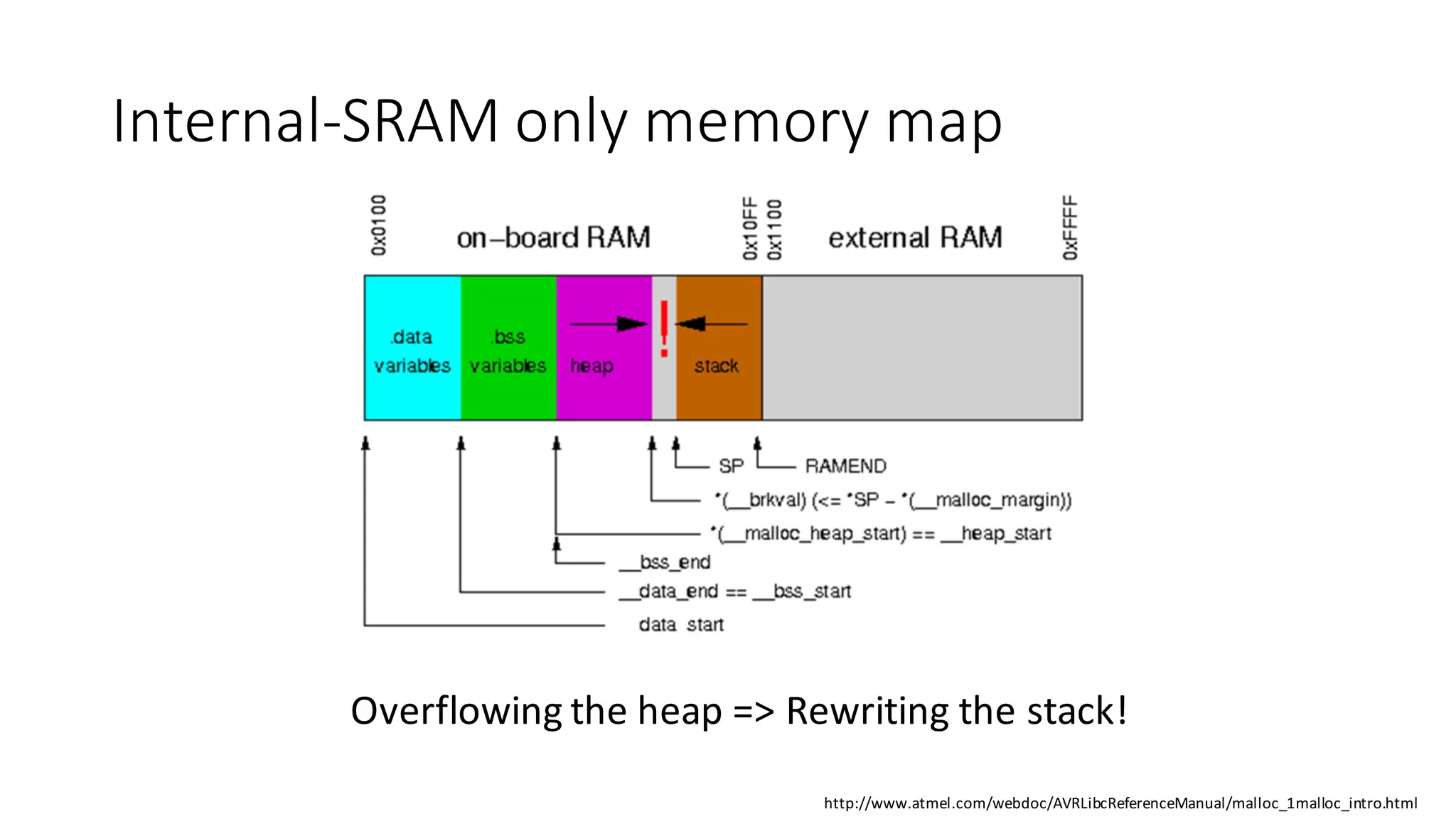
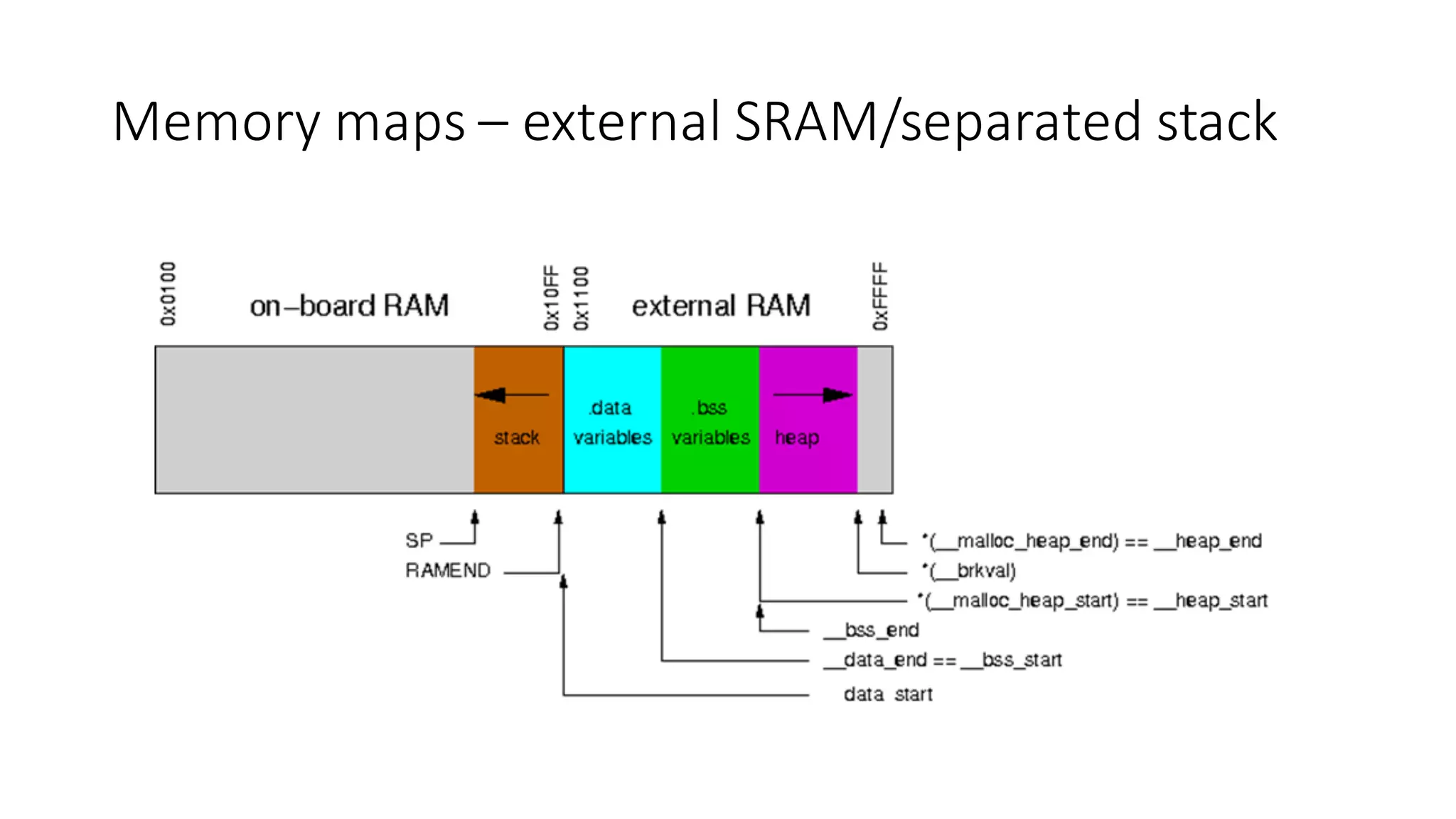
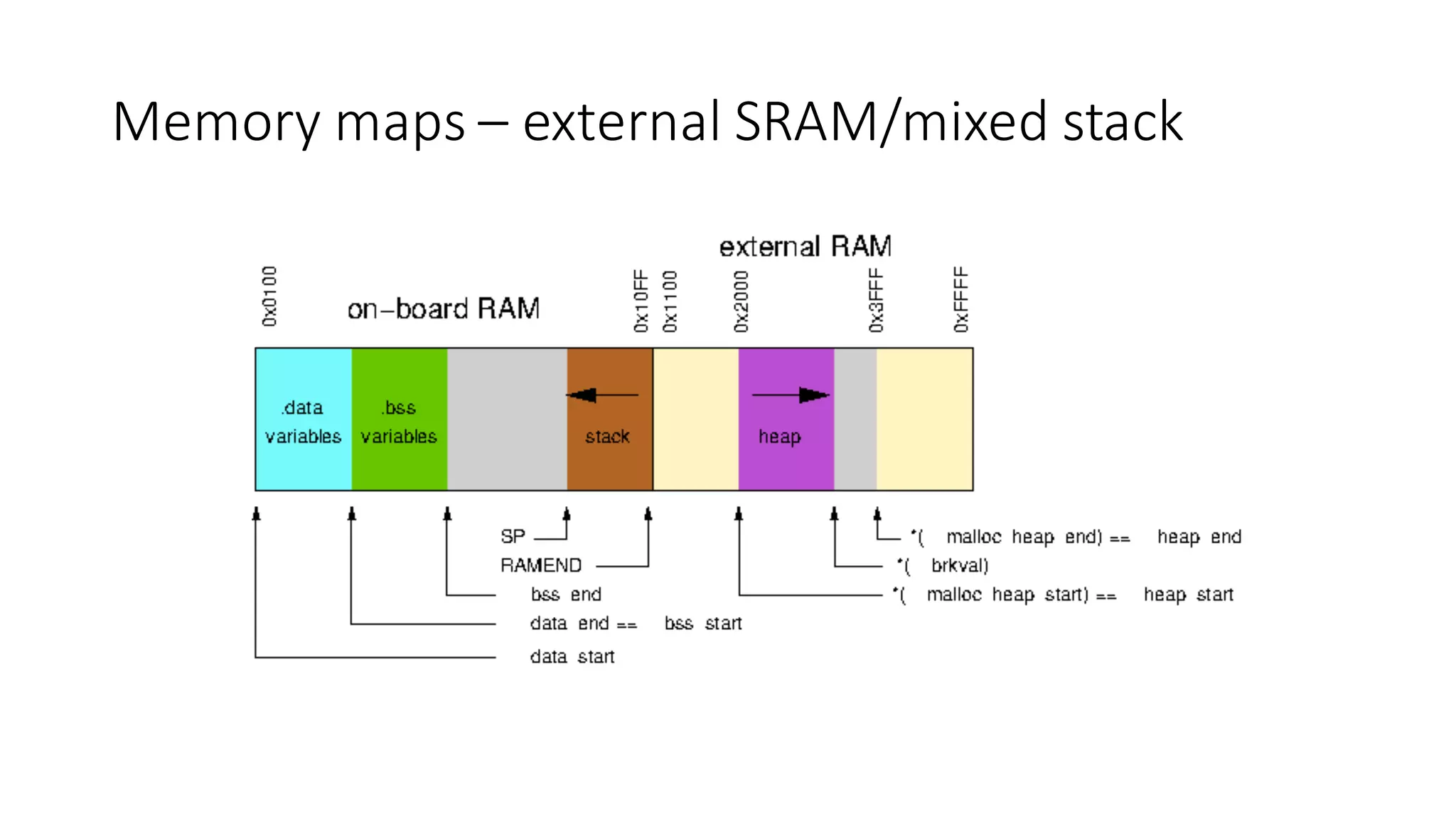
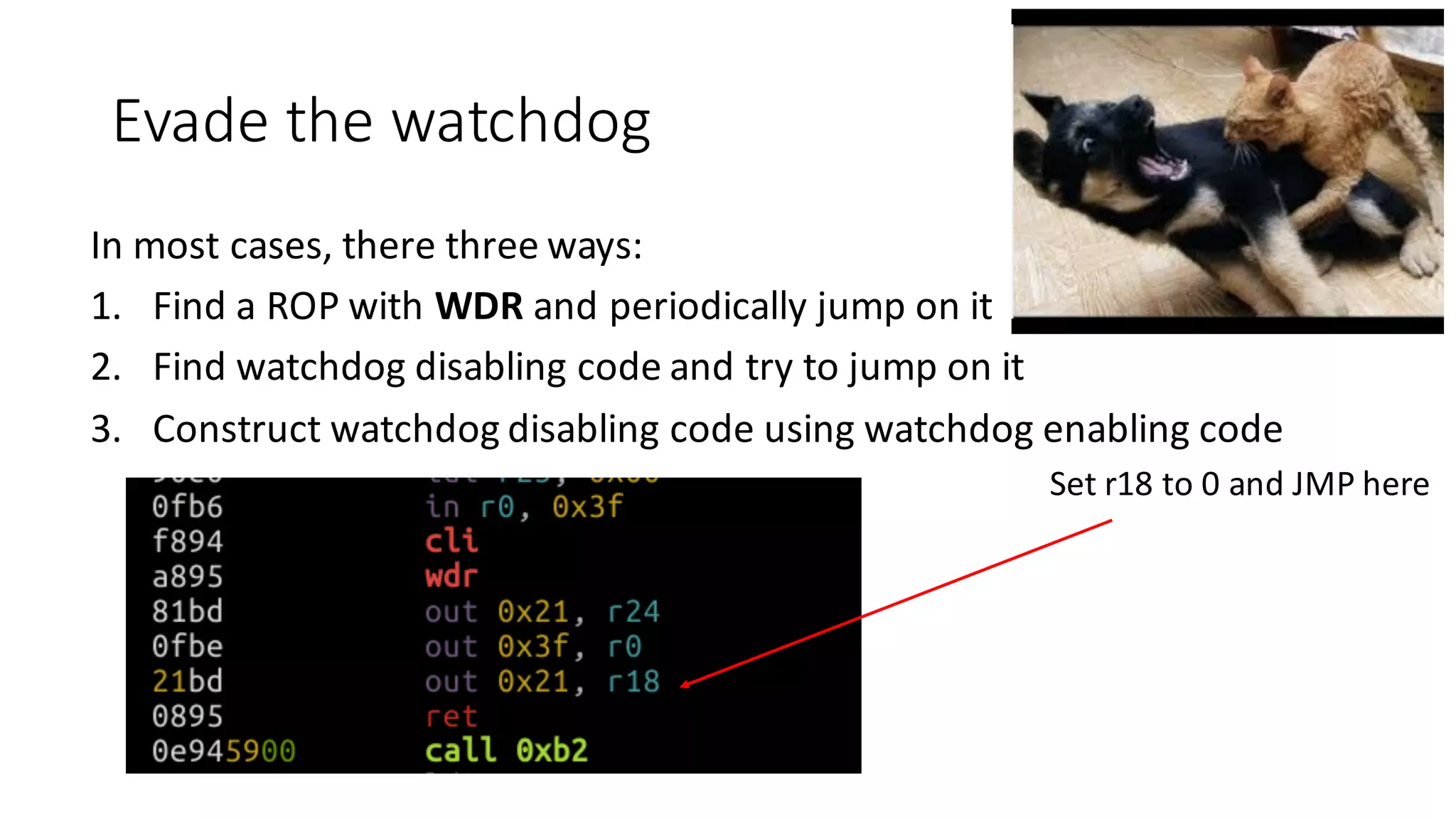
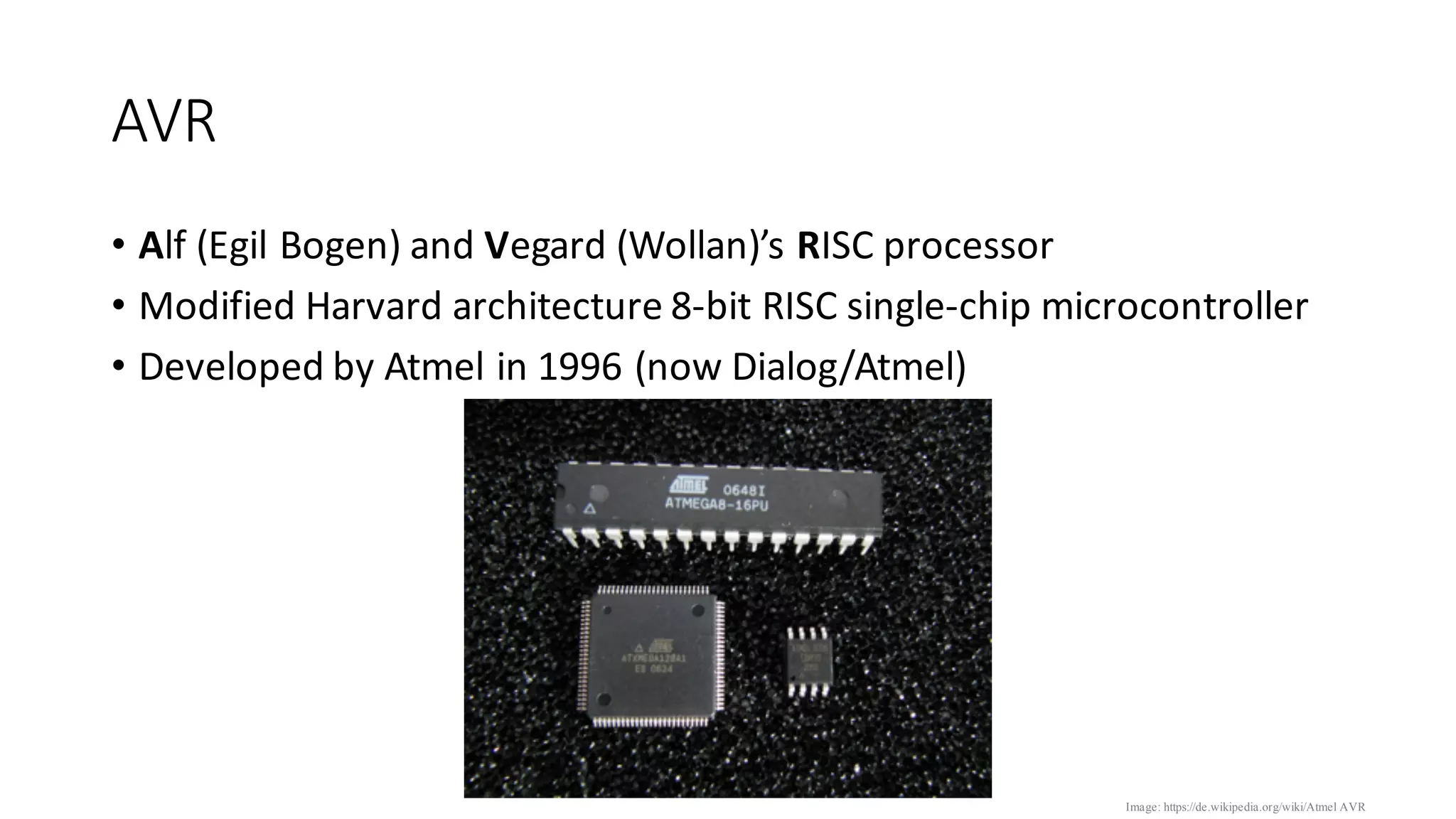
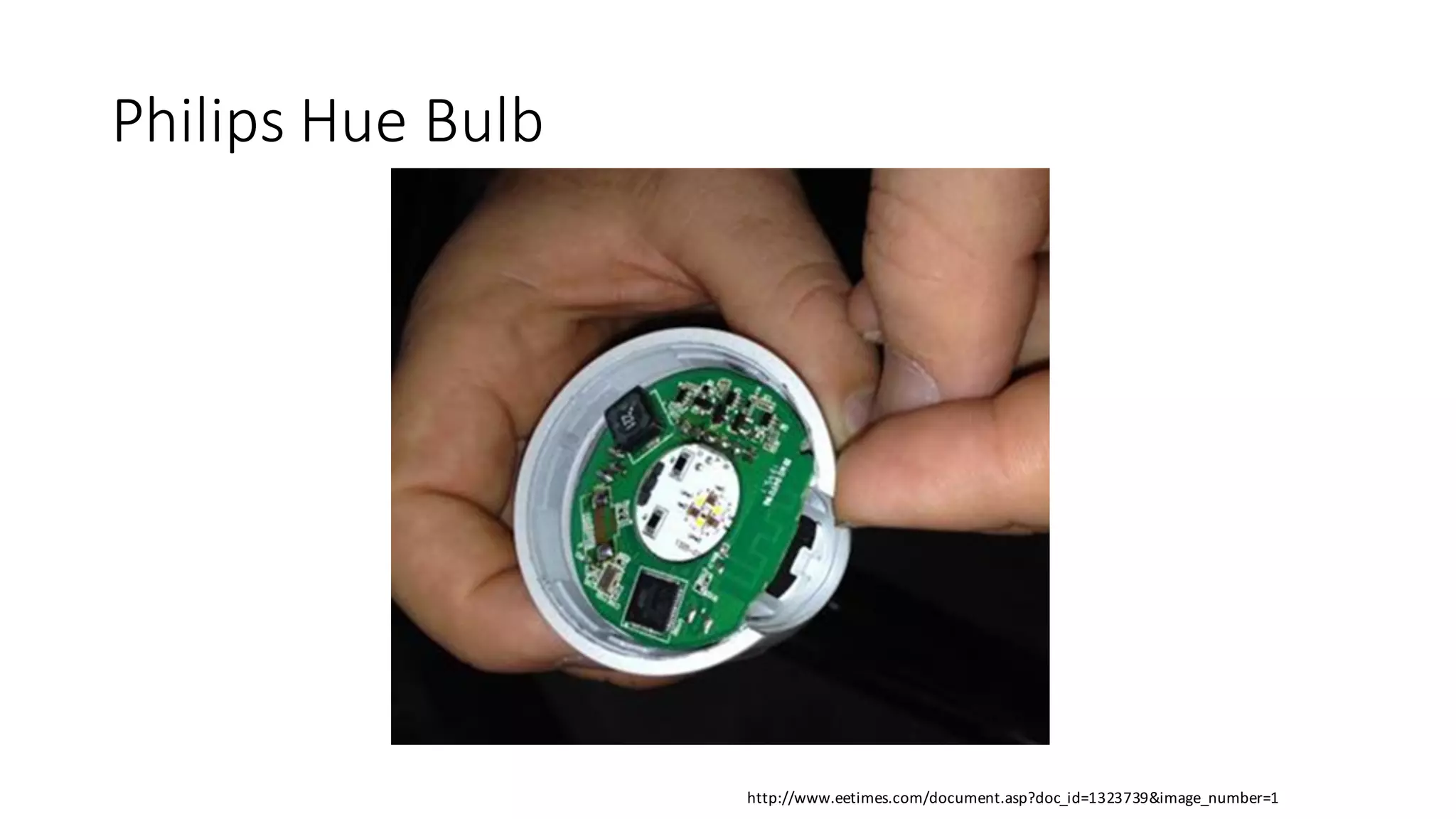
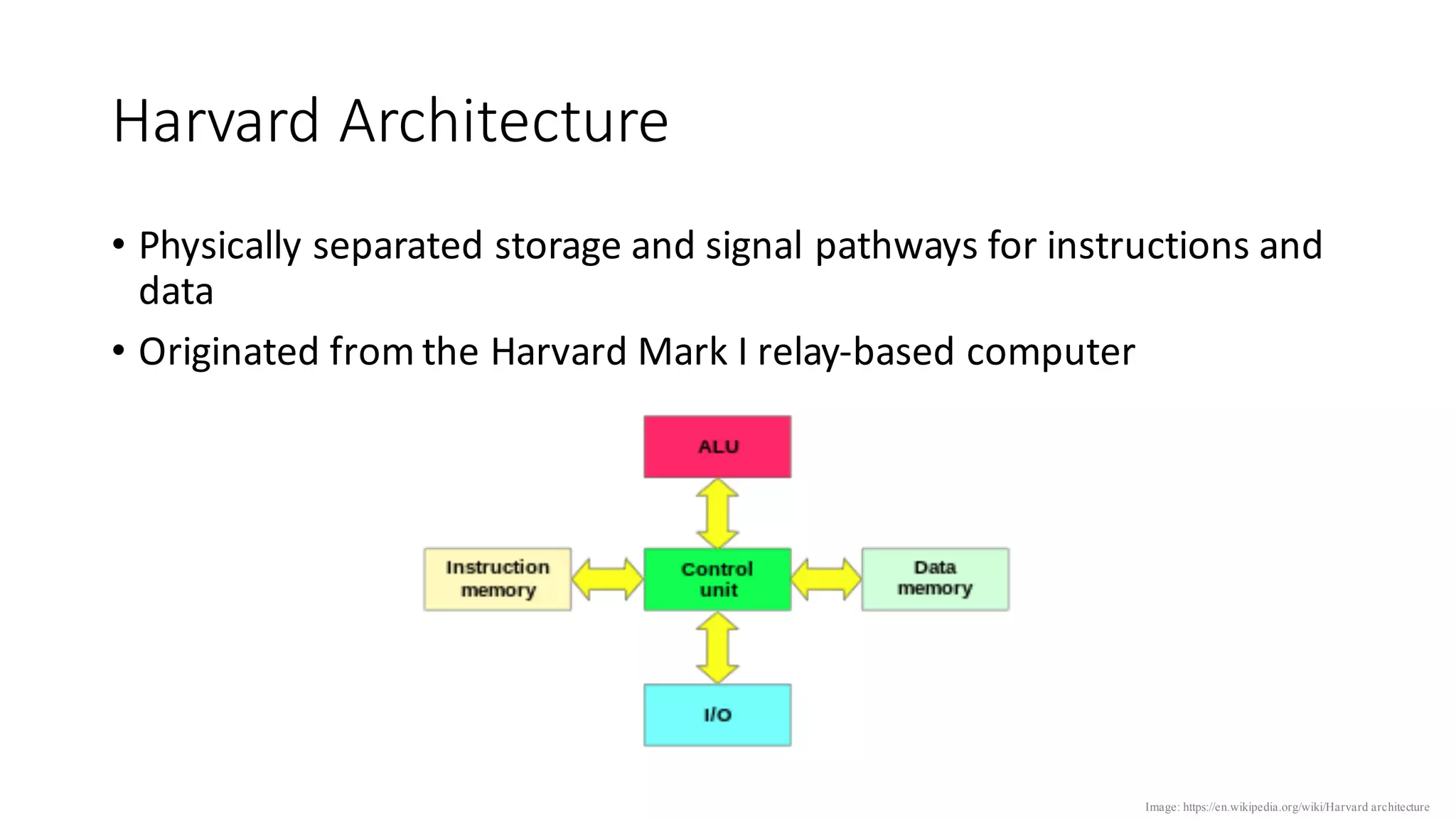
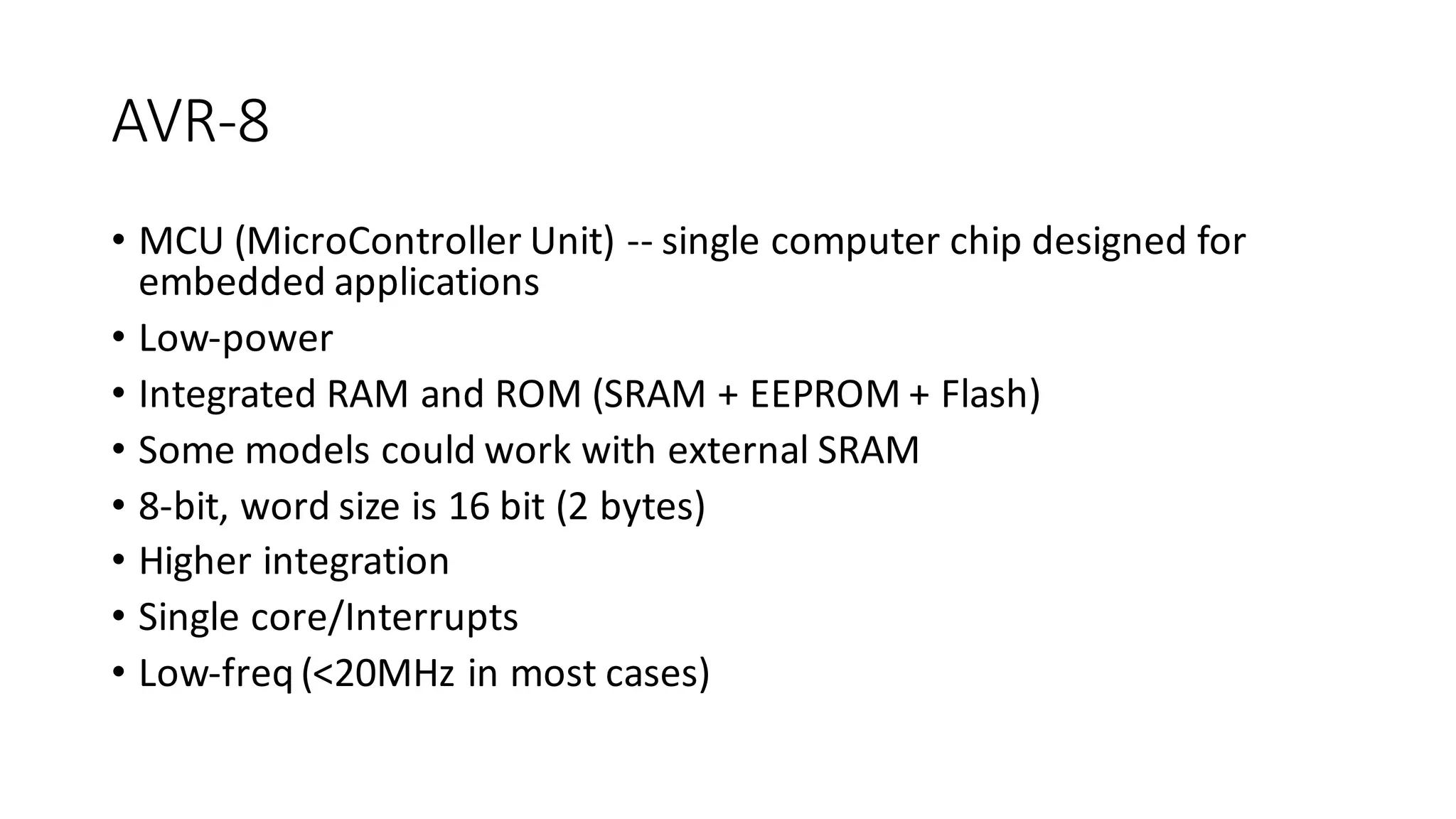
