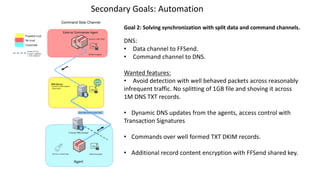
The document summarizes a technique for delivering payloads across networks with robust inspection mechanisms. It proposes using Firefox Send for private, encrypted file sharing to deliver payloads. Payloads are encrypted client-side using the WebCrypto API and can be decrypted in any browser. Notification of the encrypted file link is done over alternate covert channels like DNS to avoid inspection. A Python-based C2 framework called Foxtrot is demonstrated which uses Firefox Send for the payload delivery channel and DNS for the command and control channel to automate payload delivery between agent systems.