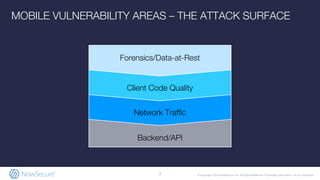
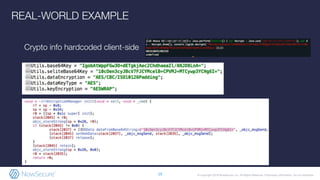
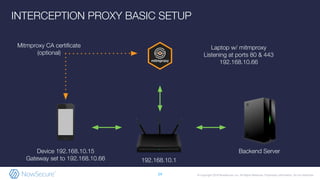
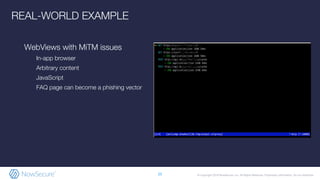
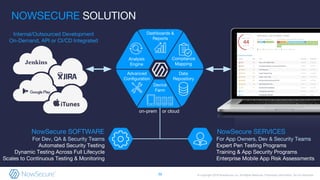
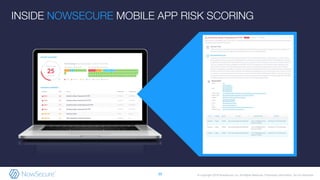
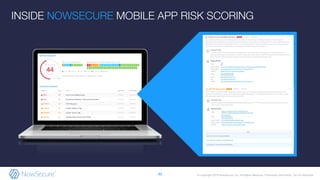
The document outlines the importance of mobile app security, highlighting that 85% of mobile apps contain vulnerabilities and nearly half leak personal data, raising concerns about compliance with GDPR. It discusses various security risks and weaknesses commonly found in mobile apps, along with strategies for testing and remediation. Additionally, it emphasizes the role of NowSecure's expertise in mobile security and offers solutions for automating security testing in the development lifecycle.