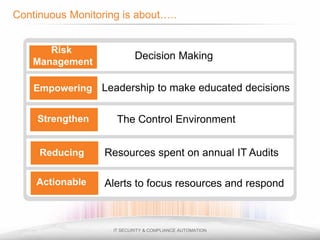
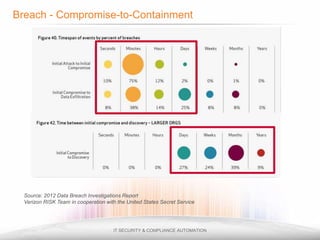
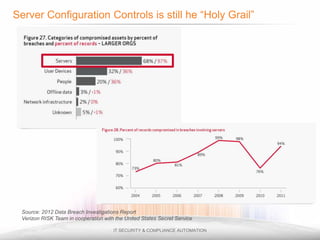
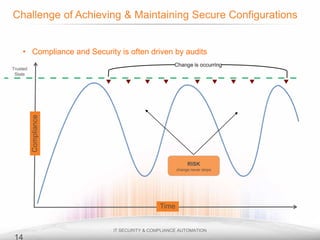
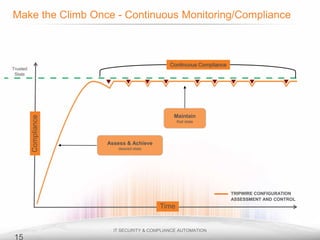
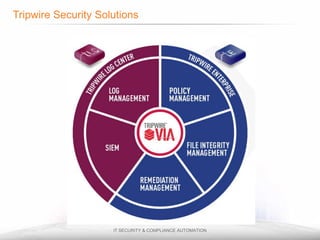
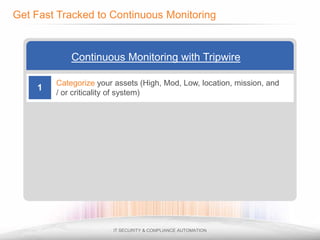
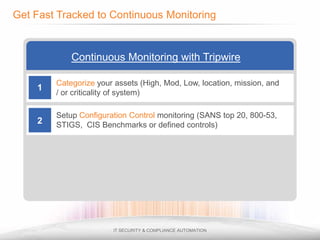
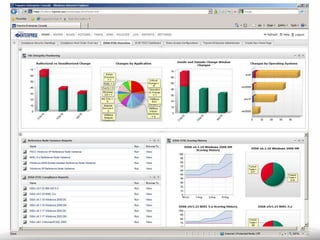
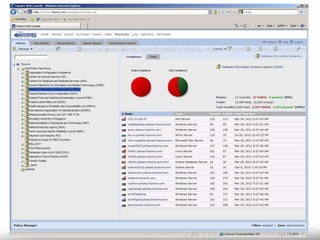
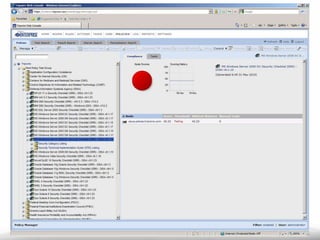
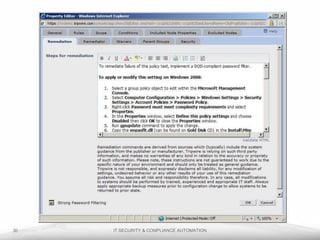
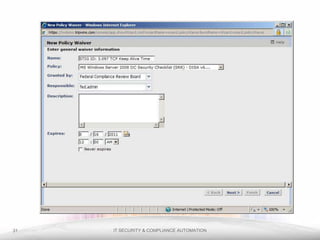
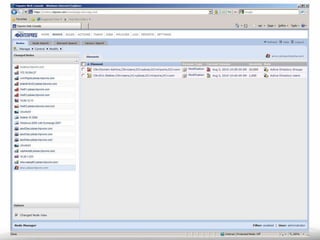
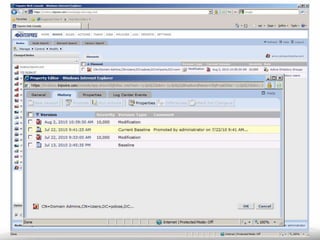
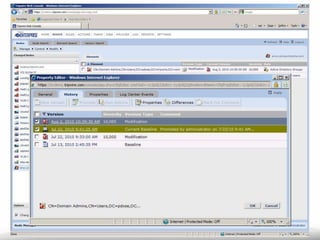
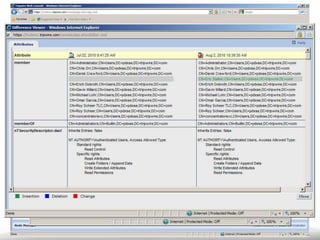
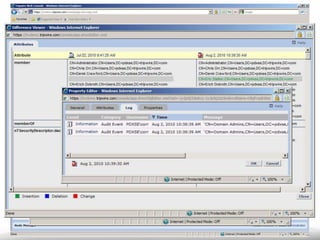
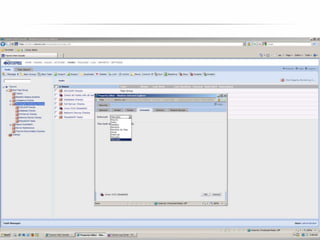
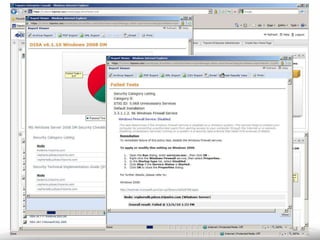
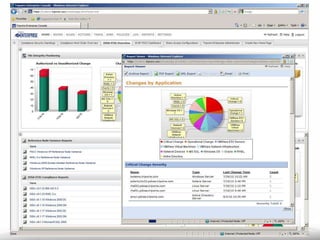
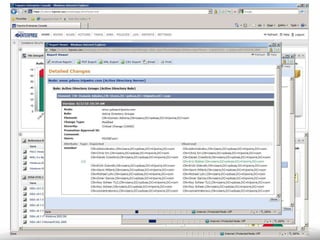
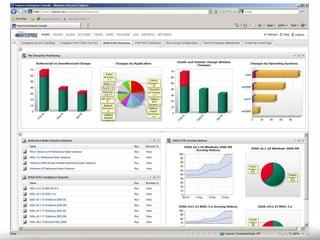
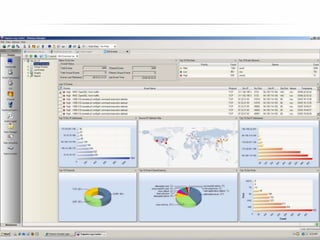
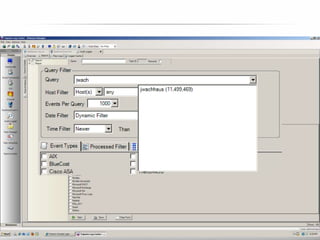
