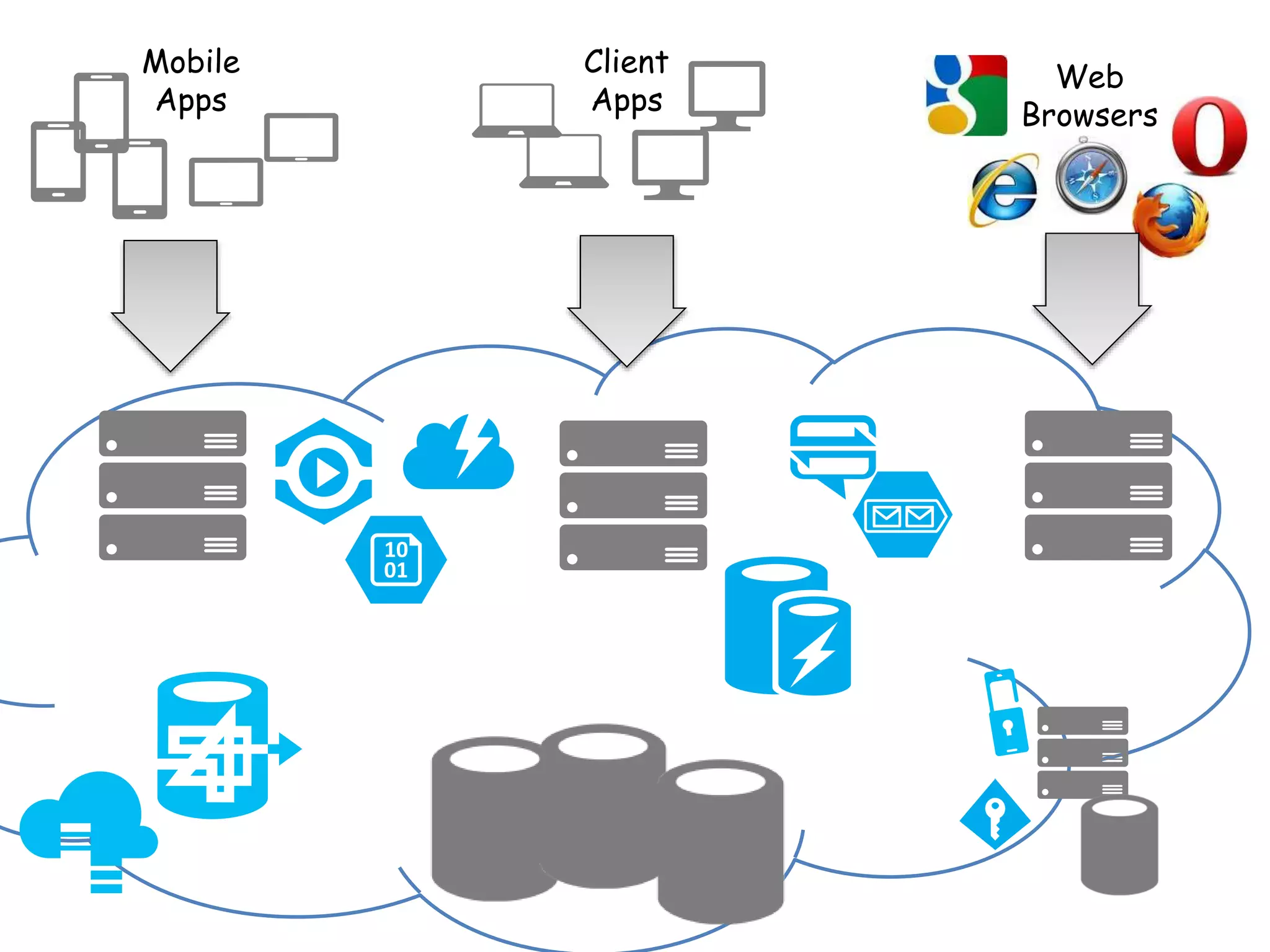
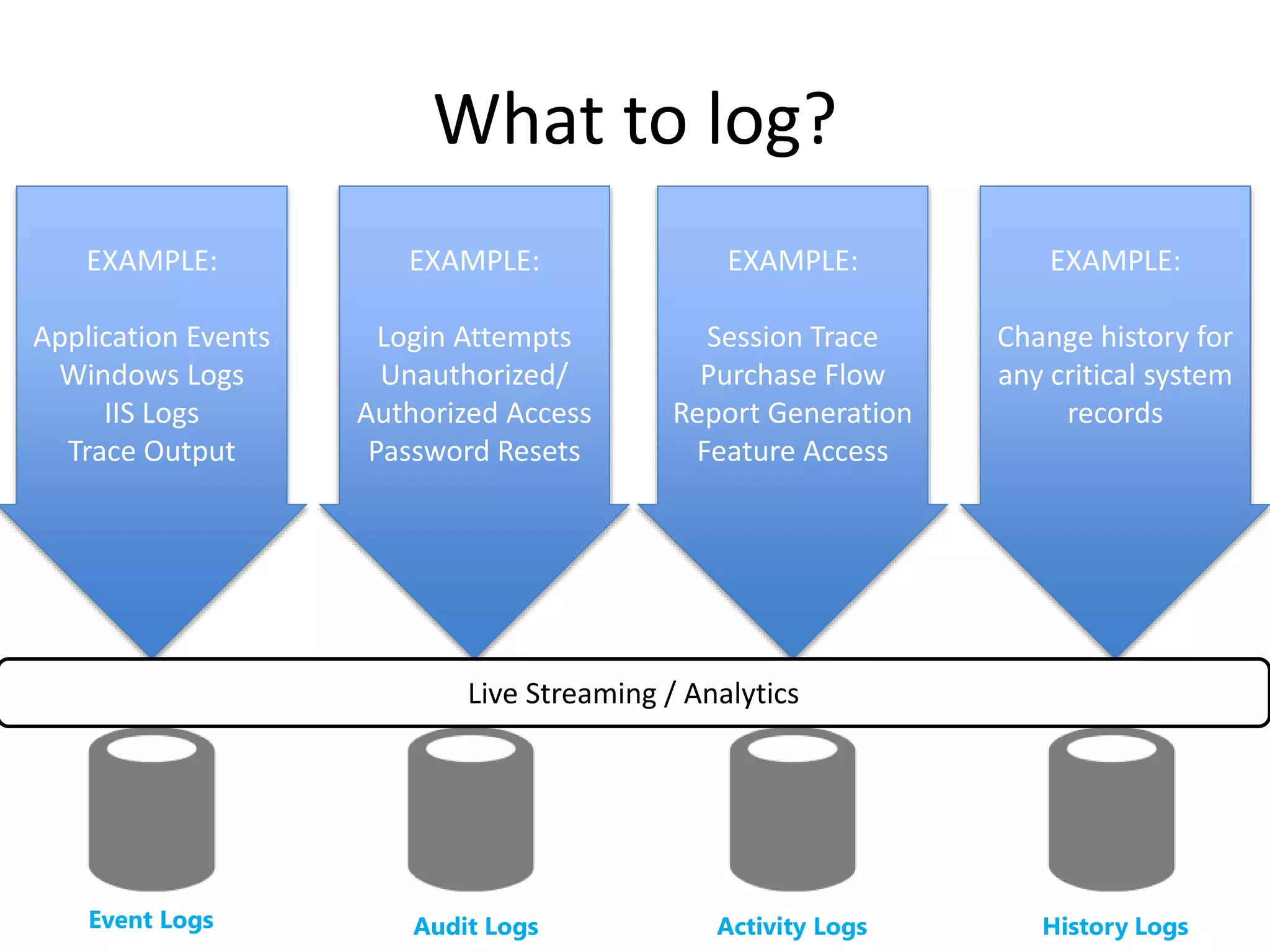
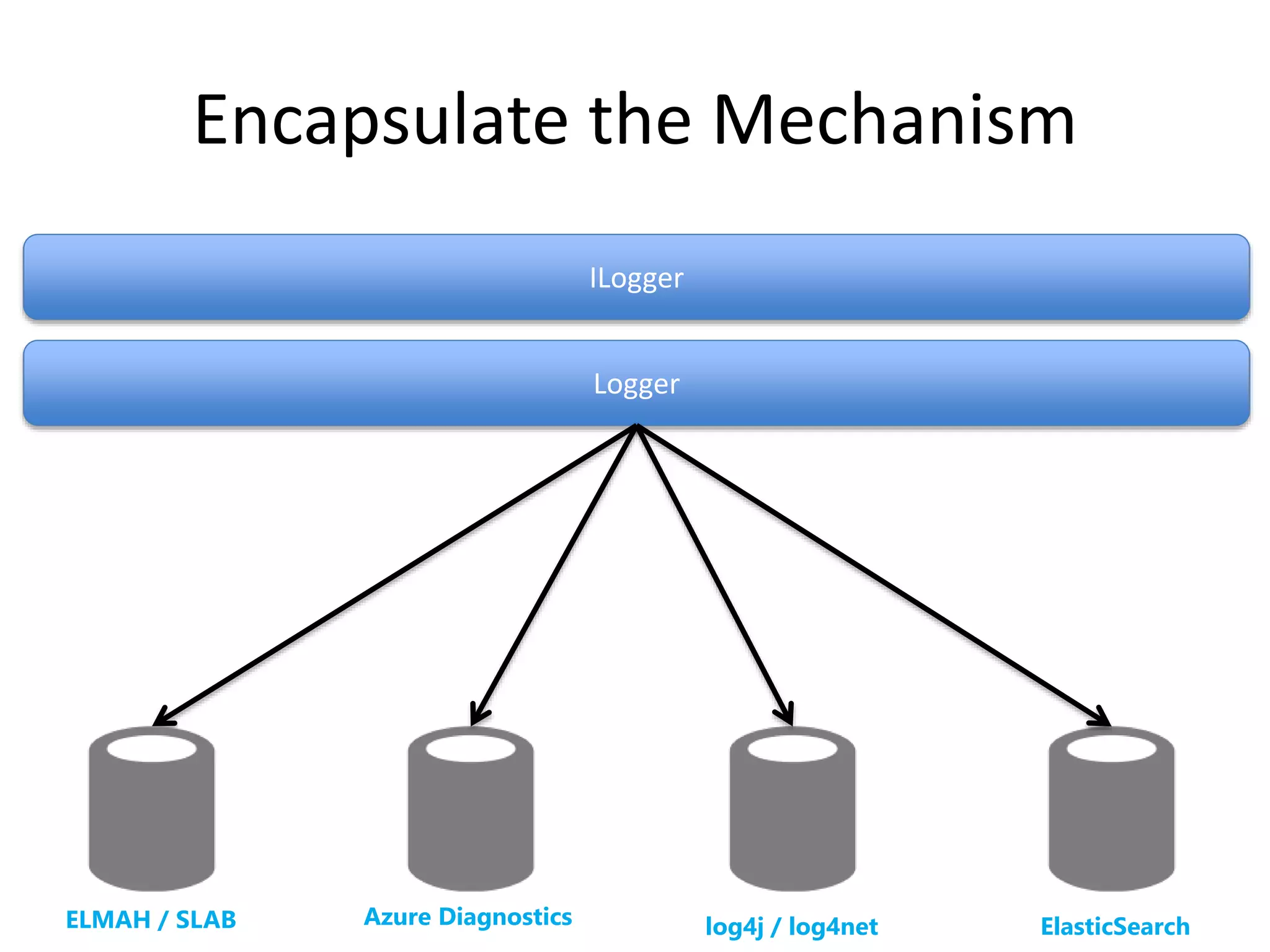
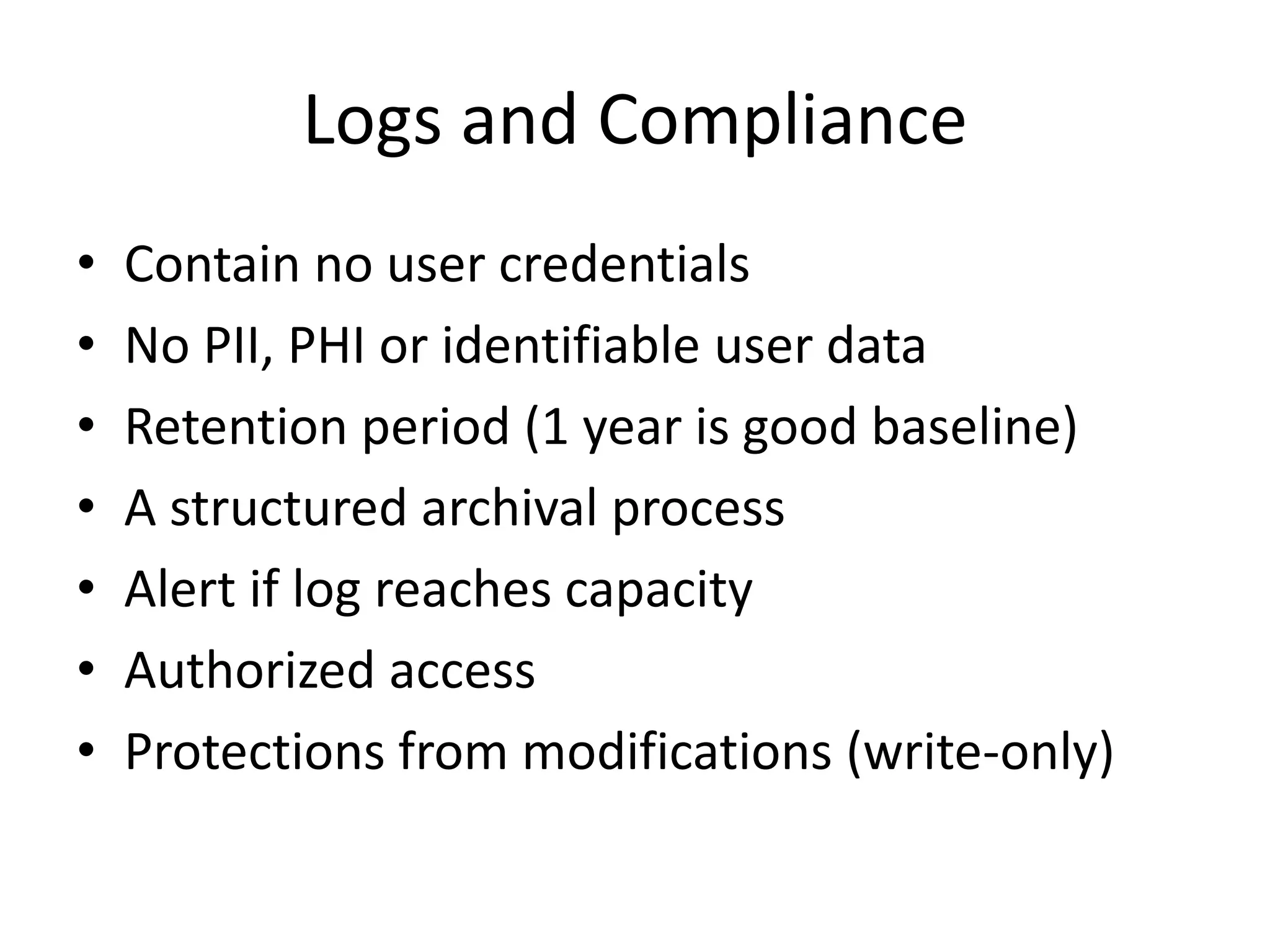
