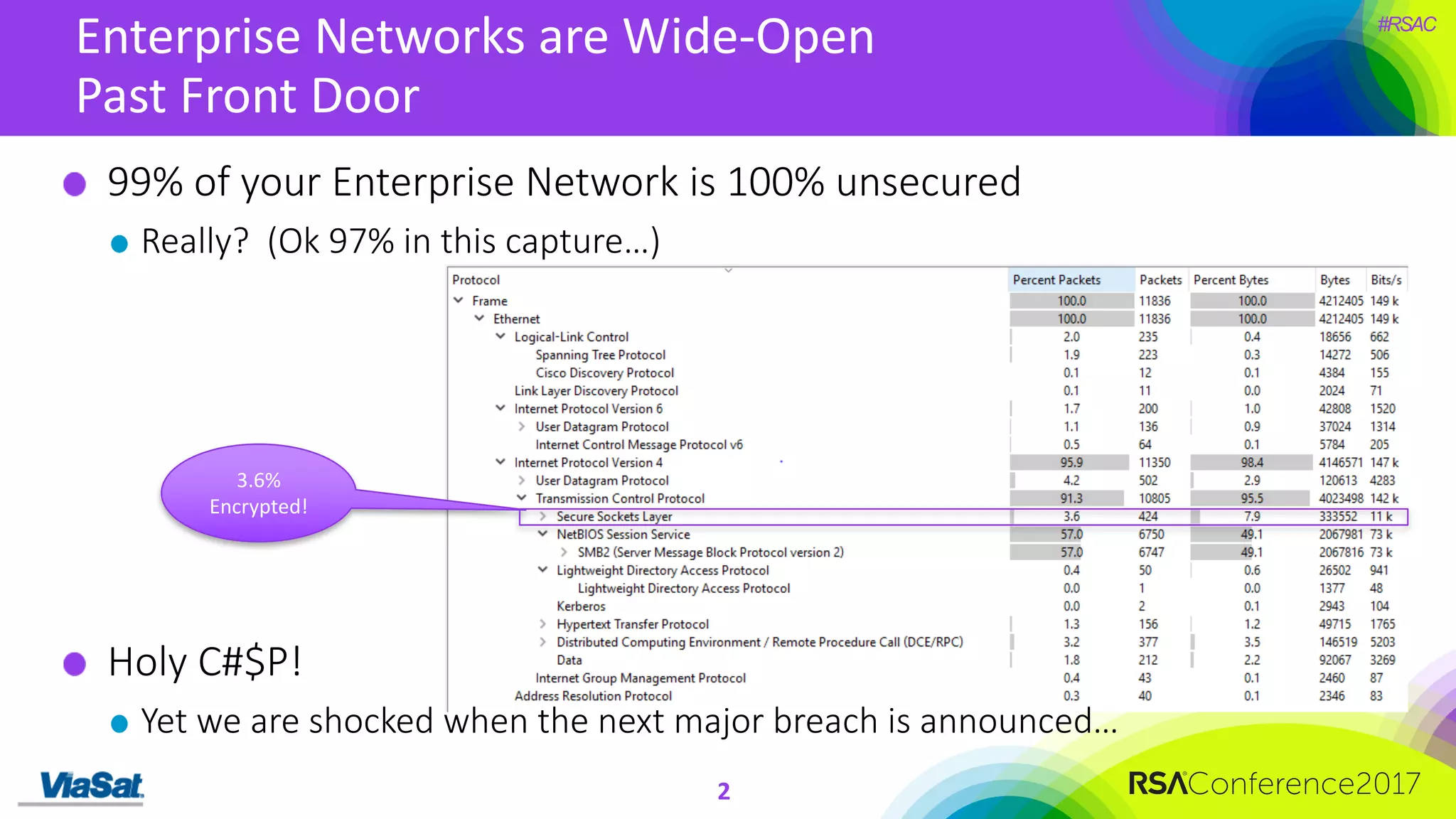