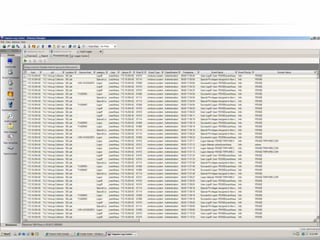
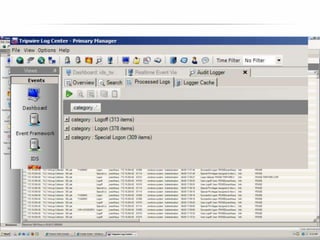
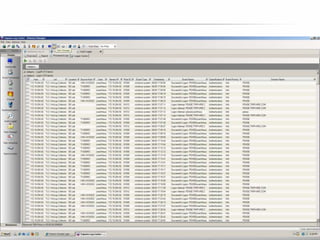
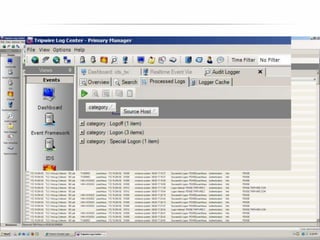
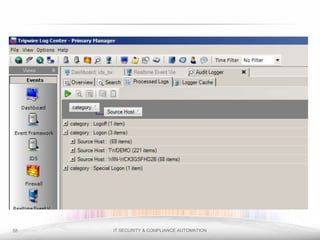
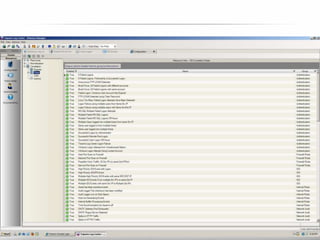
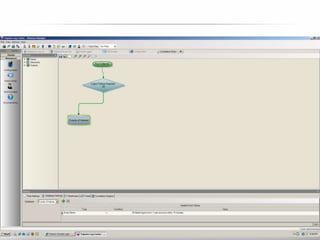
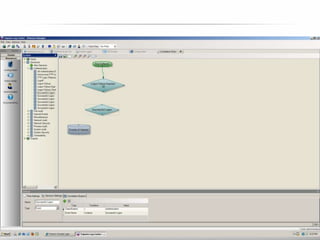
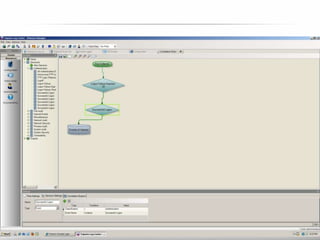
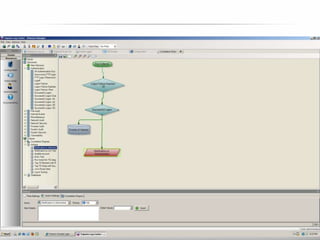
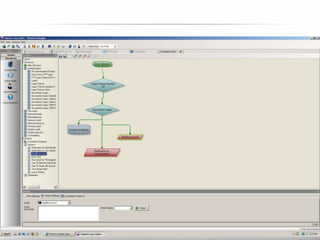
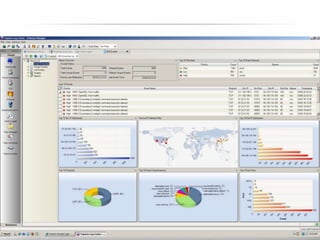
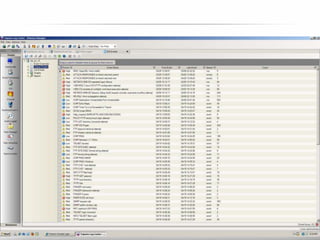
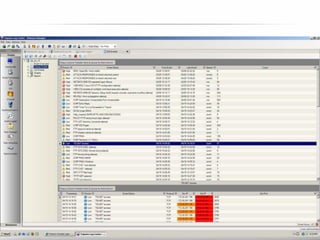
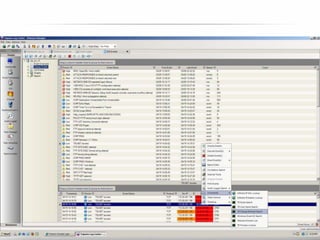
The document outlines the process and importance of achieving continuous monitoring with security automation in alignment with various frameworks such as RMF and NIST guidelines. It emphasizes asset categorization, setting up monitoring controls, determining risk thresholds, and defining response procedures to maintain compliance and security. Additionally, it provides contact information for inquiries and further resources.