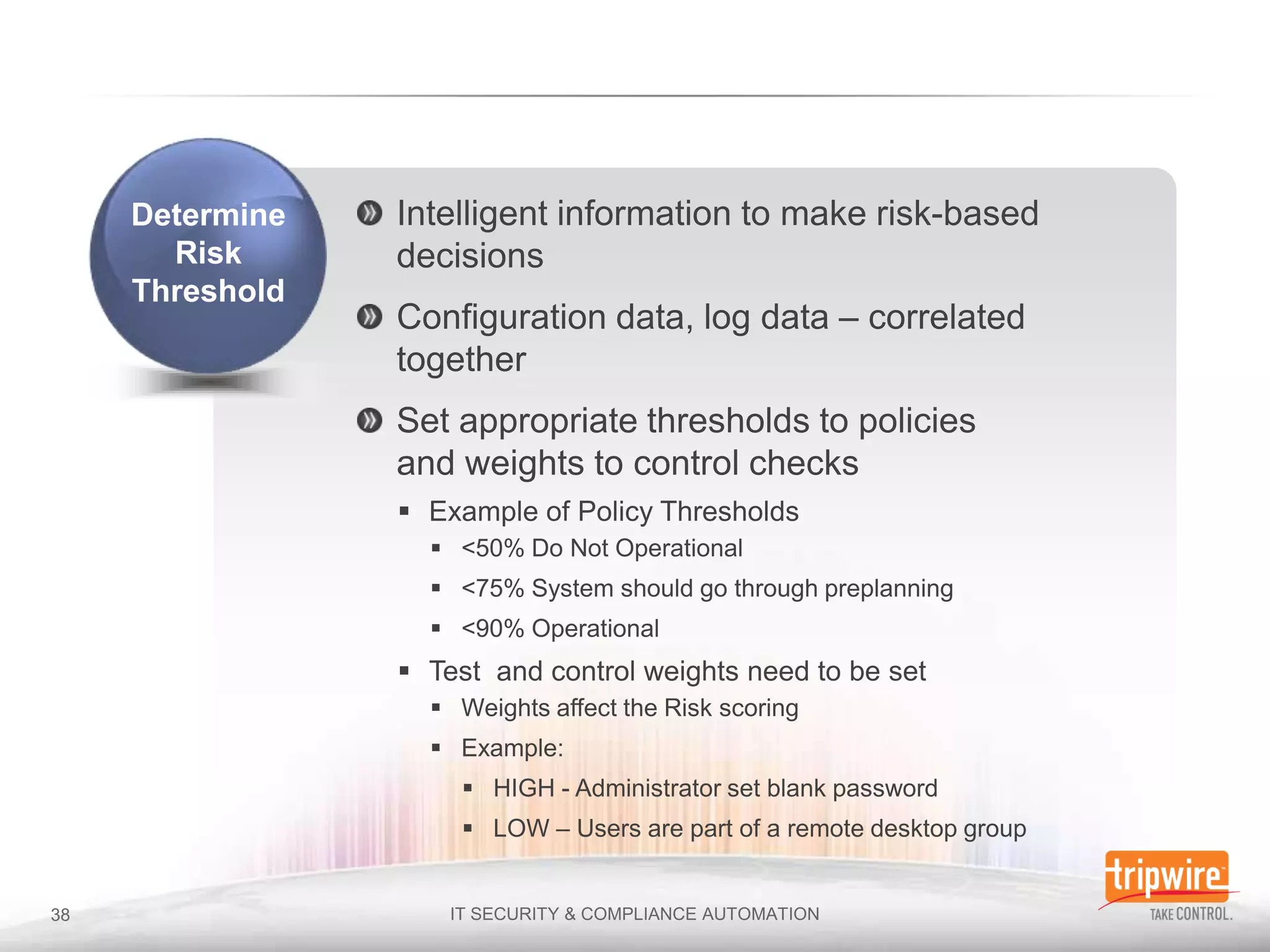
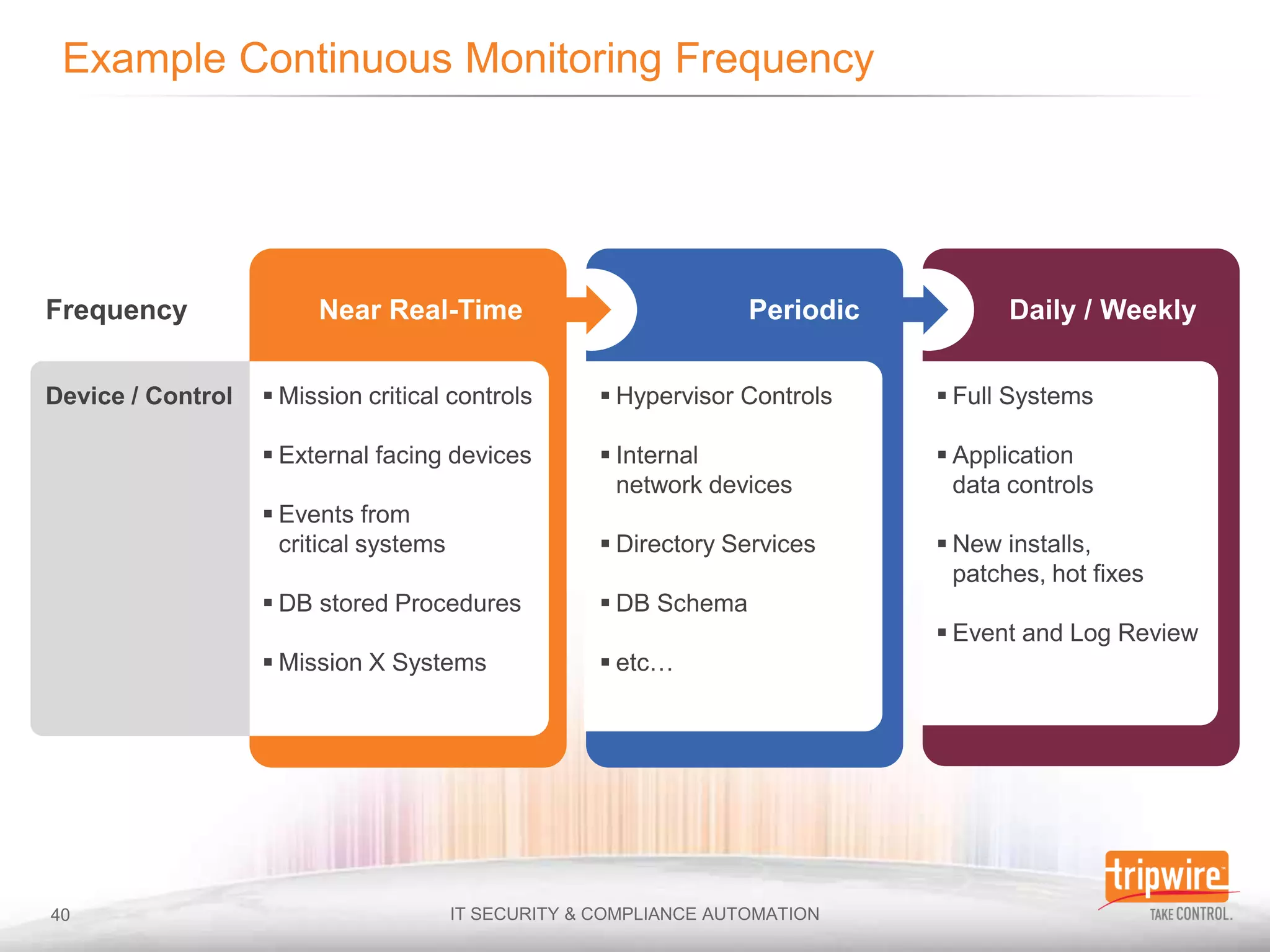
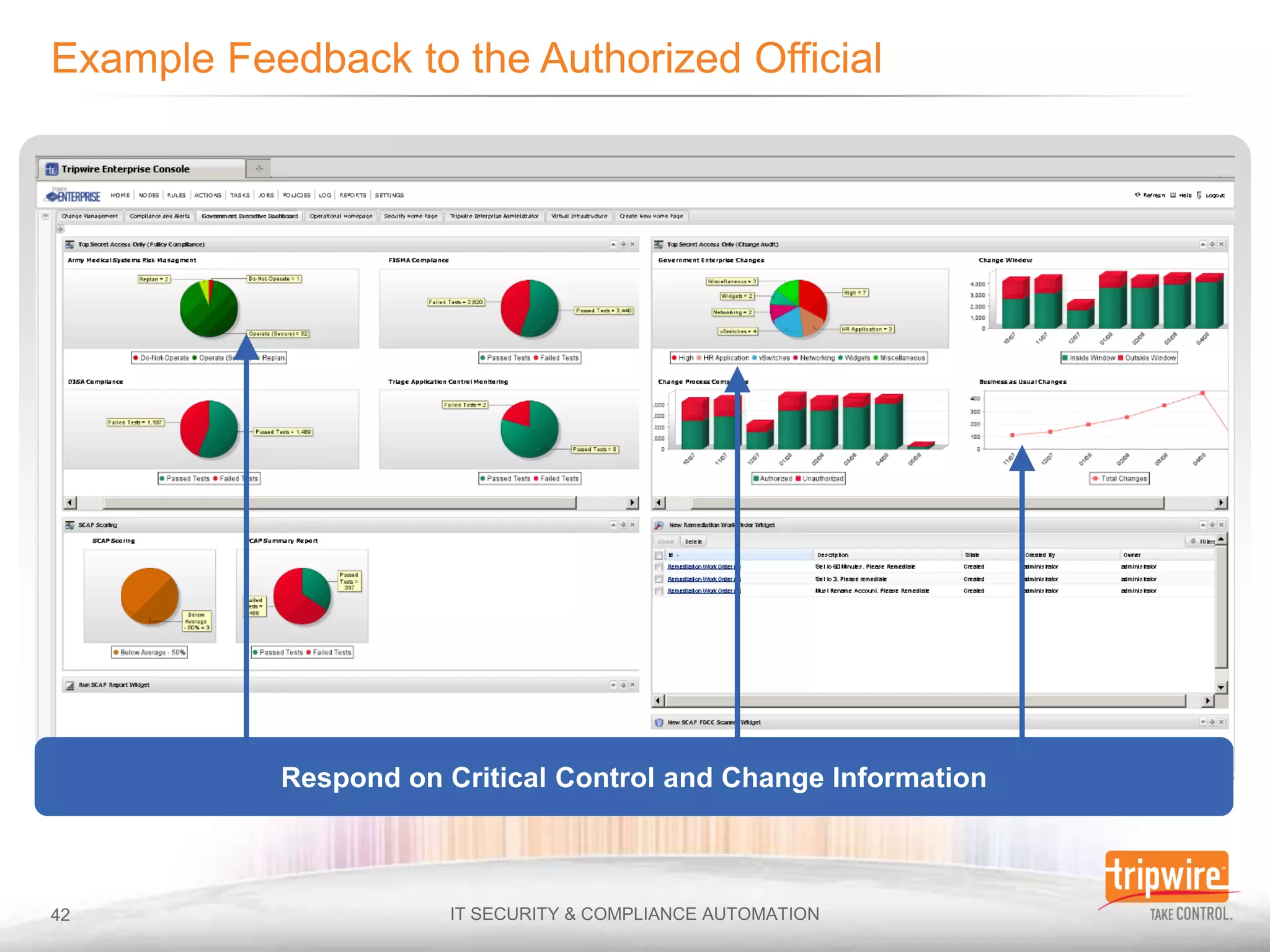
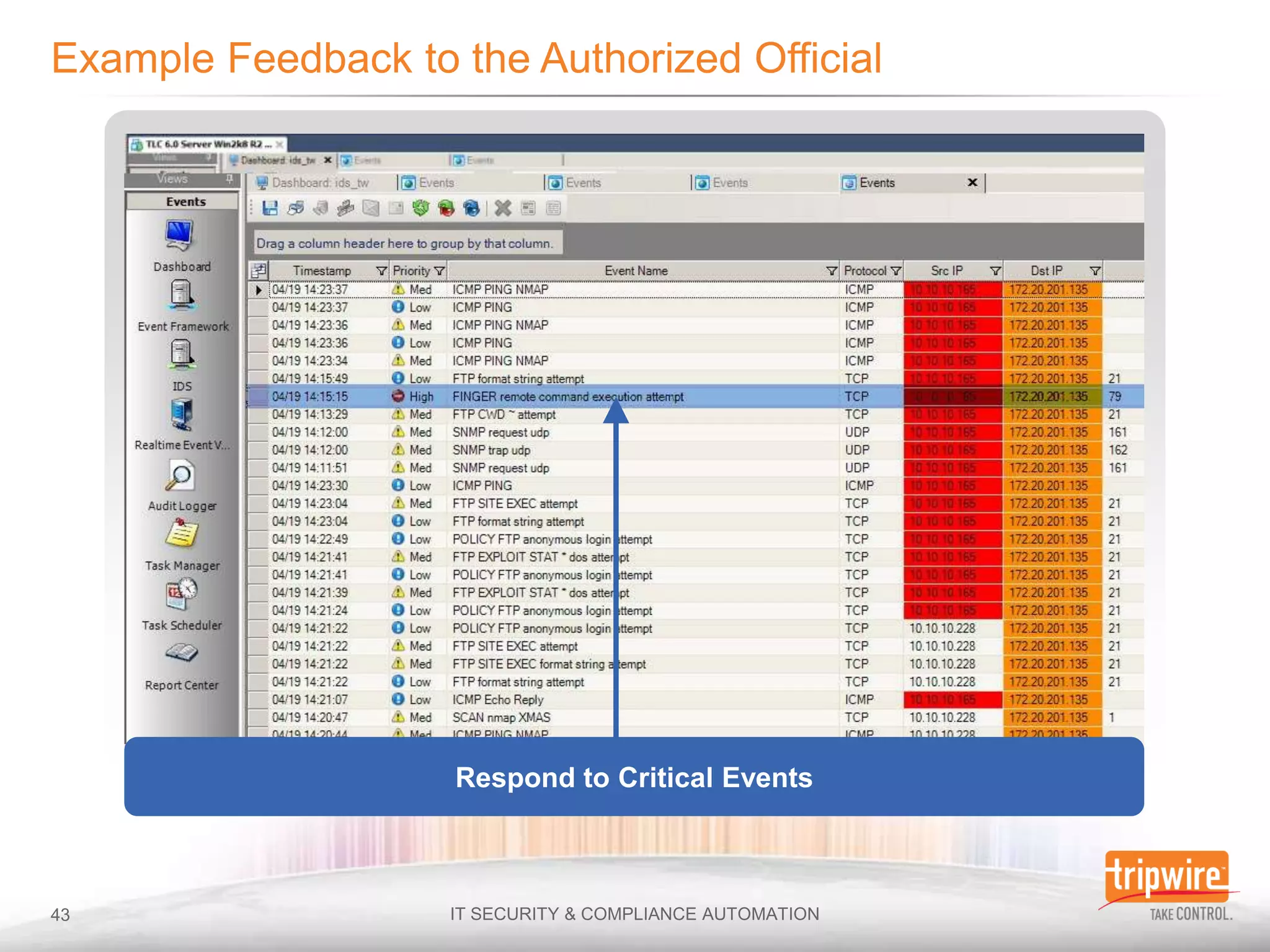