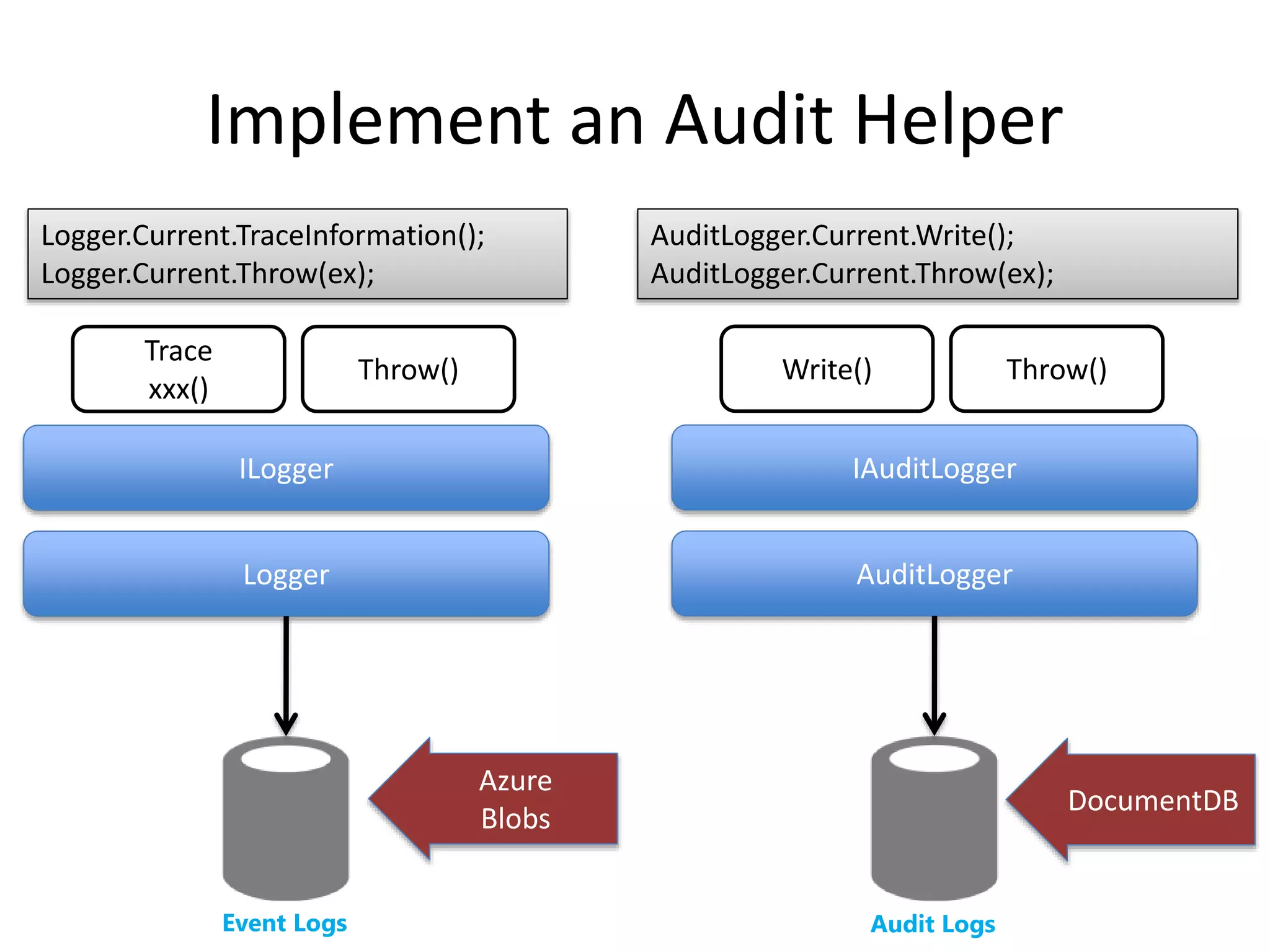
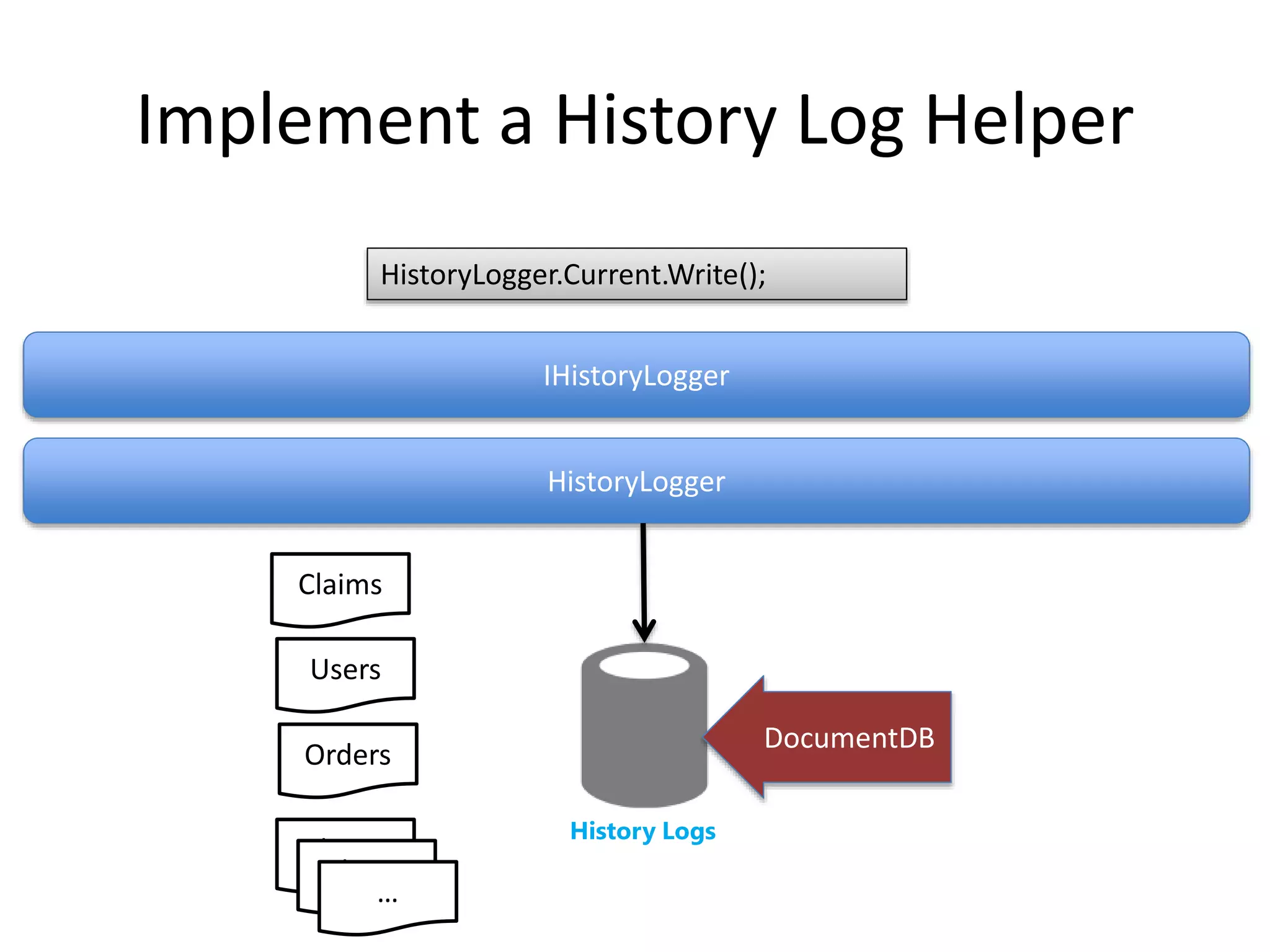
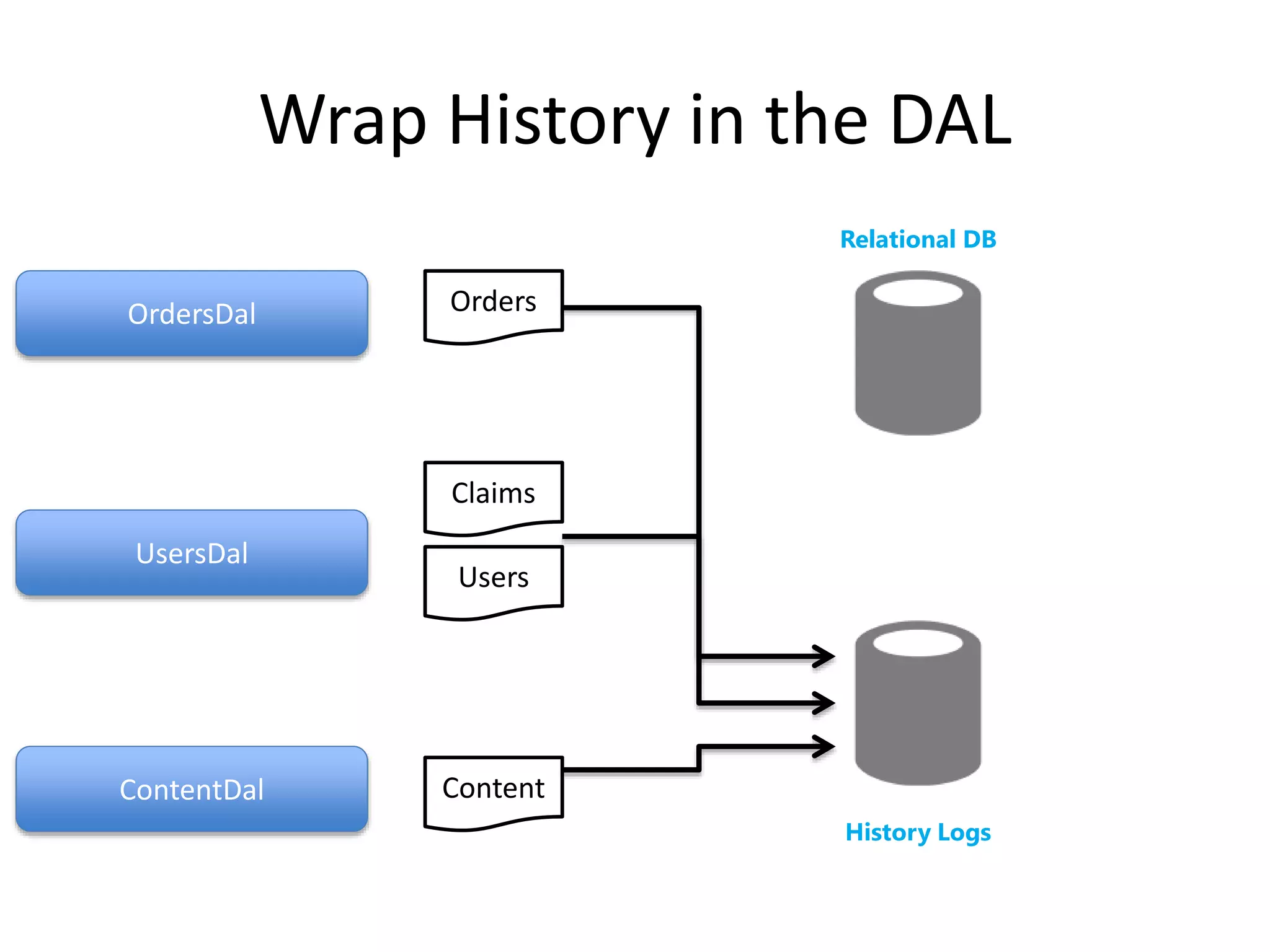