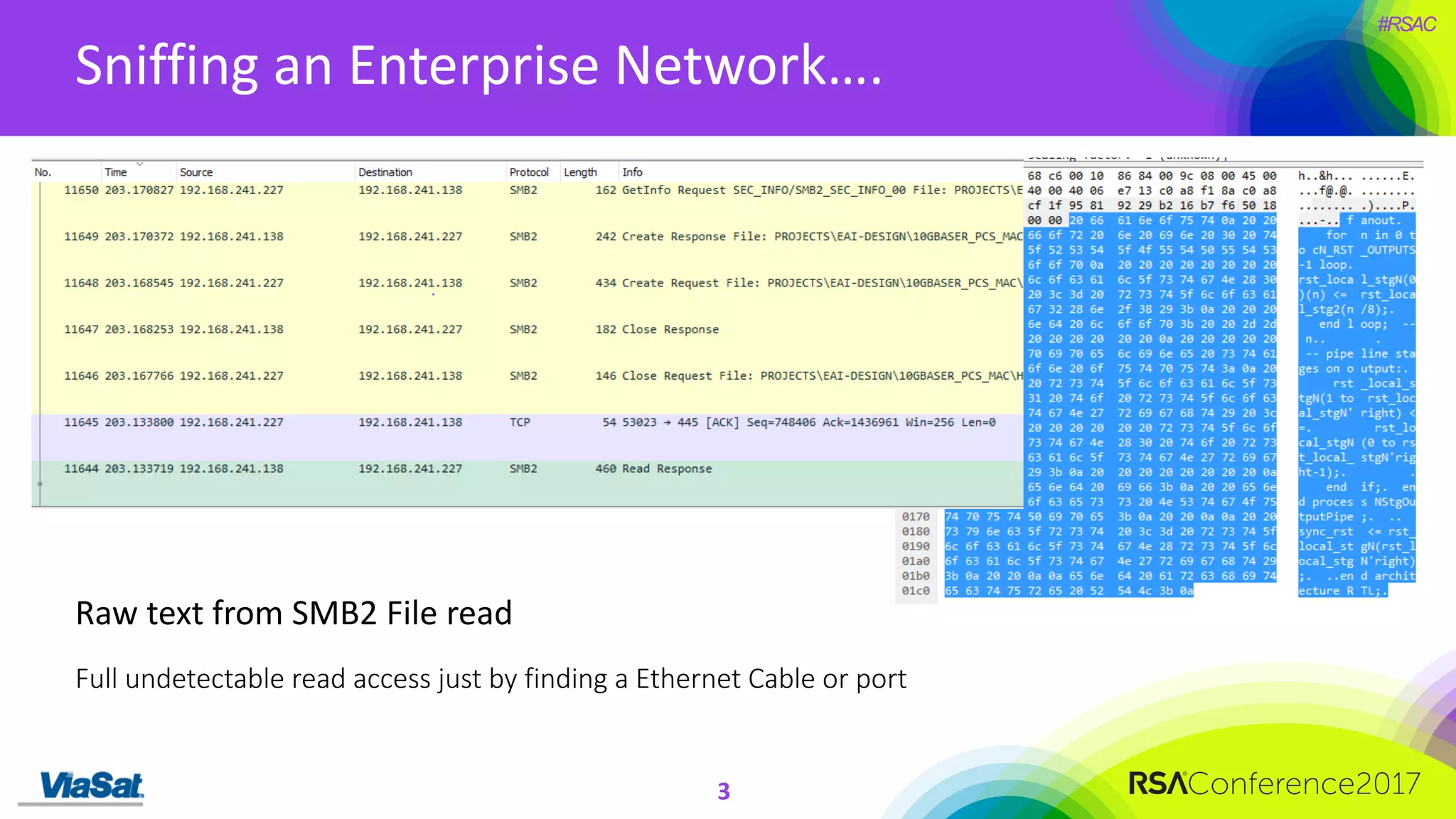