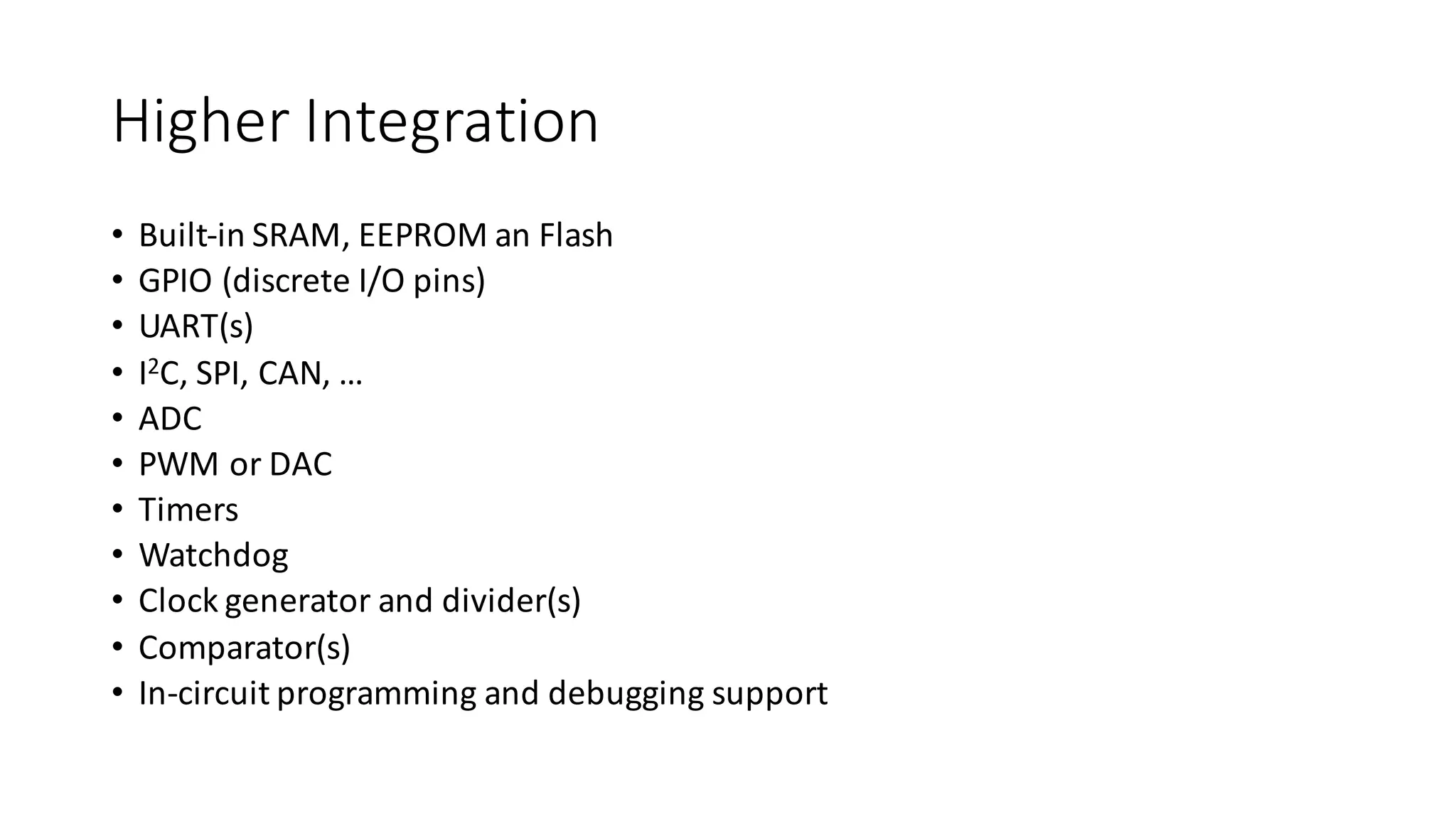
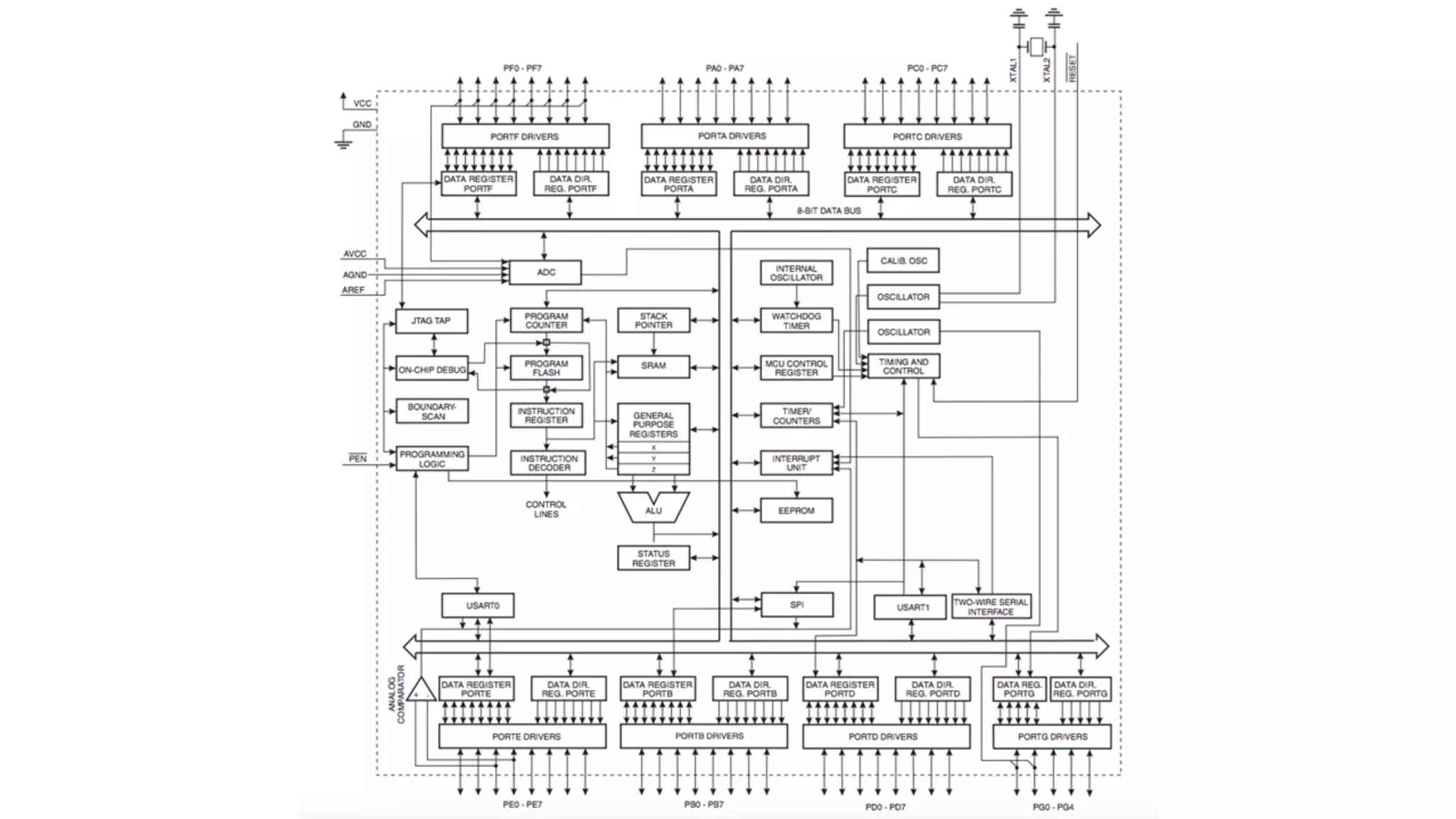
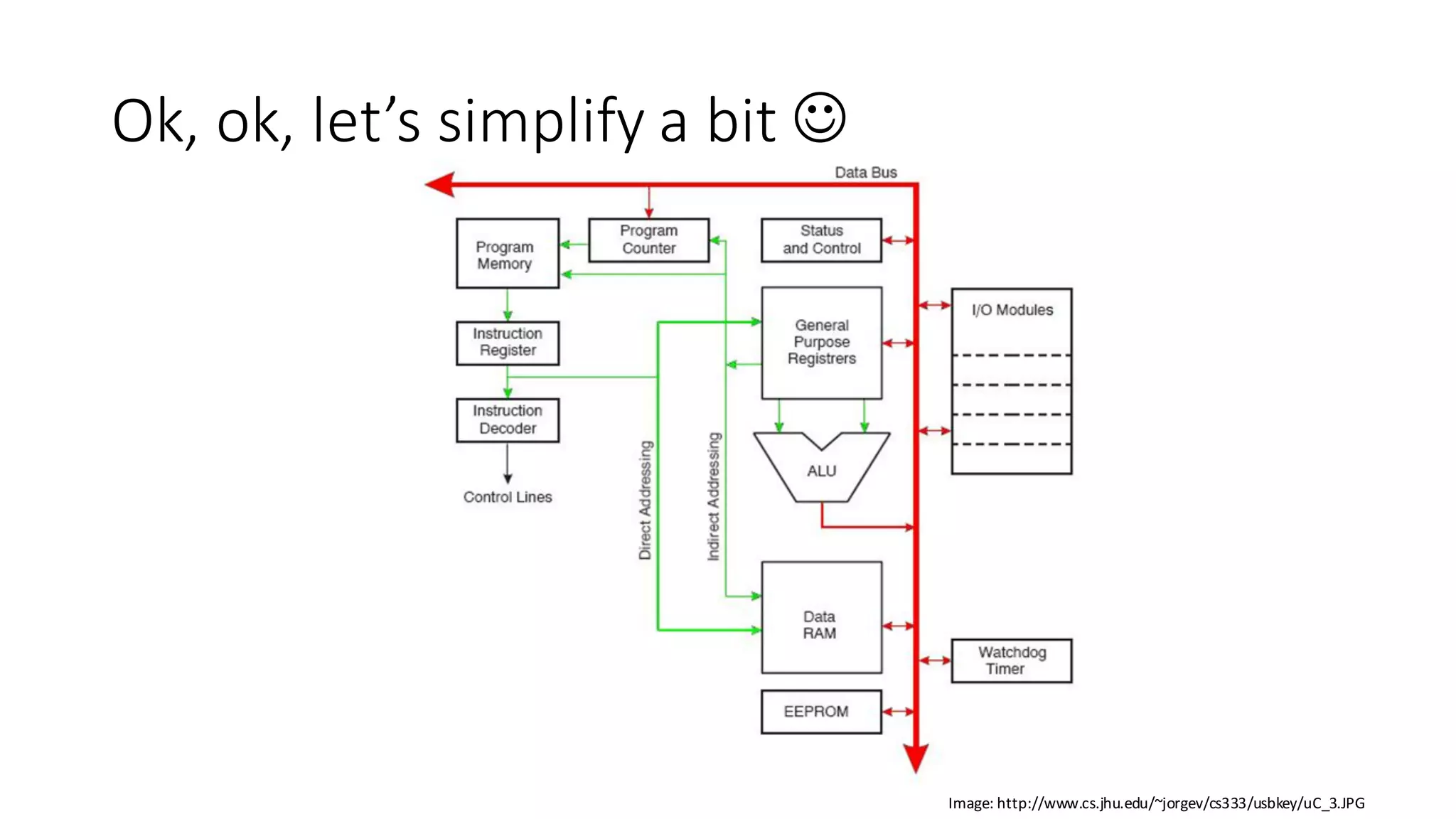
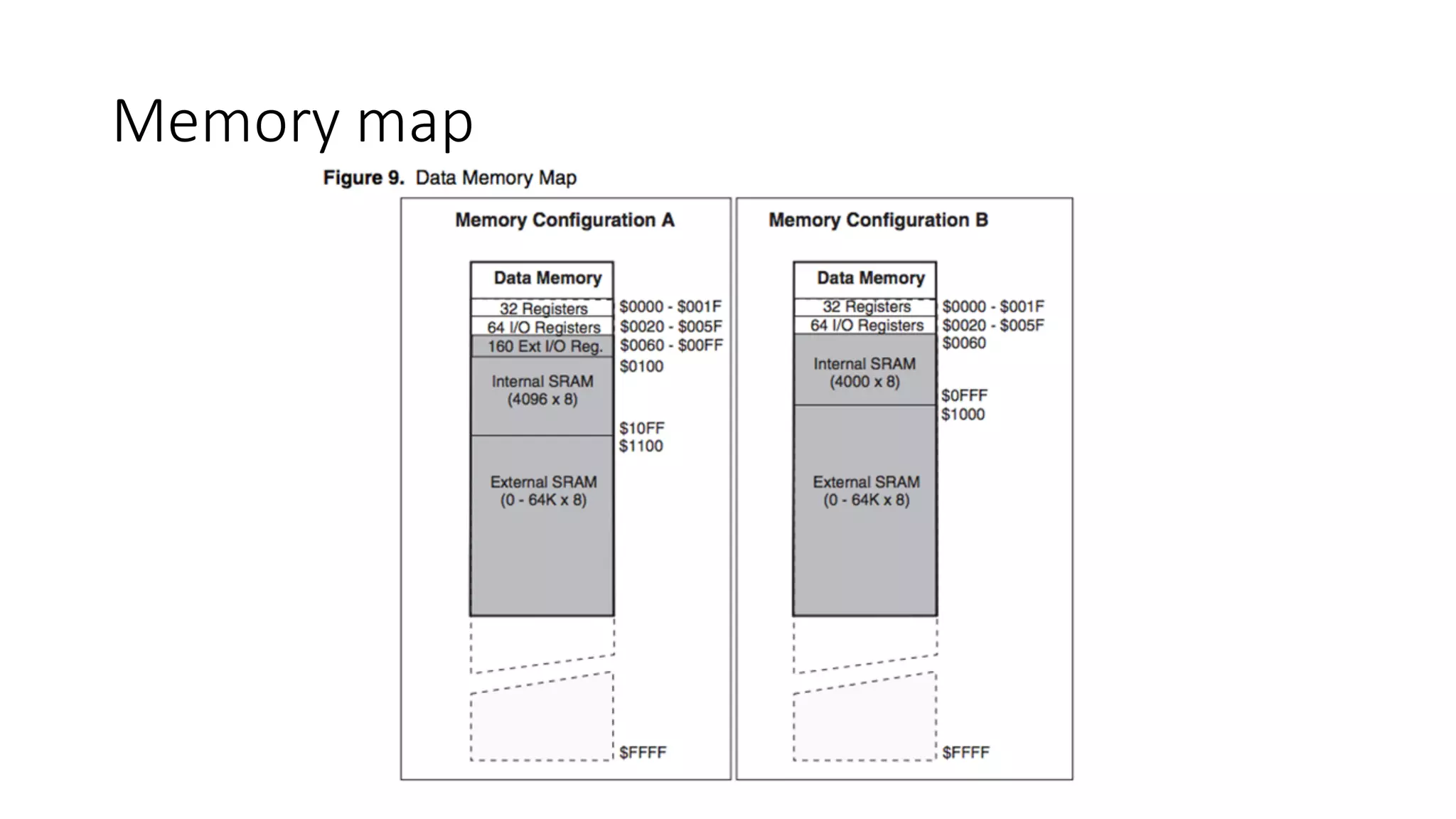
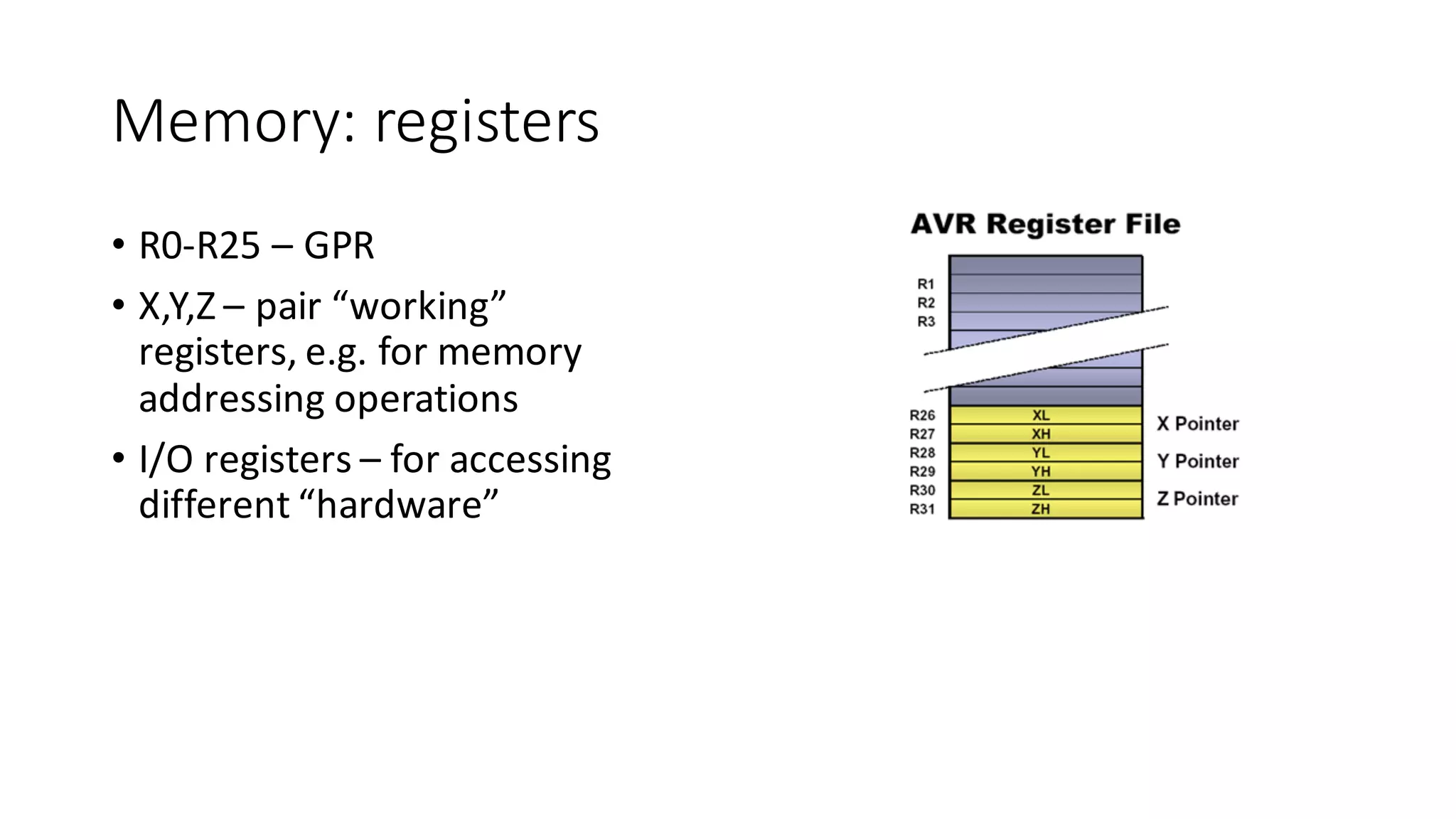
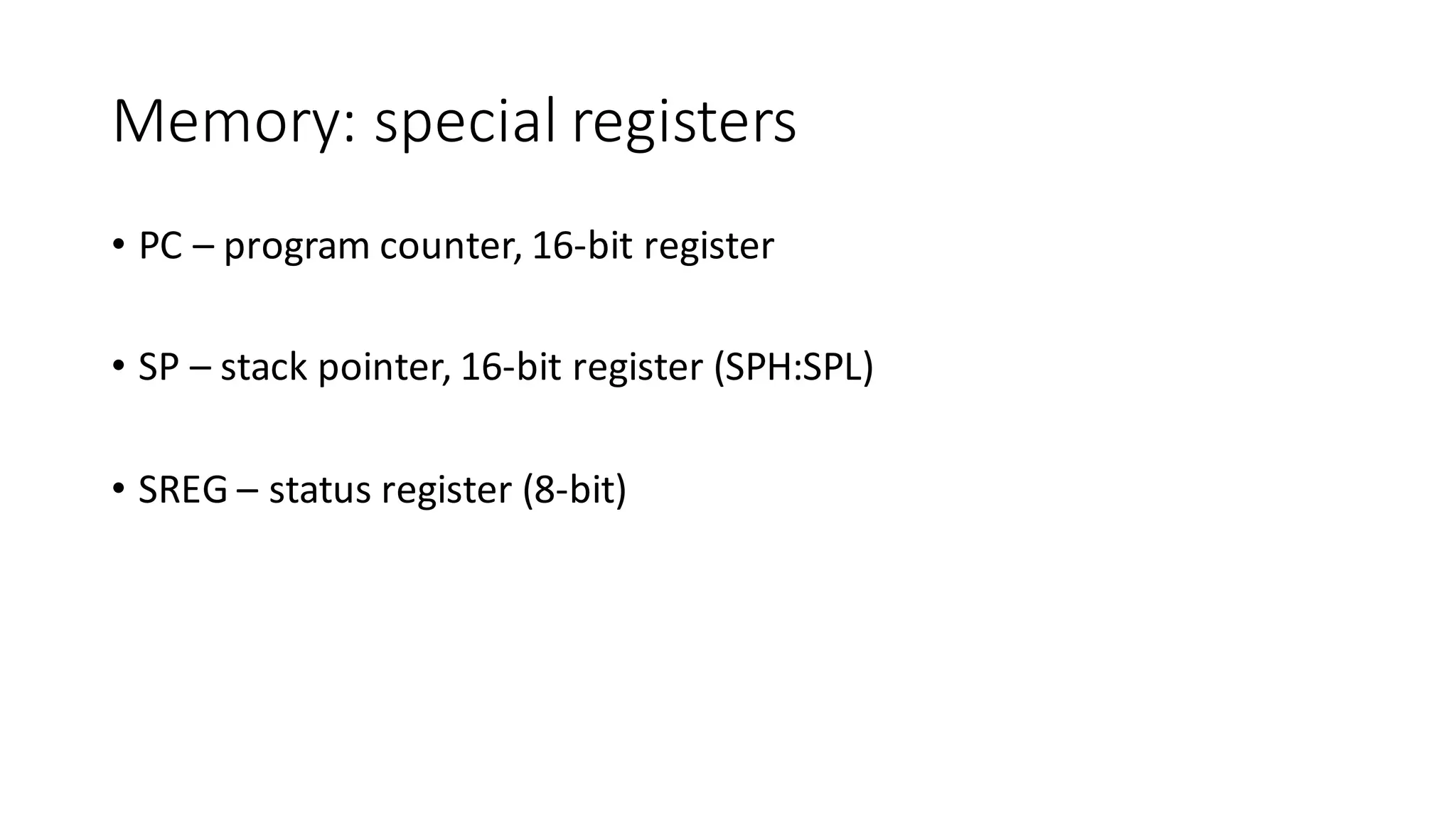
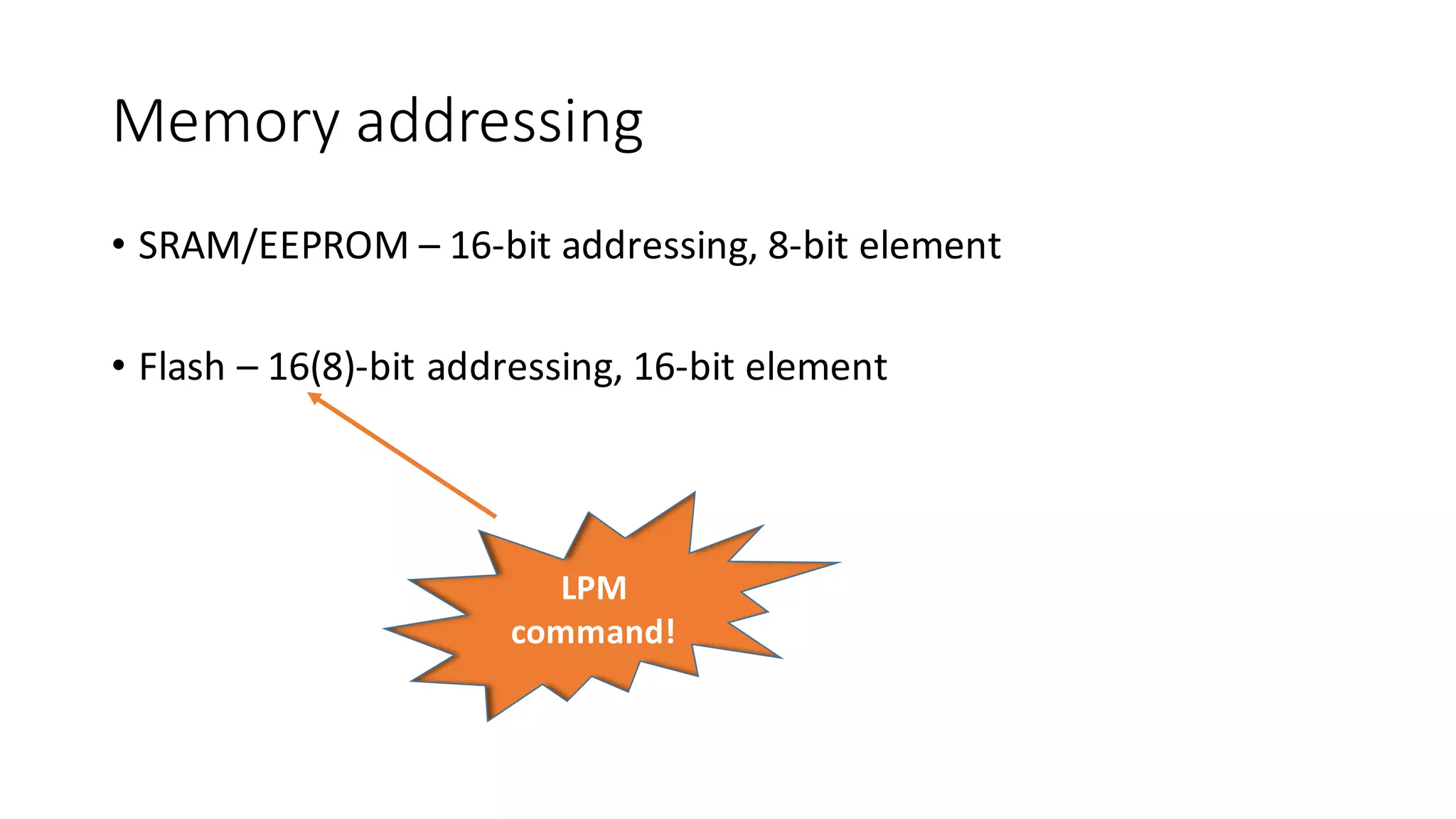
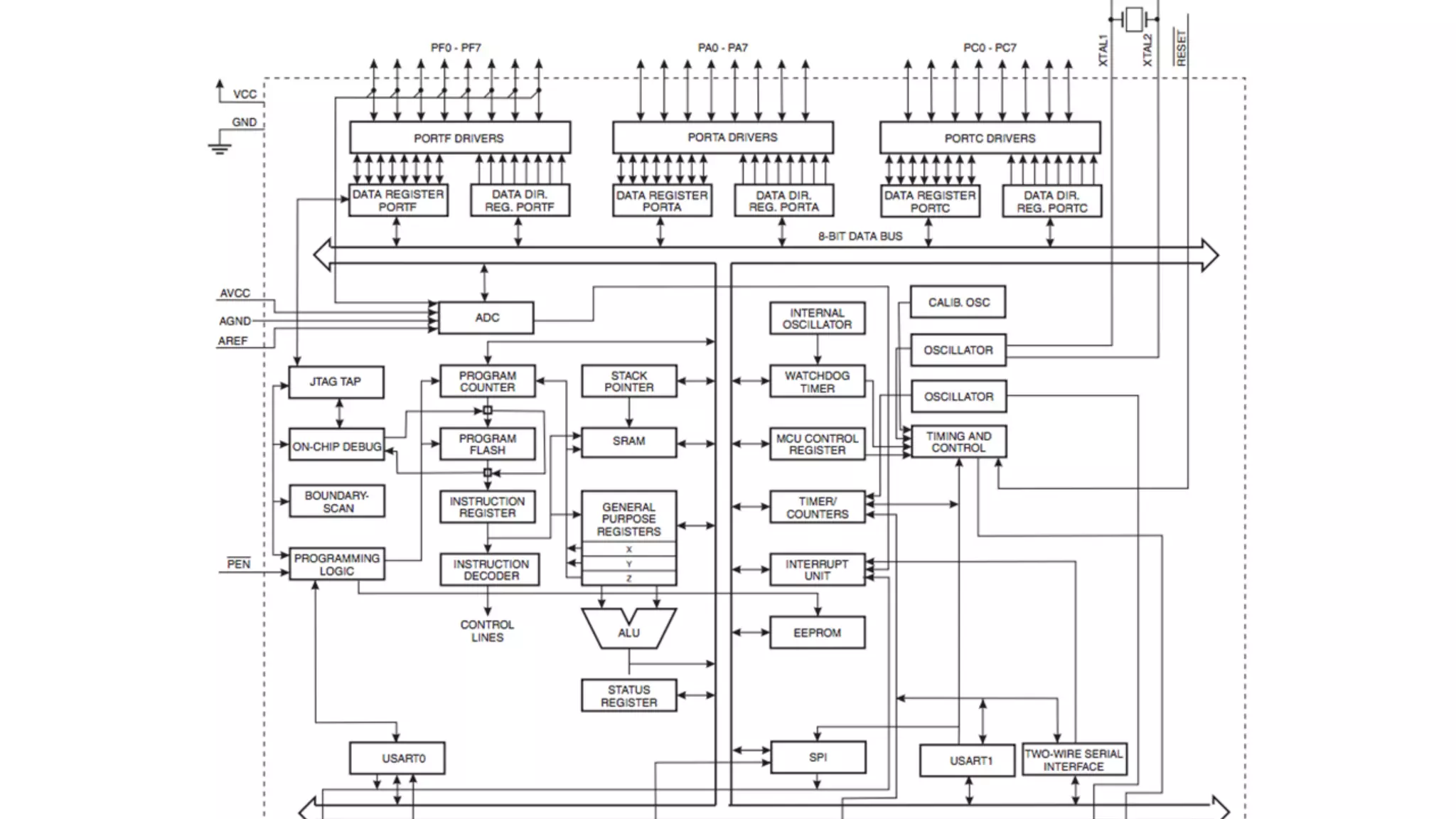