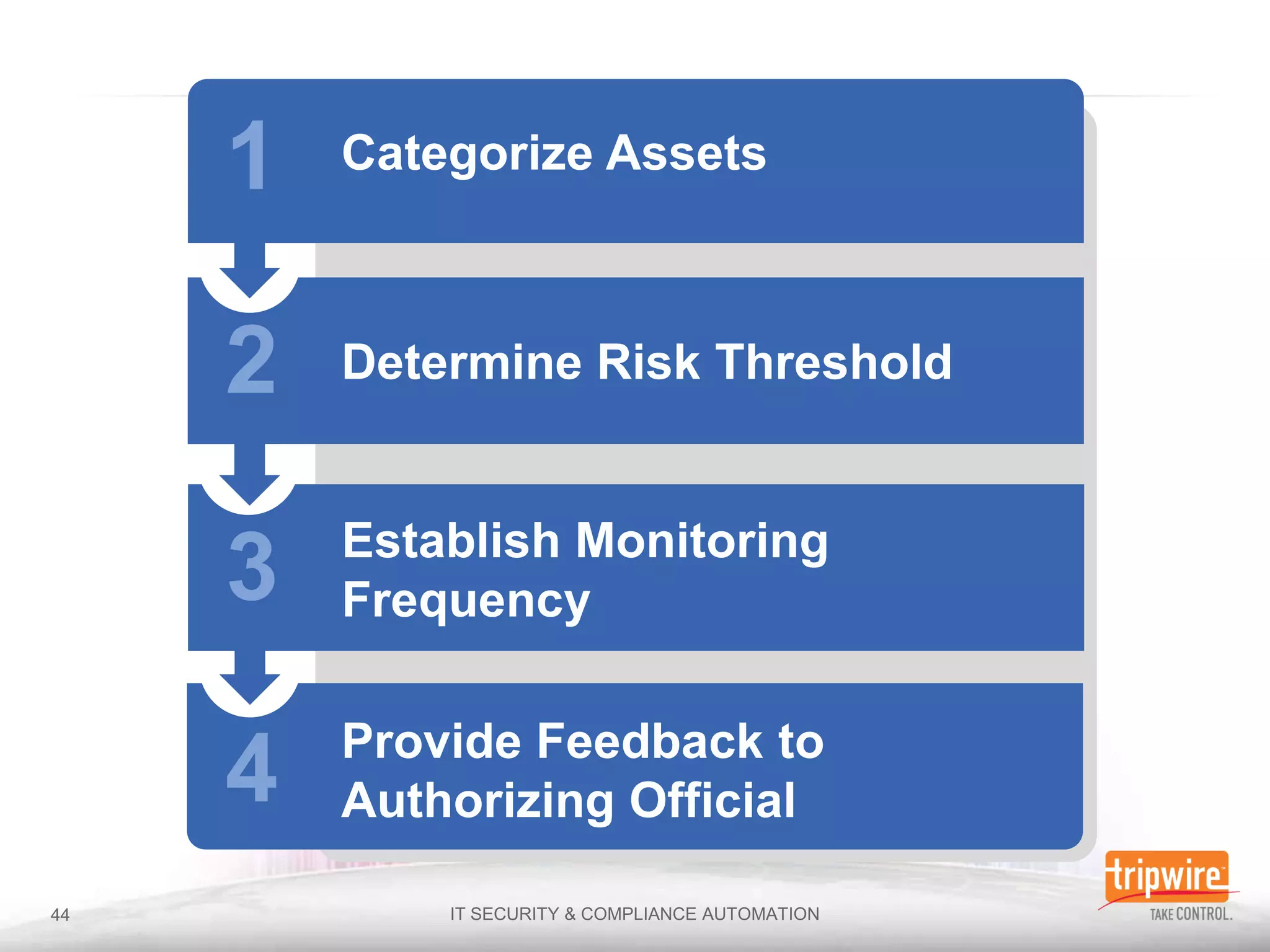
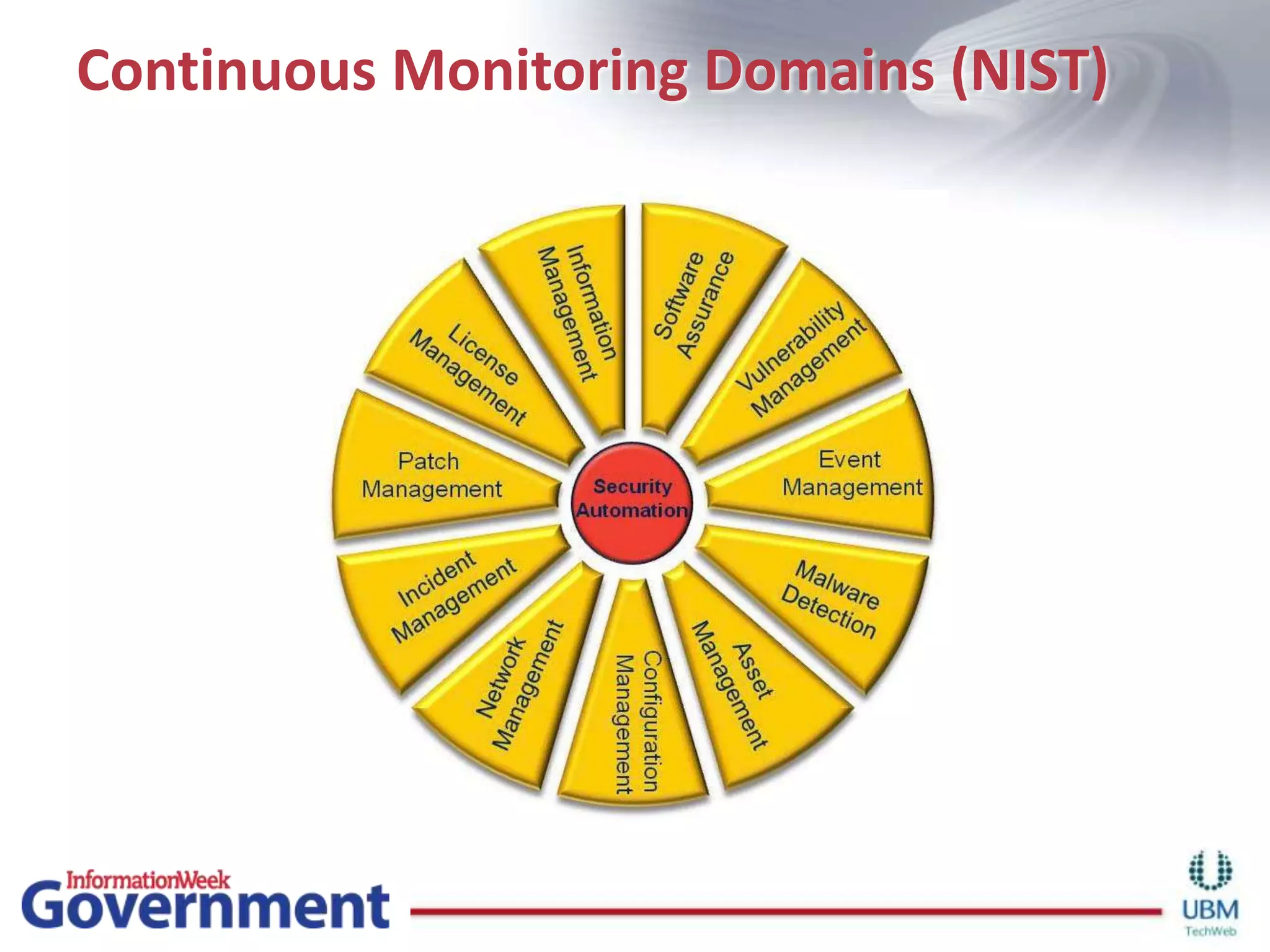
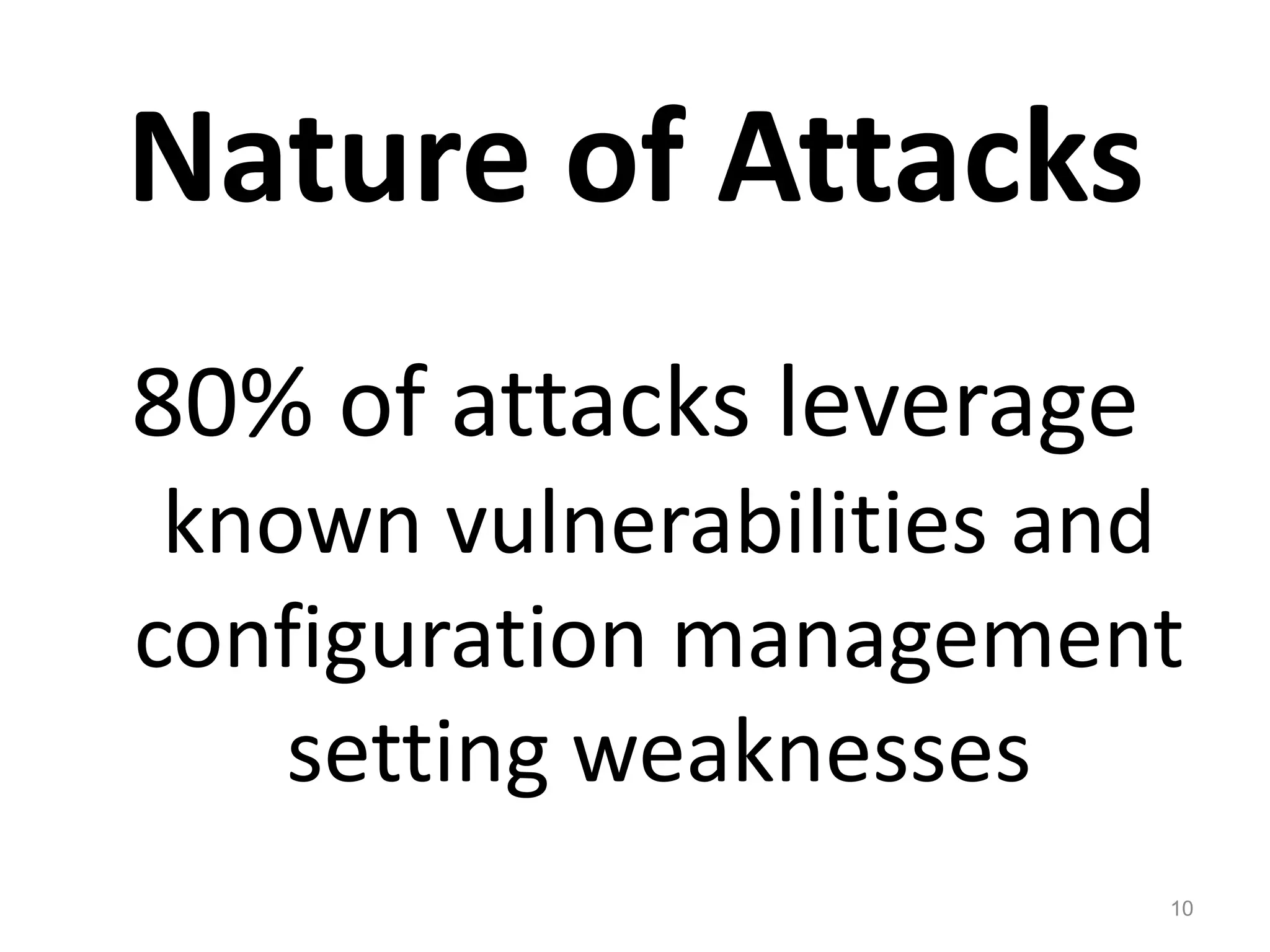
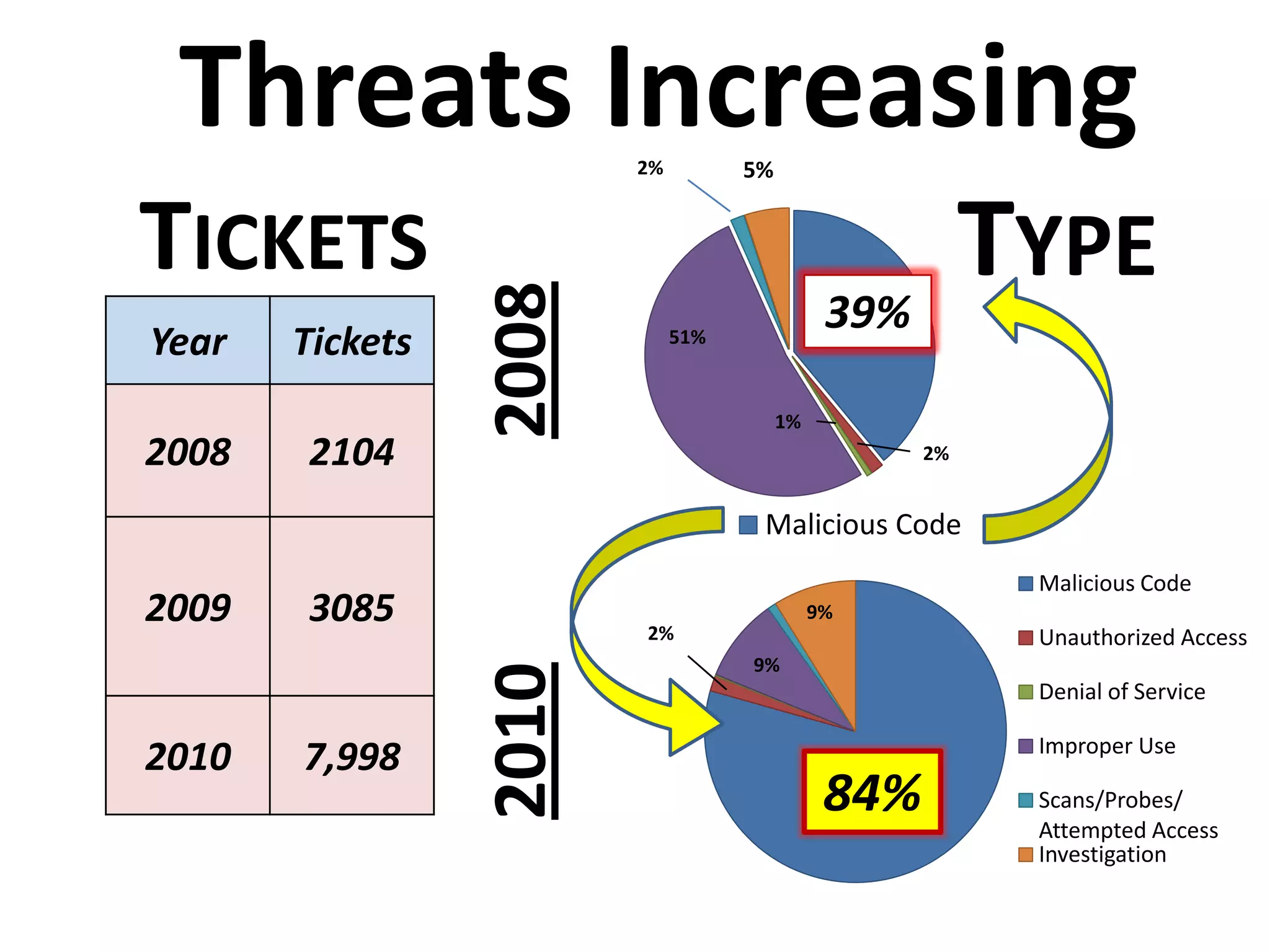