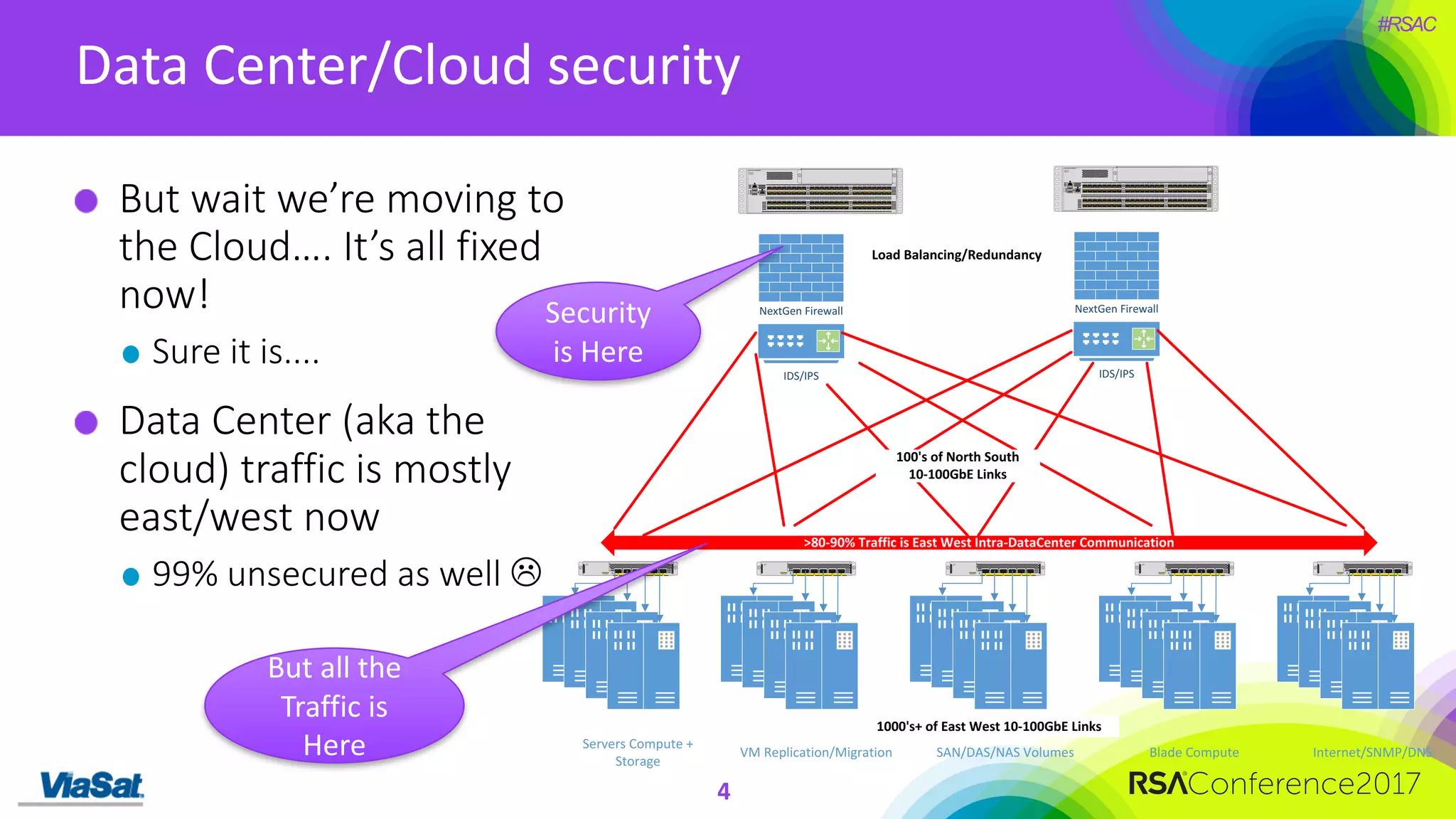
