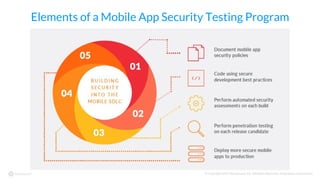
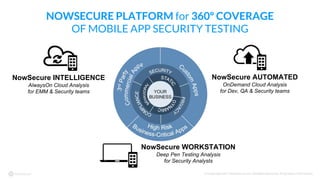
The document discusses mobile app security compliance for the banking and financial services sector, outlining various compliance frameworks, including standards from FFIEC, PCI DSS, and GLBA. It emphasizes the importance of secure coding, risk assessments, and ongoing security testing as critical components for meeting compliance requirements. A case study highlights the practical application of these standards in ensuring effective mobile app security and compliance.







![© Copyright 2017 NowSecure, Inc. All Rights Reserved. Proprietary information.
Payment Card Industry Data Security Standard (PCI DSS)
PCI DSS Version 3.2
6 Develop and maintain secure systems and applications
● 6.3 Develop internal and external software applications securely
● 6.5 Address common coding vulnerabilities in software-development
processes [based on OWASP, SANS, CERT guidance]
11 Regularly test security systems and processes
● 11.3 Implement a methodology for penetration testing…
● ...Defines application-layer penetration testis to include, at a
minimum, the vulnerabilities listed in Requirement 6.5
PCI Mobile Payment Acceptance Security Guidelines
Merchant-owned devices/apps used for payments (i.e., a POS system) are in
scope for PA-DSS. Apps on a consumer’s device that facilitate payments are
not in scope for PA-DSS, but development is in scope for PCI DSS.
Information security standard for organizations that handle payment cards. For a consumer-facing app
that facilitates a merchant’s payment acceptance process, the development of the app is in scope.](https://image.slidesharecdn.com/compliance-170822165957/85/Solving-for-Compliance-Mobile-app-security-for-banking-and-financial-services-9-320.jpg)