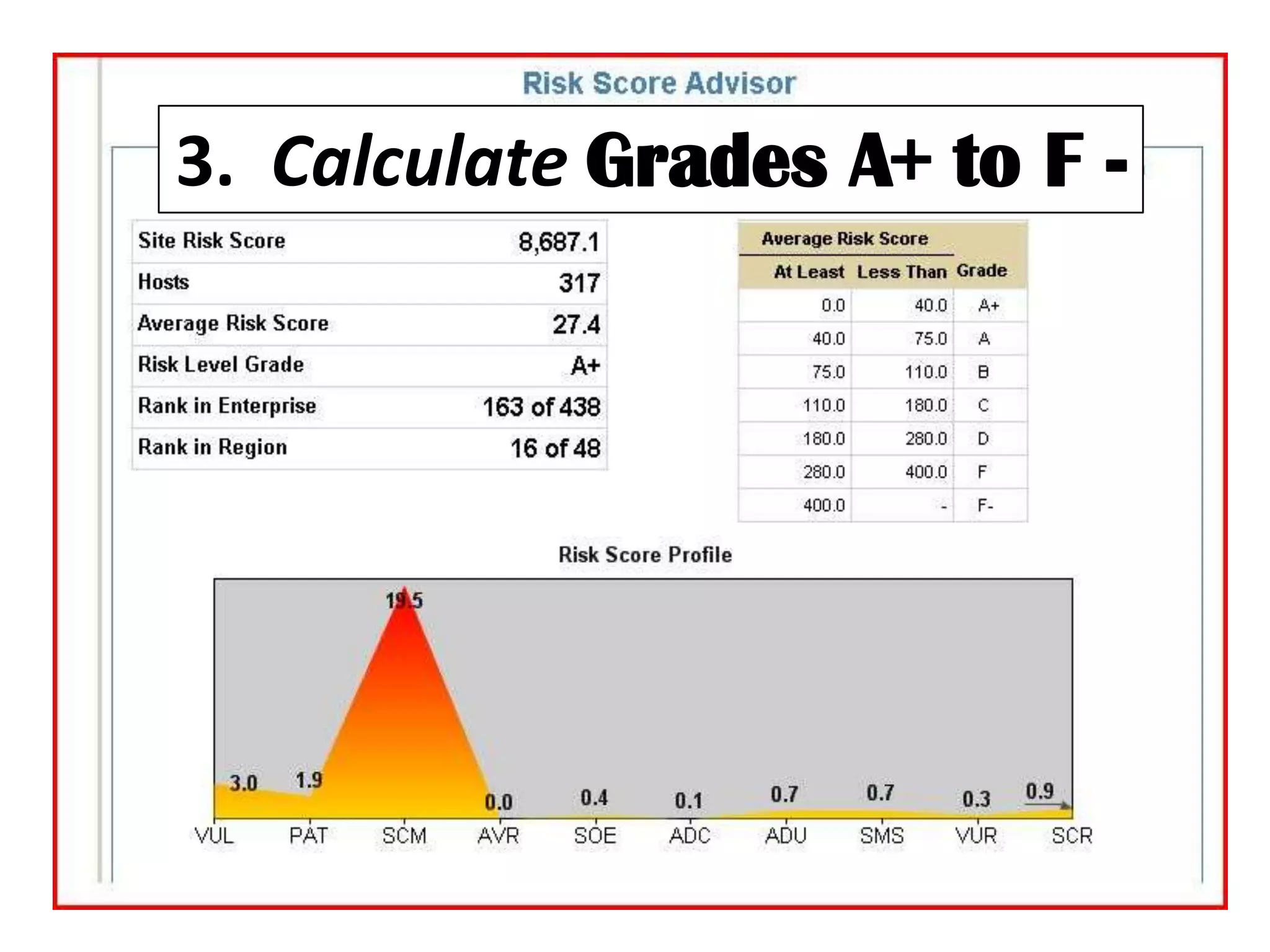
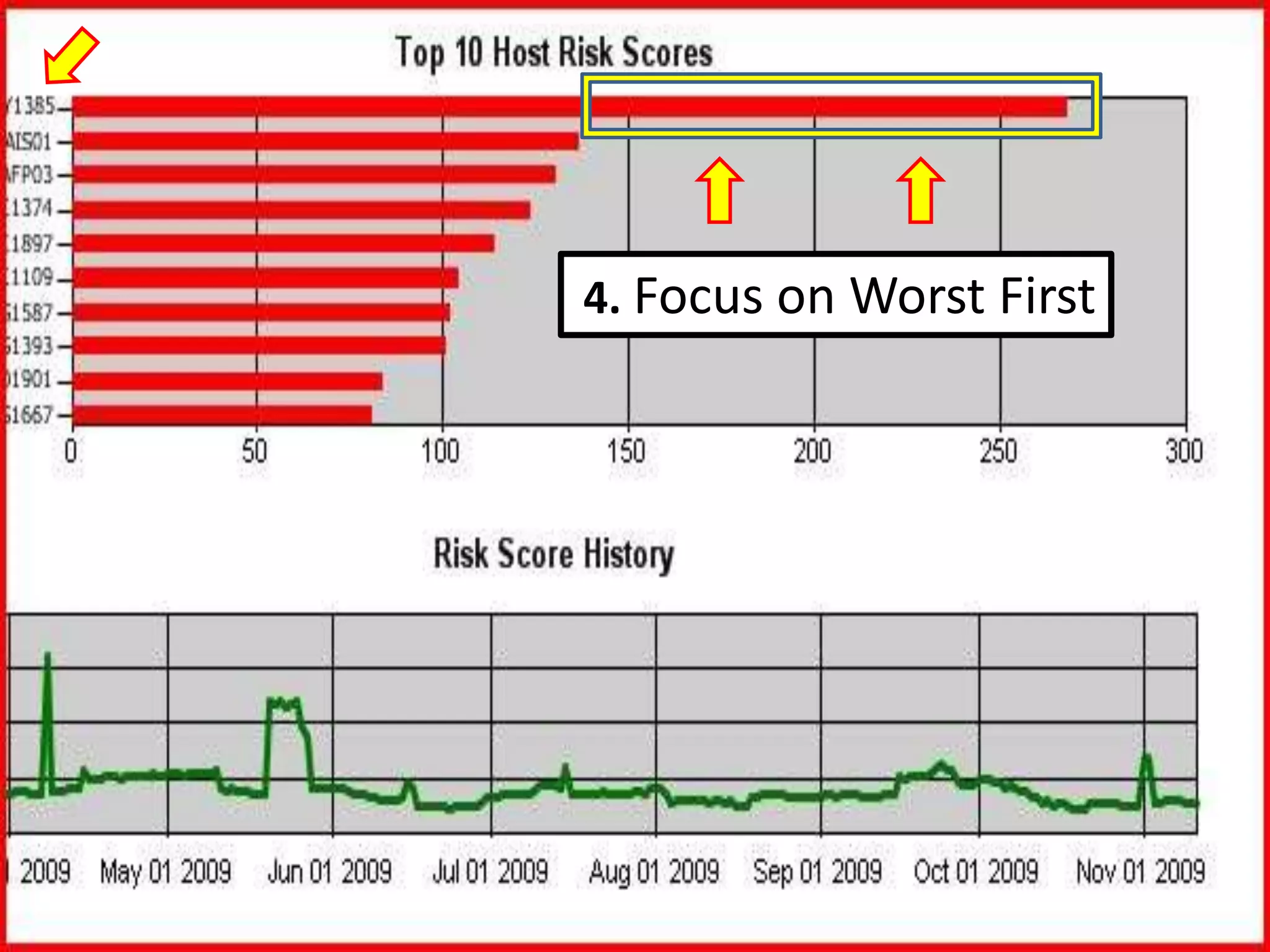
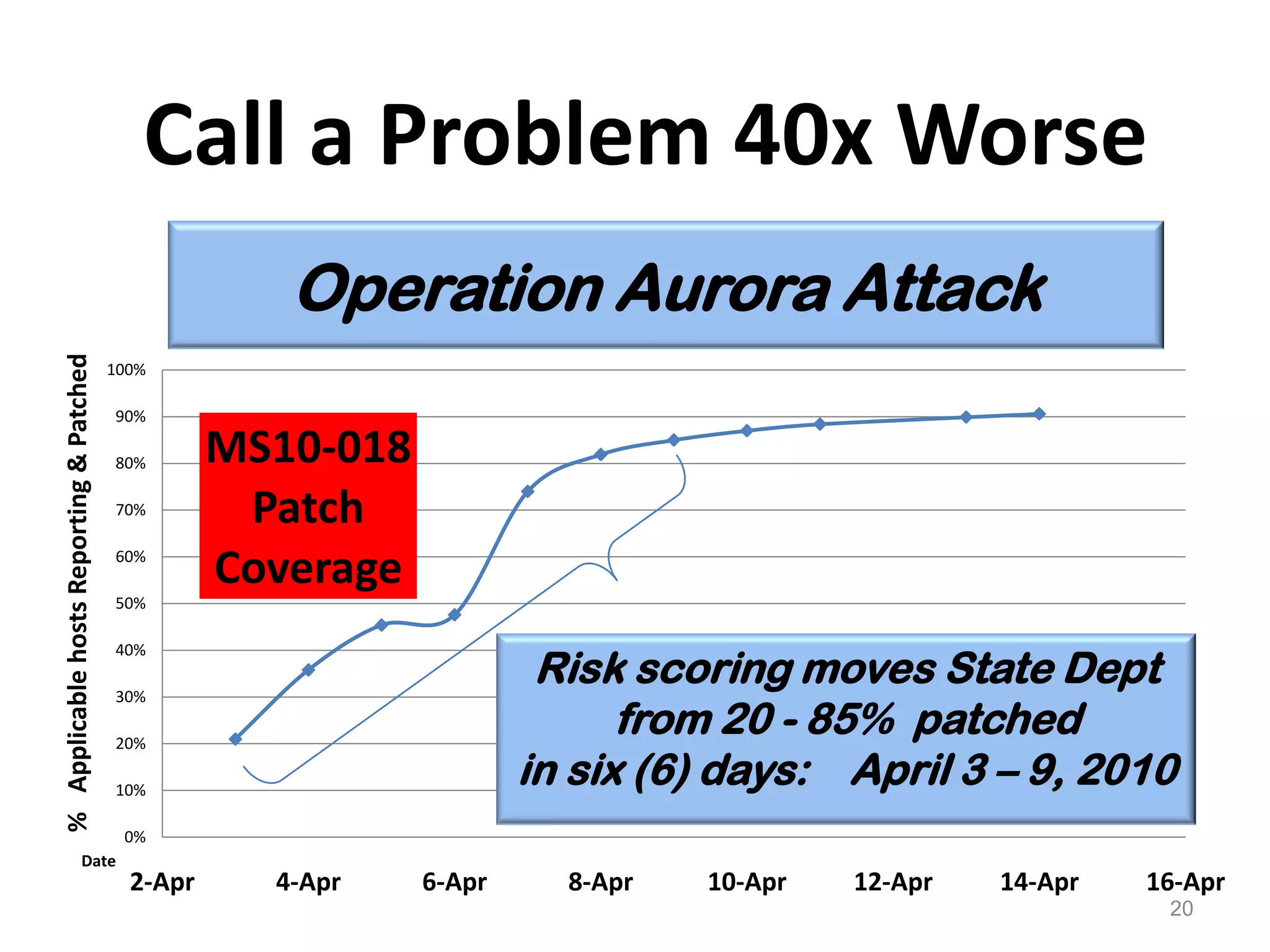
The document discusses the importance of continuous monitoring in information security, emphasizing its role in risk management and operational security through real-time monitoring and data analysis. Key points include the need for organizations to integrate continuous monitoring into their IT budgets and practices, leveraging data for rapid risk assessment and management. Best practices outlined include asset categorization, risk threshold determination, monitoring frequency, and detailed reporting to enhance security responses.