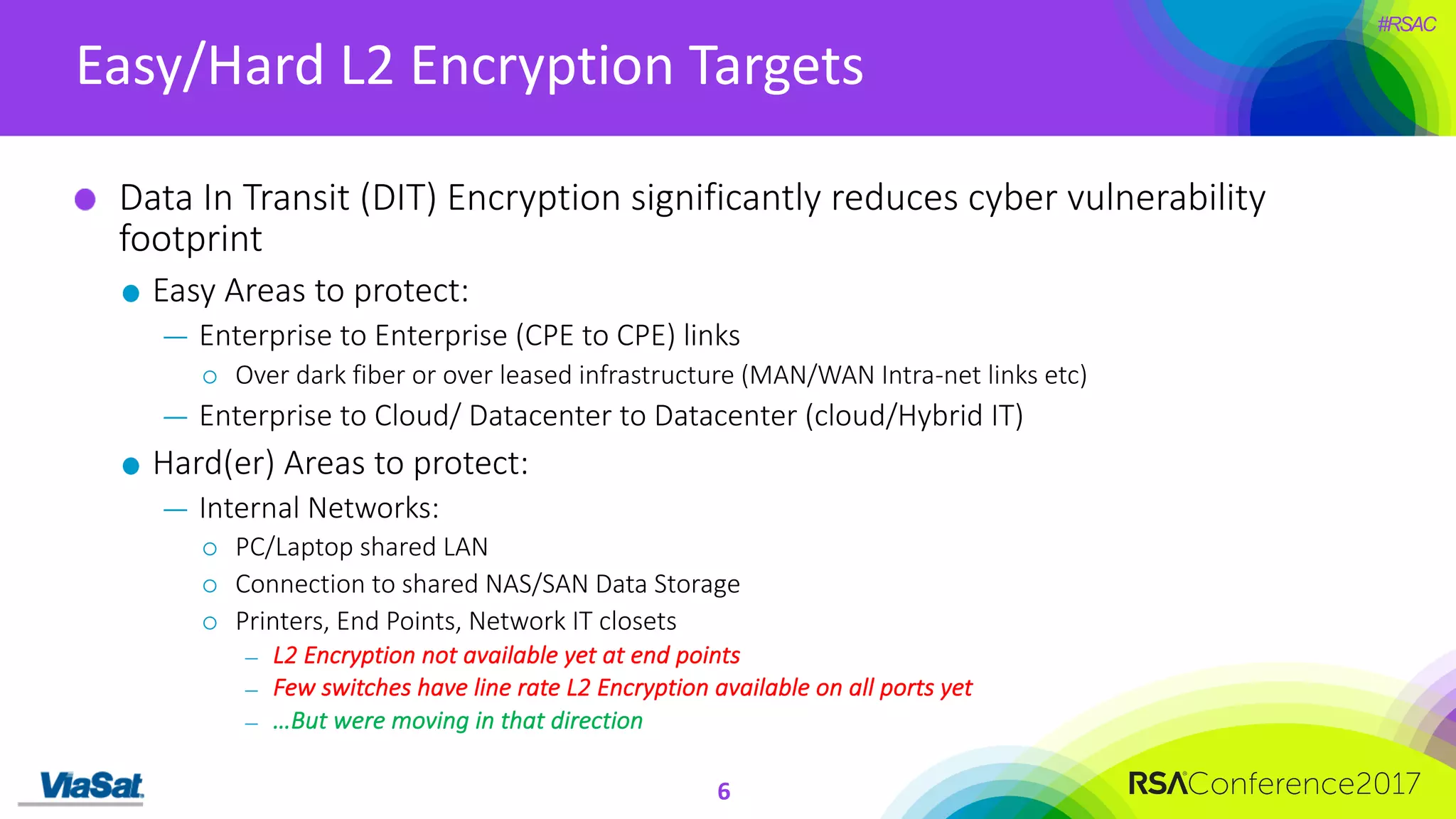