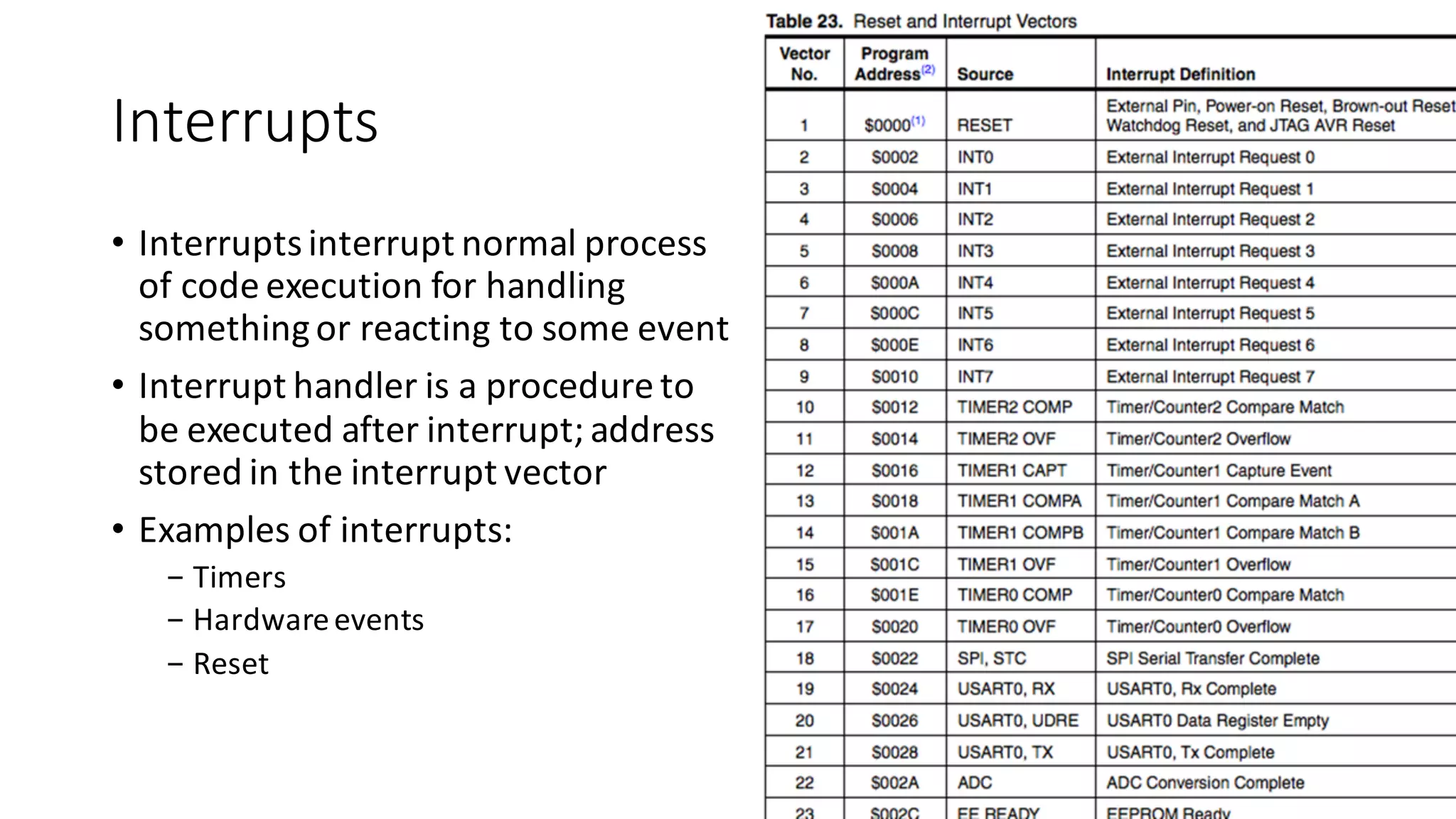
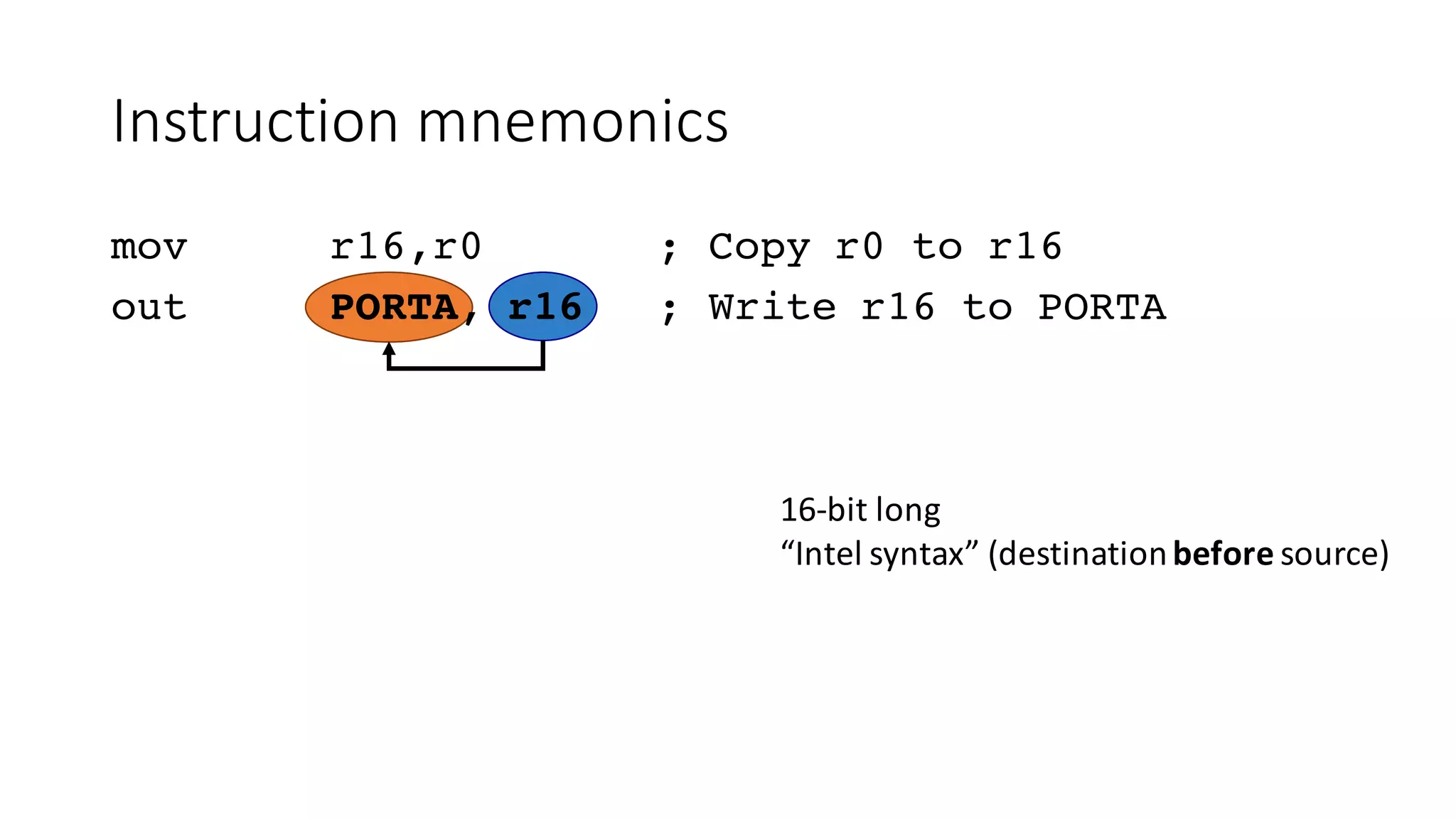
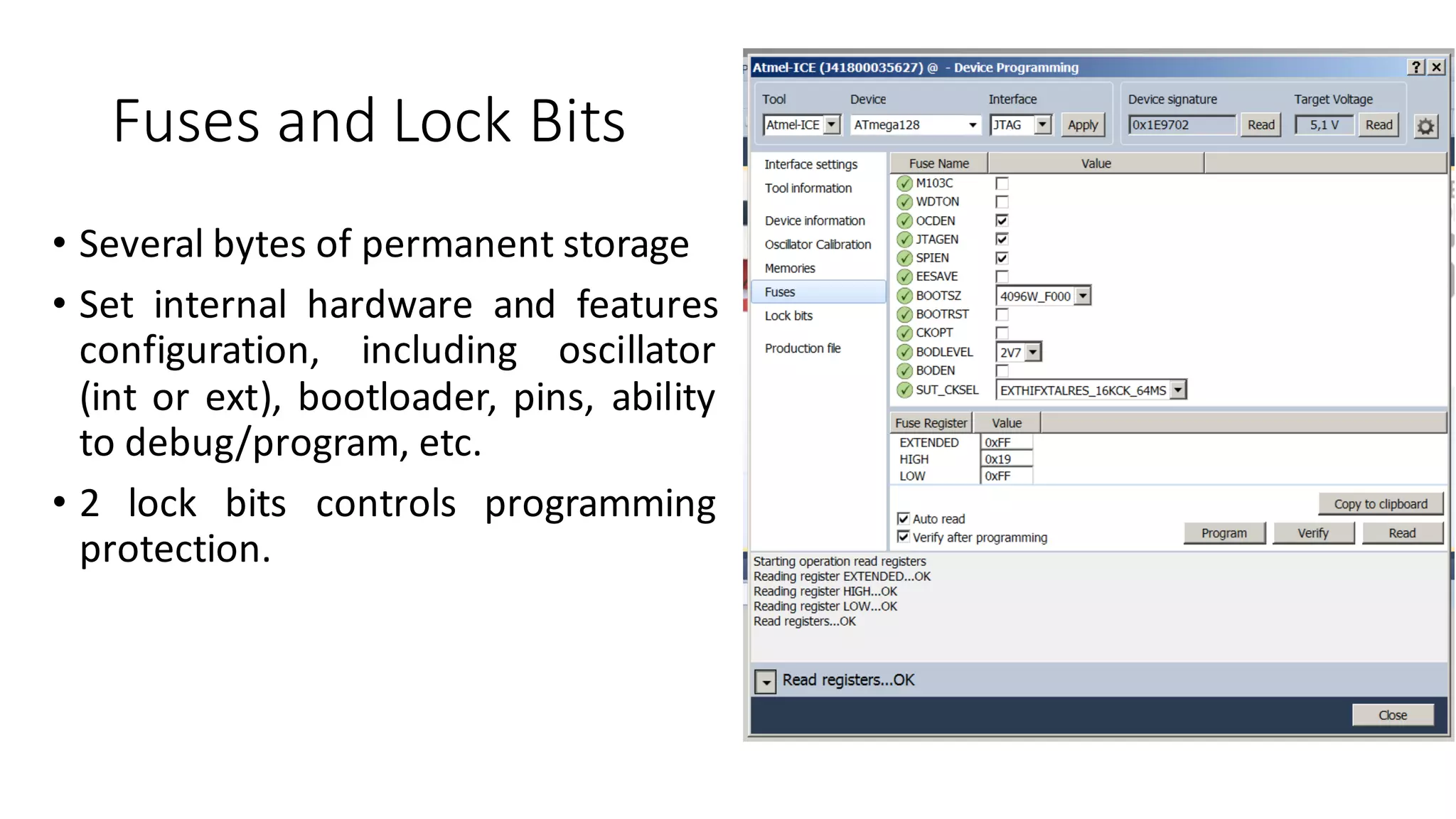
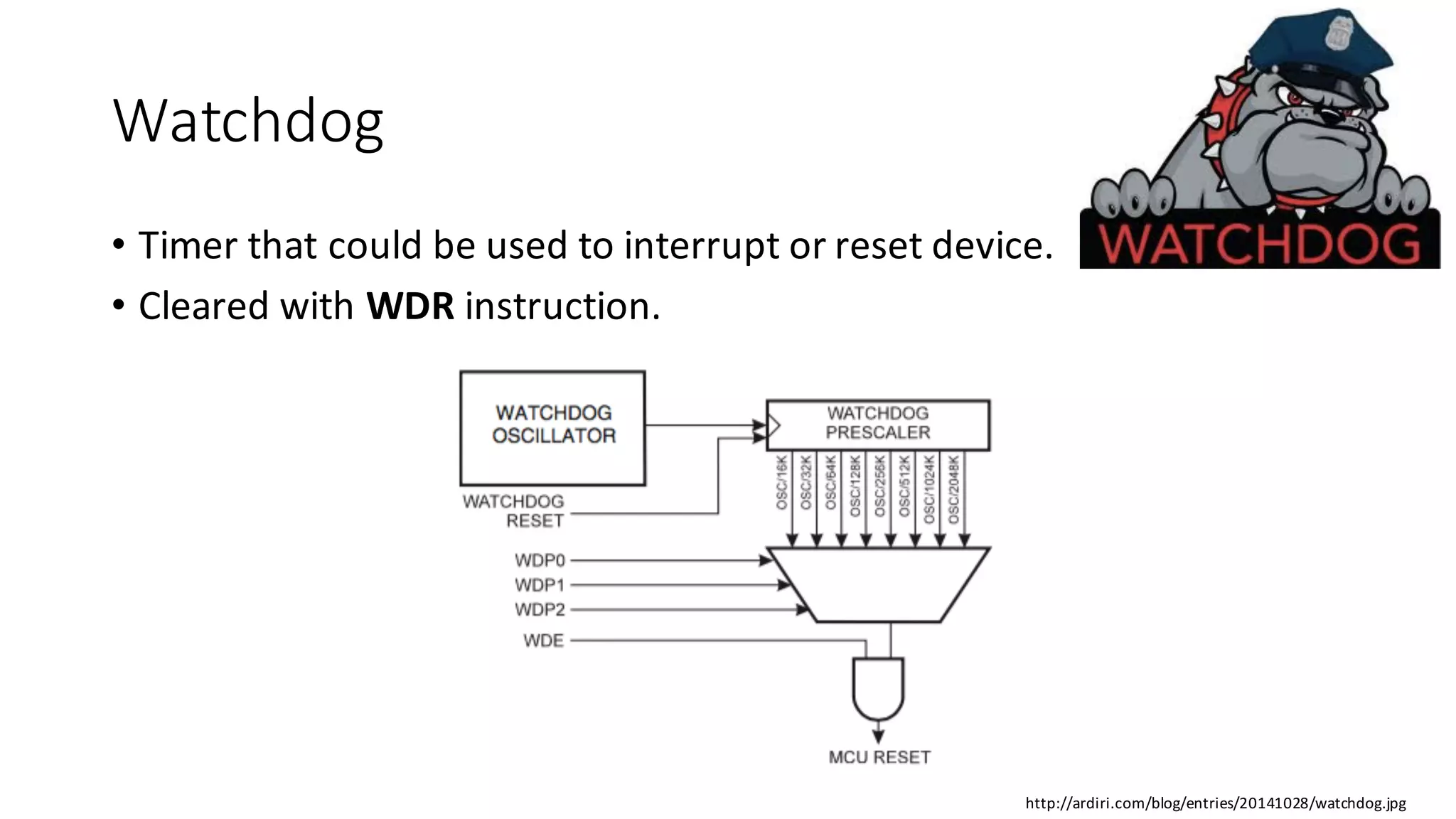
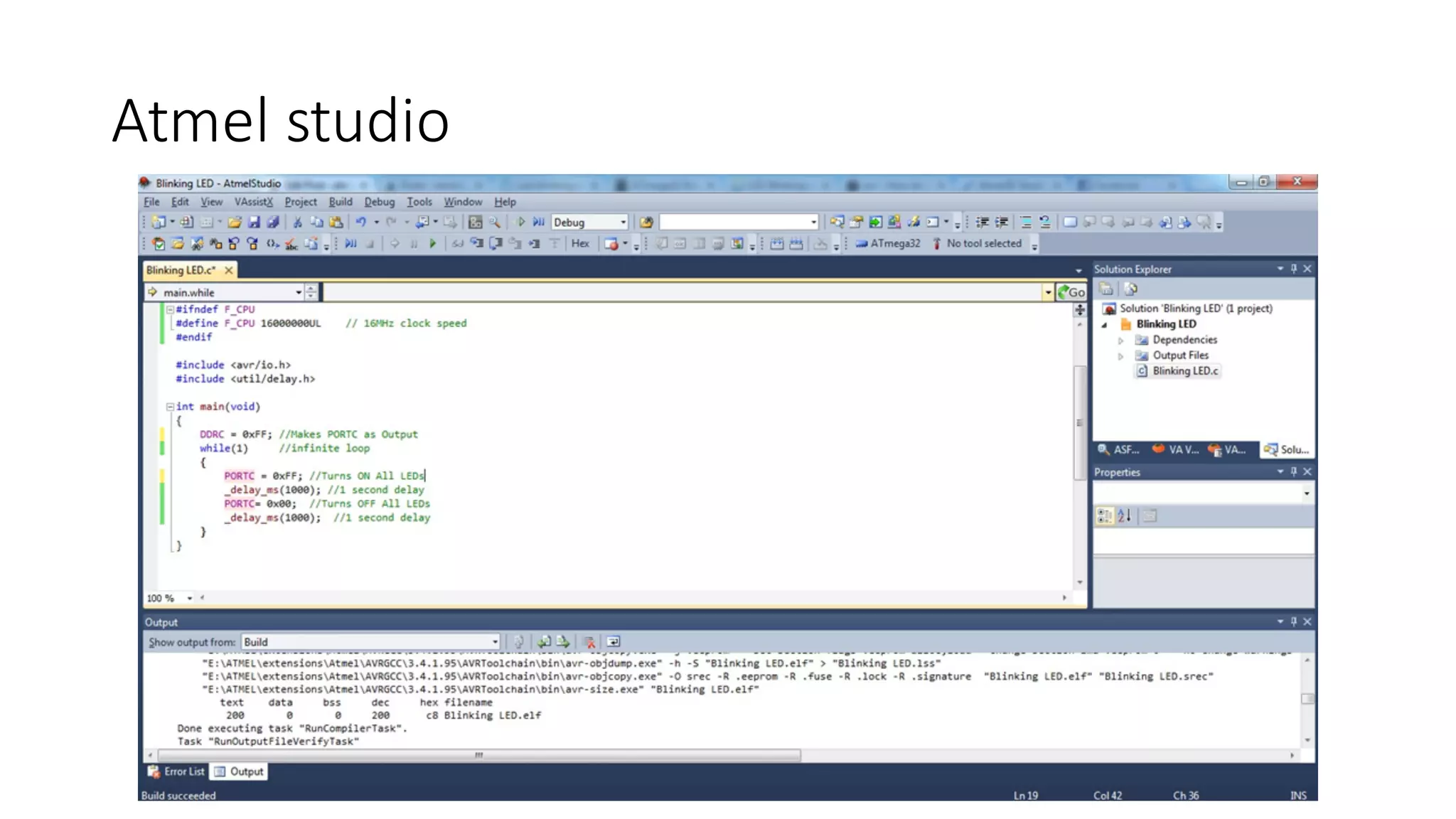
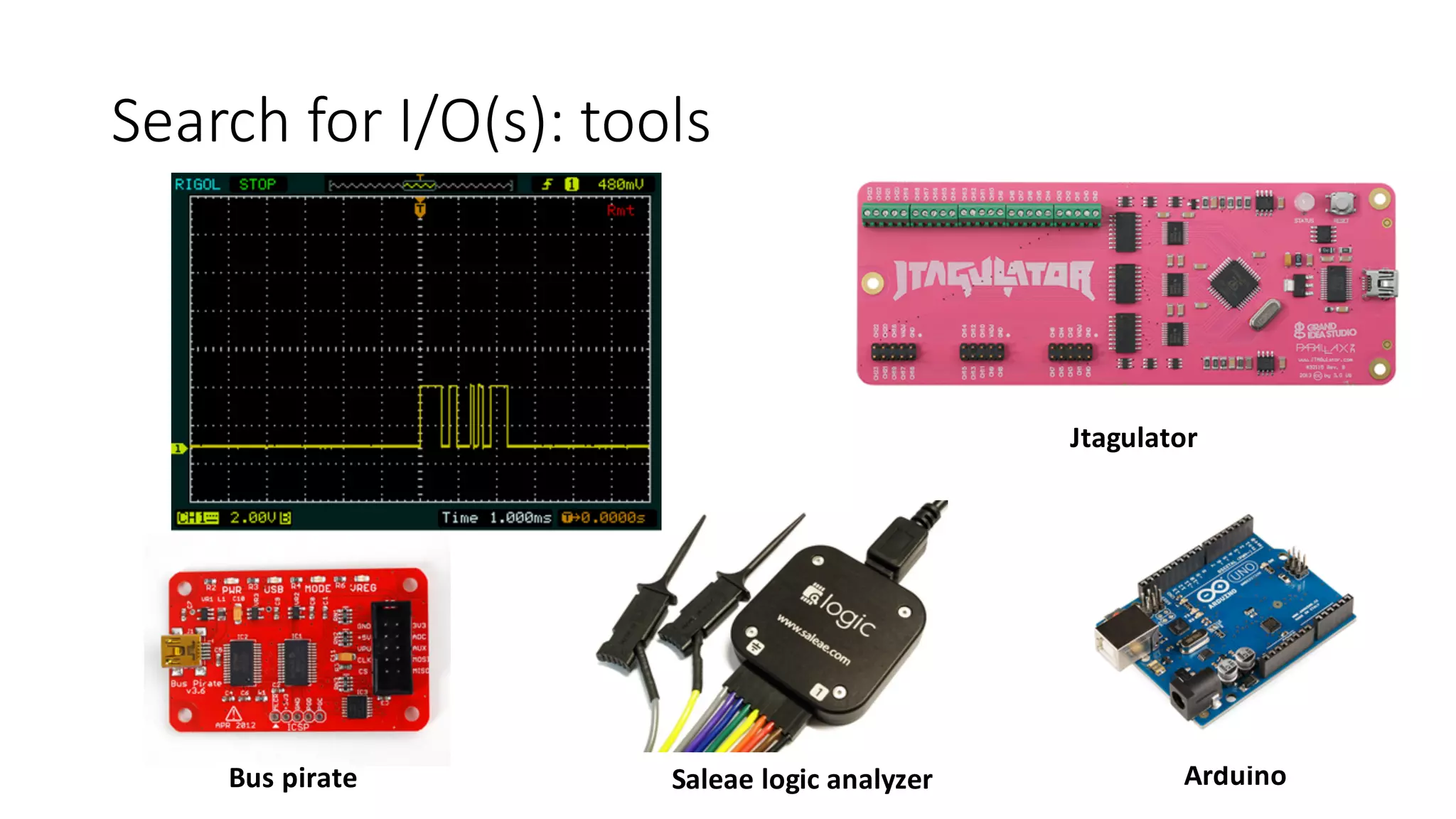
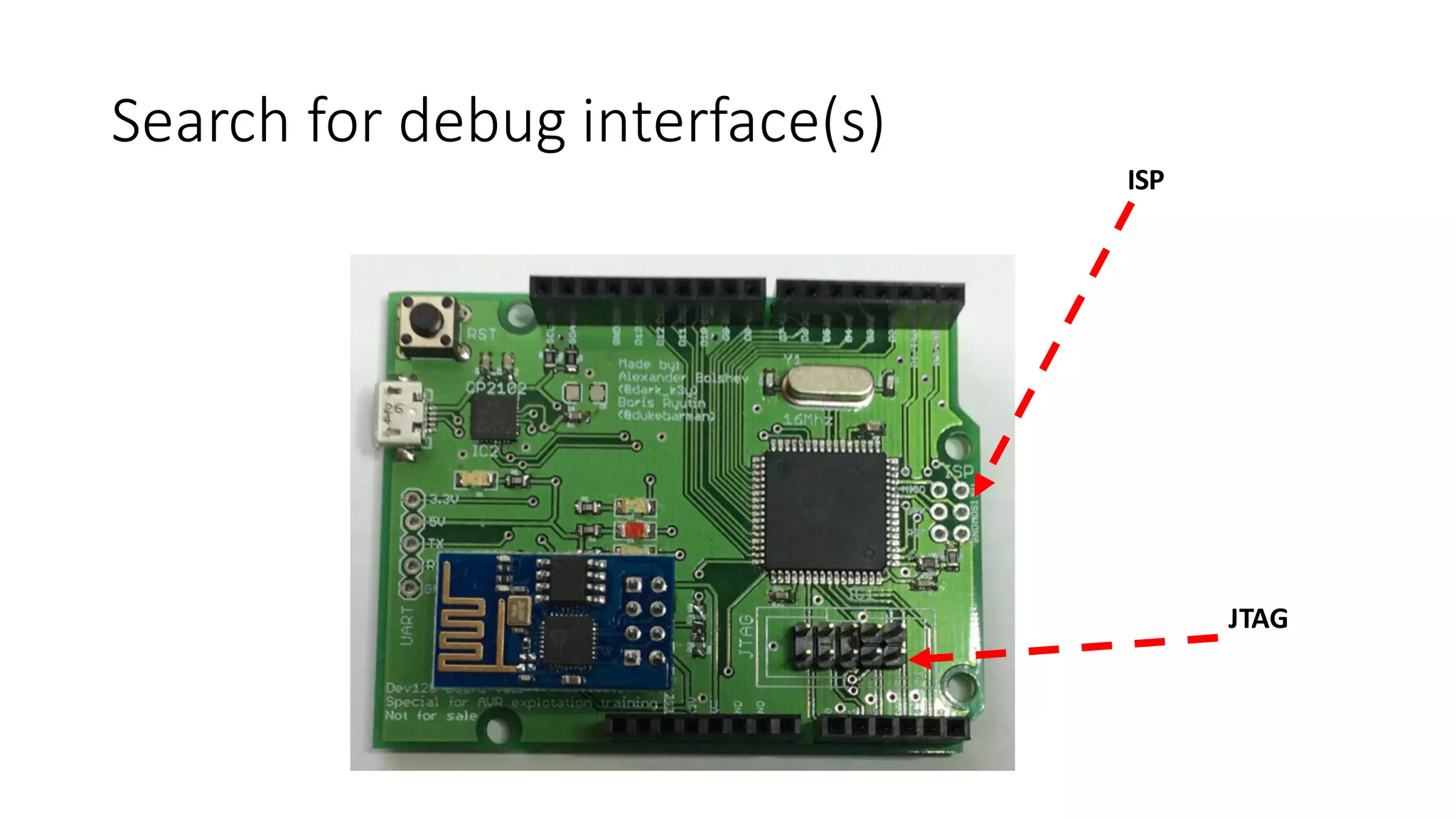
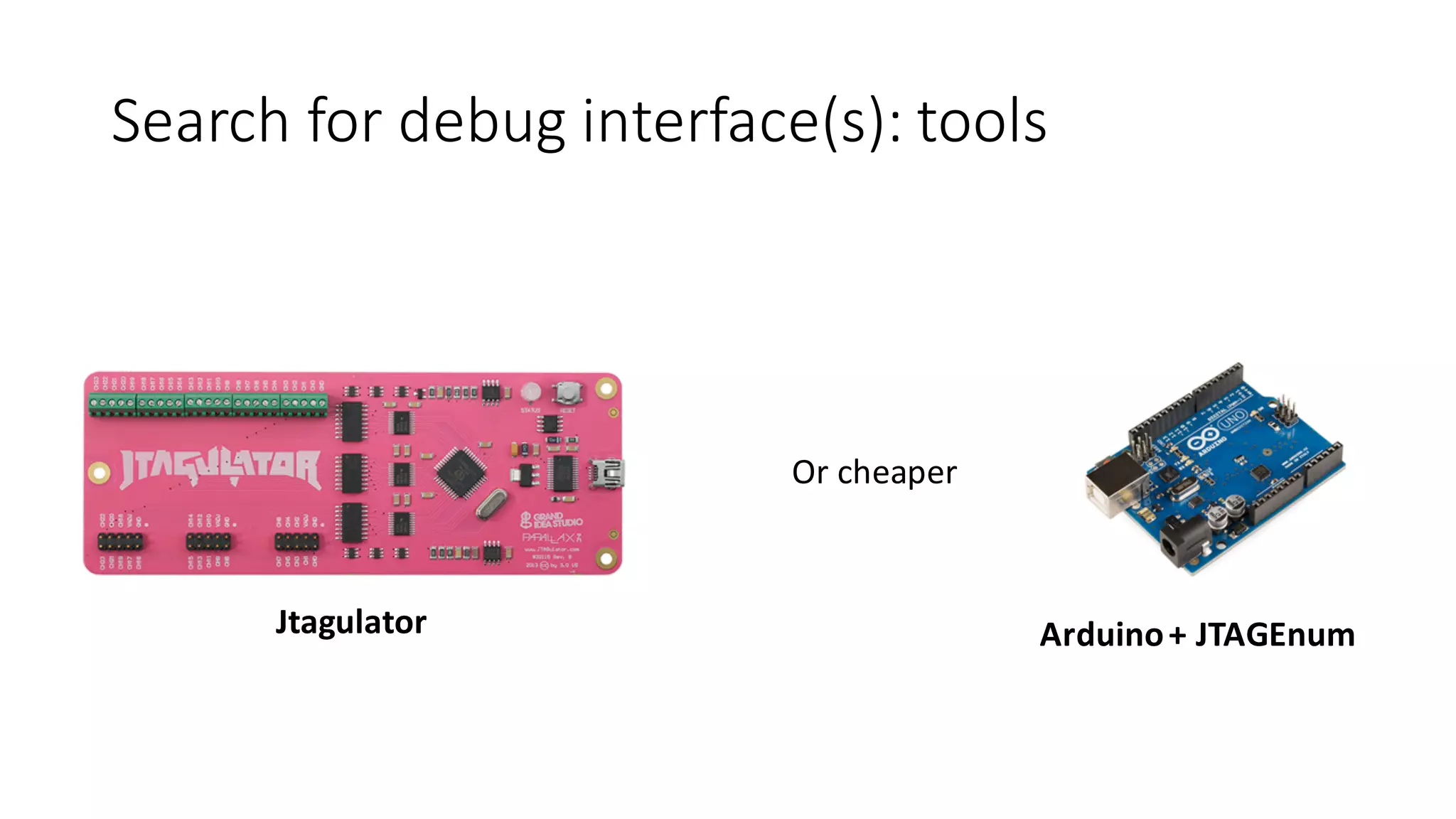
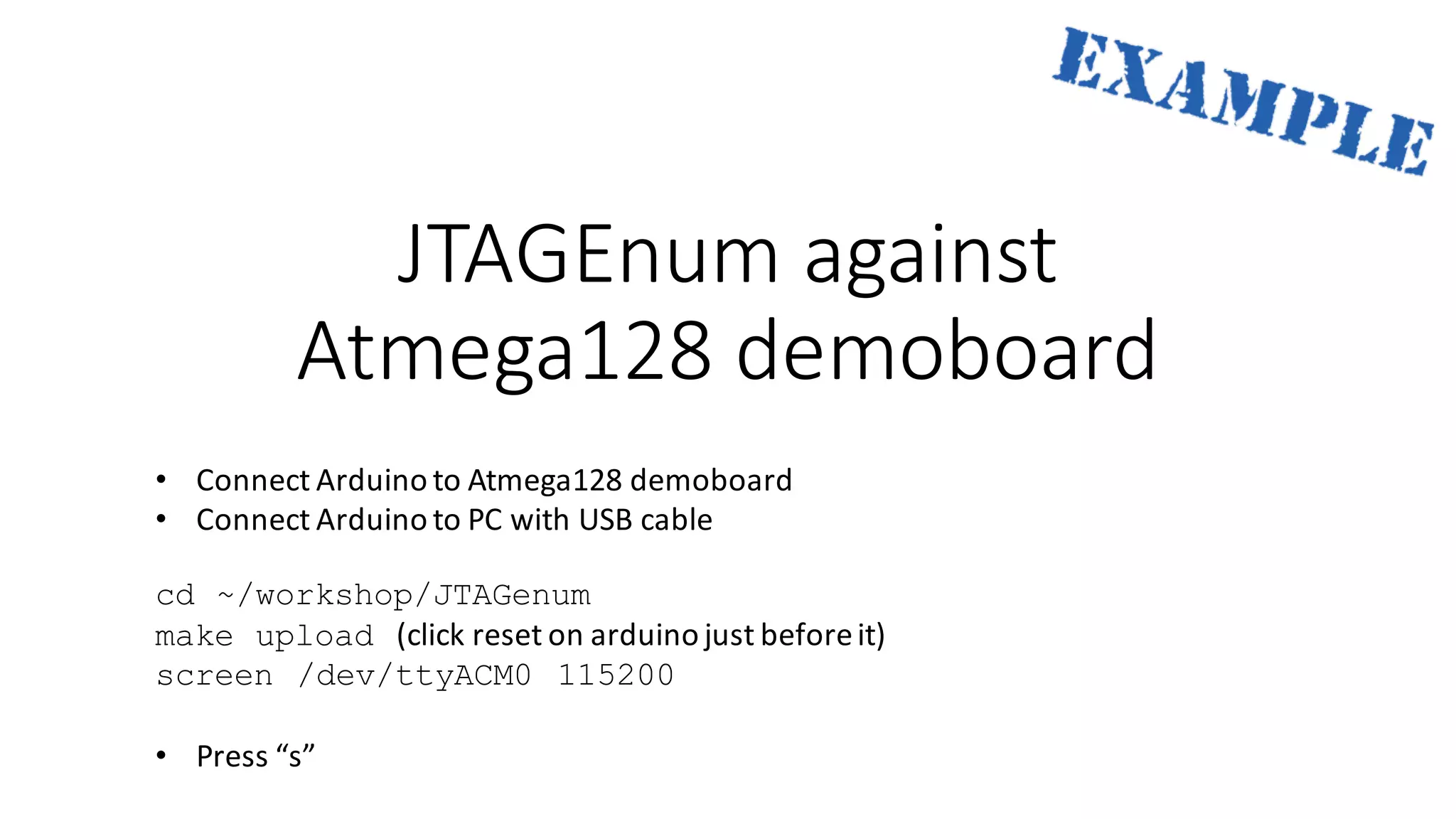