![How: 1. Narrow Aim13[11 months before Feb 09]](https://image.slidesharecdn.com/02142011tripwireandinformationweekgovwebcastfinal2-110620131845-phpapp01/75/Developing-a-Continuous-Monitoring-Action-Plan-13-2048.jpg)

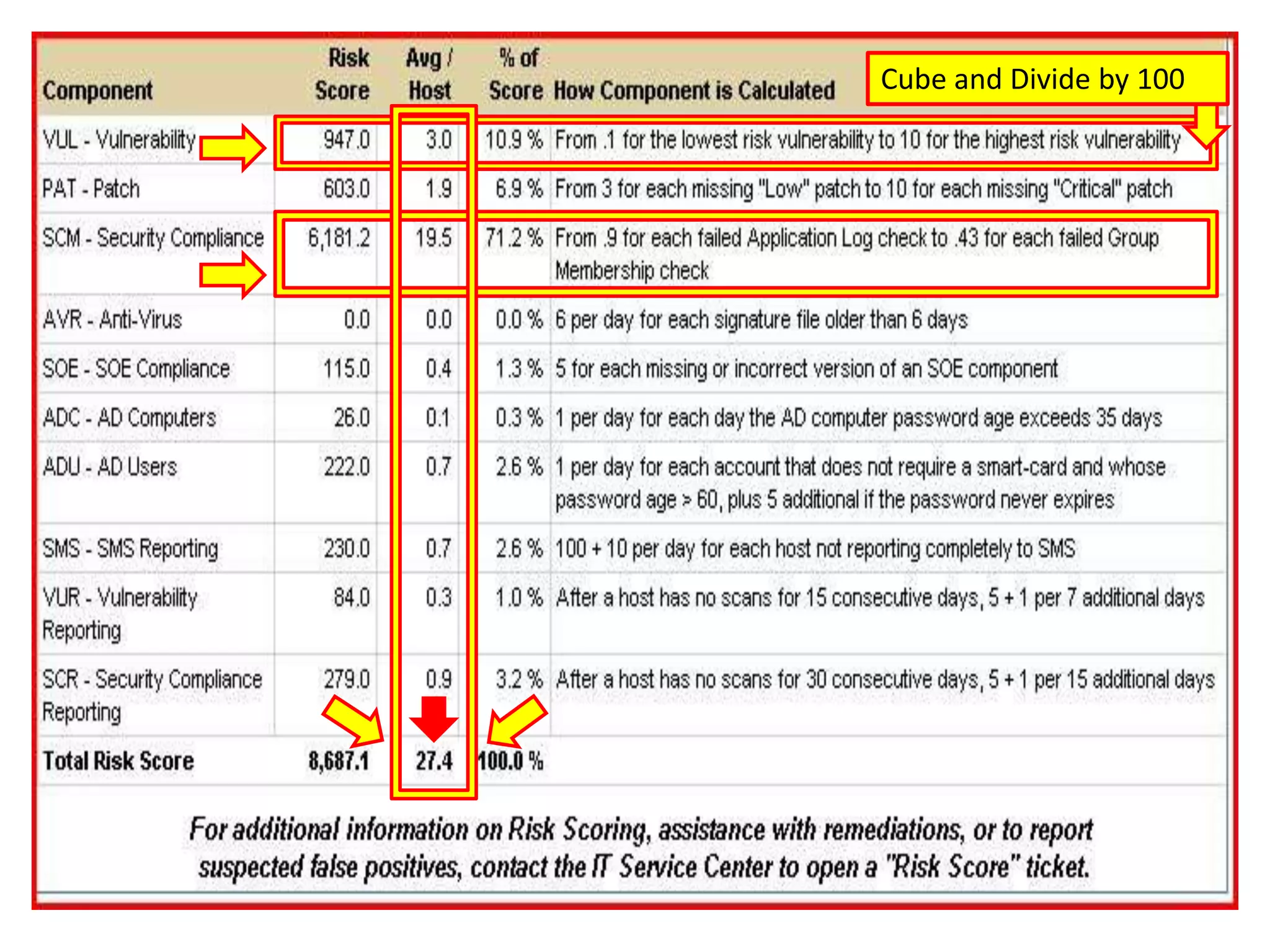
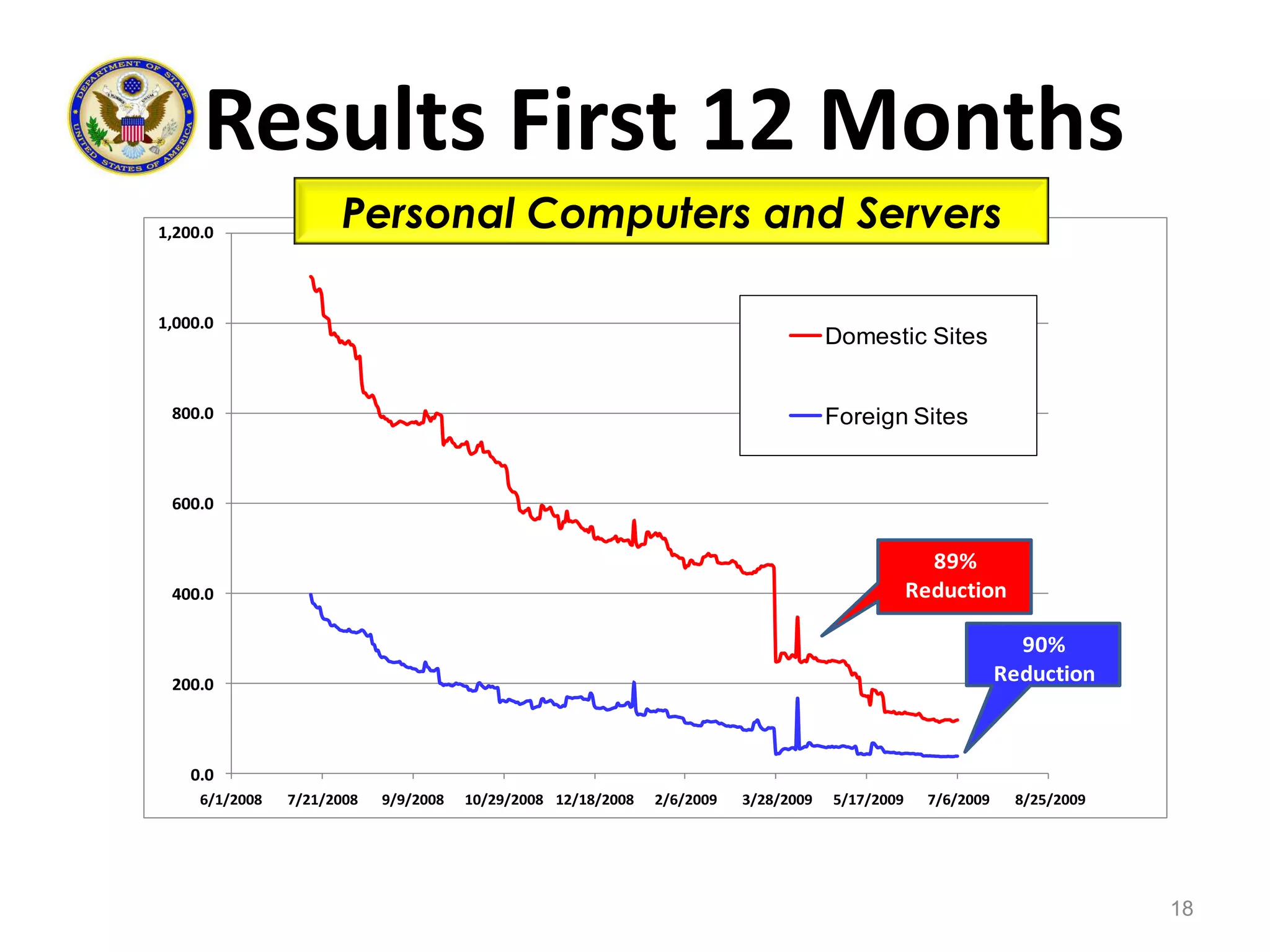

