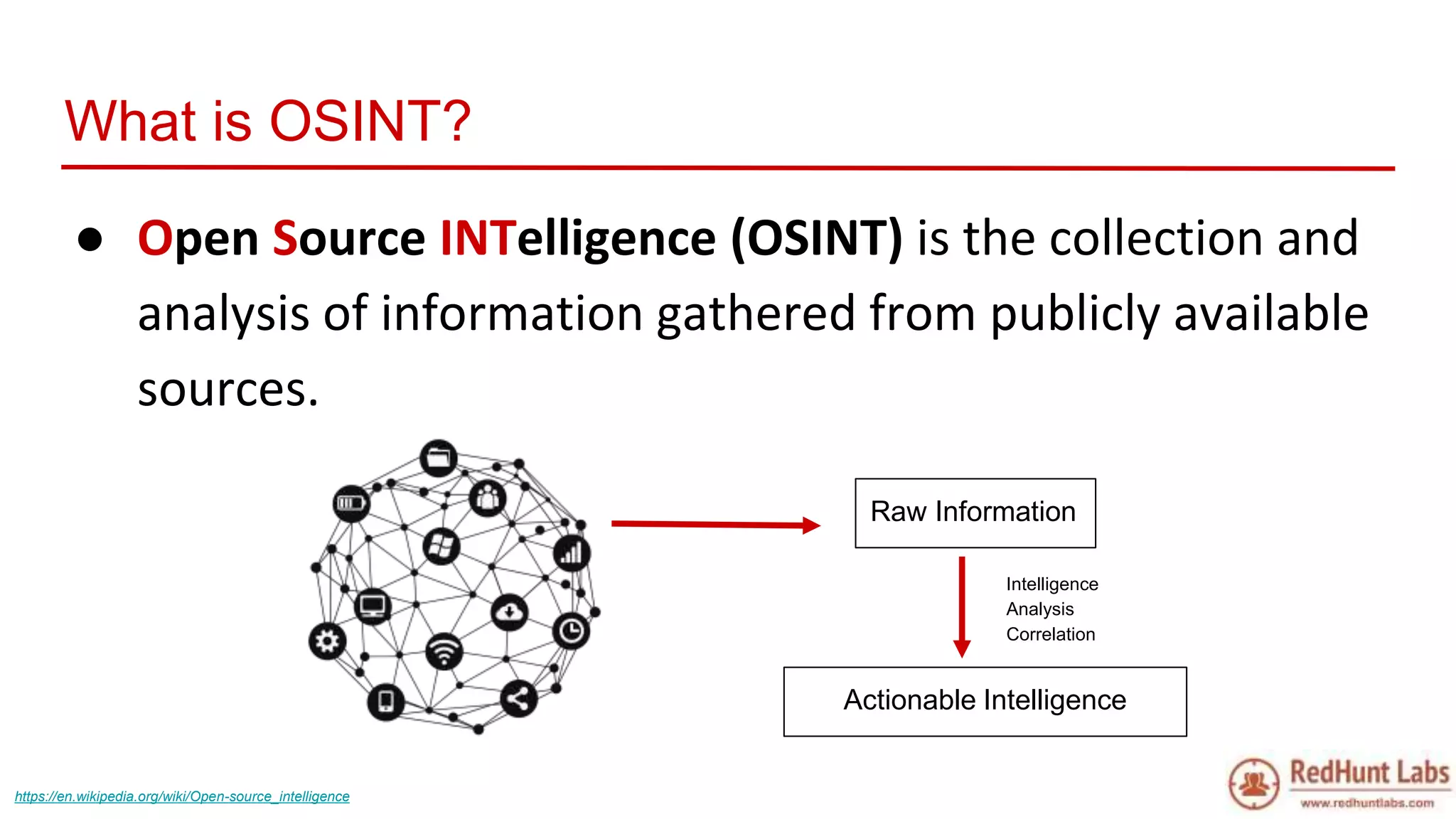
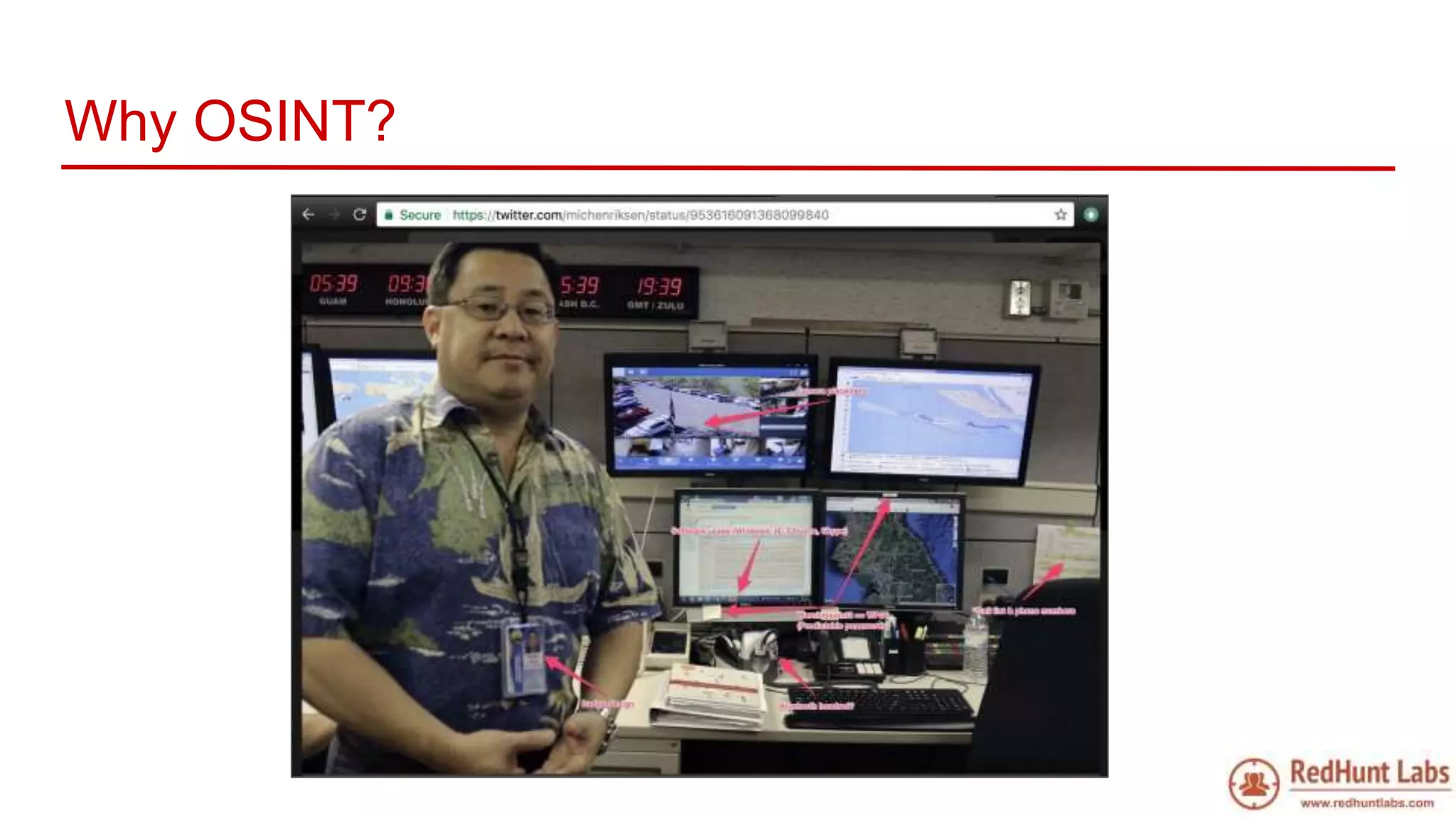
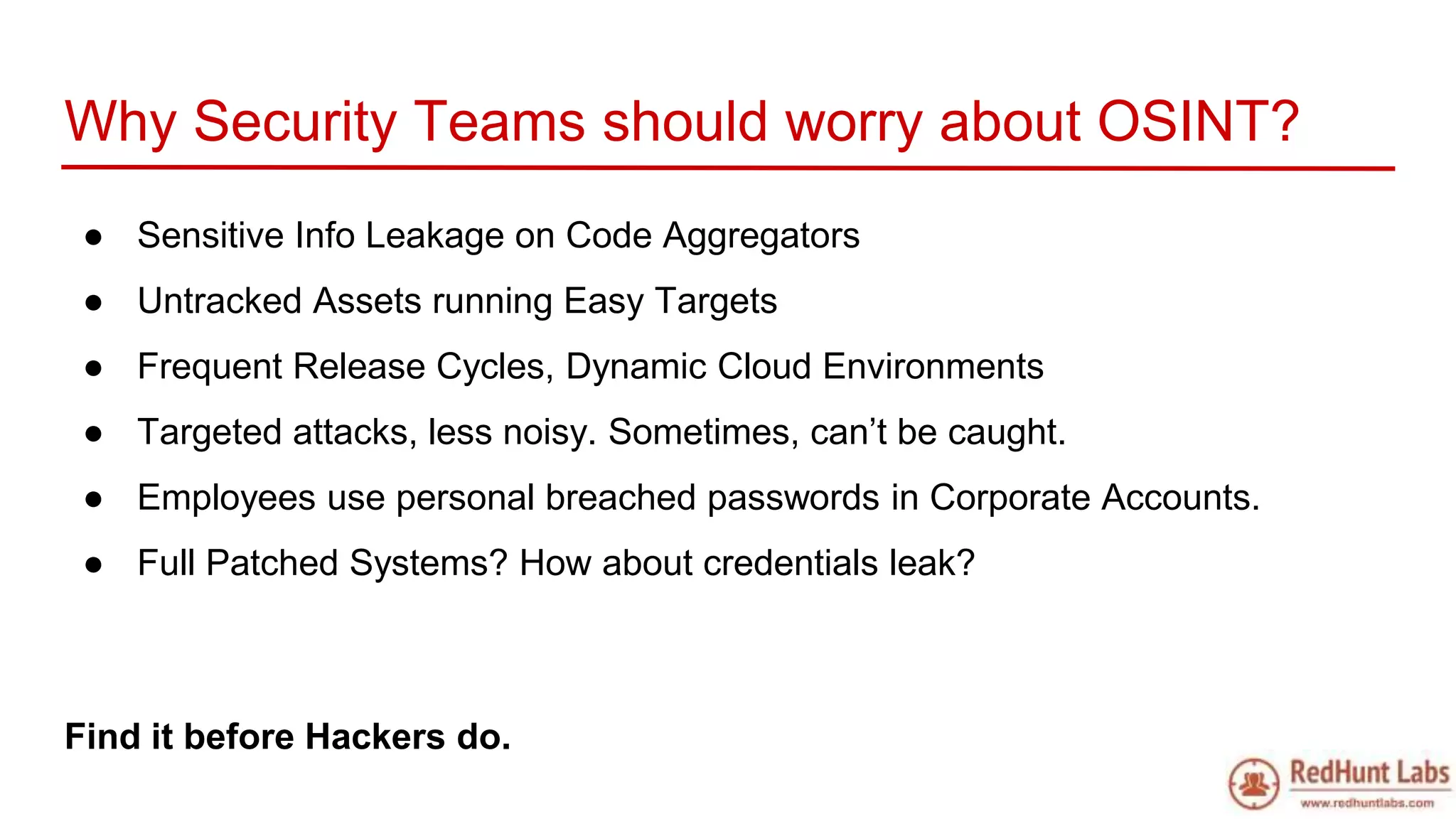