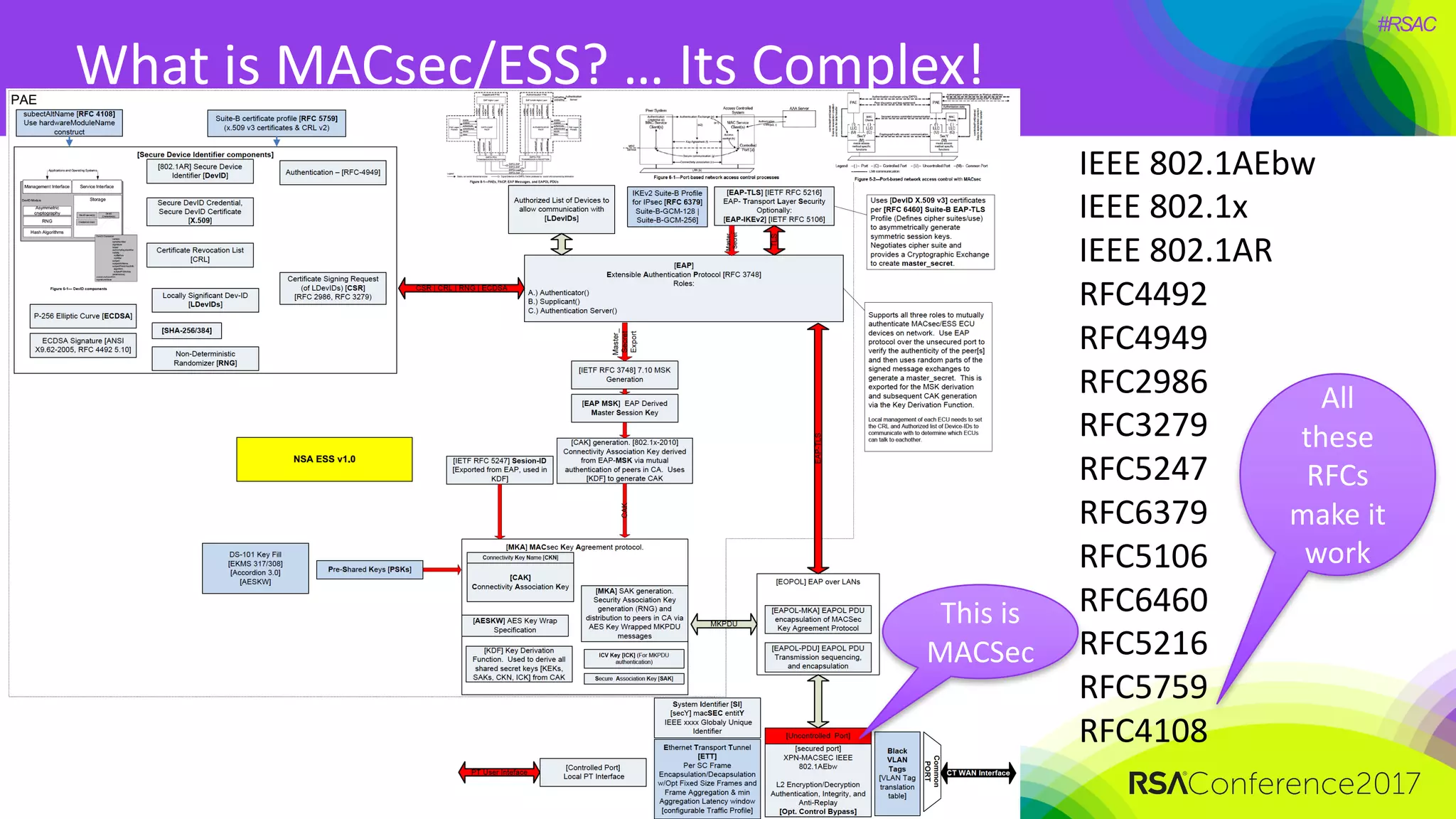
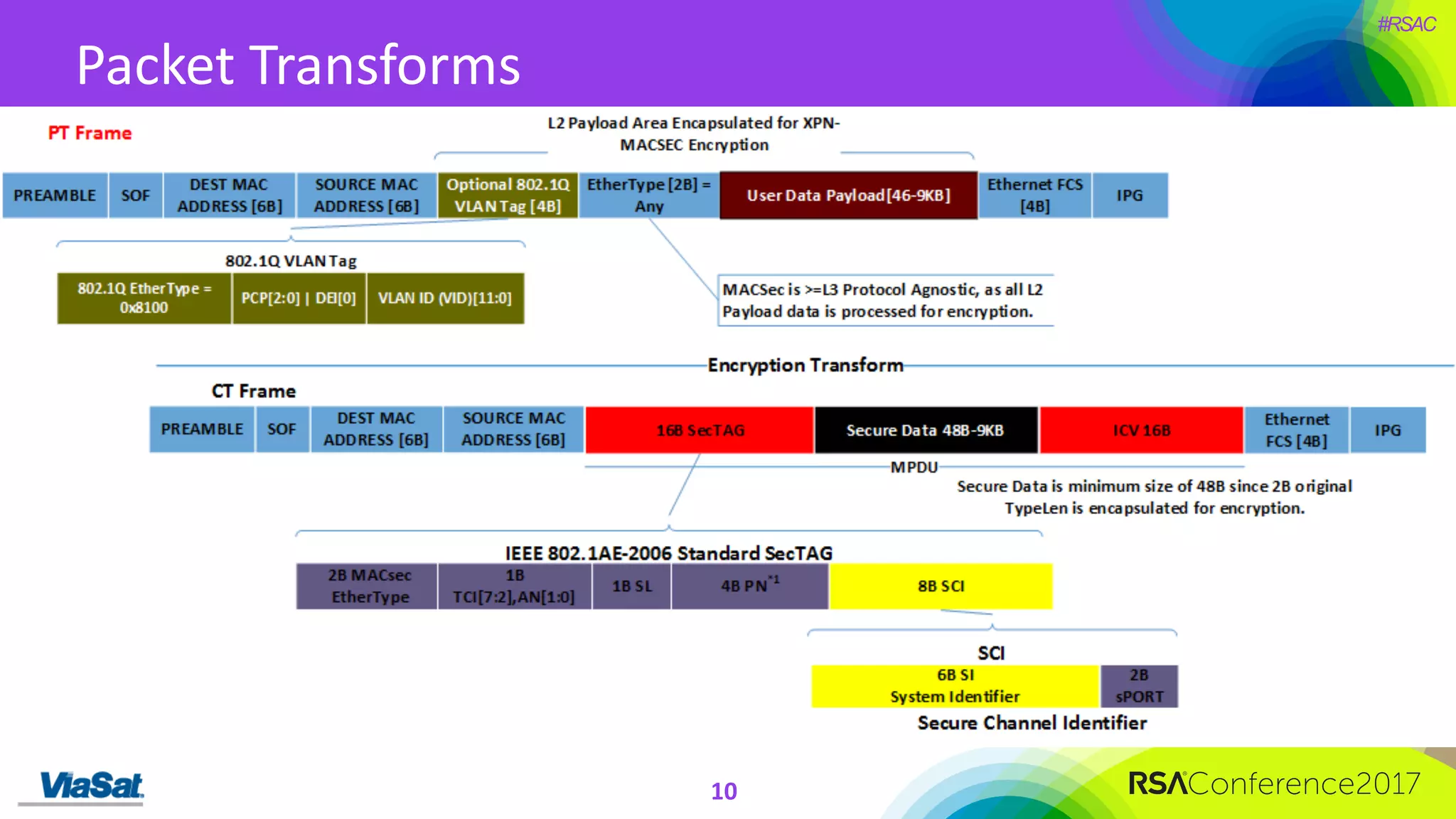