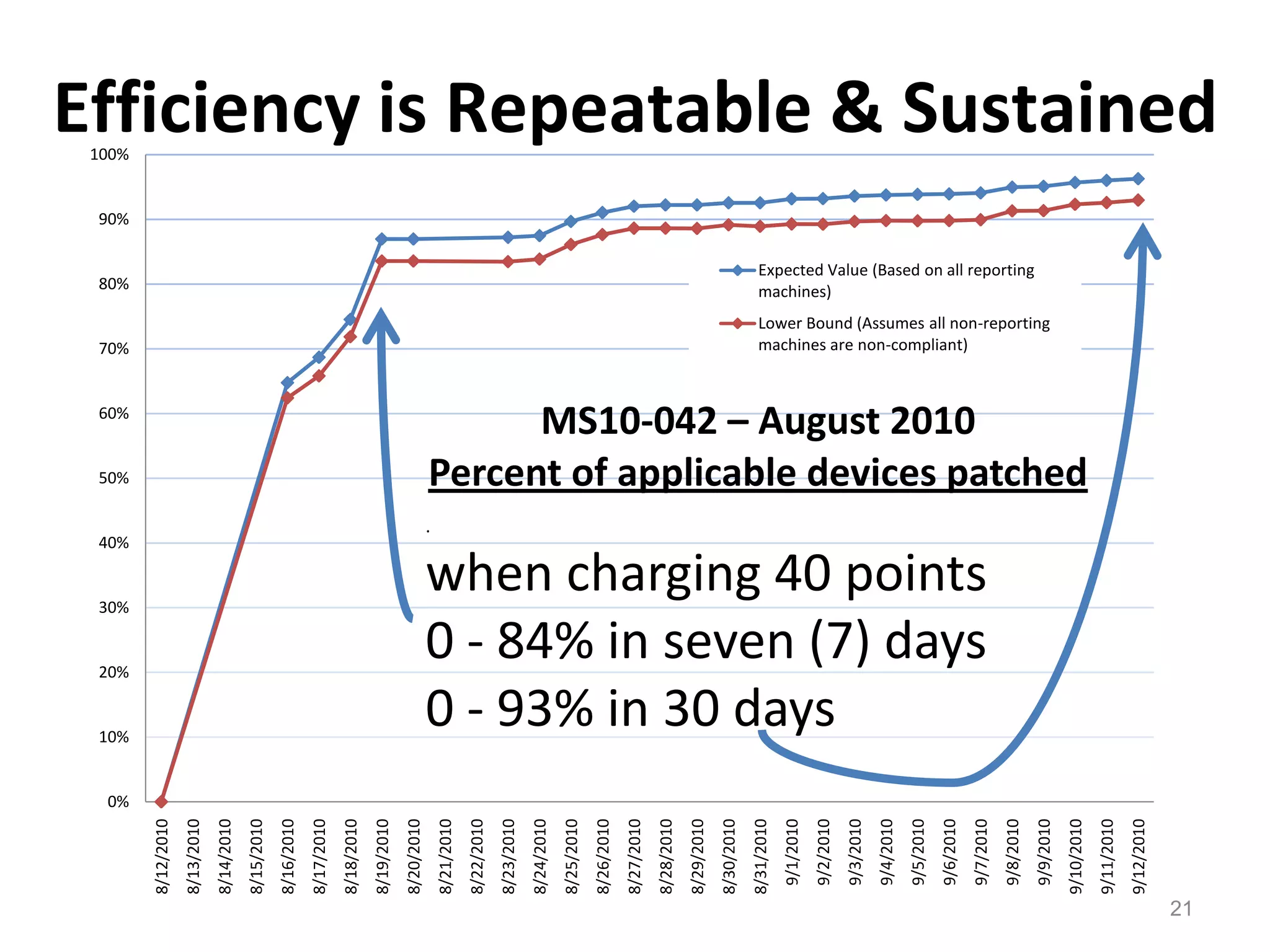
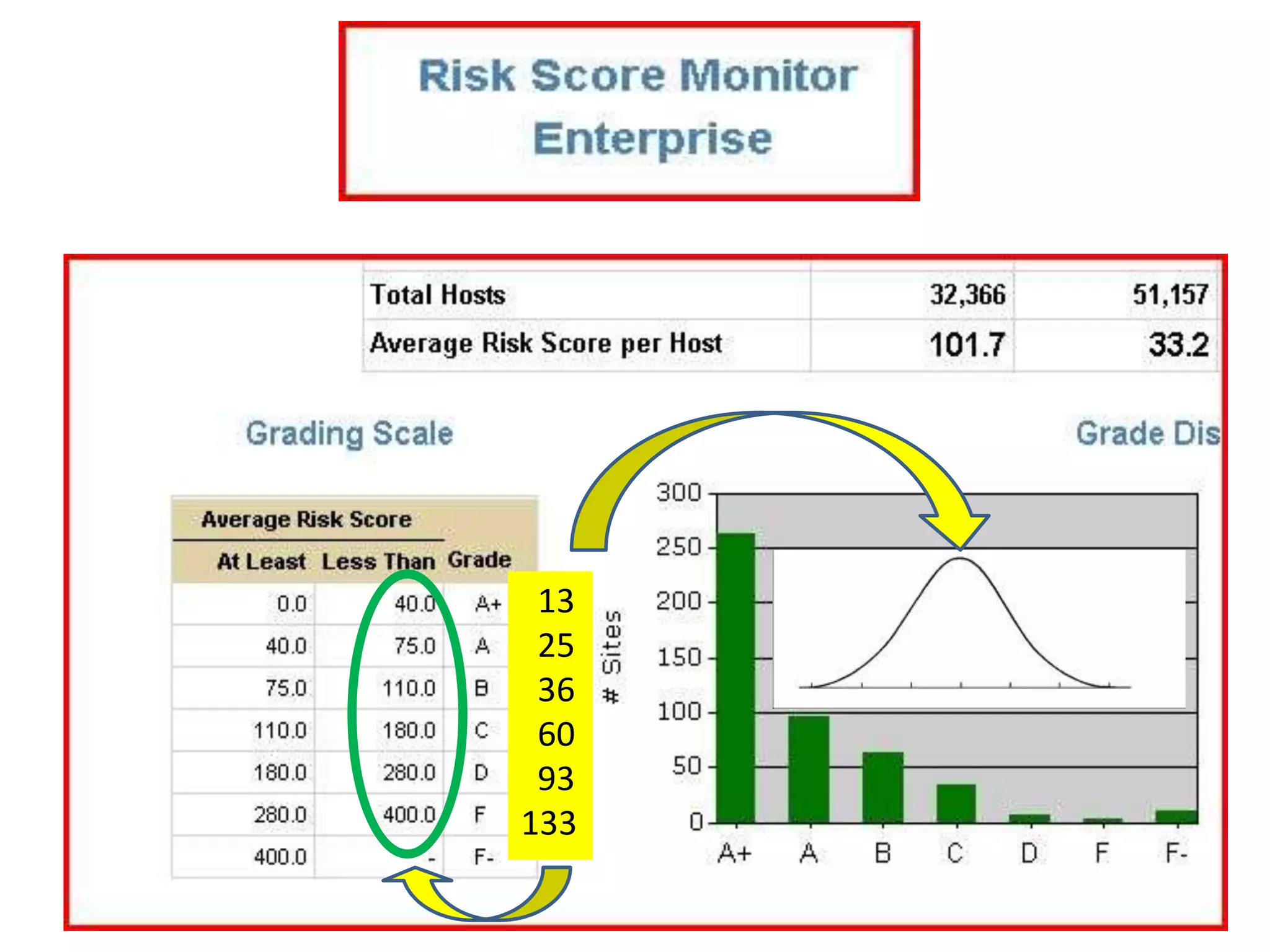
![1/3 of Remaining Risk Removed23[Year 2: PC’s/Servers]](https://image.slidesharecdn.com/02142011tripwireandinformationweekgovwebcastfinal2-110620131845-phpapp01/75/Developing-a-Continuous-Monitoring-Action-Plan-23-2048.jpg)