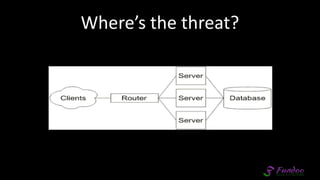
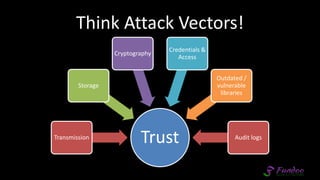
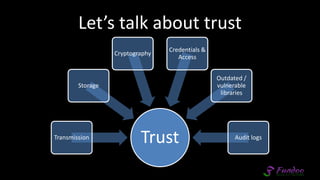
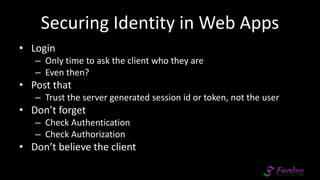
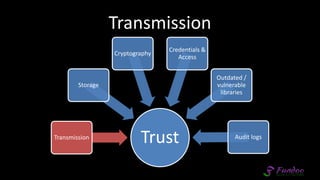
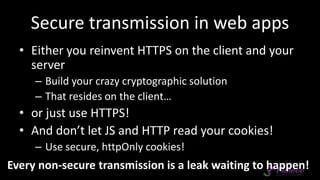
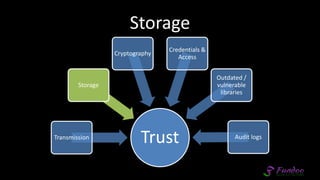
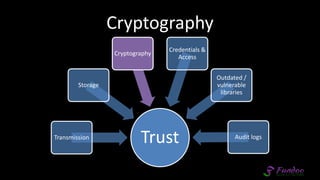
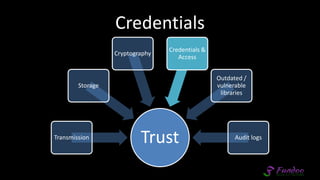
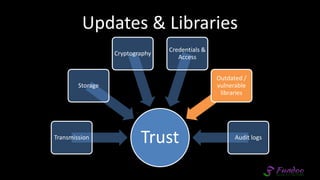
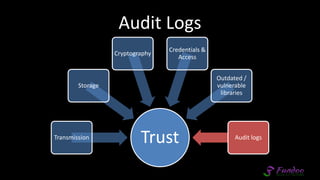
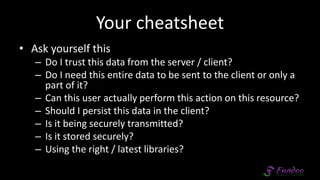
The document presents an overview of application security, discussing various threats such as XSS, CSRF, and basic principles of trust in web applications. It emphasizes the importance of secure data transmission, proper access control, and the need for regular updates and audits to safeguard application integrity. The discussion also highlights the critical role of developers in maintaining security standards amid evolving vulnerabilities.