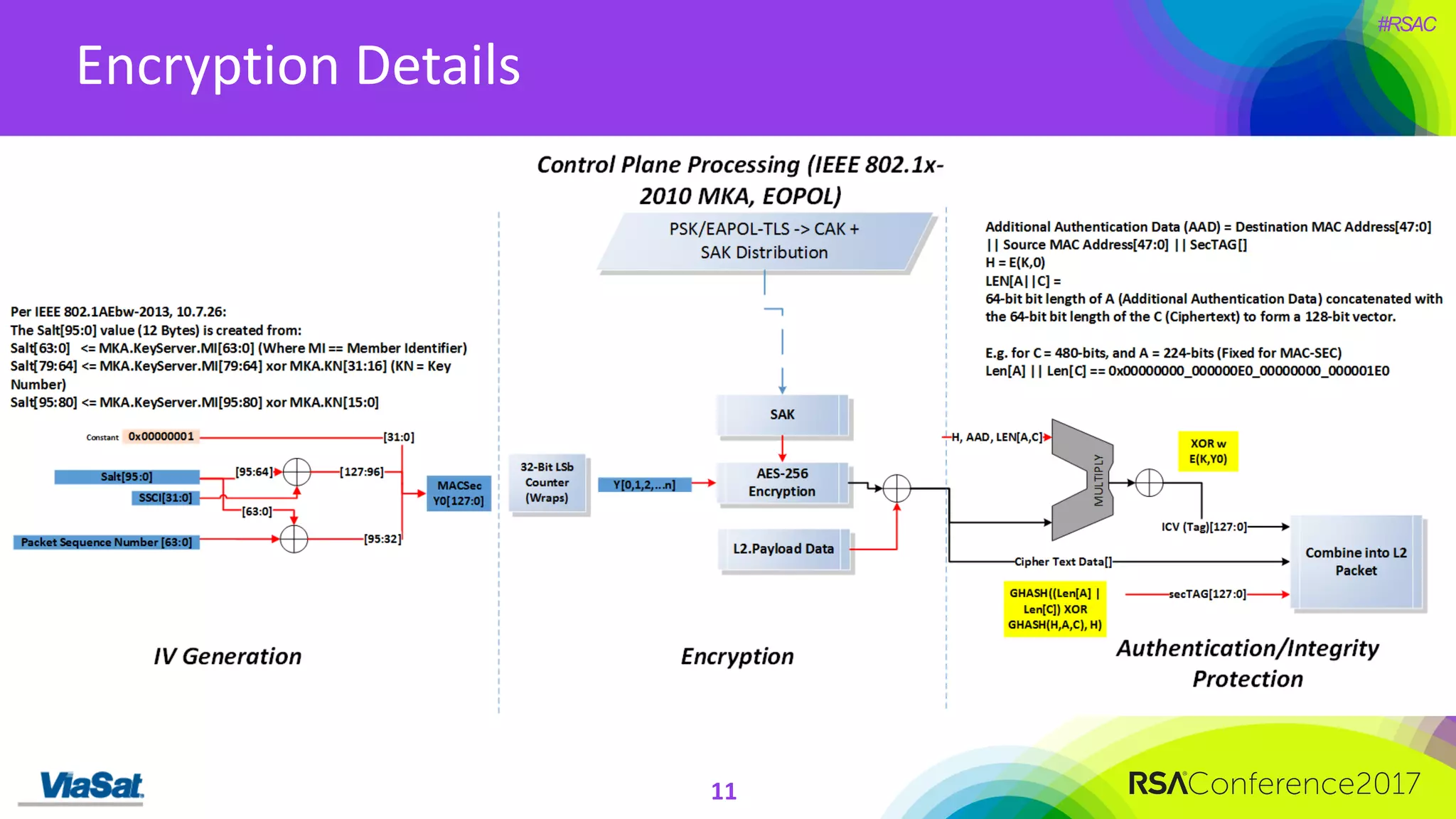
