Explore the major shift in MySQL 8.4 audit logging with Vinoth Kanna, Founding Partner at Mydbops, in this insightful edition of MyWebinar 45.
What you'll learn:
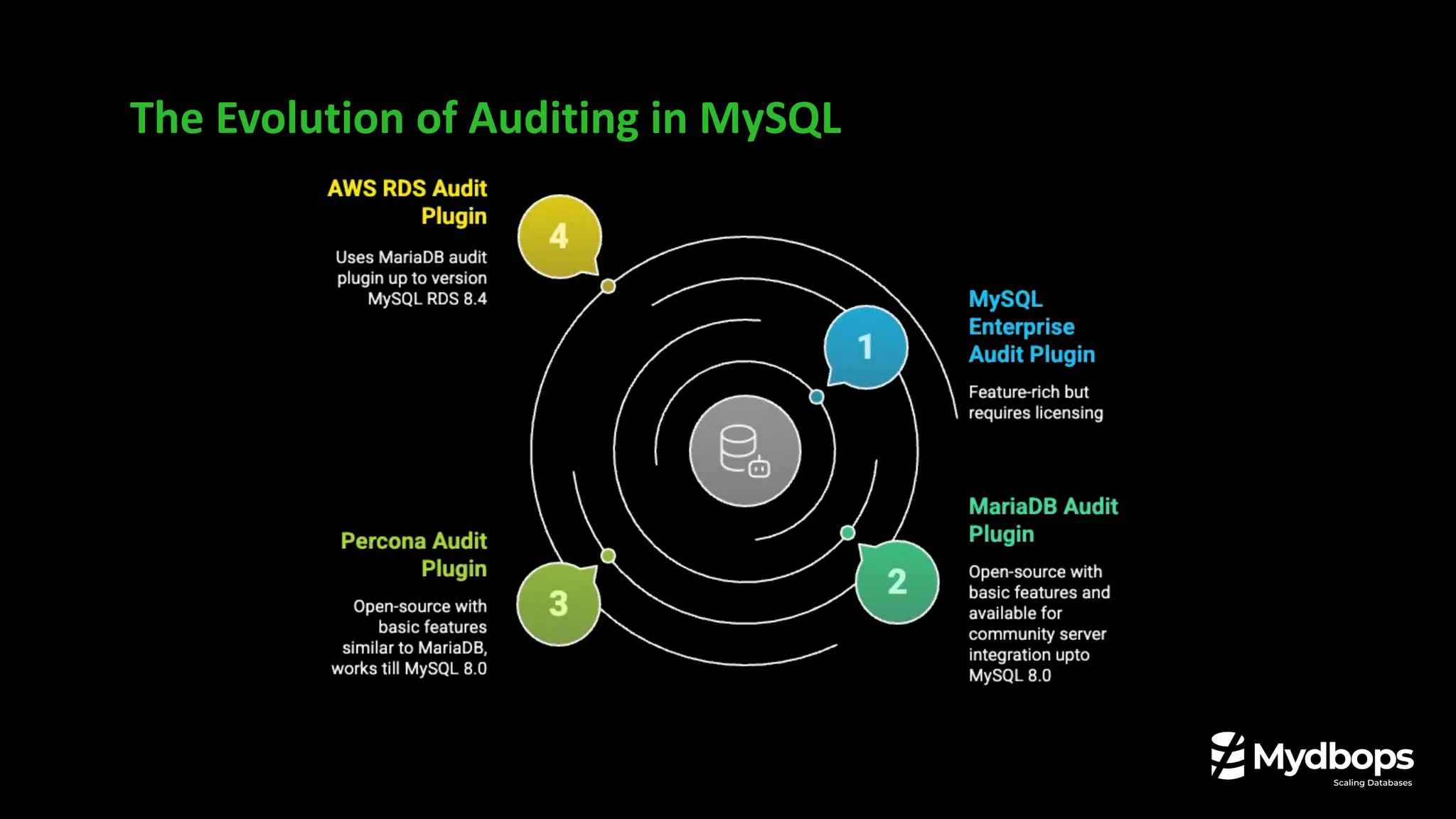
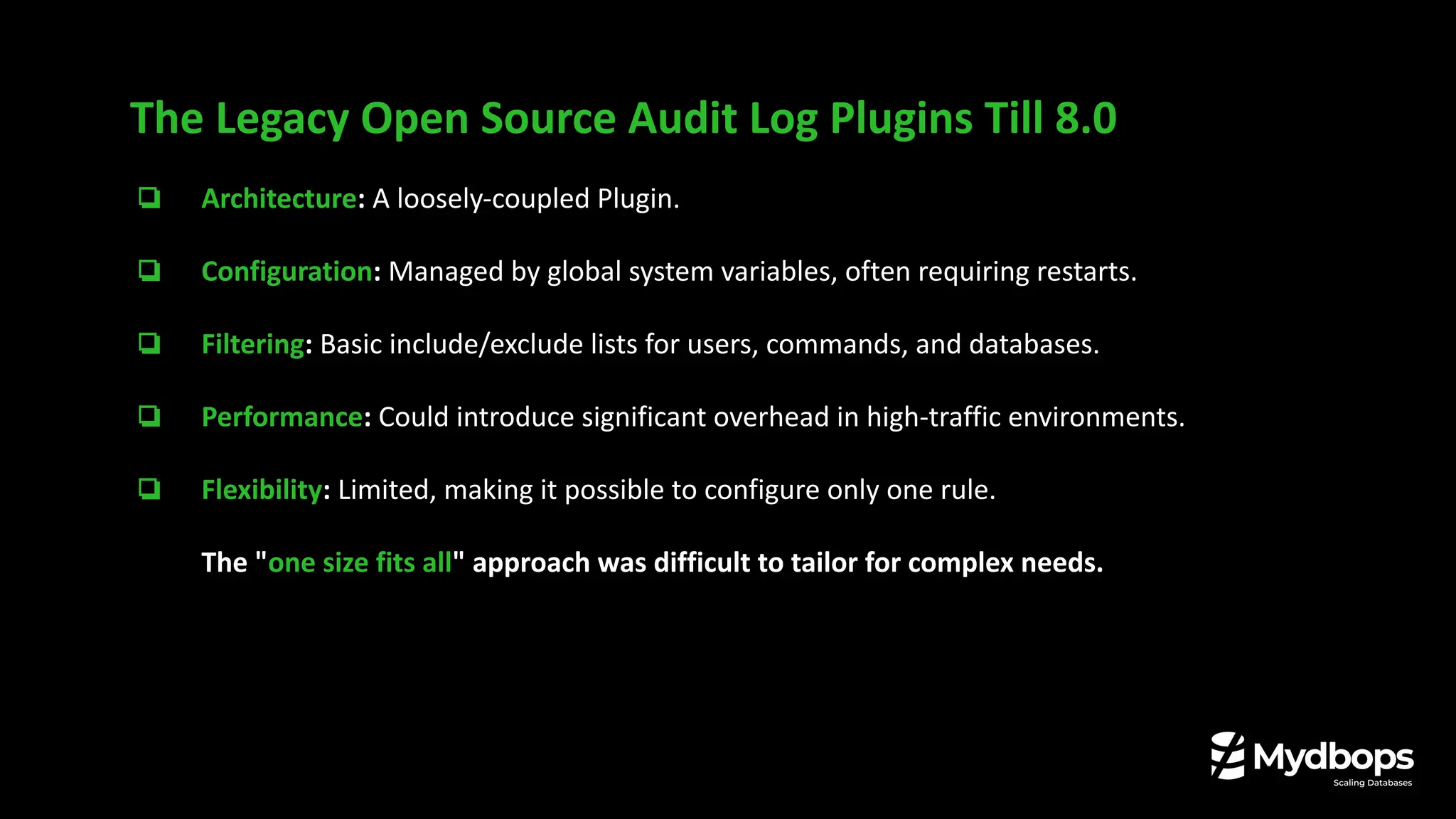
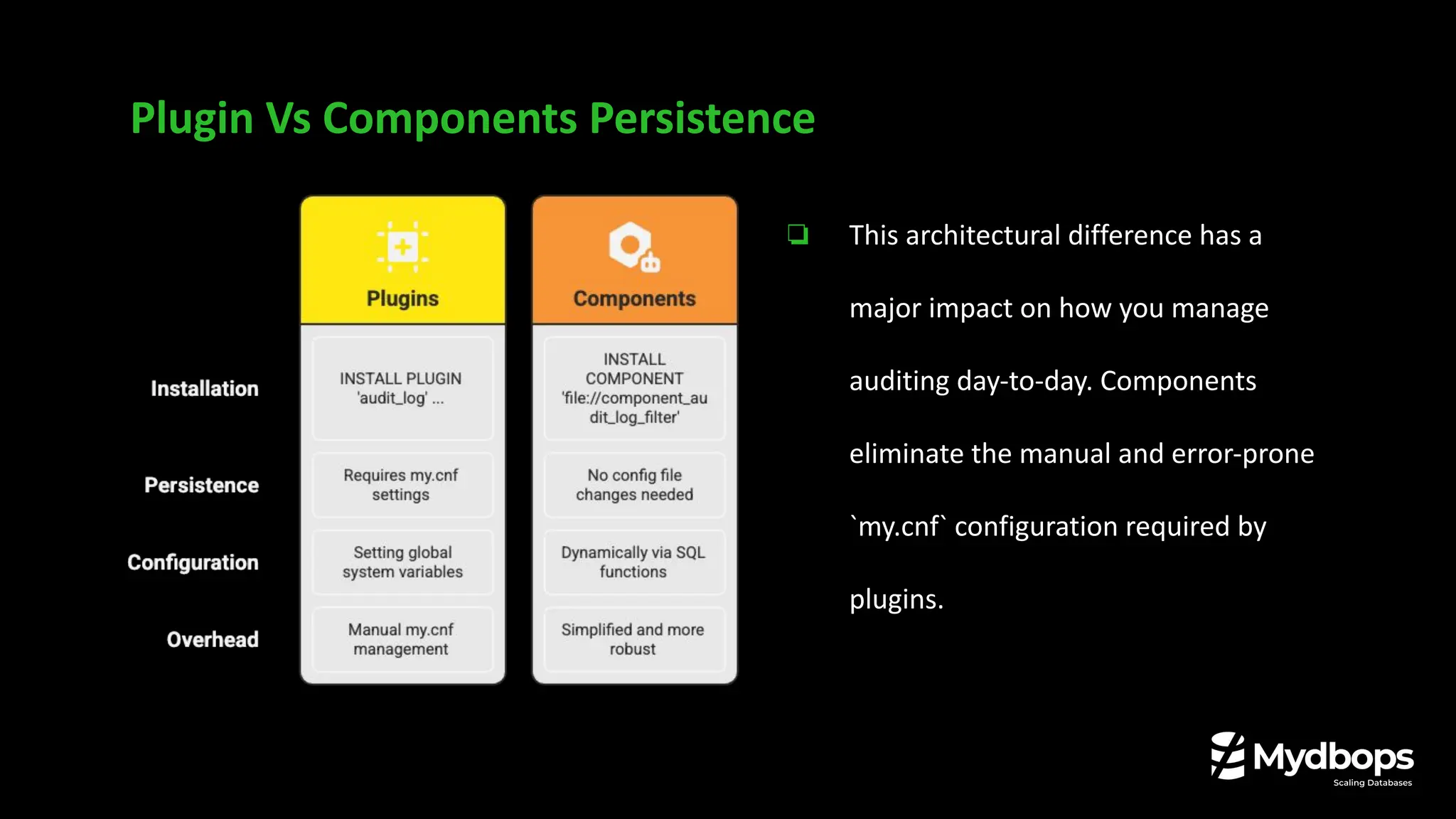
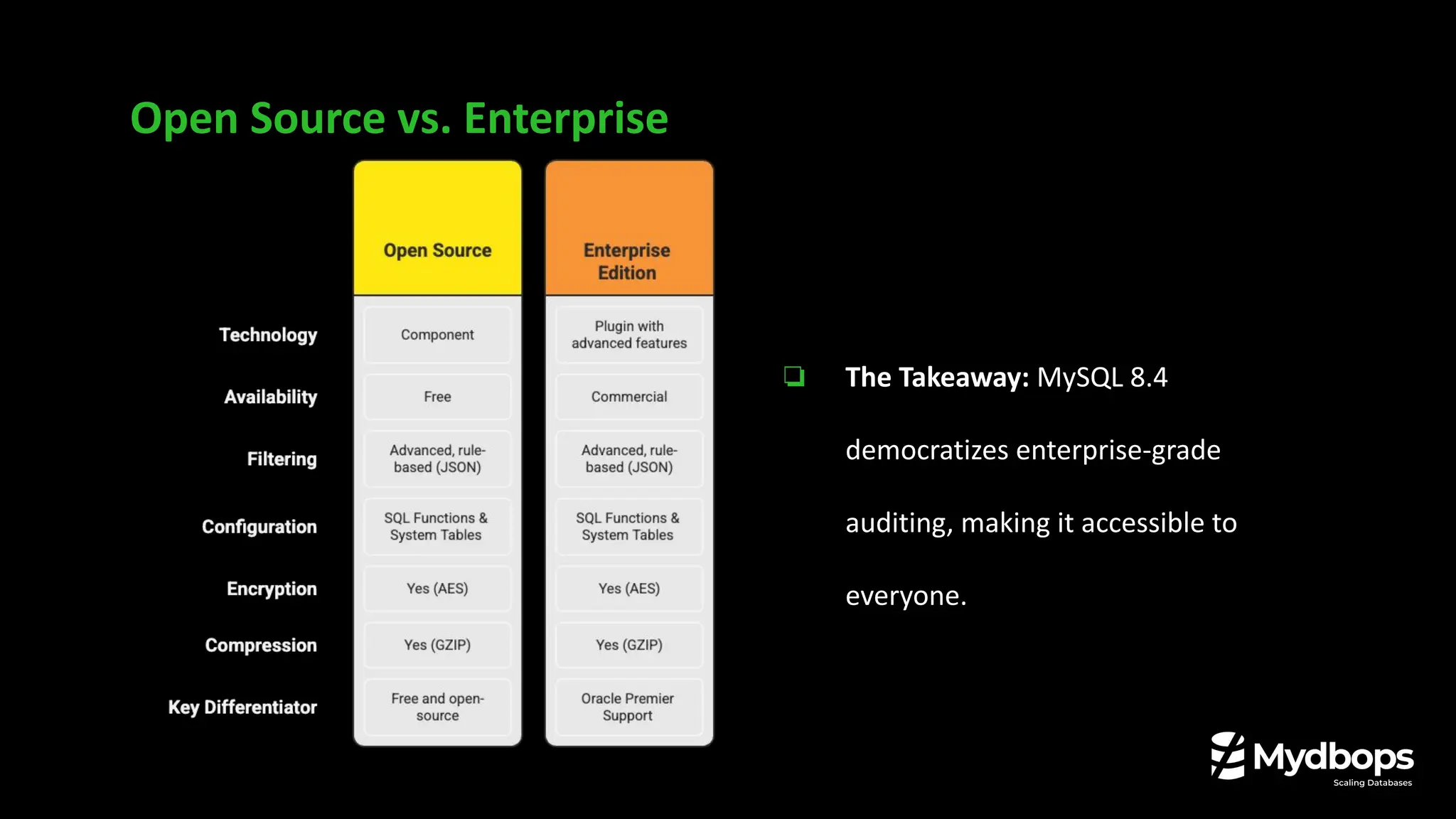
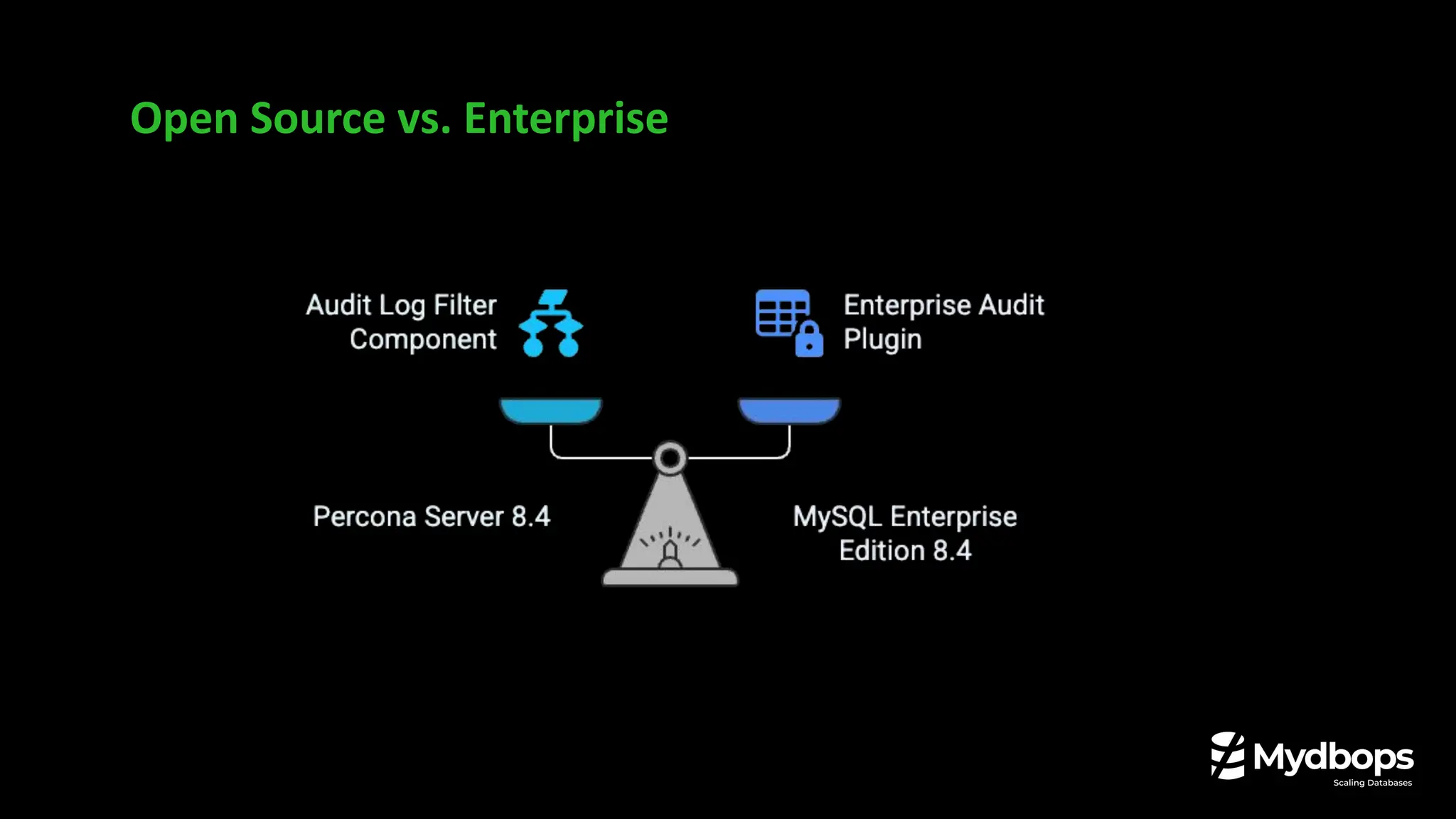