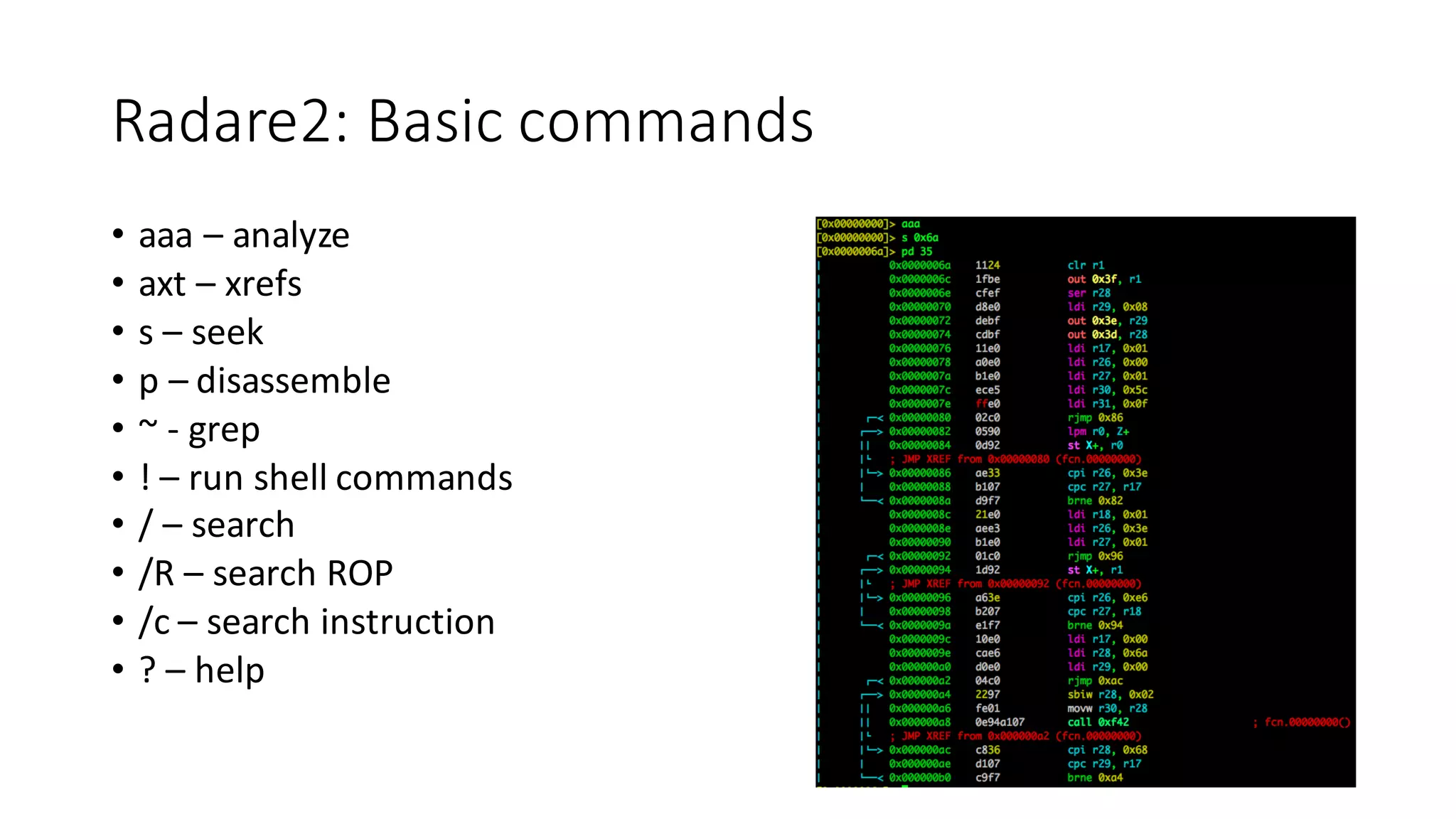
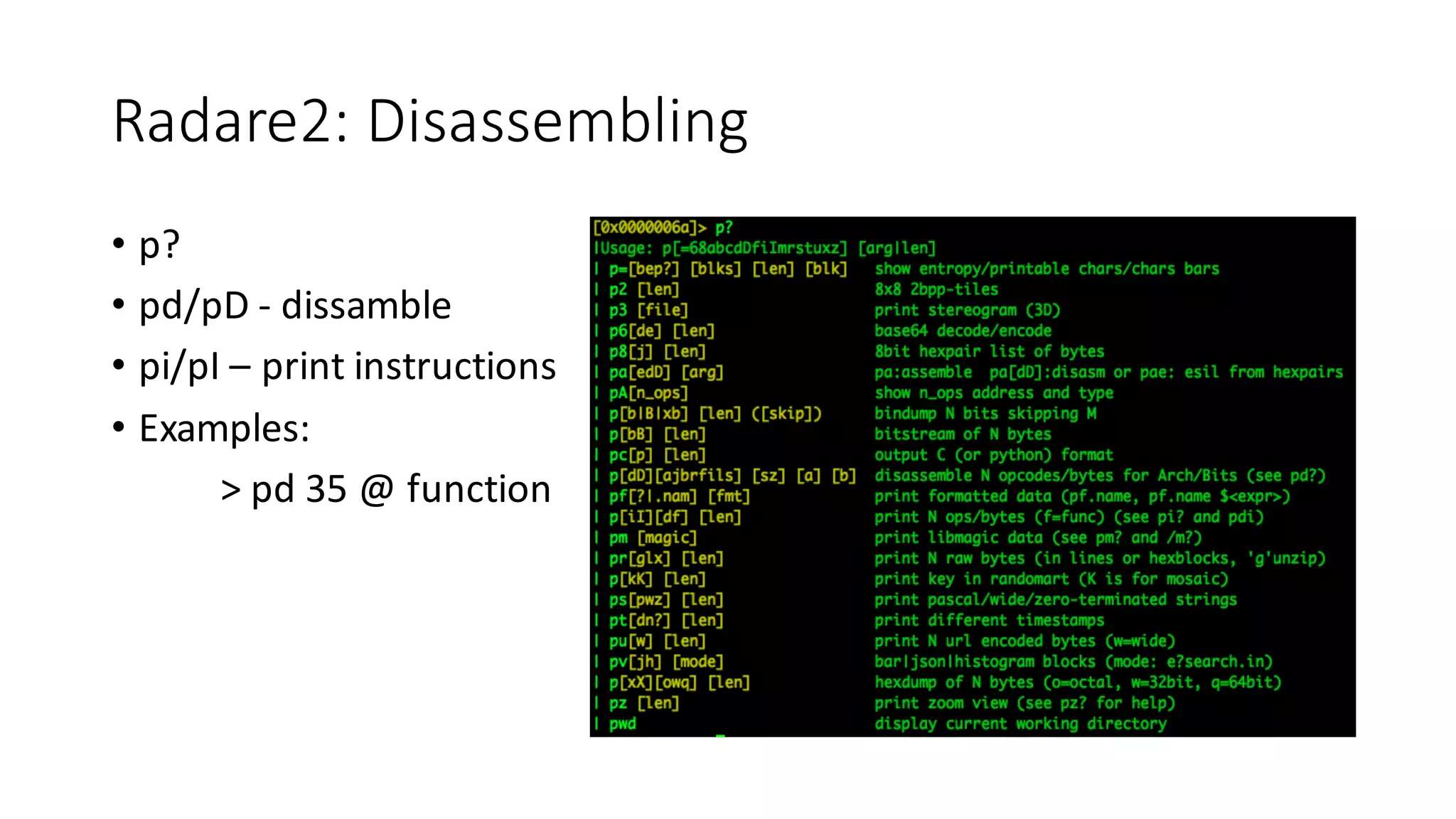
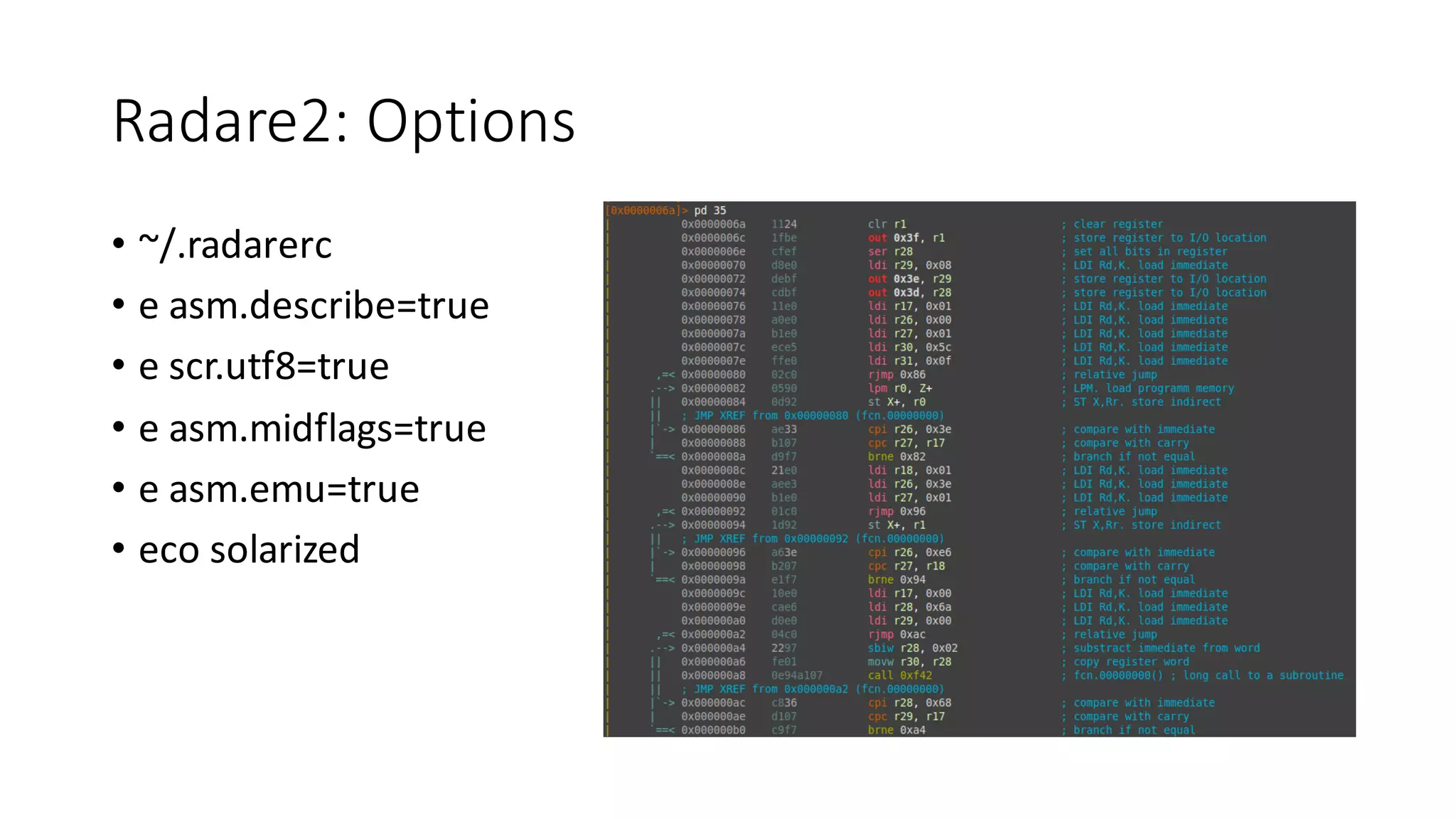
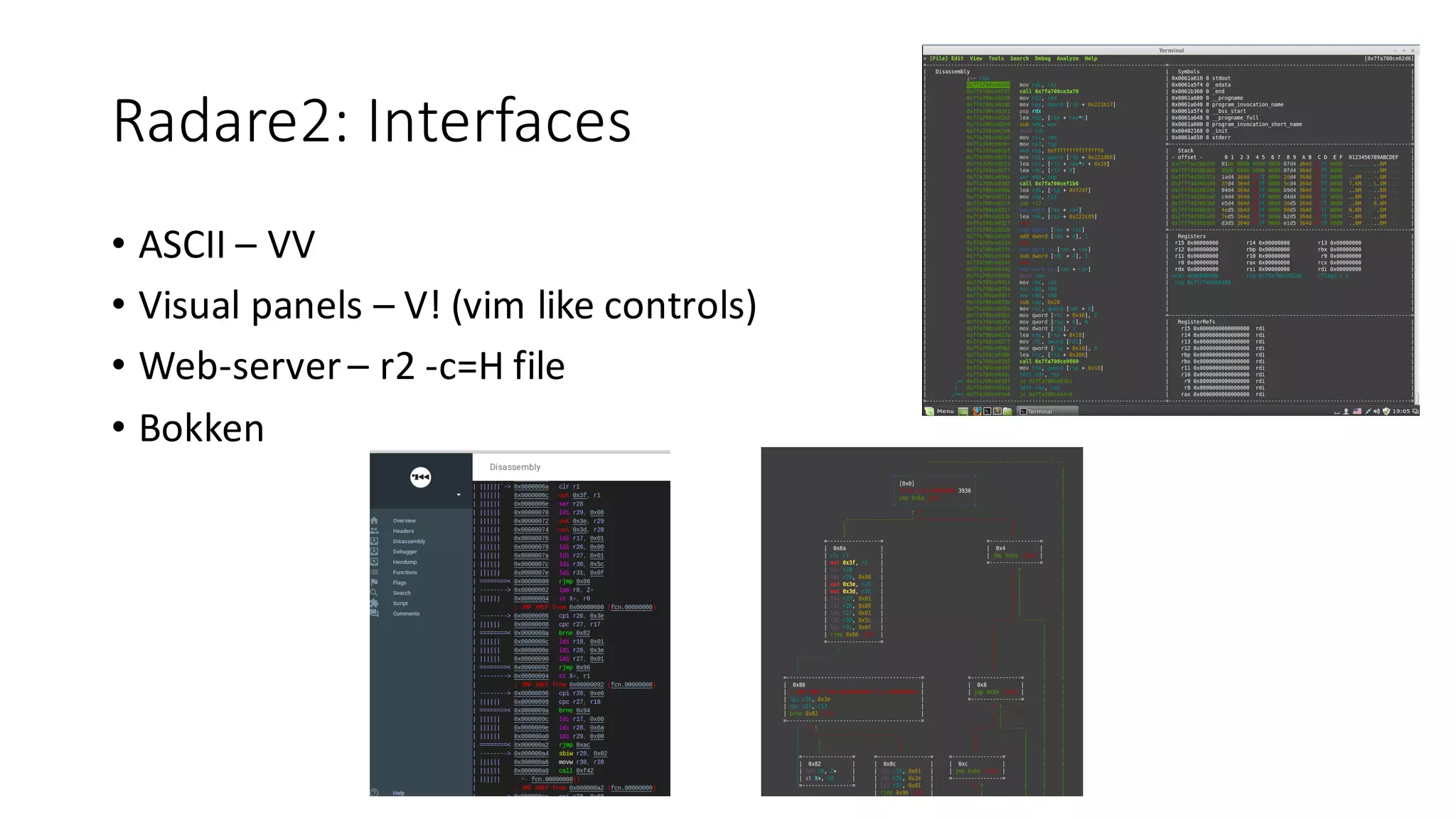
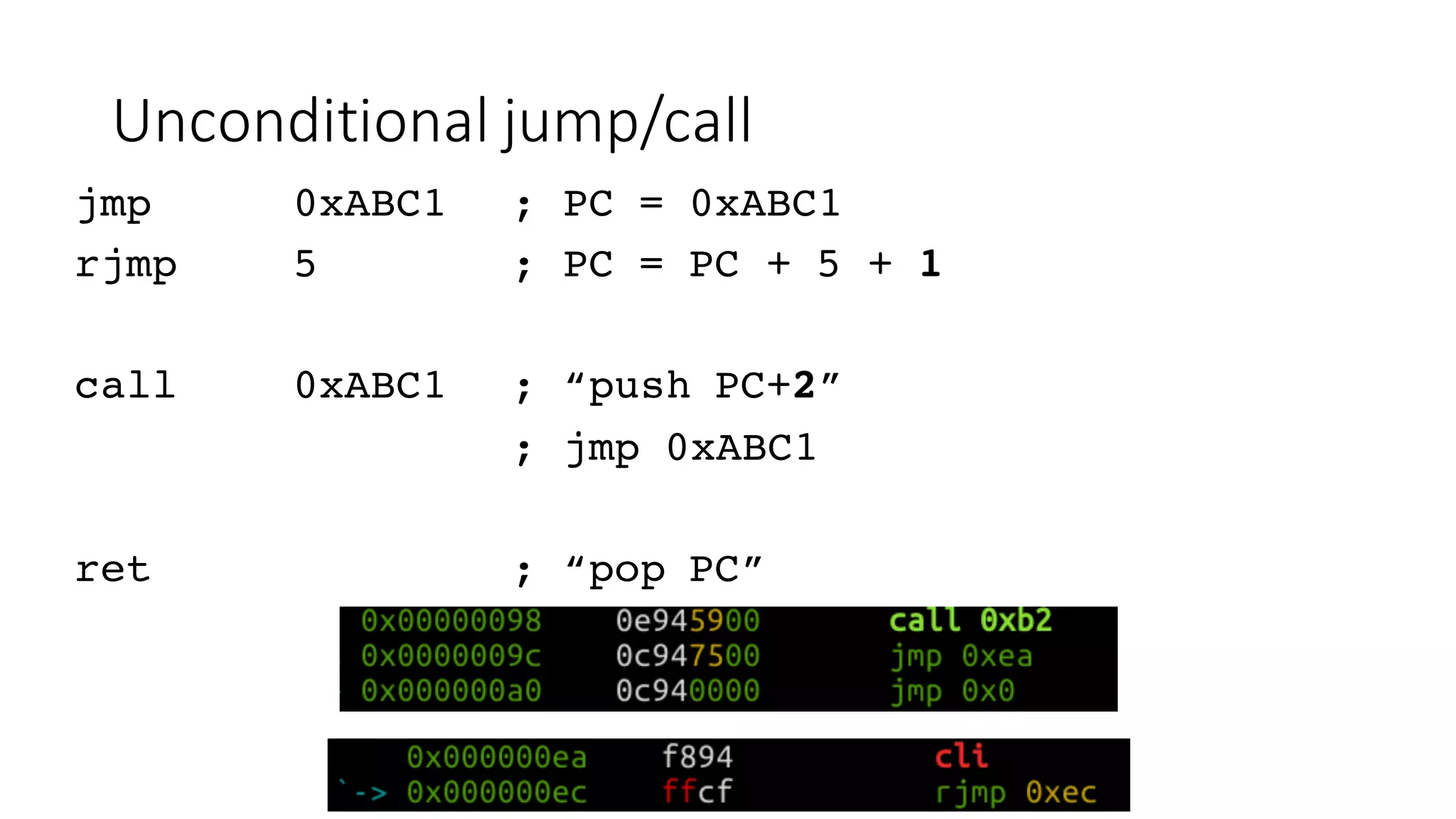
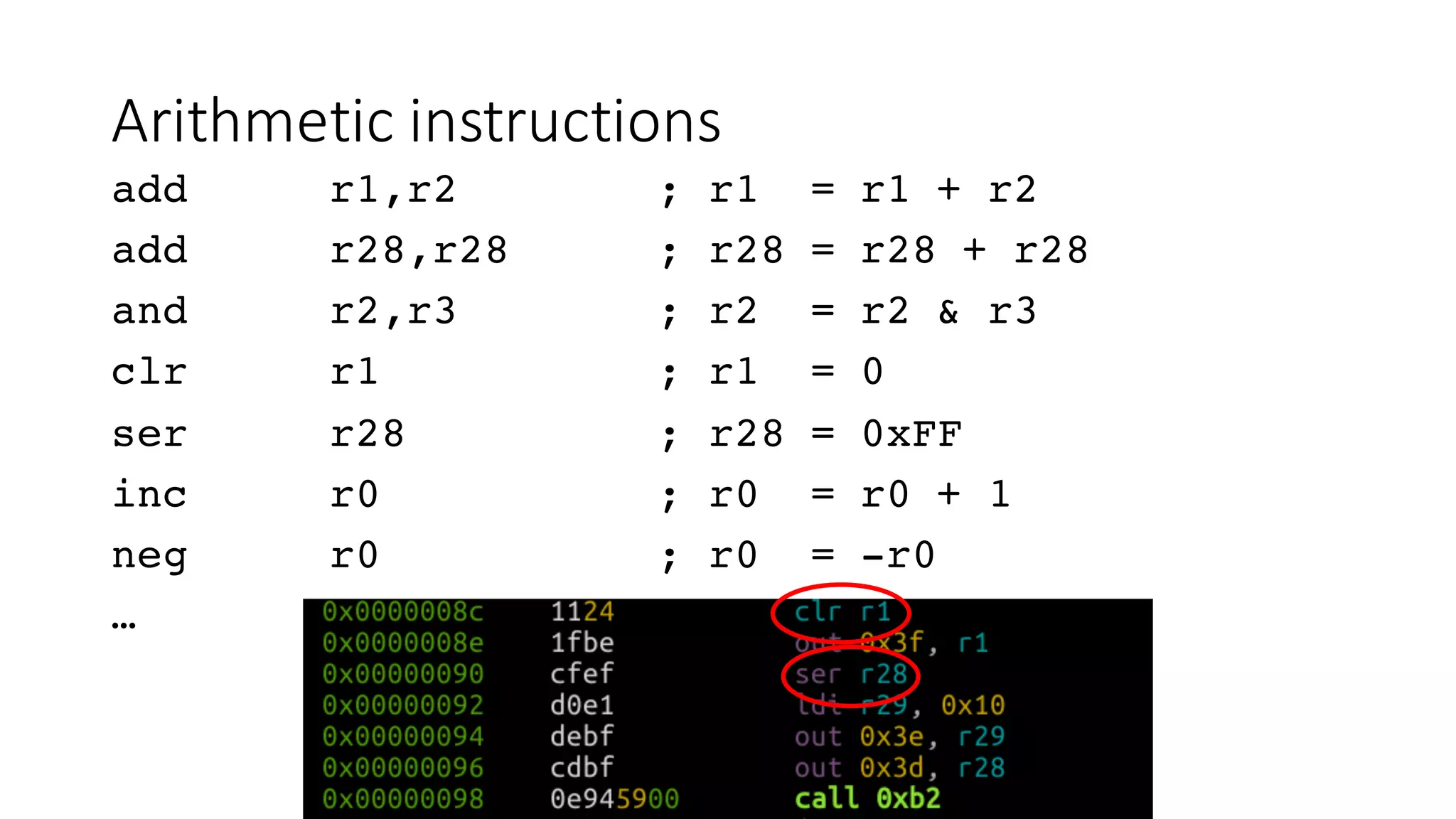
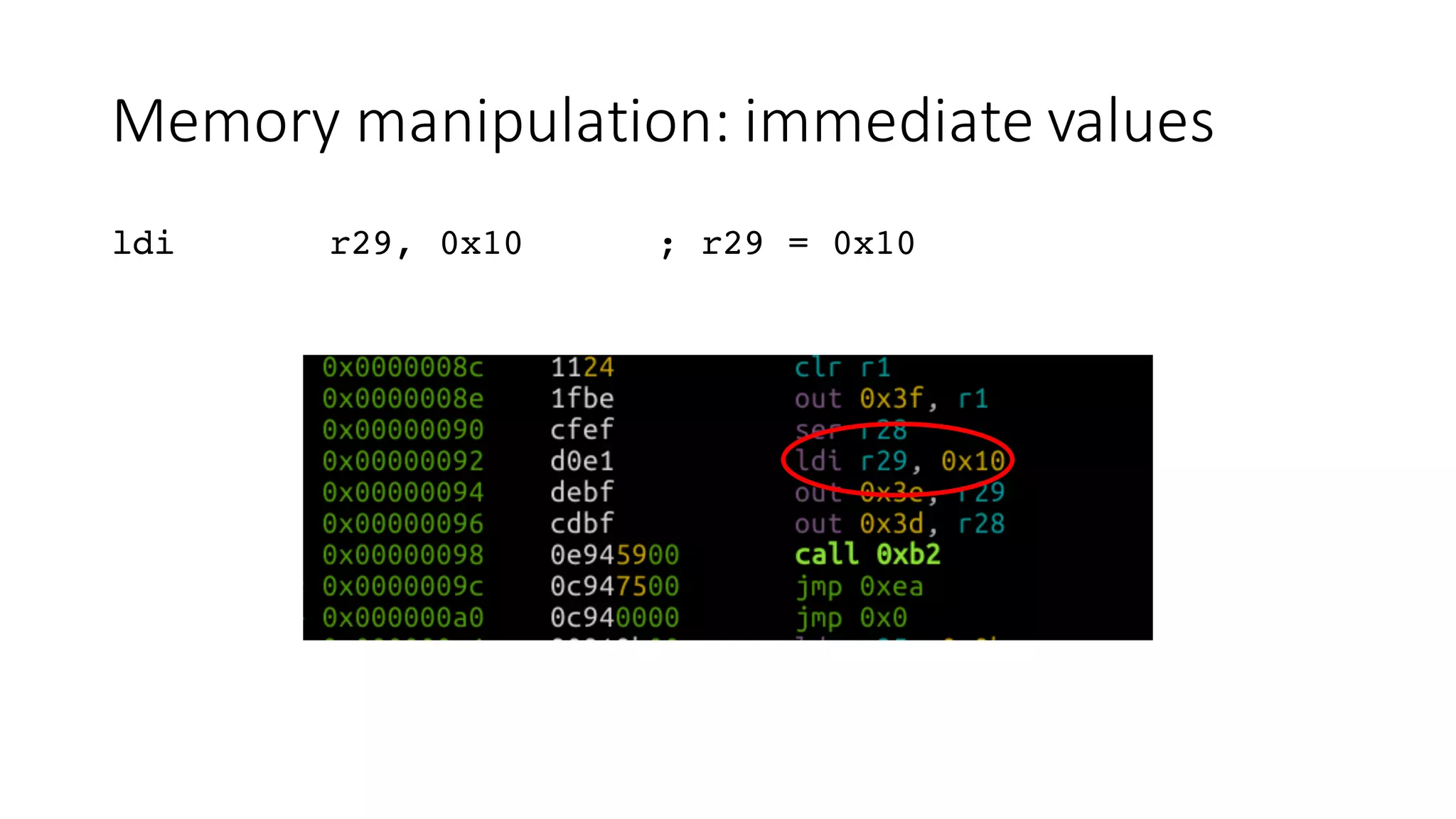
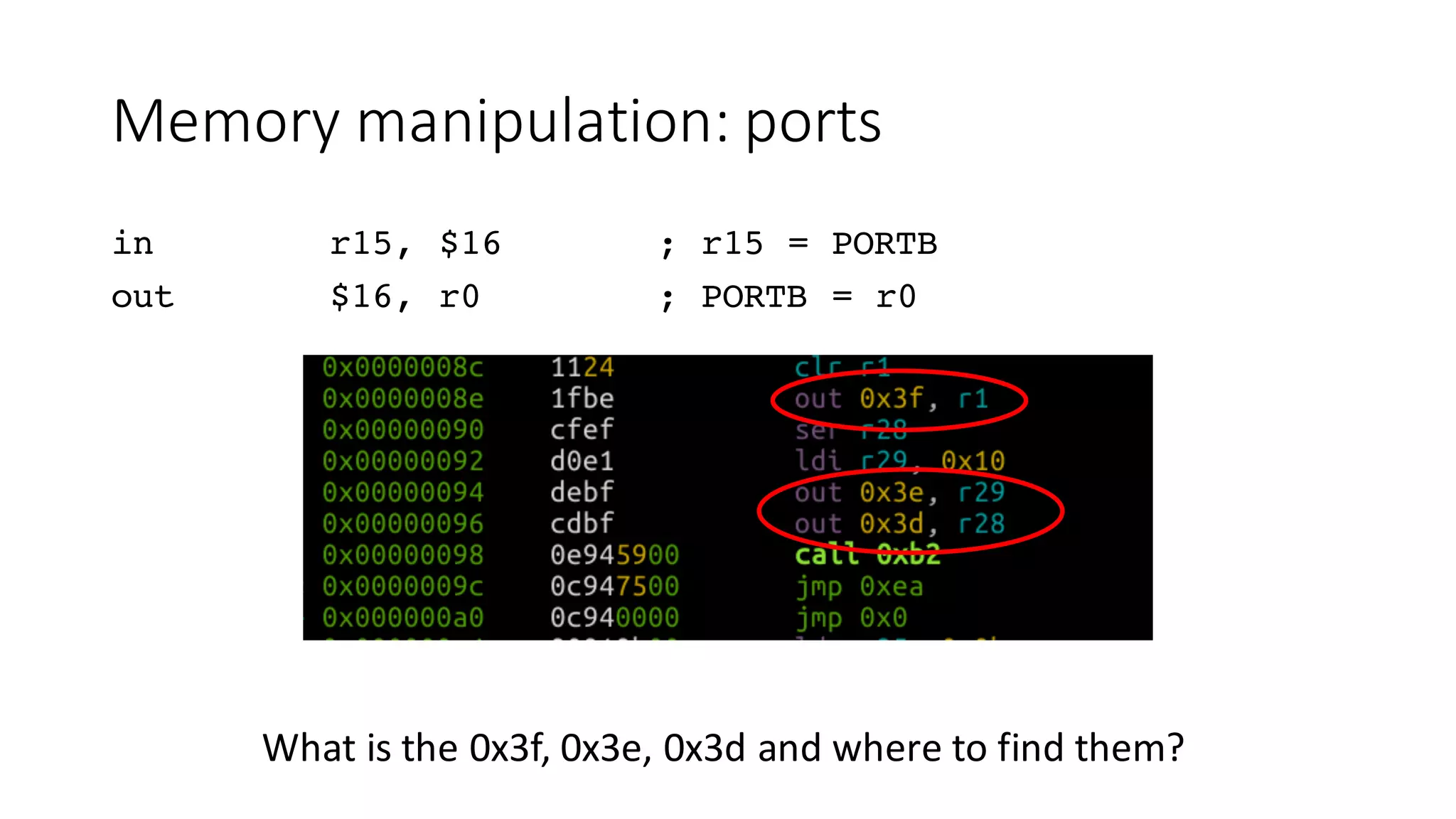