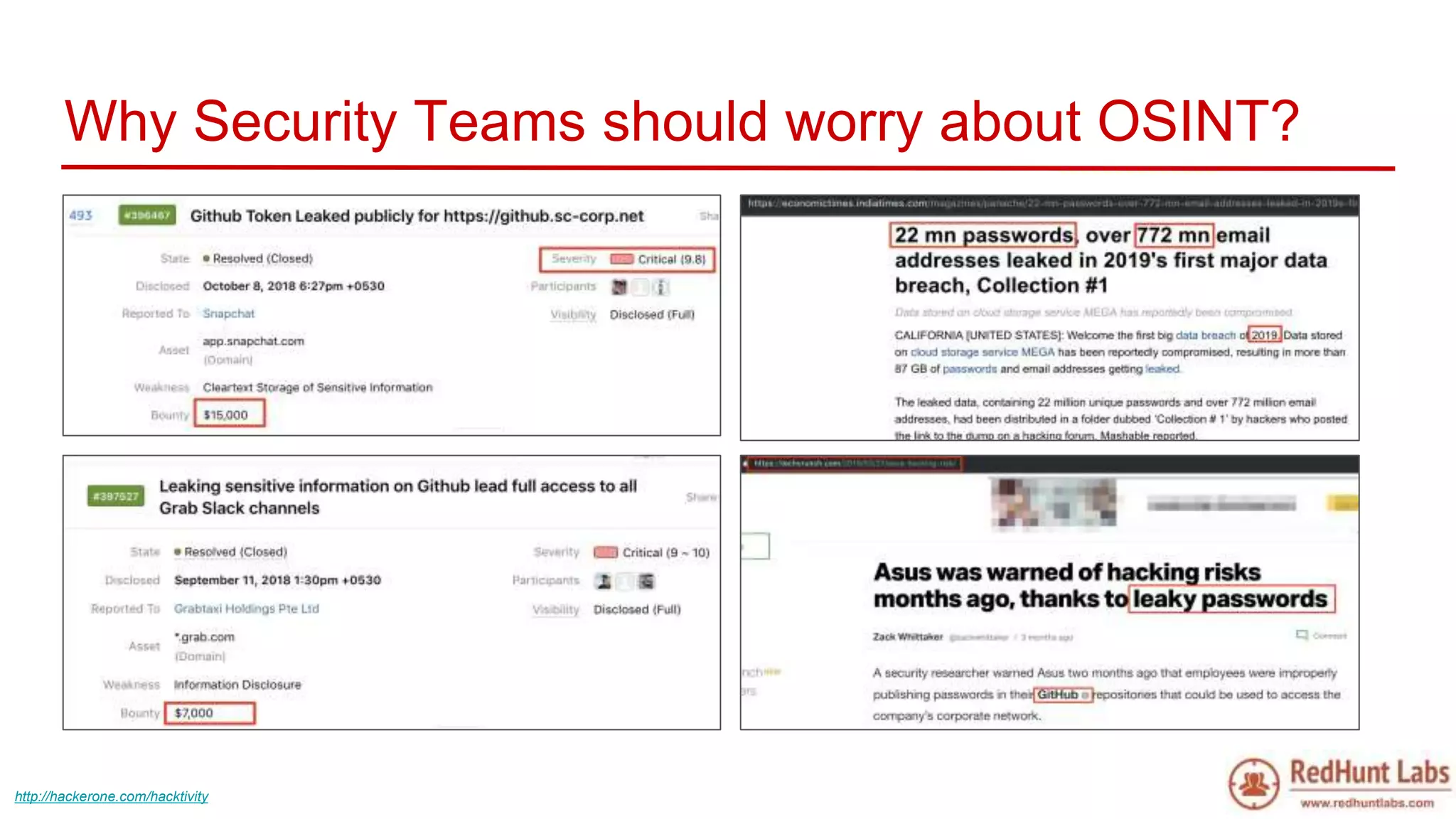
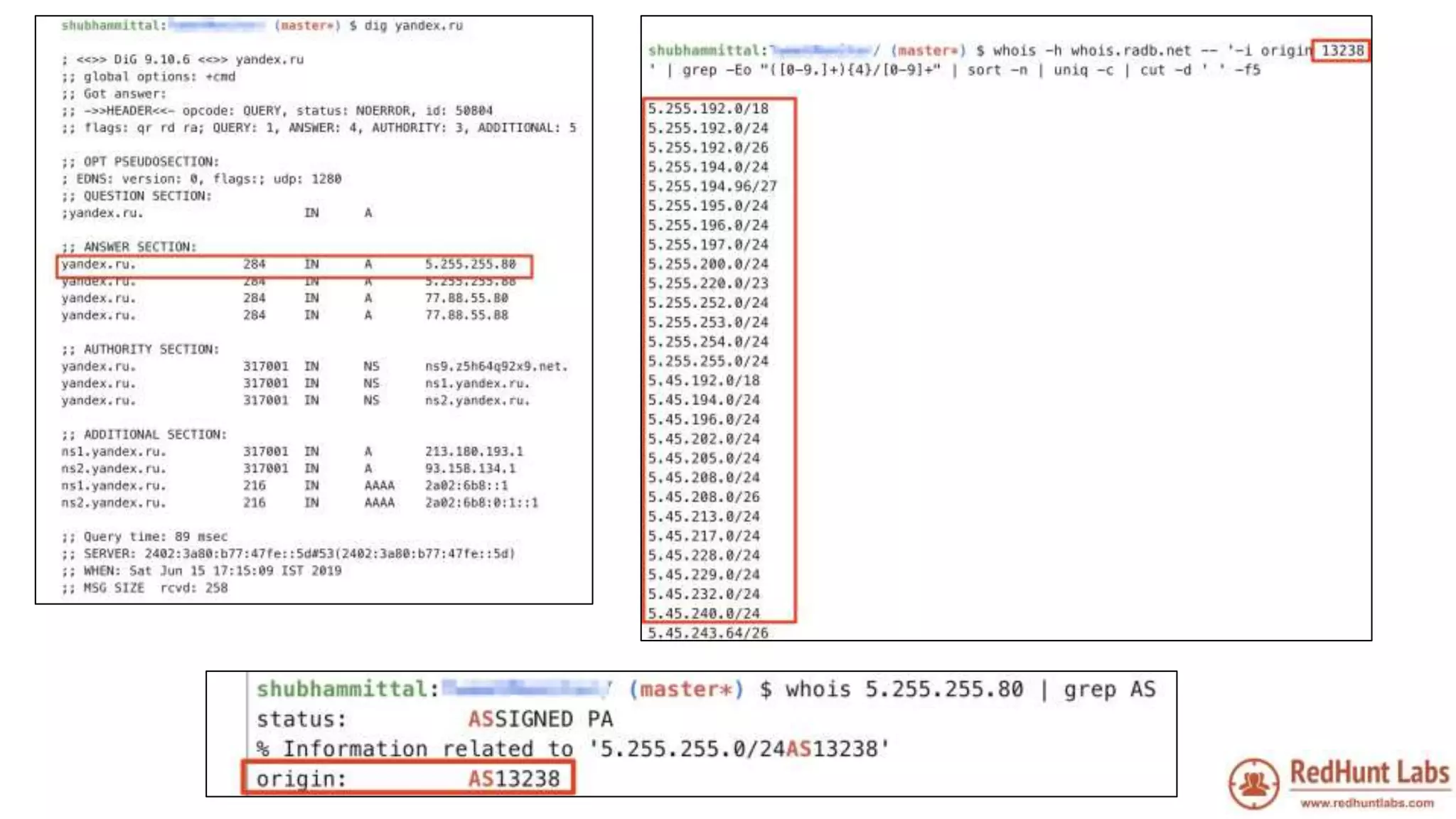
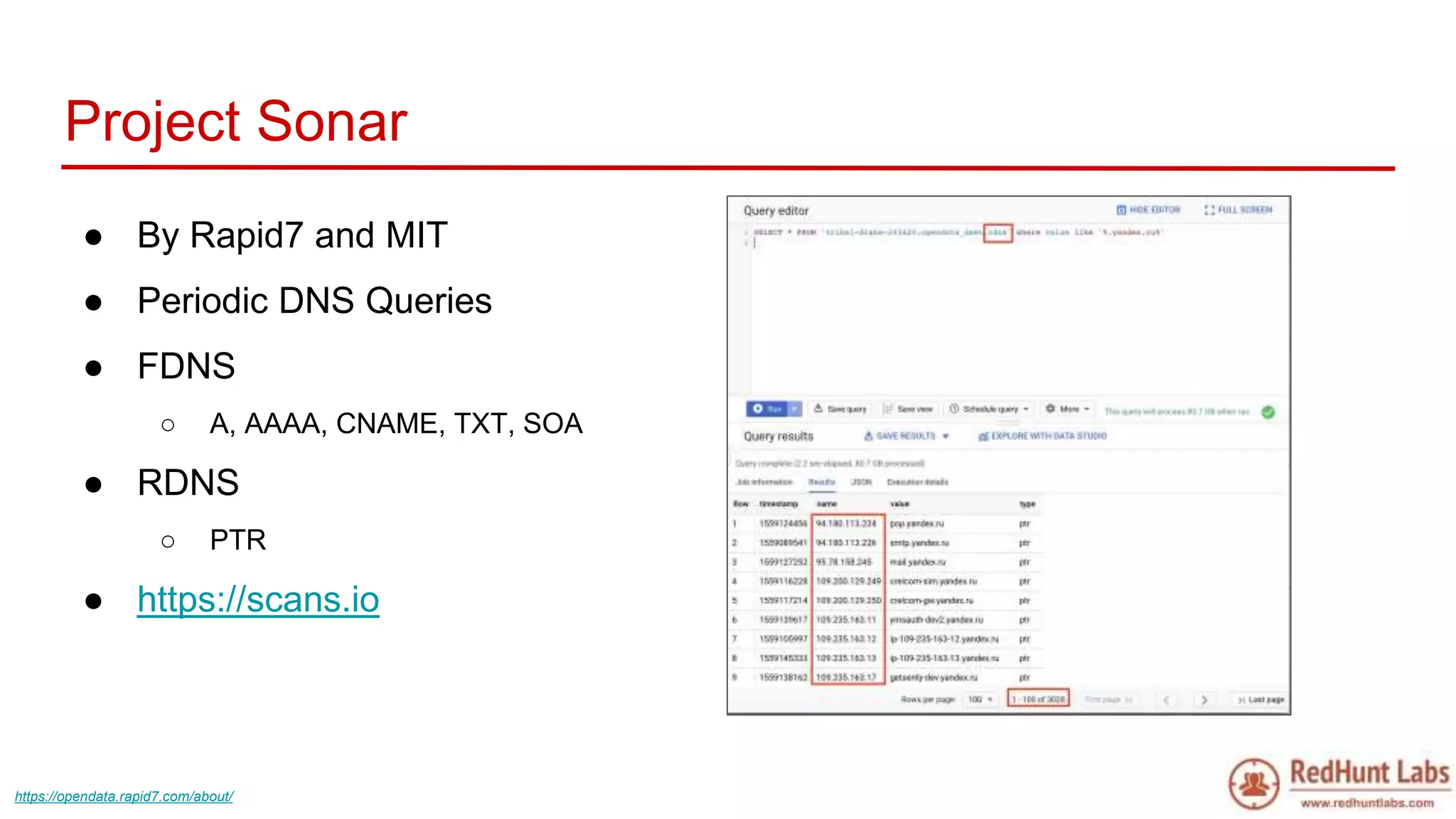