• Key differences between the Percona Audit Log Plugin and the new Audit Log Filter
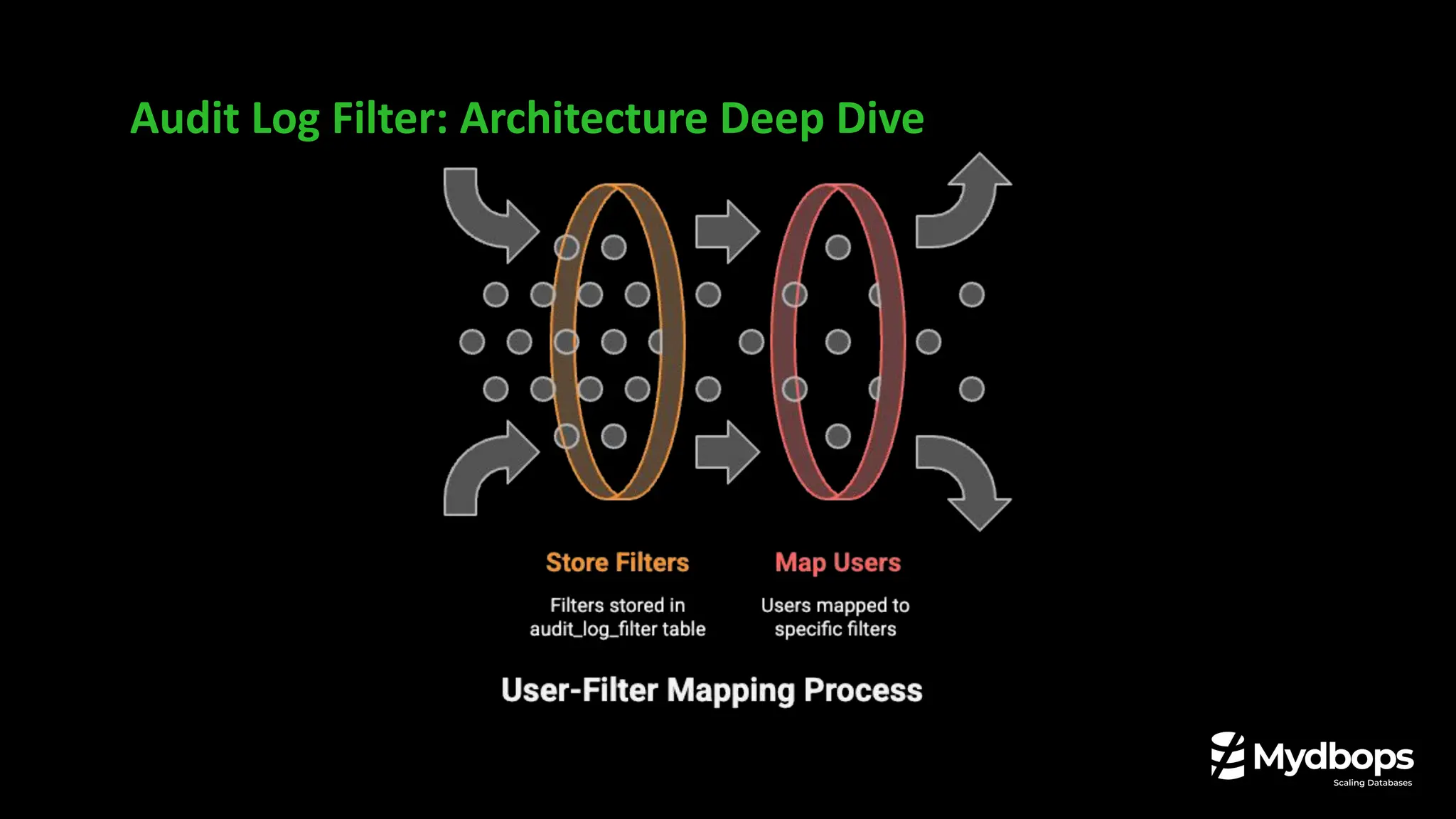
• How to configure and use the new Audit Log Filter
• Best practices for secure and compliant auditing
• Real-world security and compliance use cases
• Live Q&A insights from the expert
📌 Who should watch?
MySQL DBAs, Developers, DevOps, Architects, Security Engineers, Compliance Teams
About Mydbops:
Since 2015, Mydbops has been helping companies manage, secure, and optimize MySQL, MariaDB, MongoDB, PostgreSQL, TiDB and Cassandra environments. We provide consulting, managed services, support, and performance optimization tailored for your databases.