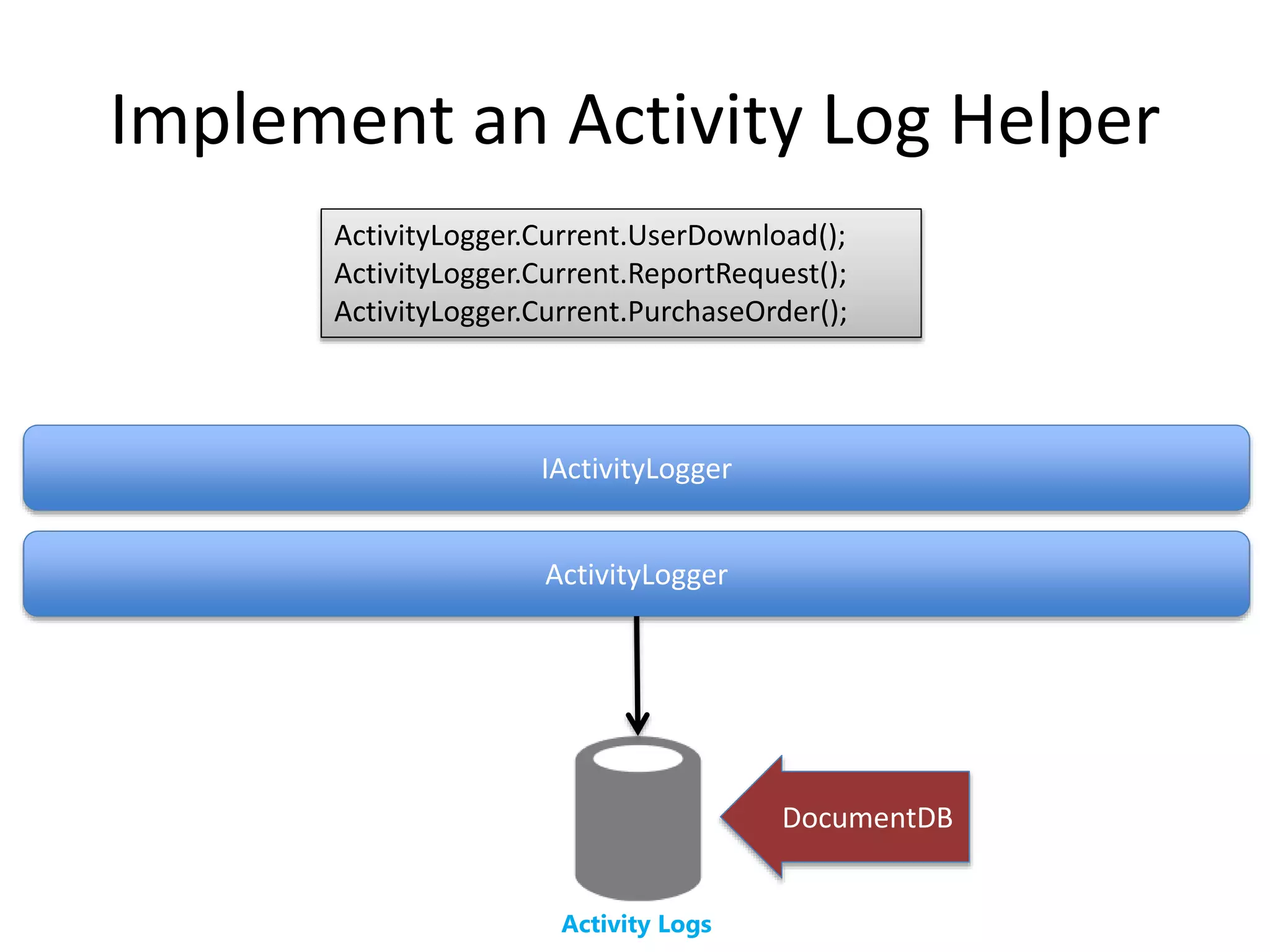
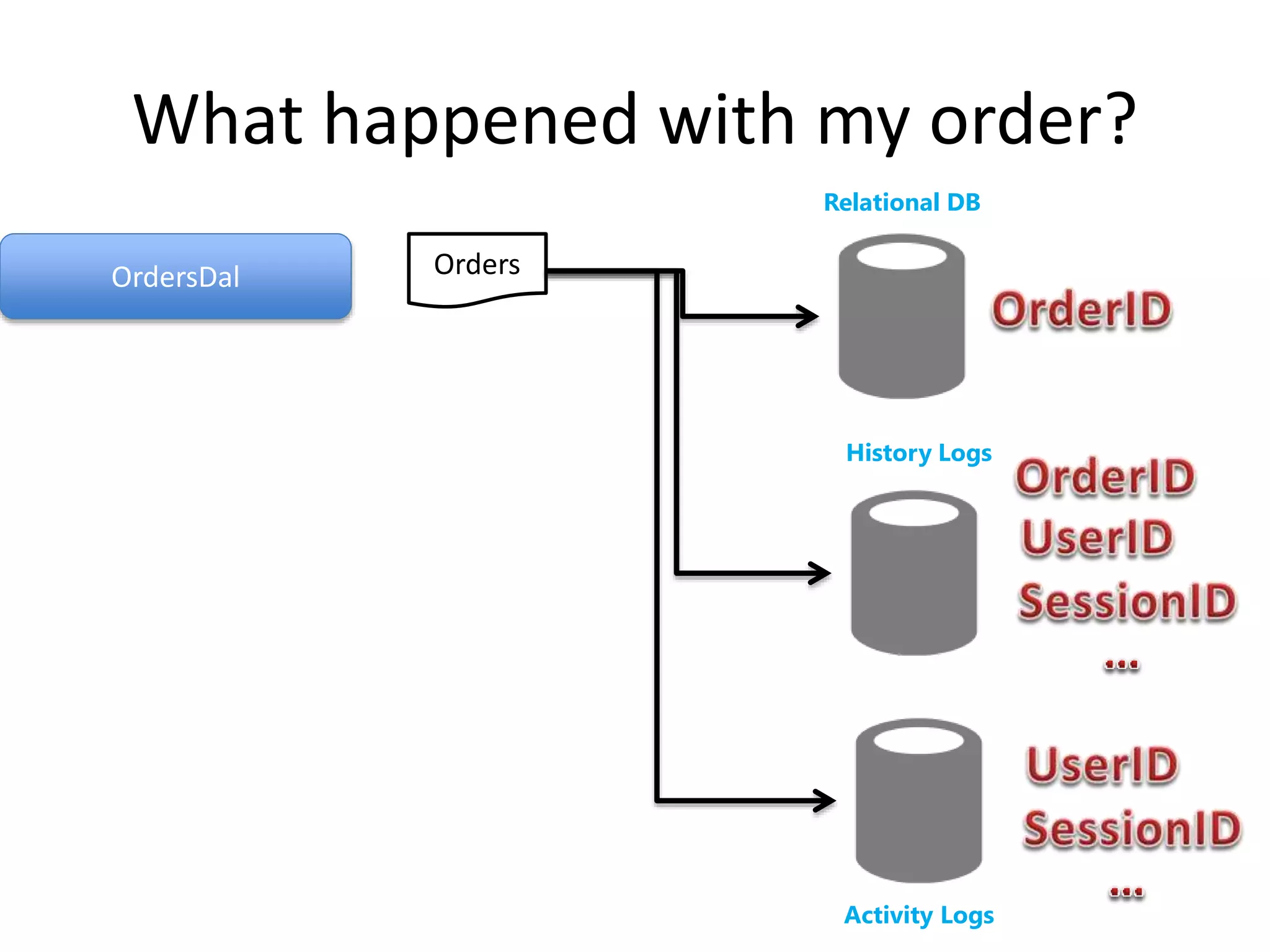
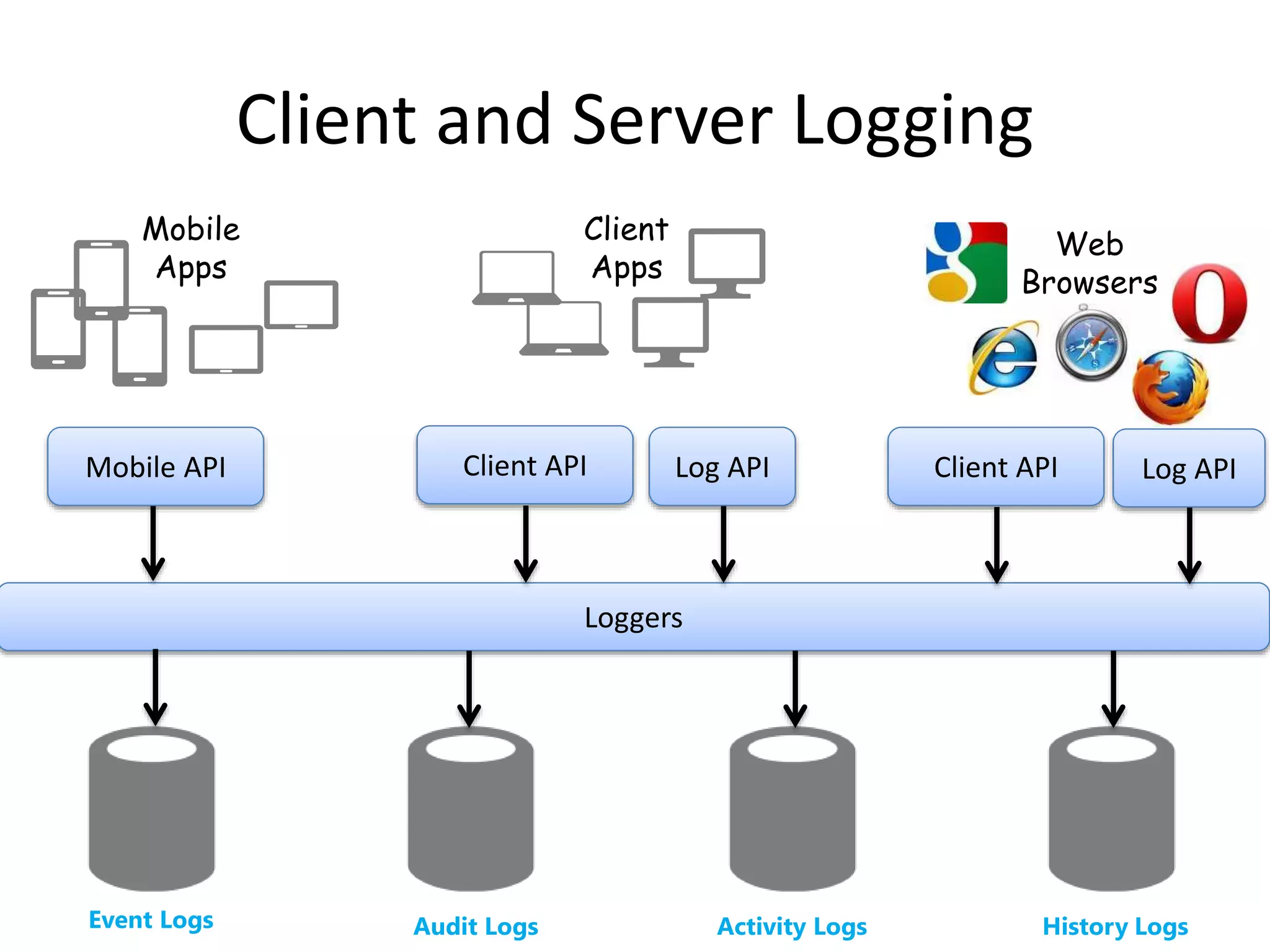
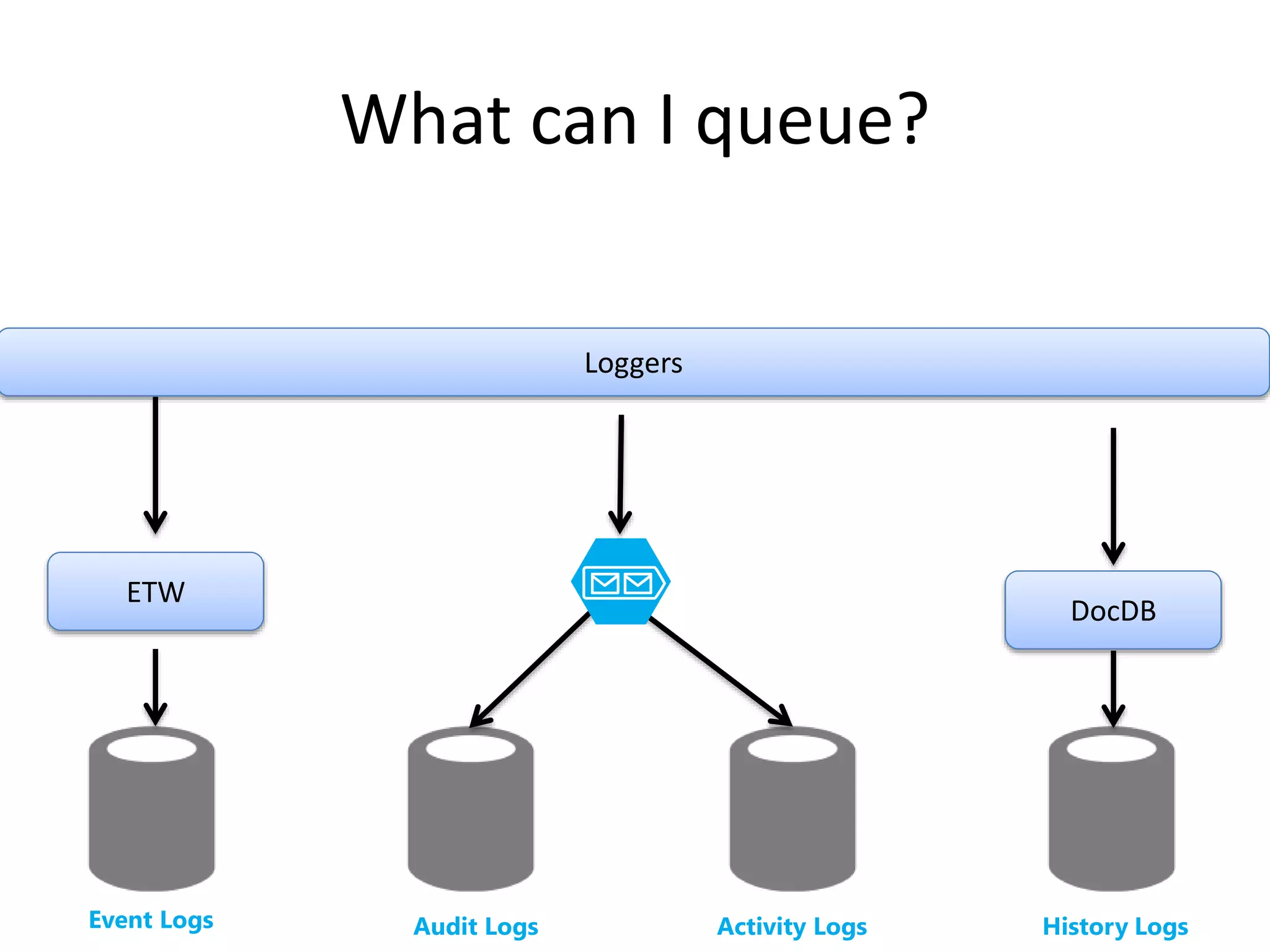
