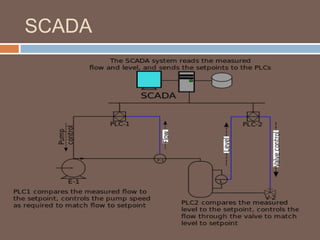
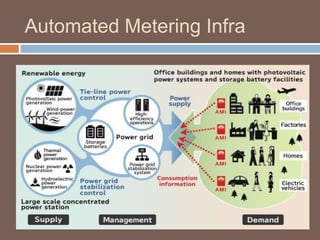
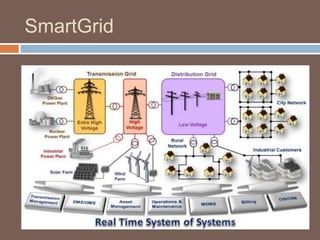
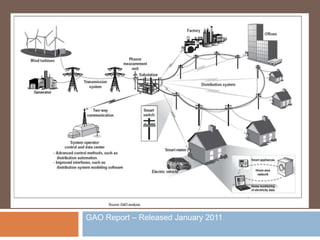
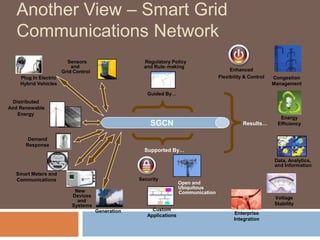
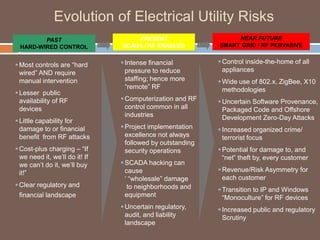
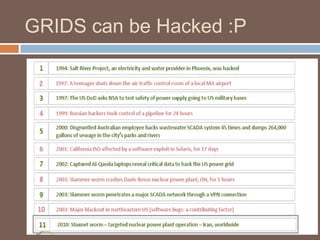
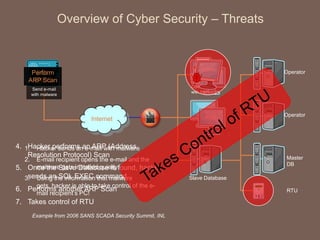
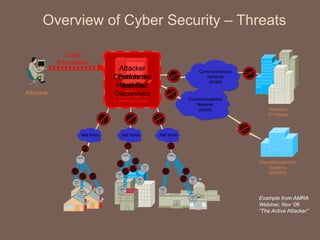
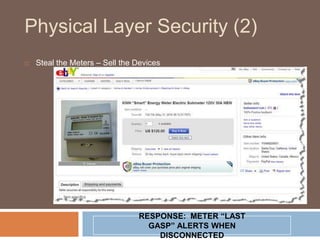
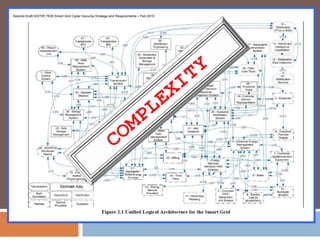
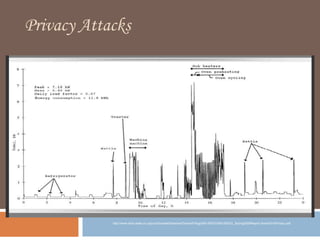
The document discusses the concept of smart grids, emphasizing their reliance on advanced technologies and communication systems to efficiently manage electricity demand. It highlights the importance of cybersecurity, detailing various threats like hacking and malware attacks on smart grid infrastructure, along with proposed defense strategies. The document concludes with recommendations for enhancing security and managing risks, advocating for comprehensive planning and collaboration with security experts.