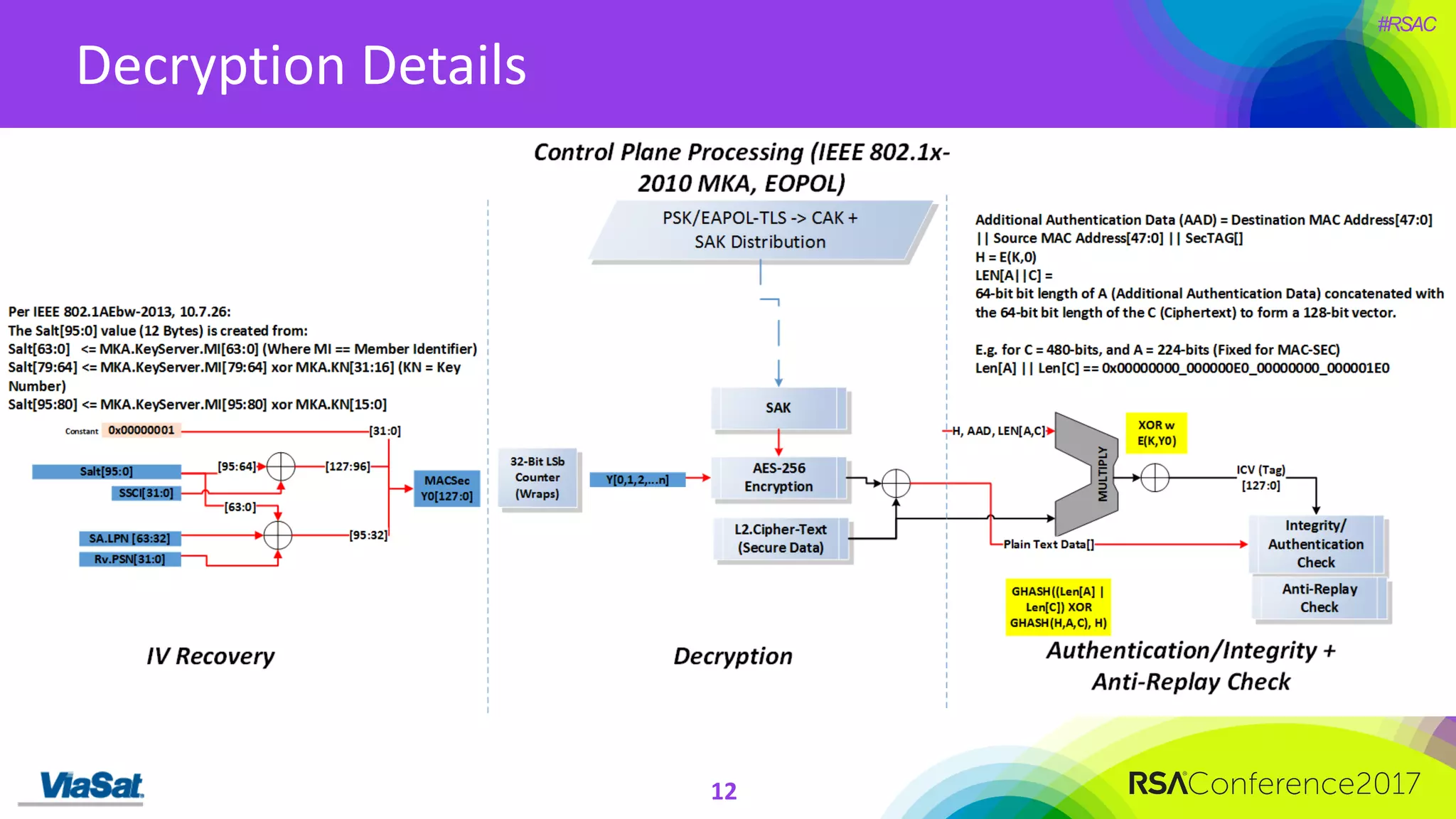
