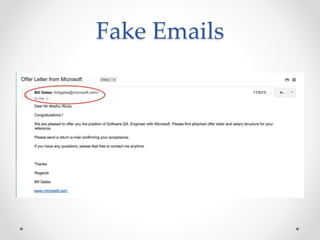
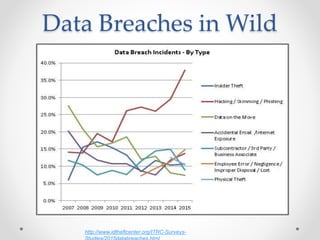
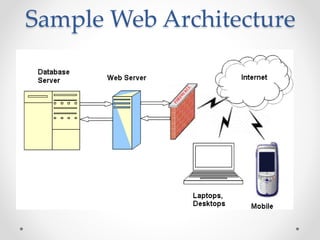
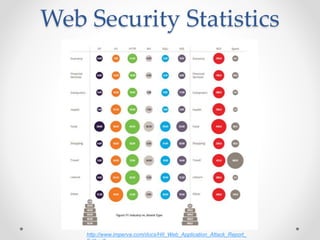
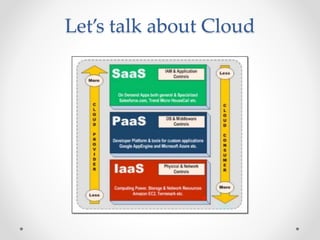
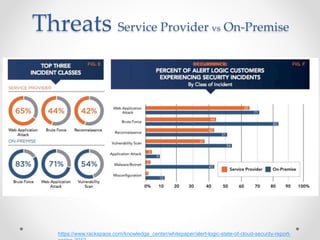
This document discusses web and cloud security challenges. It begins with an introduction of the speaker and their background in security research. Various web attacks like SQL injection, cross-site scripting, and remote code execution are explained. Cloud security threats from misconfigured applications and infrastructure are also examined, including real-world examples. Best practices for hardening systems and securing data in the cloud are provided. Resources for further learning about web and cloud security are listed at the end.