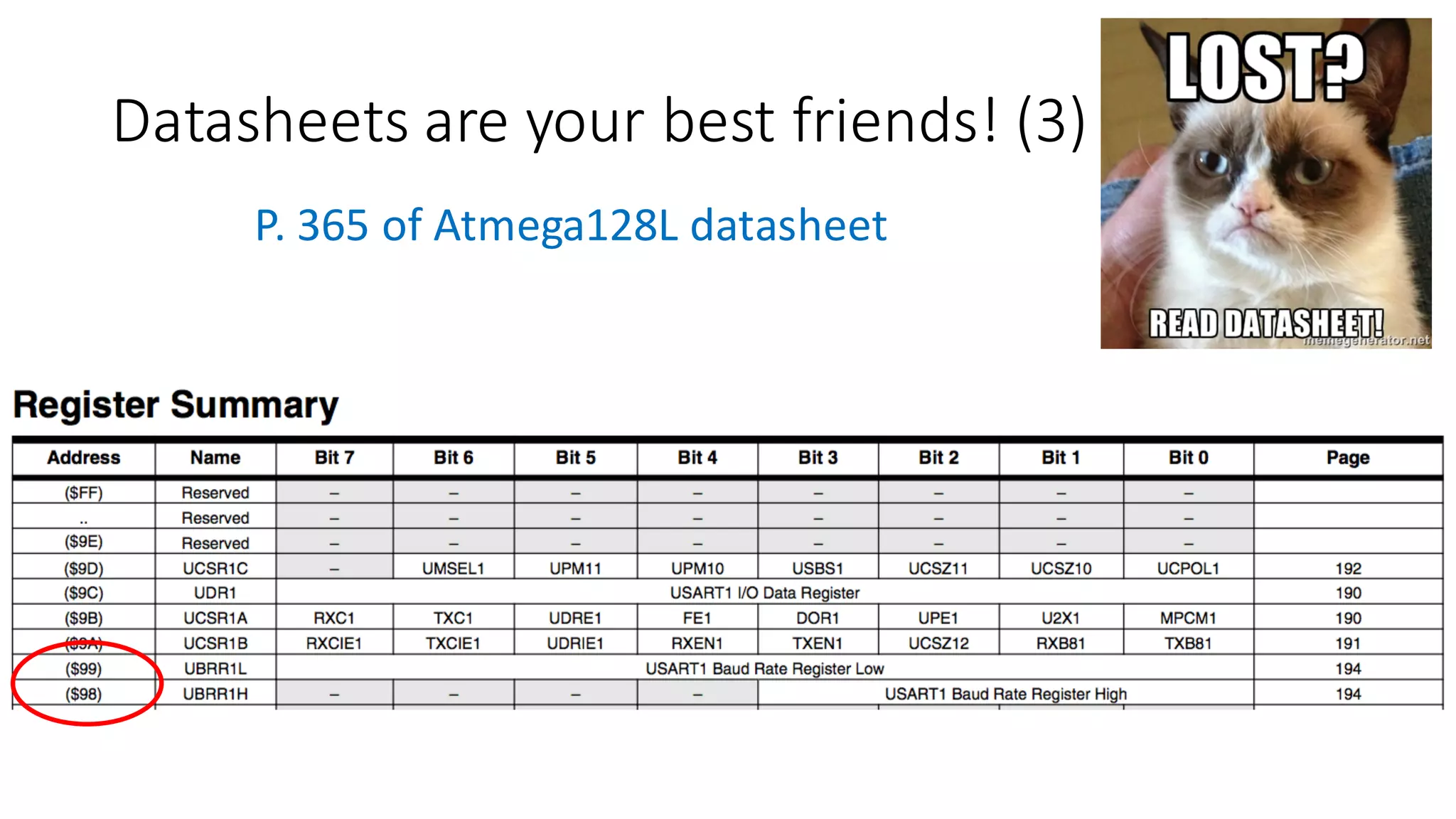
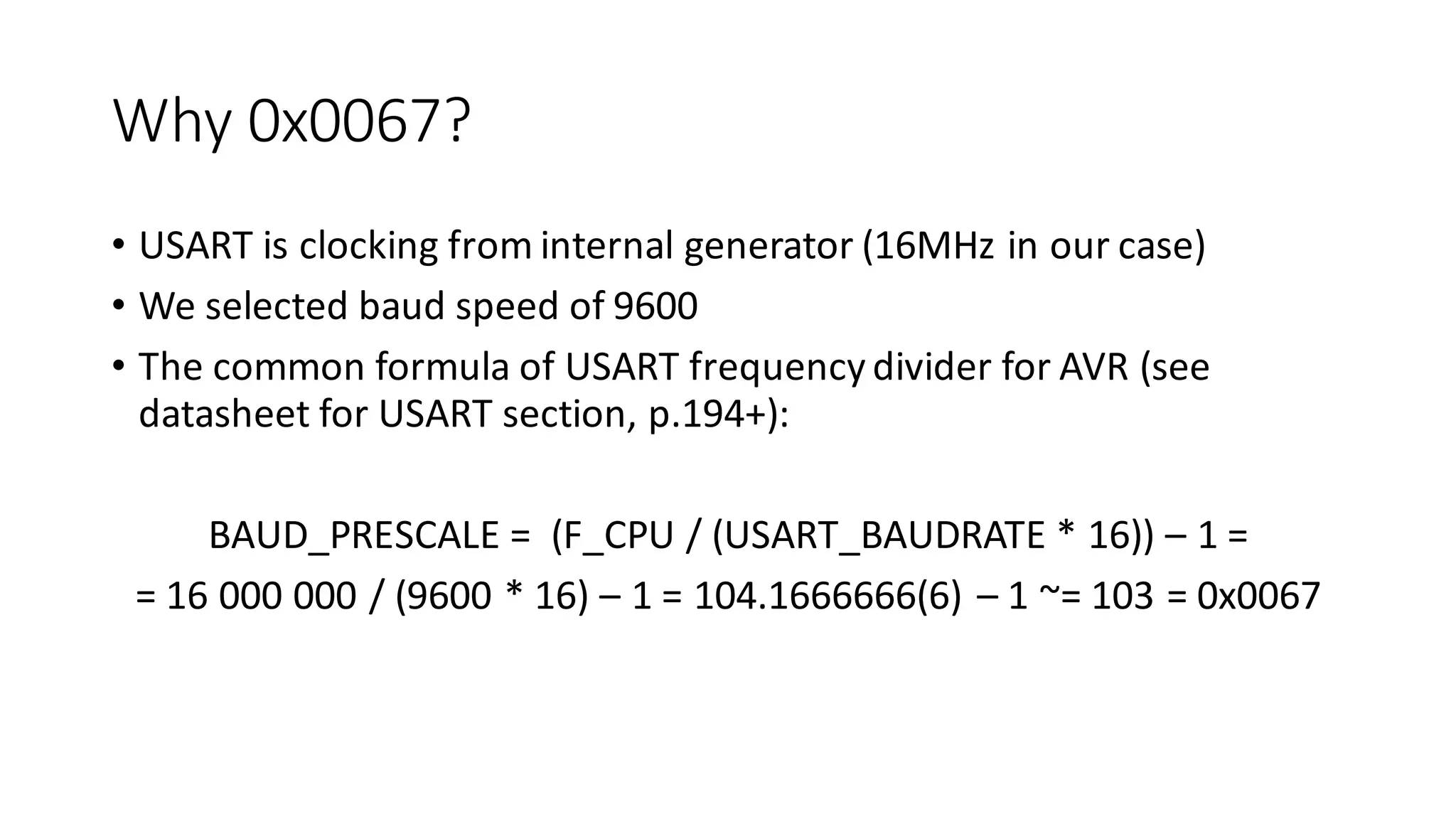
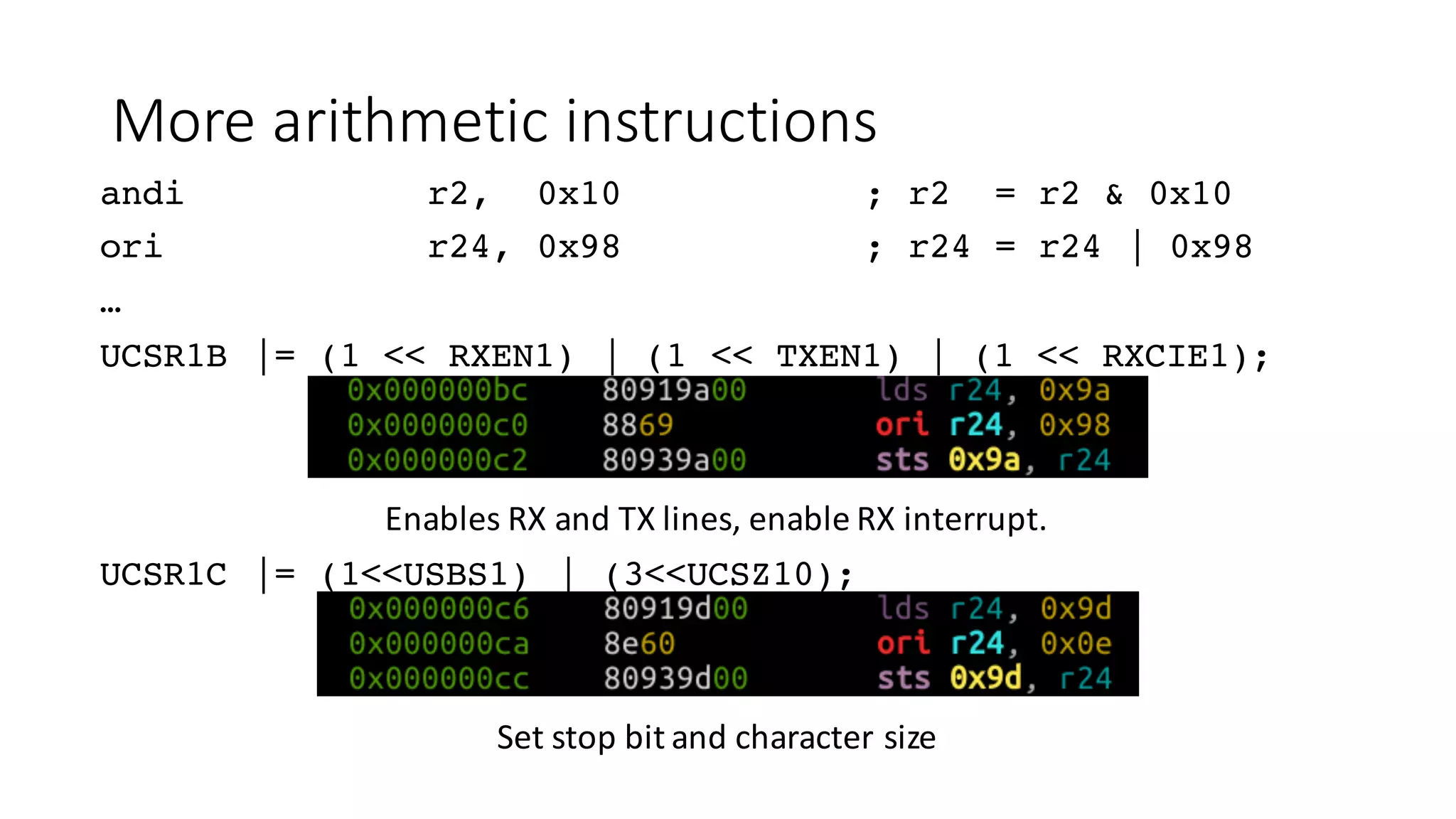
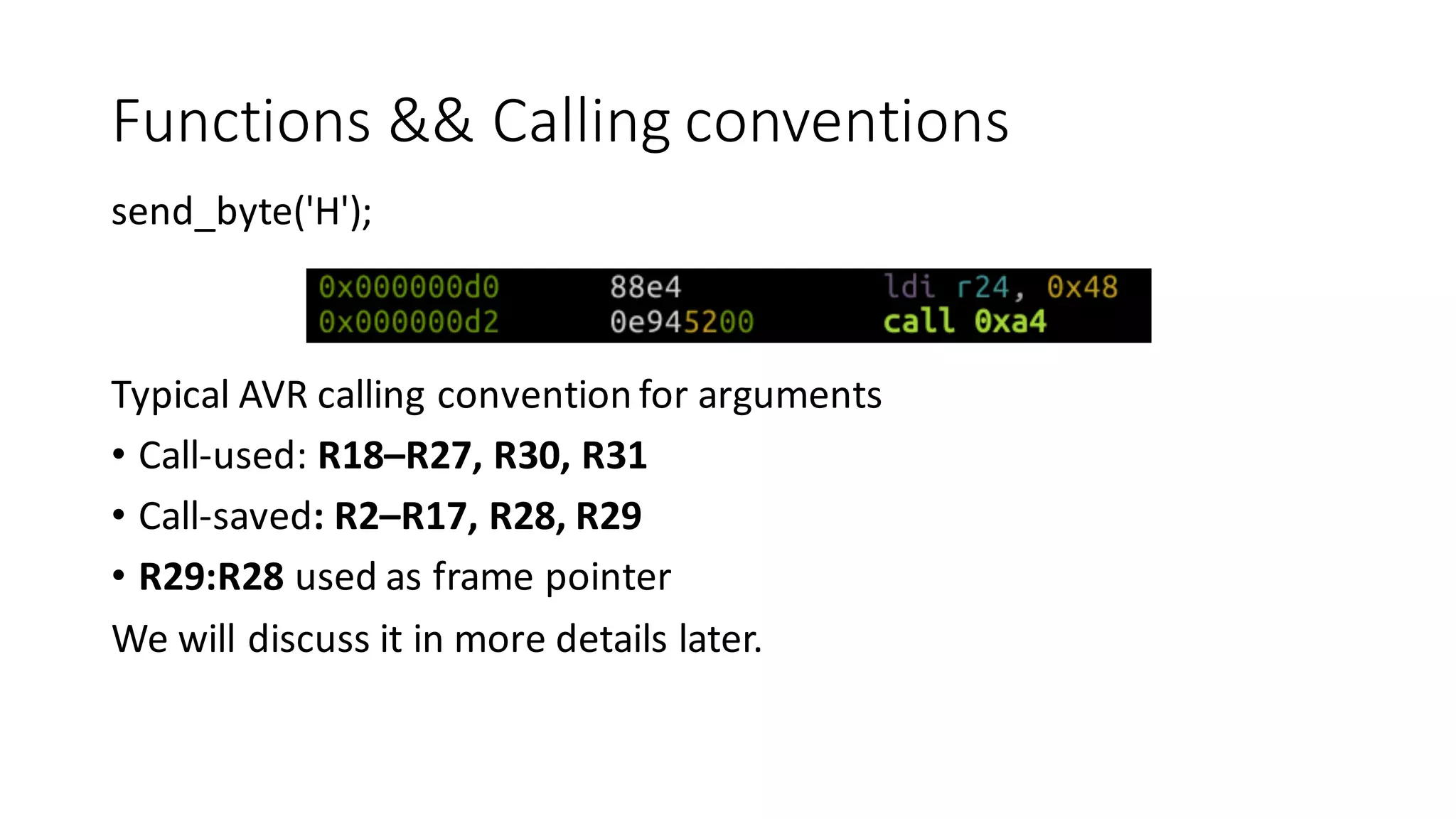
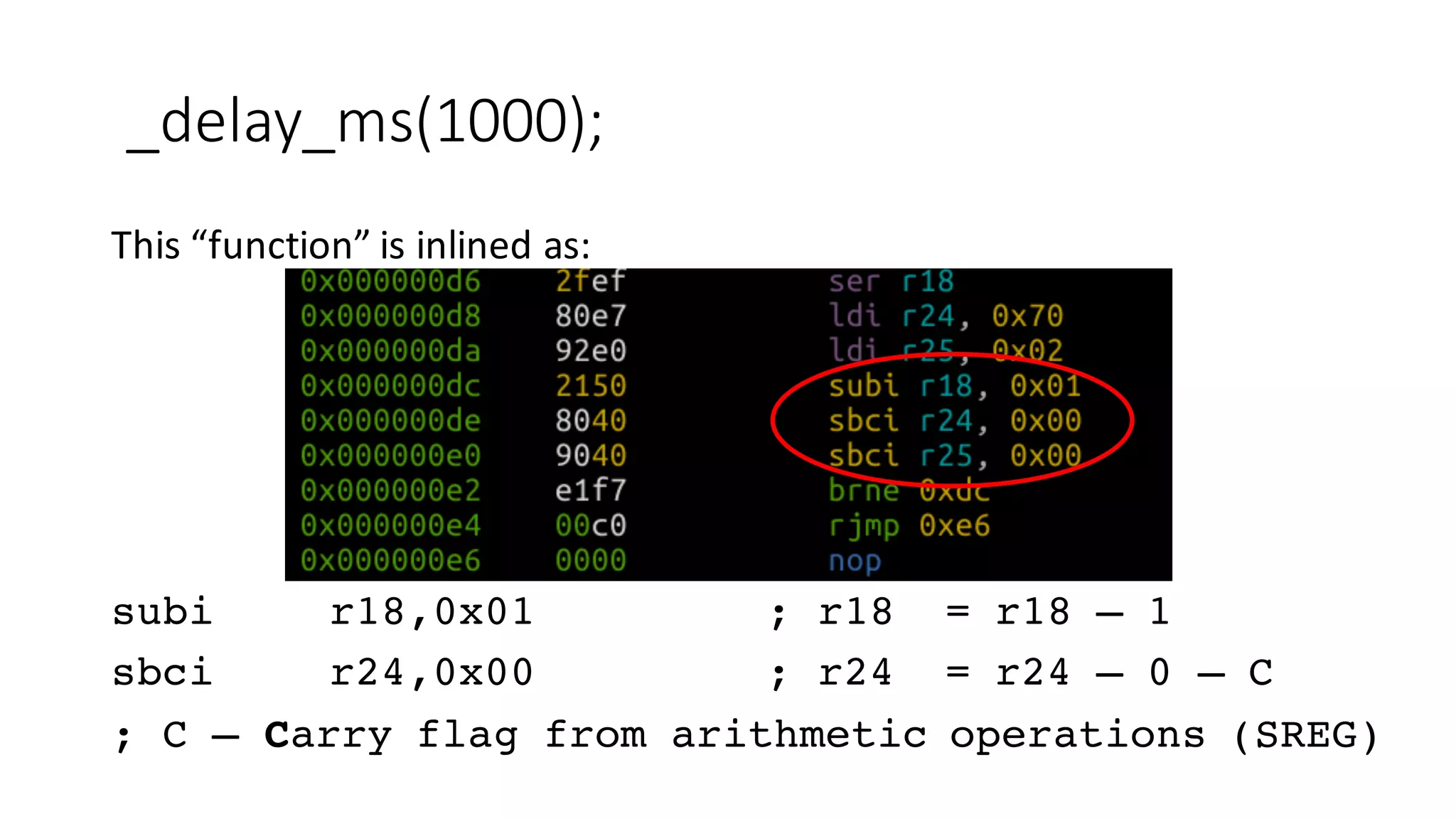
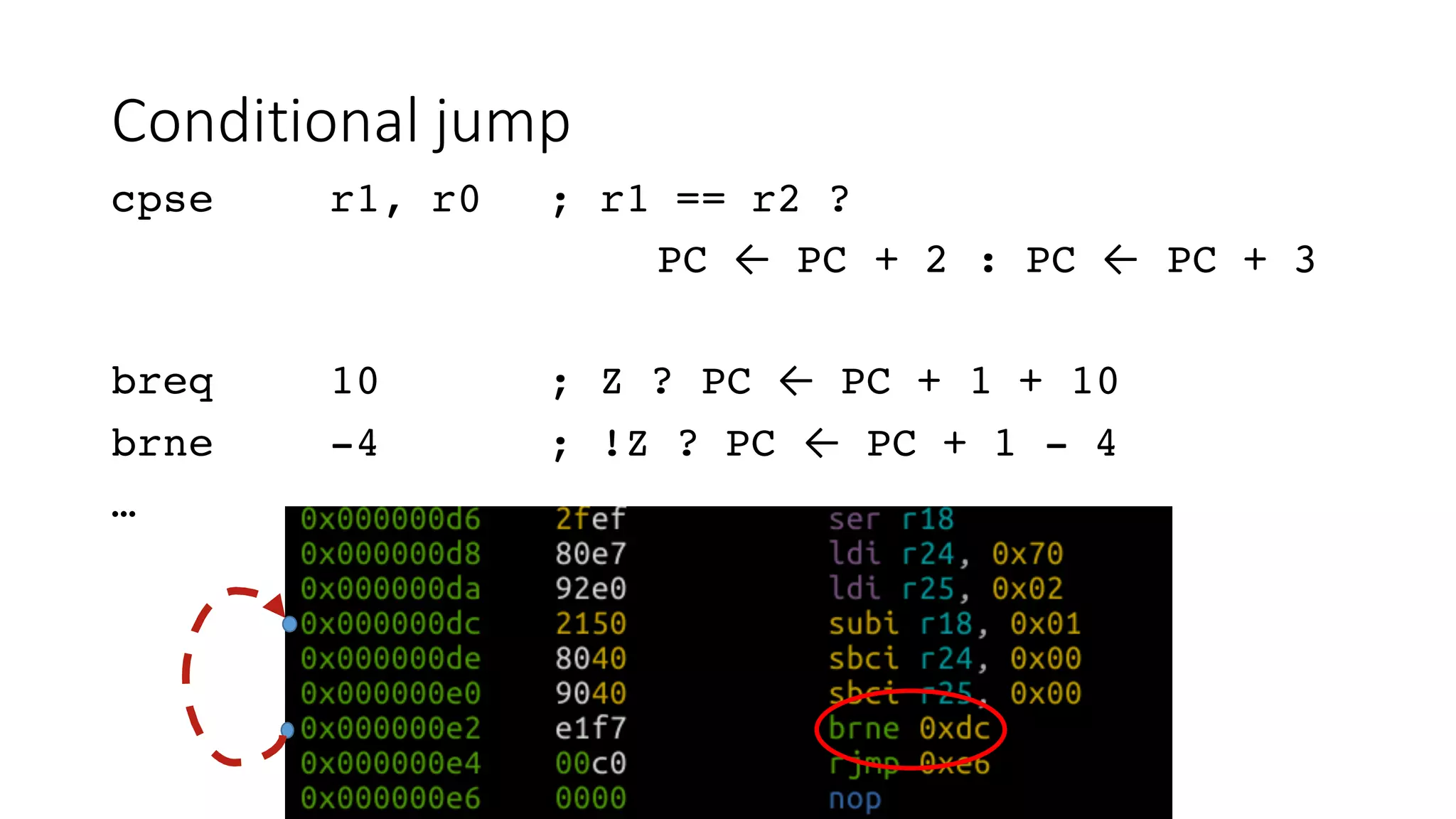
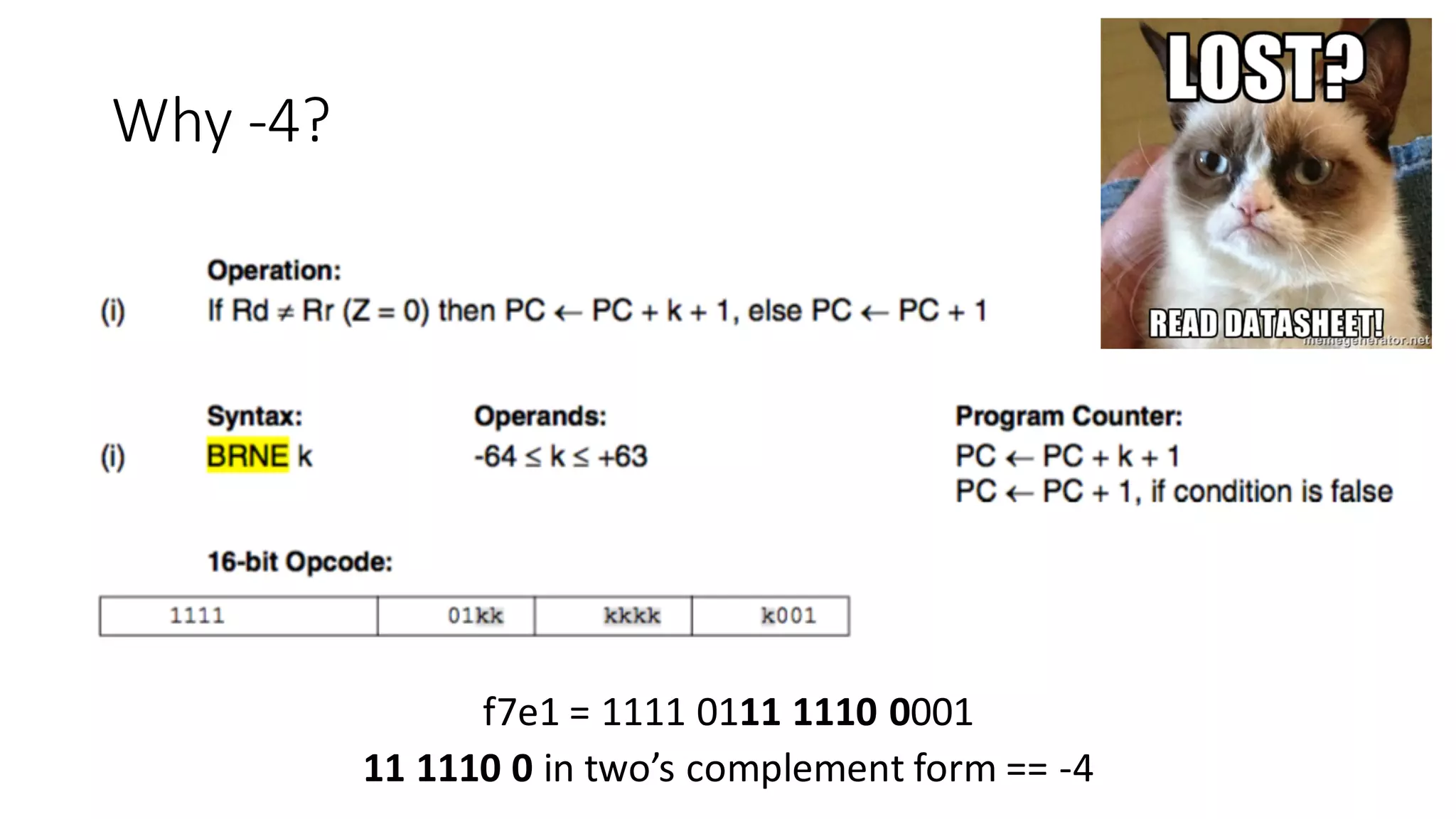
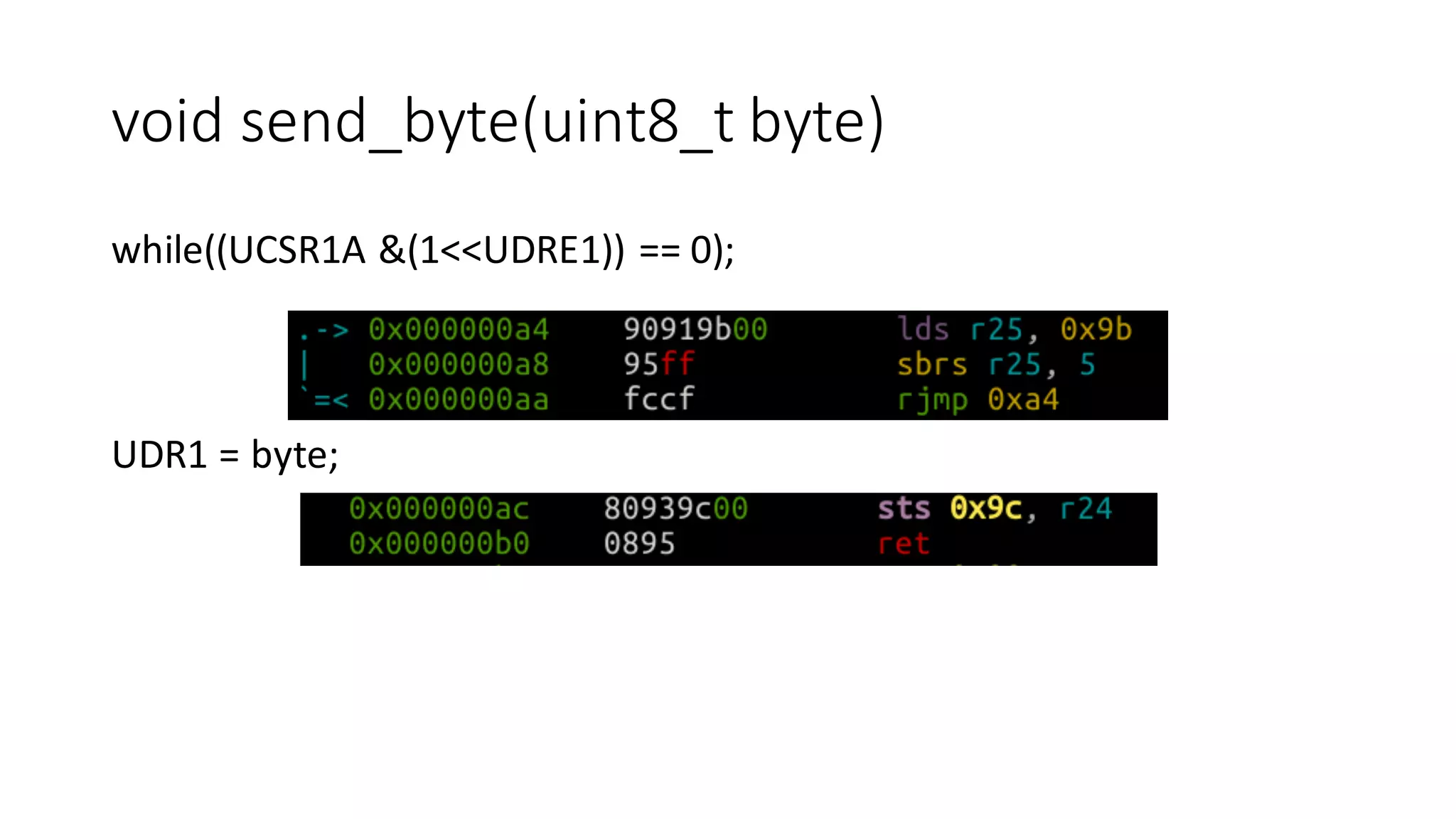
The document outlines an agenda for a training on practical firmware reversing and exploit development for AVR-based embedded devices. The training will cover: (1) an introduction to the AVR architecture through an example; (2) pre-exploitation techniques; (3) exploitation and building return-oriented programming (ROP) chains; and (4) post-exploitation tricks. It provides background information on the AVR architecture, which is used widely in embedded and IoT devices, and discusses features like memory organization, registers, interrupts, and assembly instructions. Development tools for AVR like Atmel Studio, AVR-GCC, and debuggers are also briefly mentioned.











