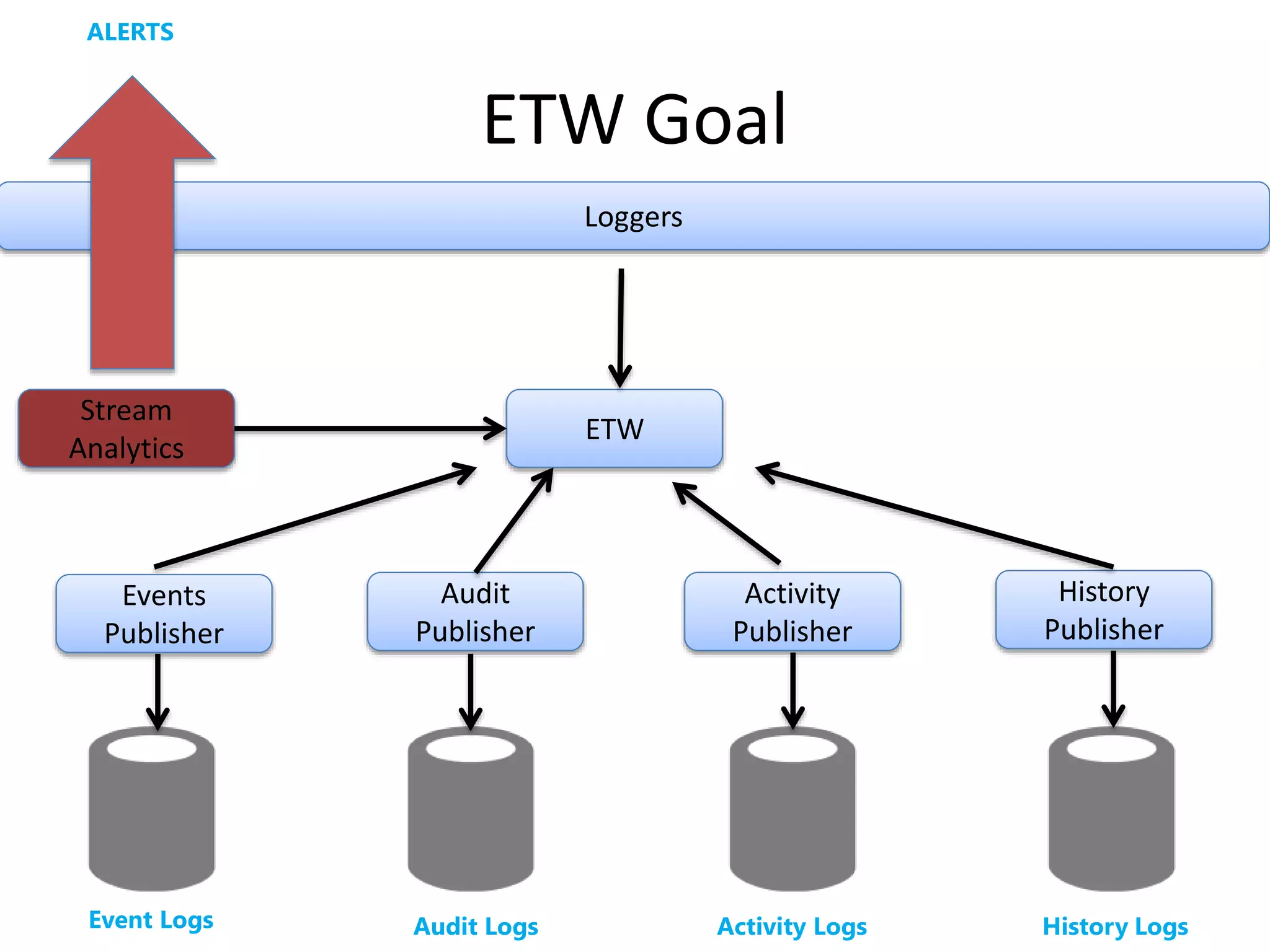
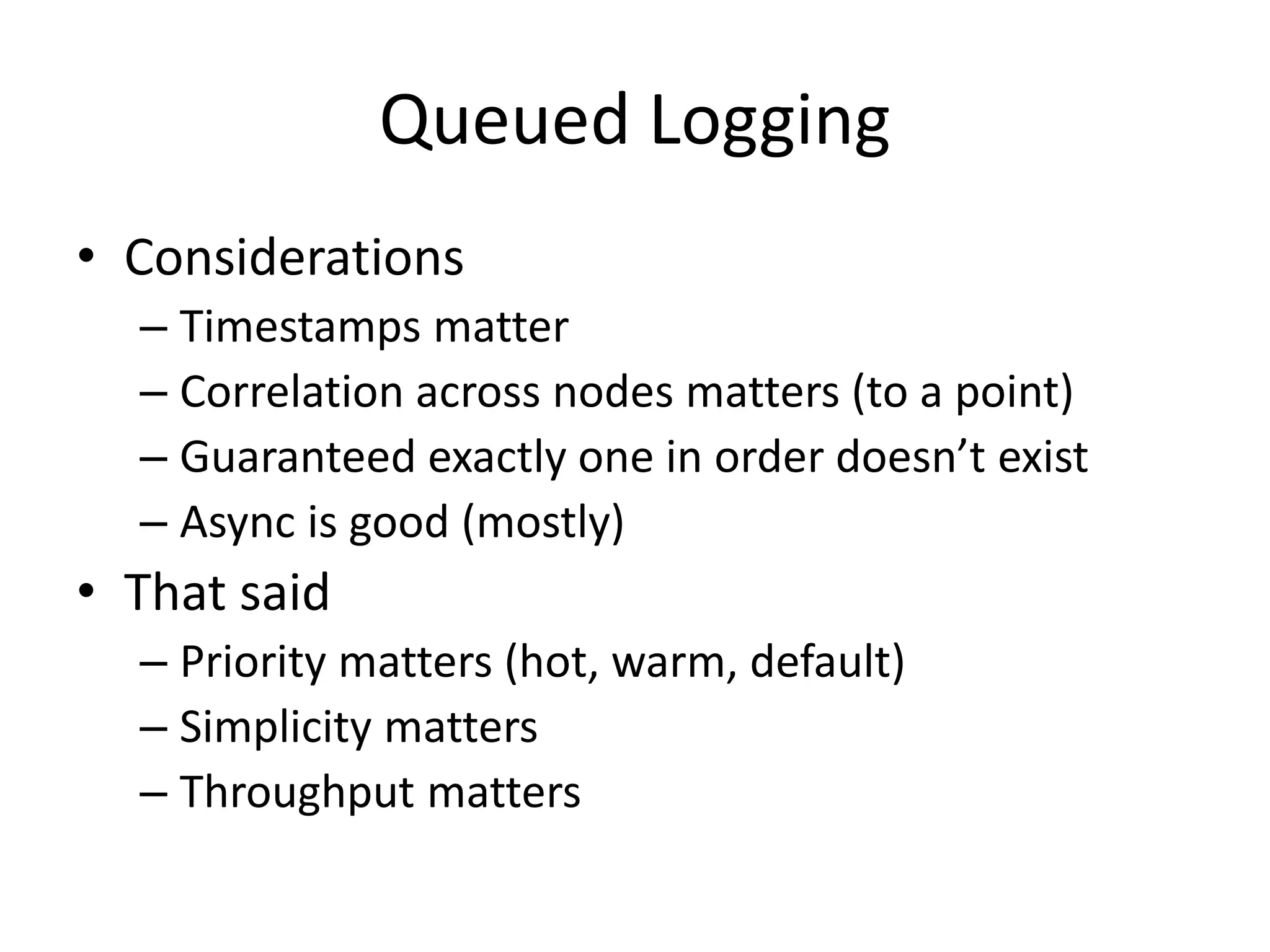
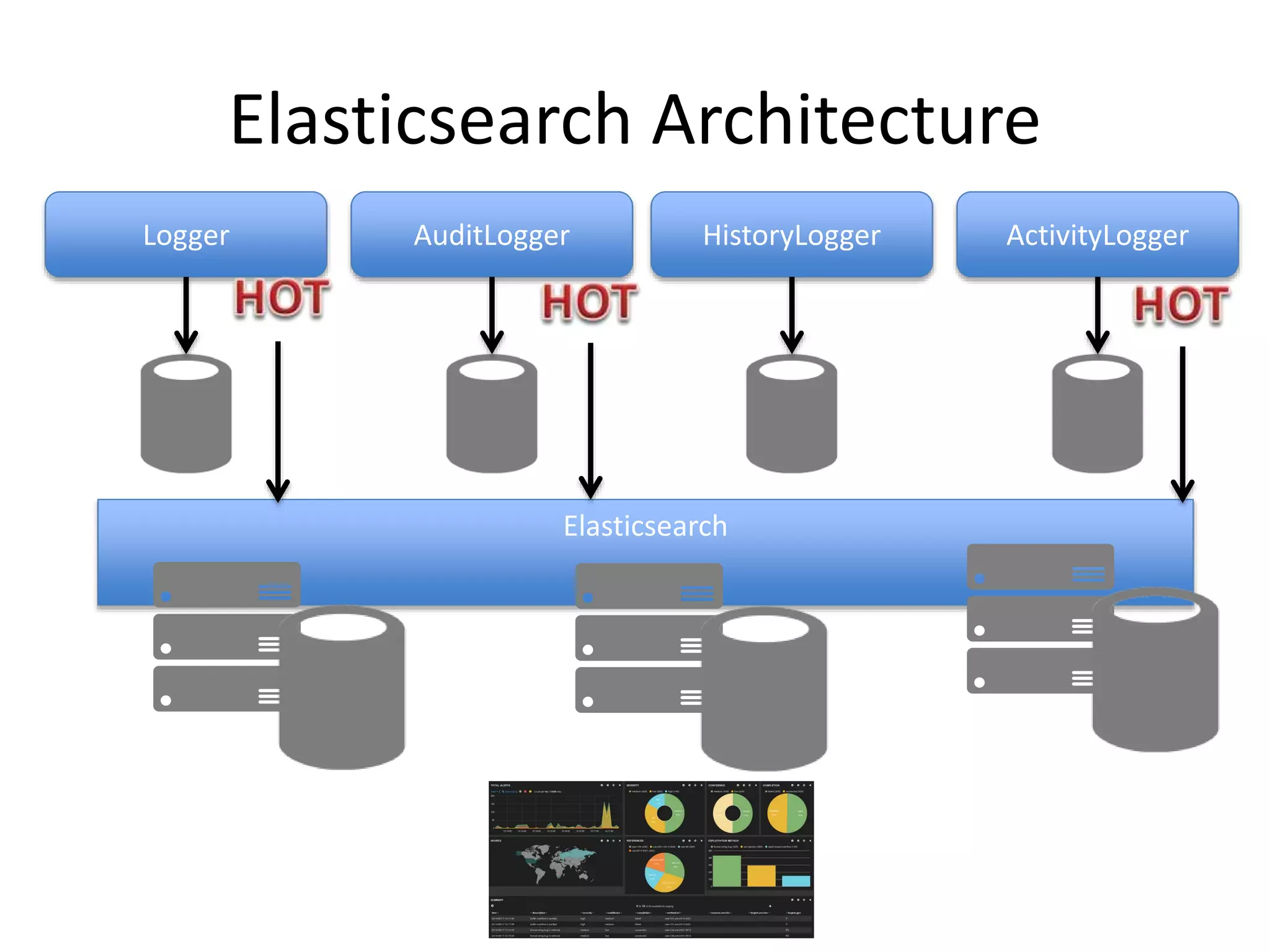