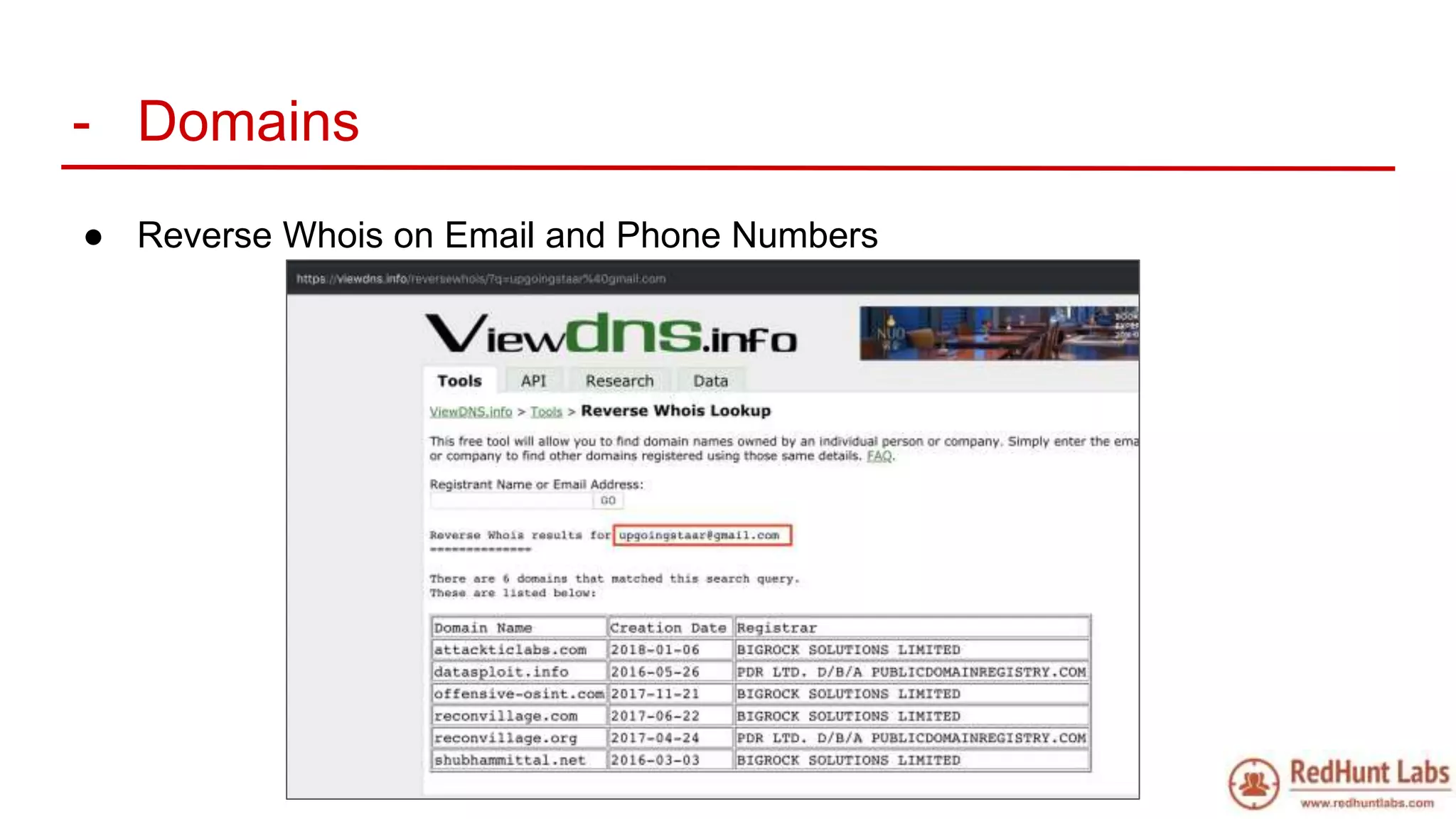
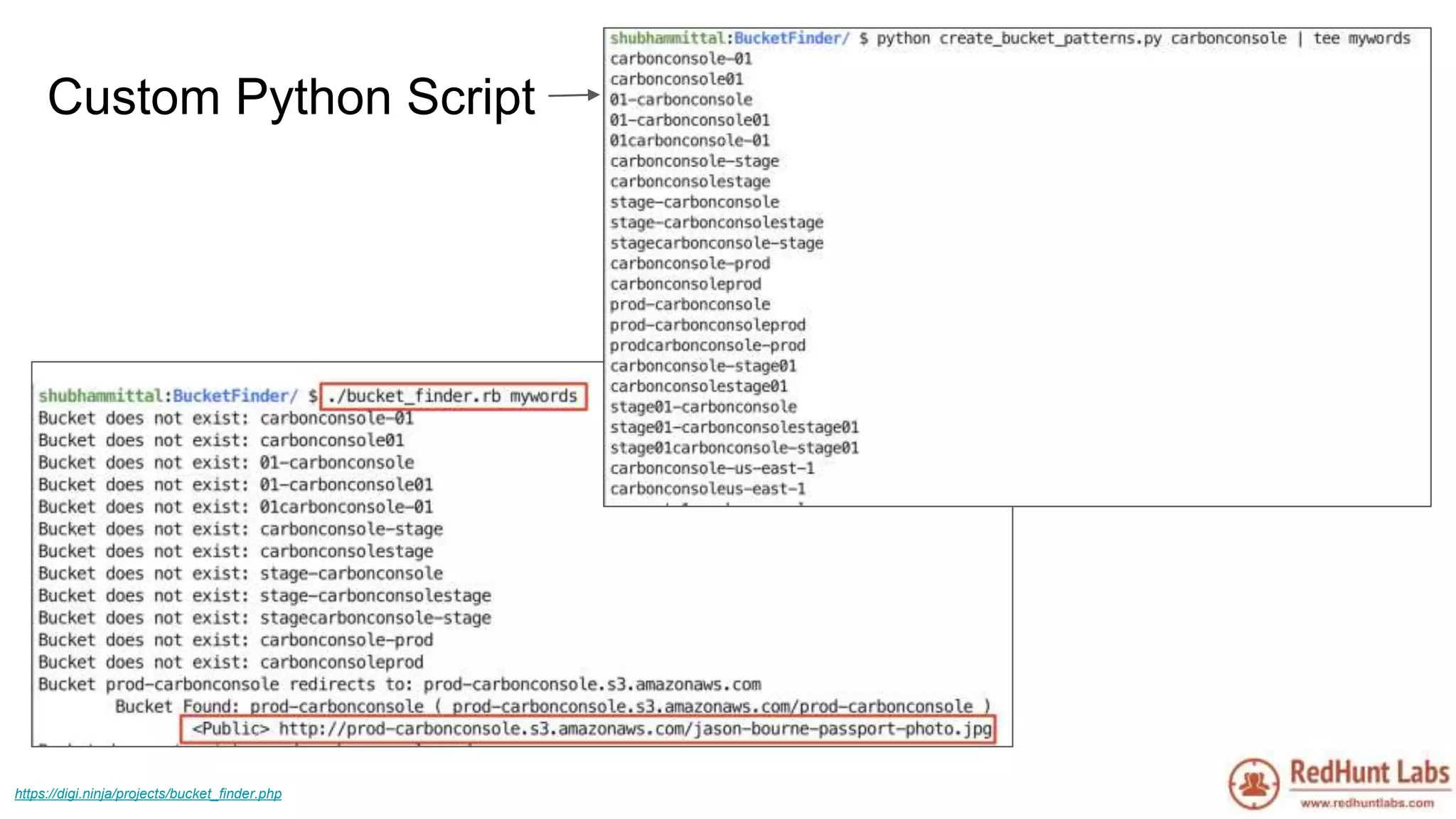