Contact us: info@mydbops.com
Visit: https://www.mydbops.com/
#MySQL #MySQL8 #Mydbops #DatabaseSecurity #AuditLogs #DBA #OpenSource #Webinar #Compliance #DevOps #Percona #CloudDatabases #DatabaseAuditing #MyWebinar










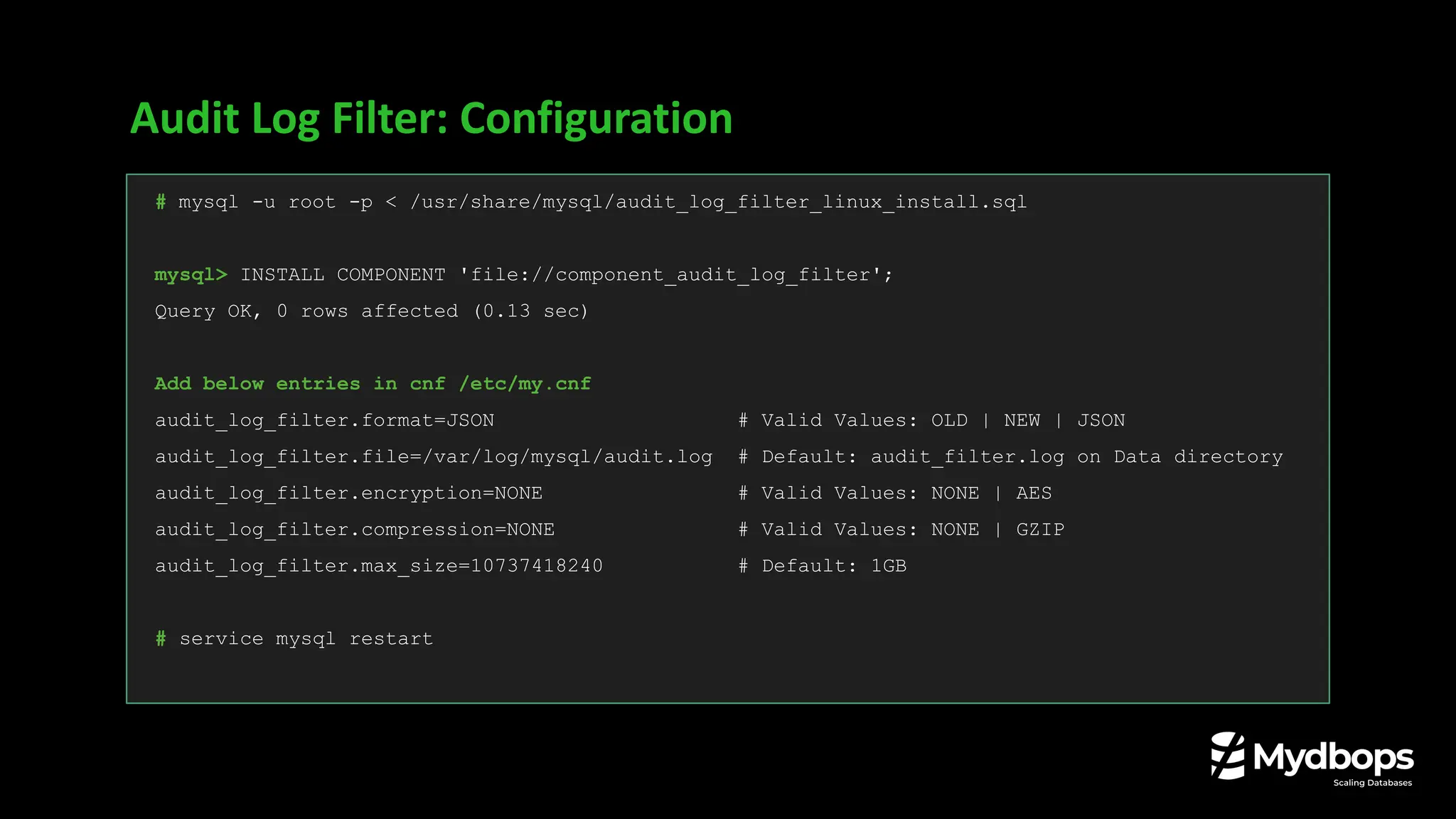
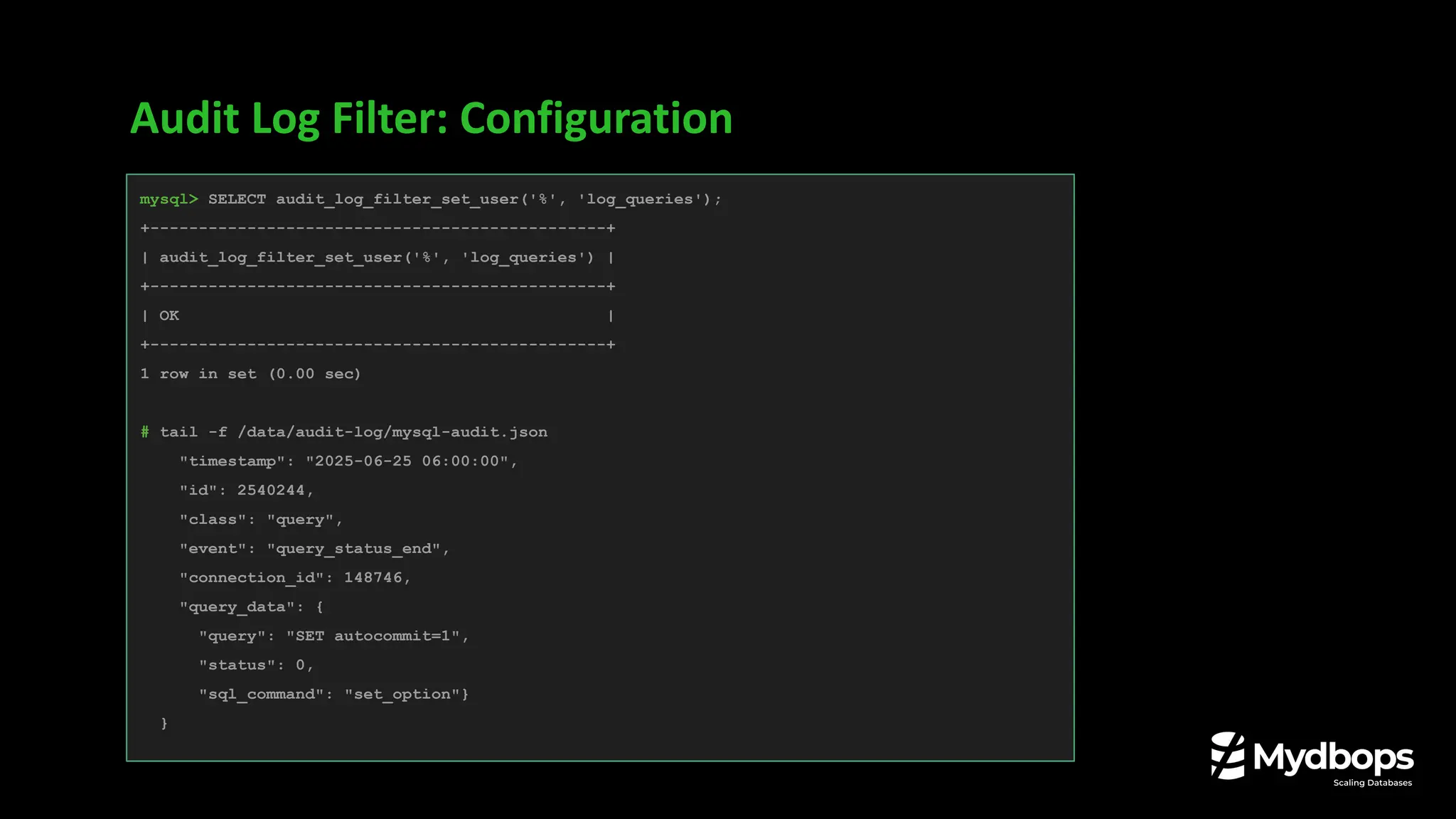
![Audit Log Filter: Configuration
# SELECT audit_log_filter_remove_filter( 'log_queries');
mysql> SELECT audit_log_filter_remove_filter('log_queries');
+-----------------------------------------------+
| OK |
+-----------------------------------------------+
mysql> SET @fj = '{ "filter": { "class": [ { "name": "connection", "event": [{"name":
"connect"}, {"name": "disconnect"}] }, { "name": "table_access", "operation": [{"name":
"read"}, {"name": "write"}, {"name": "dcl"}, {"name": "ddl"}] }, { "name": "query" } ] }}';
Query OK, 0 rows affected (0.00 sec)
mysql> SELECT audit_log_filter_set_filter('log_queries',@fj);
+------------------------------------------------------+
| OK |
+------------------------------------------------------+](https://image.slidesharecdn.com/mydbops-secureauditlogsinmysql8-250926093532-cec1d7c5/75/Secure-Audit-Logs-in-MySQL-8-4-Vinoth-Kanna-Mydbops-Webinar-45-20-2048.jpg)