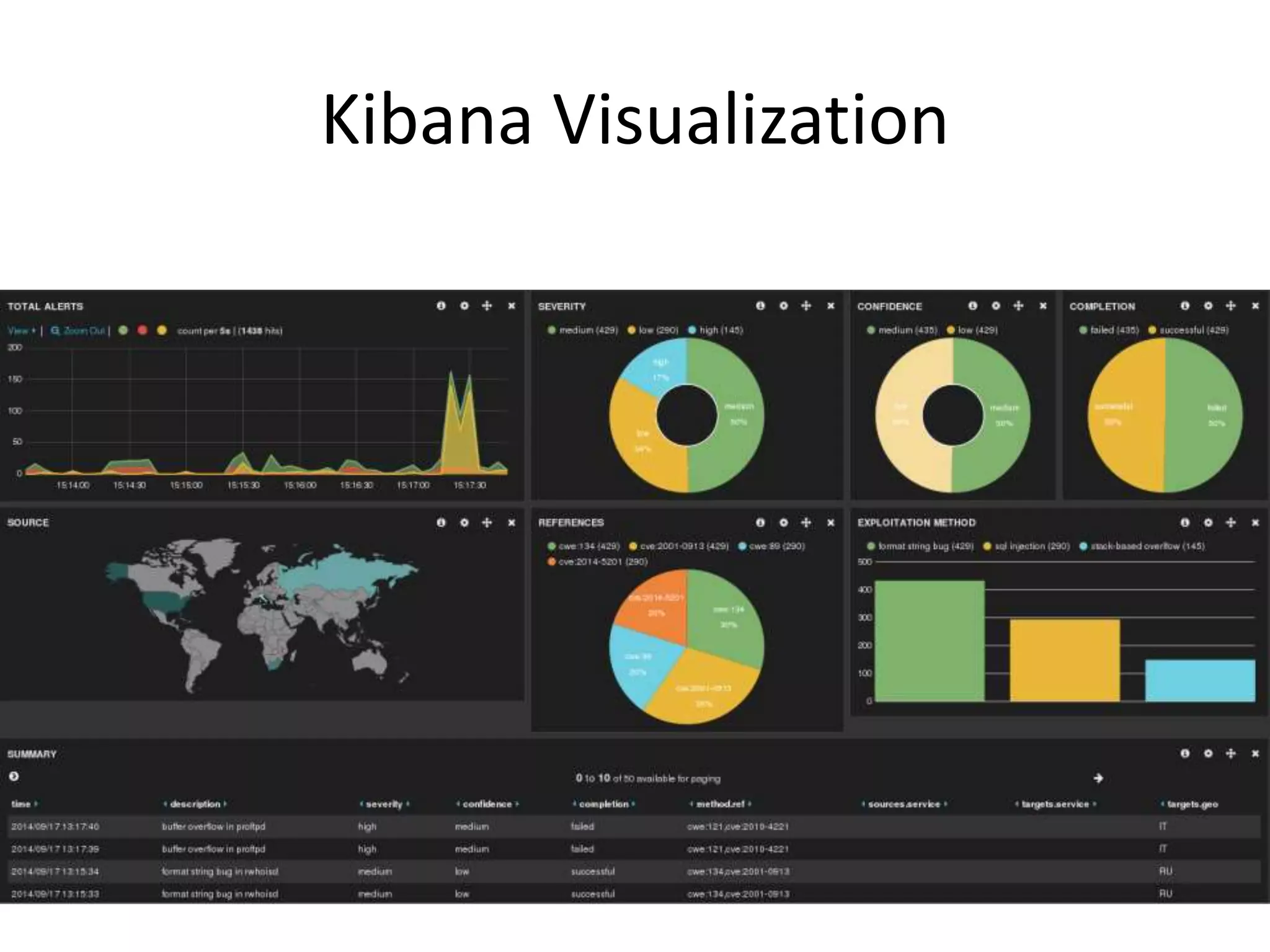
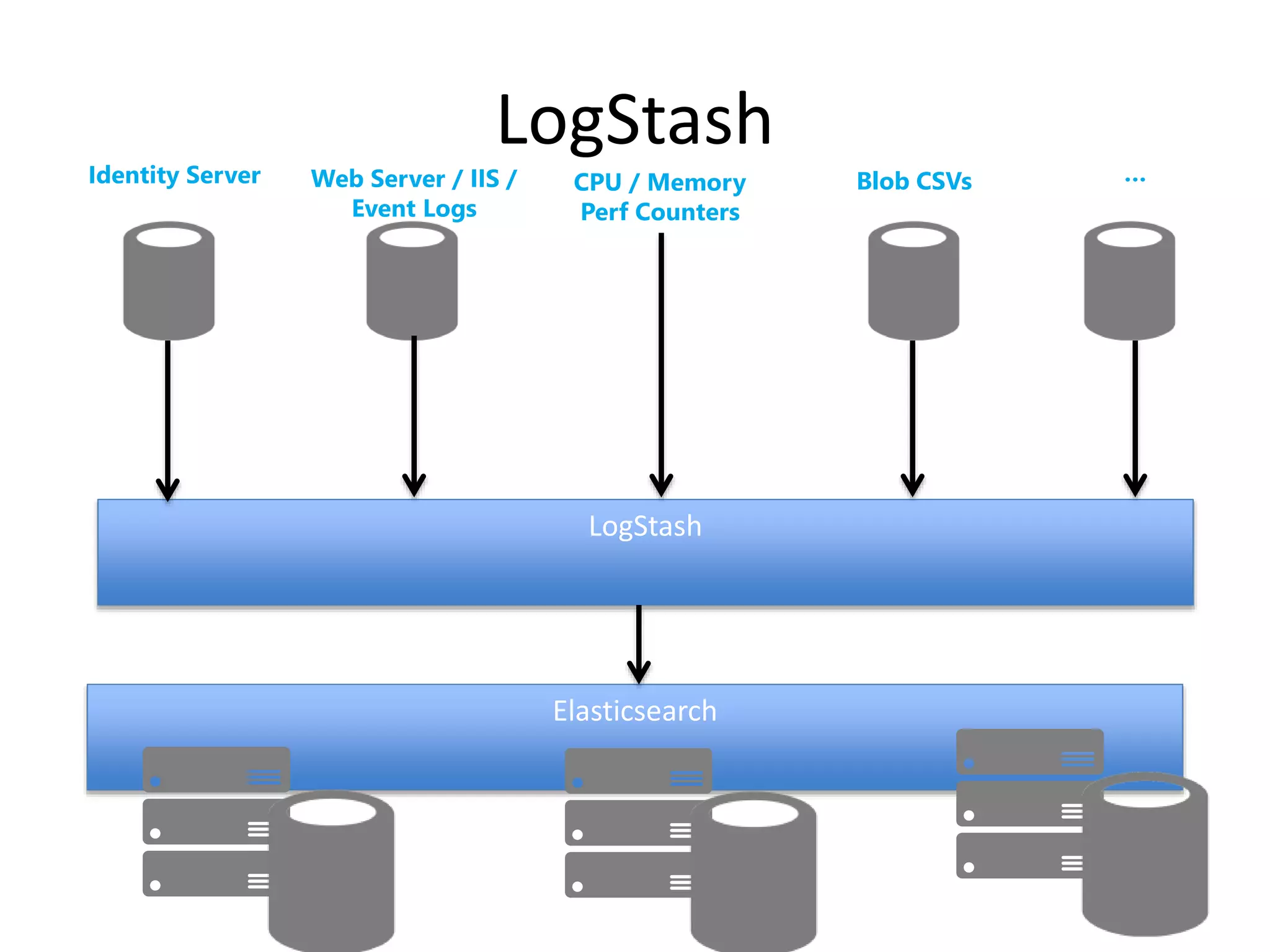
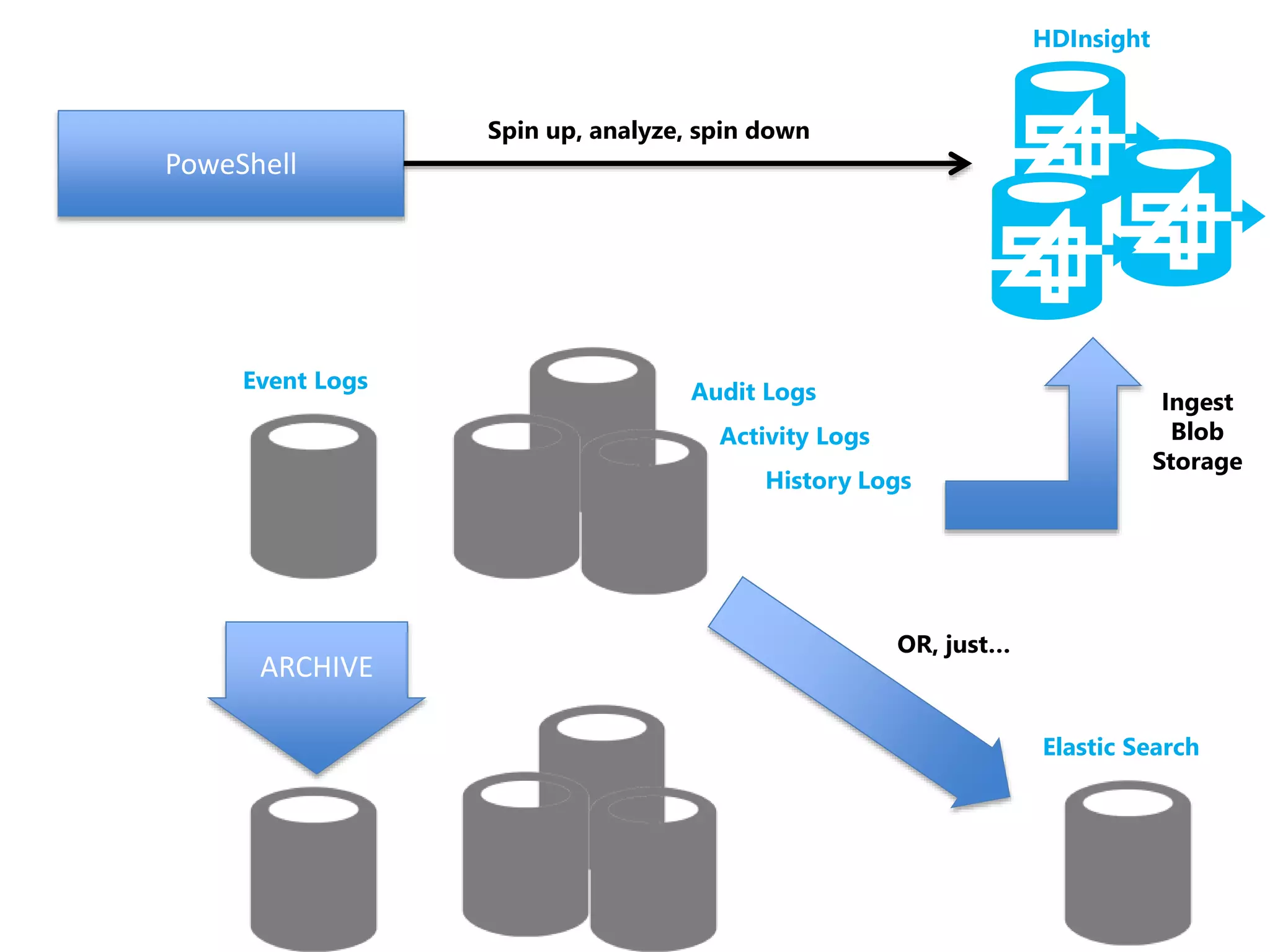
The document discusses comprehensive logging architecture essential for troubleshooting, security audits, and gaining insights into user activity. It outlines various types of logs, including event, audit, and activity logs, along with best practices for implementing logging mechanisms and ensuring compliance. Additionally, it emphasizes the importance of robust logging solutions that evolve over time and facilitate real-time analysis and archival processes.