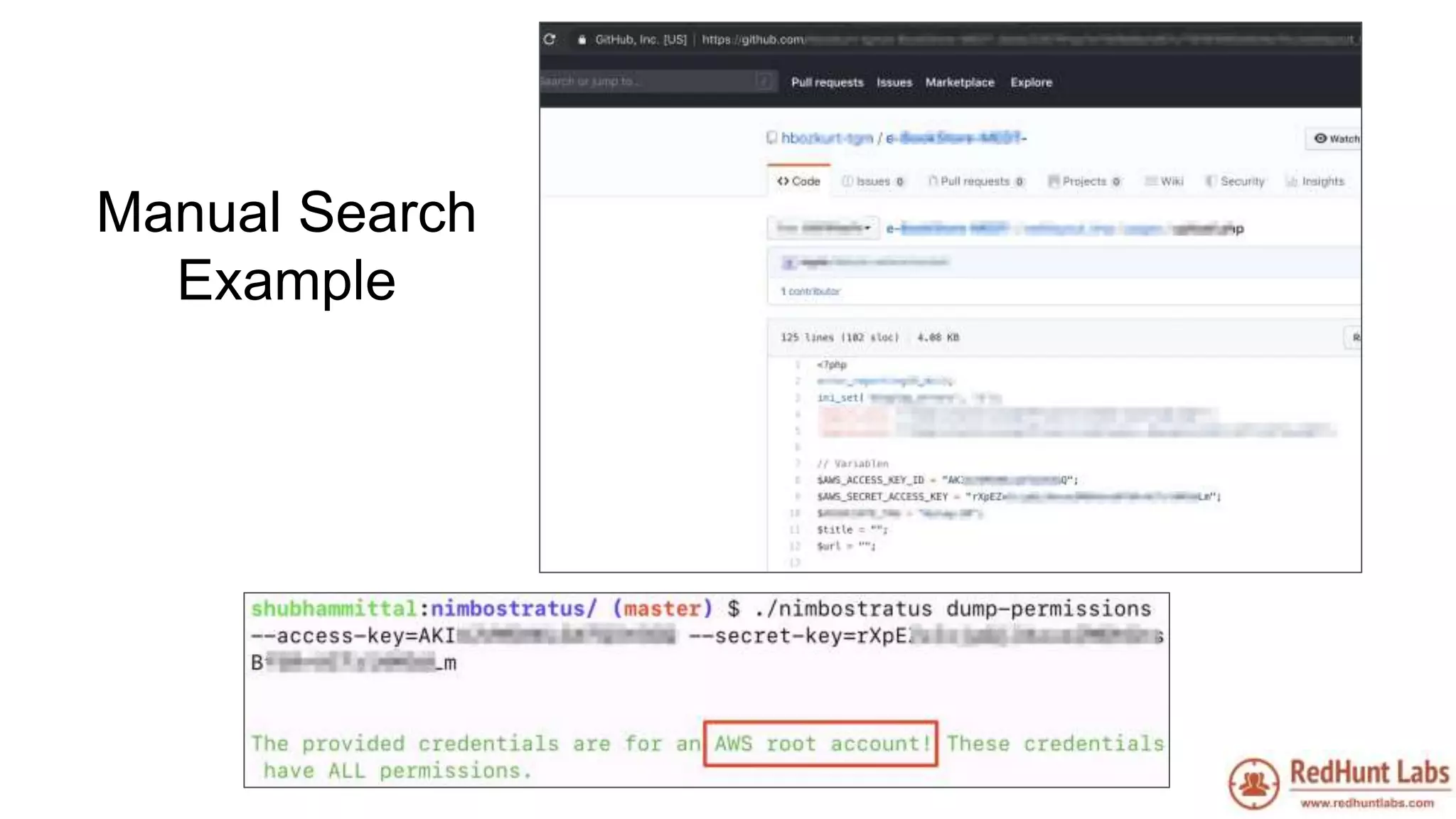
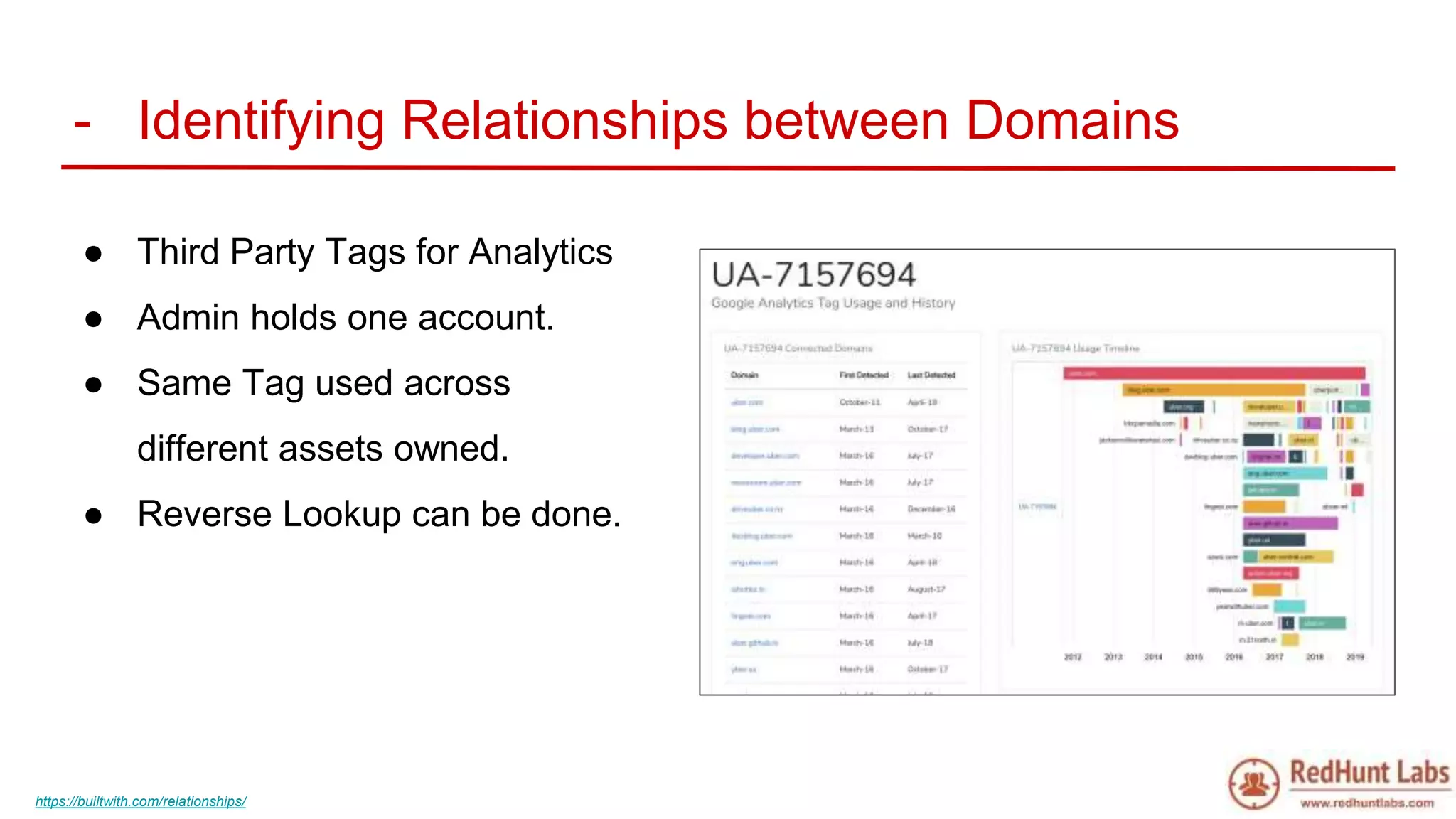
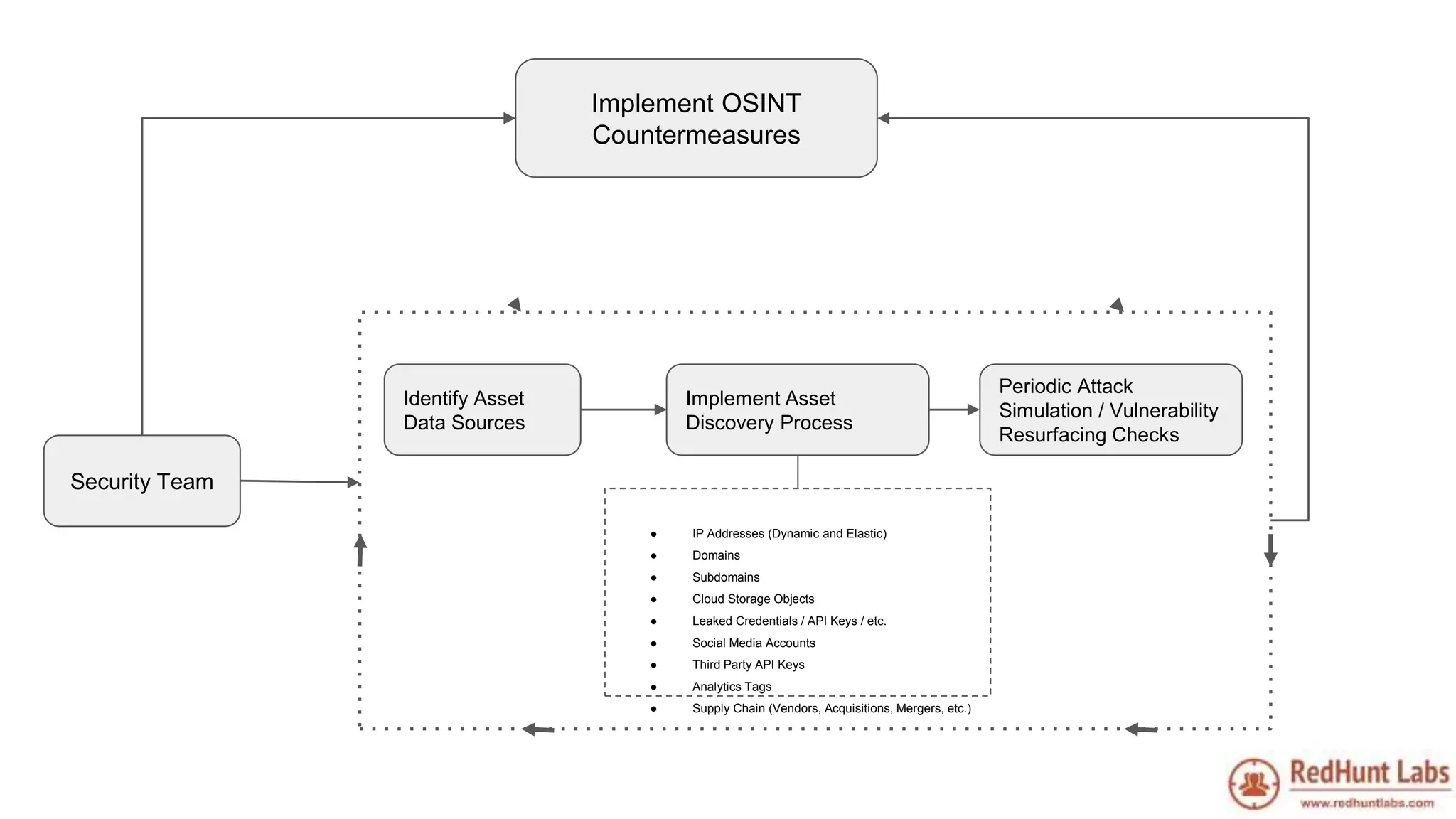
The document discusses open-source intelligence (OSINT) and its importance for security teams, emphasizing the need for proactive asset monitoring and vulnerability management. It outlines various methods and tools for continuous discovery and periodic attack simulation to safeguard against potential threats and sensitive data leakage. Furthermore, it provides resources and recommendations for implementing OSINT practices effectively within organizations.