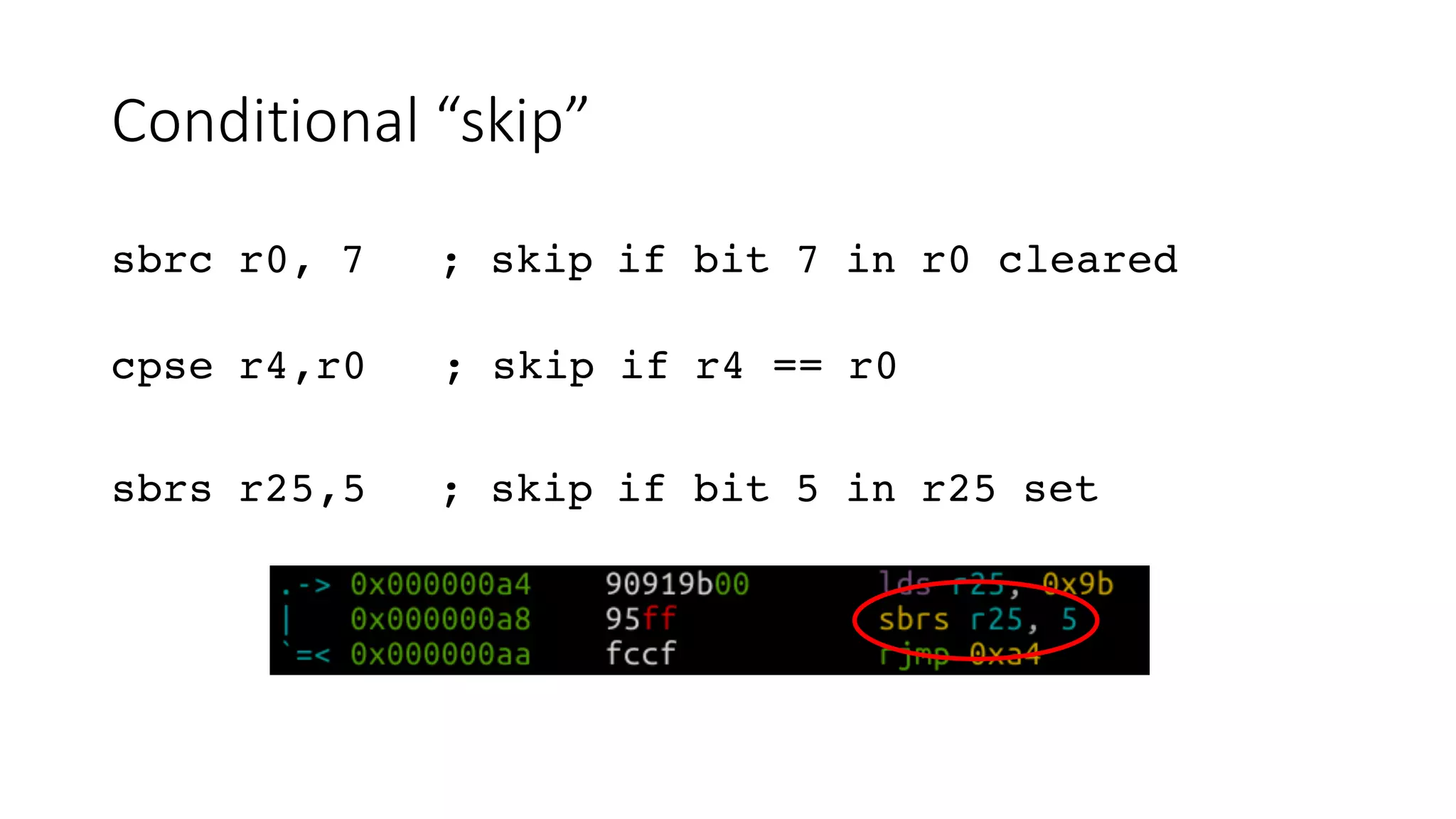


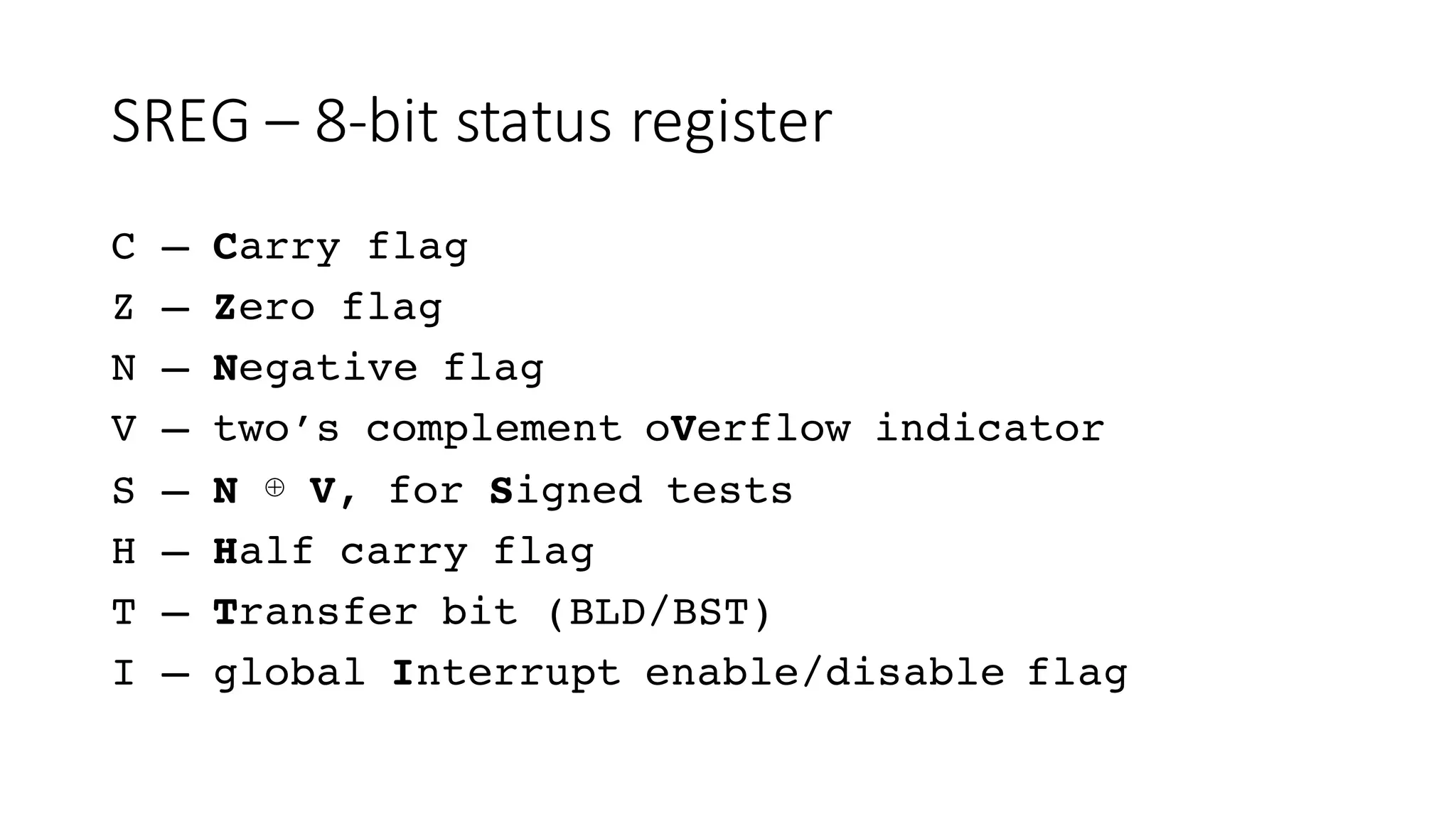

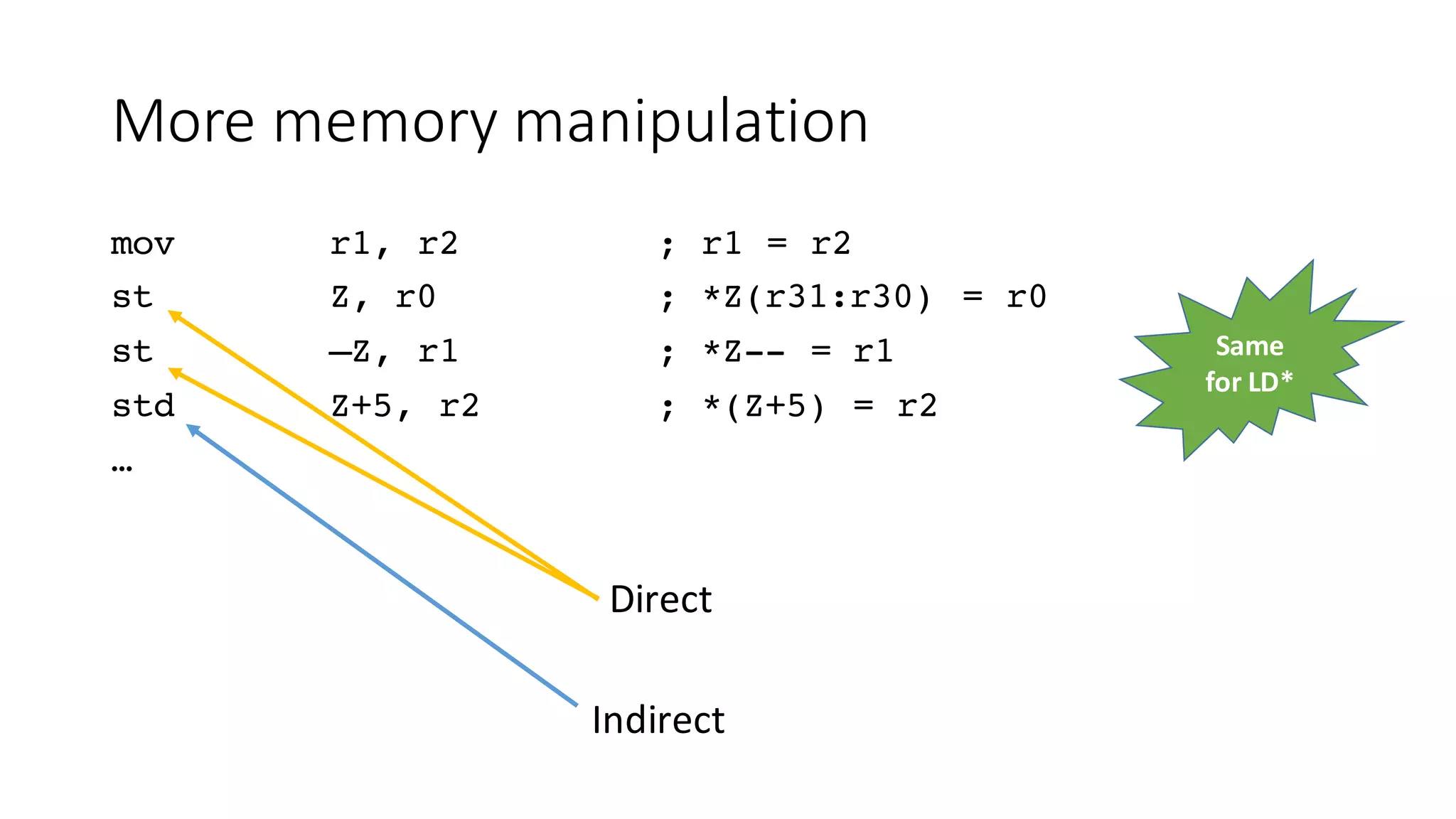
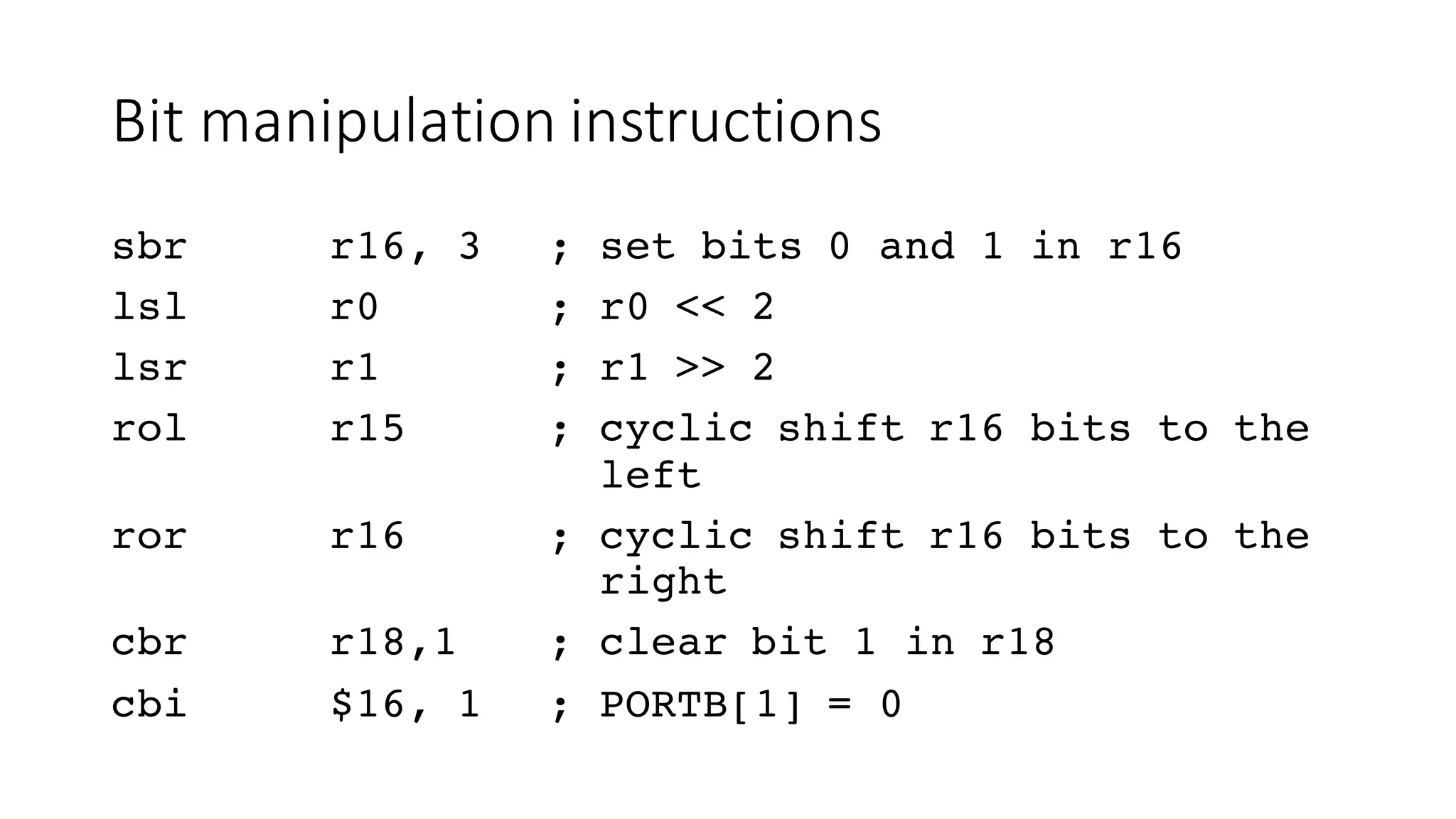
![Bit
manipulation
instructions
sbr r16, 3 ; set bits 0 and 1 in r16
lsl r0 ; r0 << 2
lsr r1 ; r1 >> 2
rol r15 ; cyclic shift r16 bits to the
left
ror r16 ; cyclic shift r16 bits to the
right
cbr r18,1 ; clear bit 1 in r18
cbi $16, 1 ; PORTB[1] = 0](https://image.slidesharecdn.com/avrworkshops4-160116003058/75/Practical-reverse-engineering-and-exploit-development-for-AVR-based-Embedded-Devices-s4x16-117-2048.jpg)