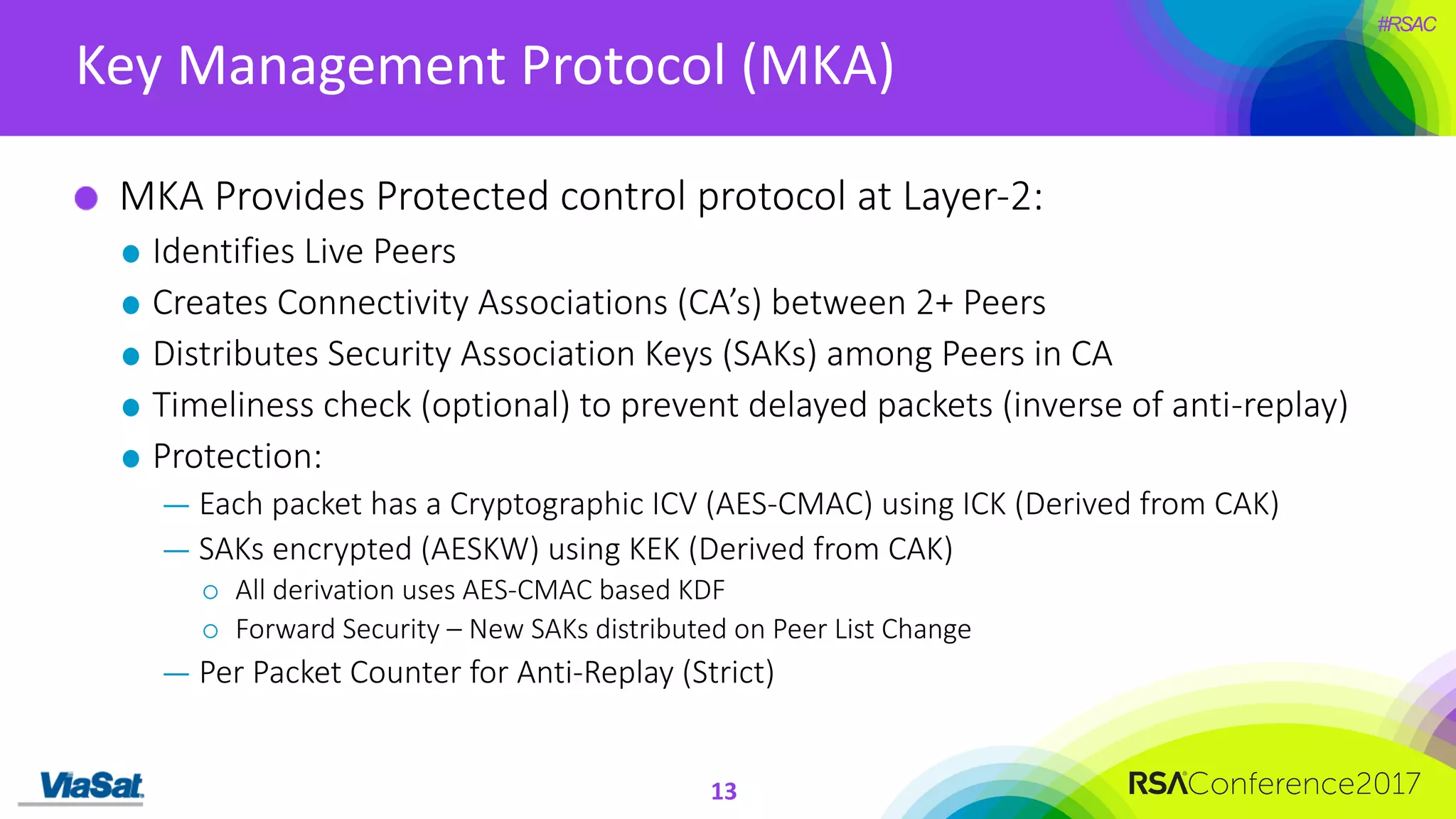
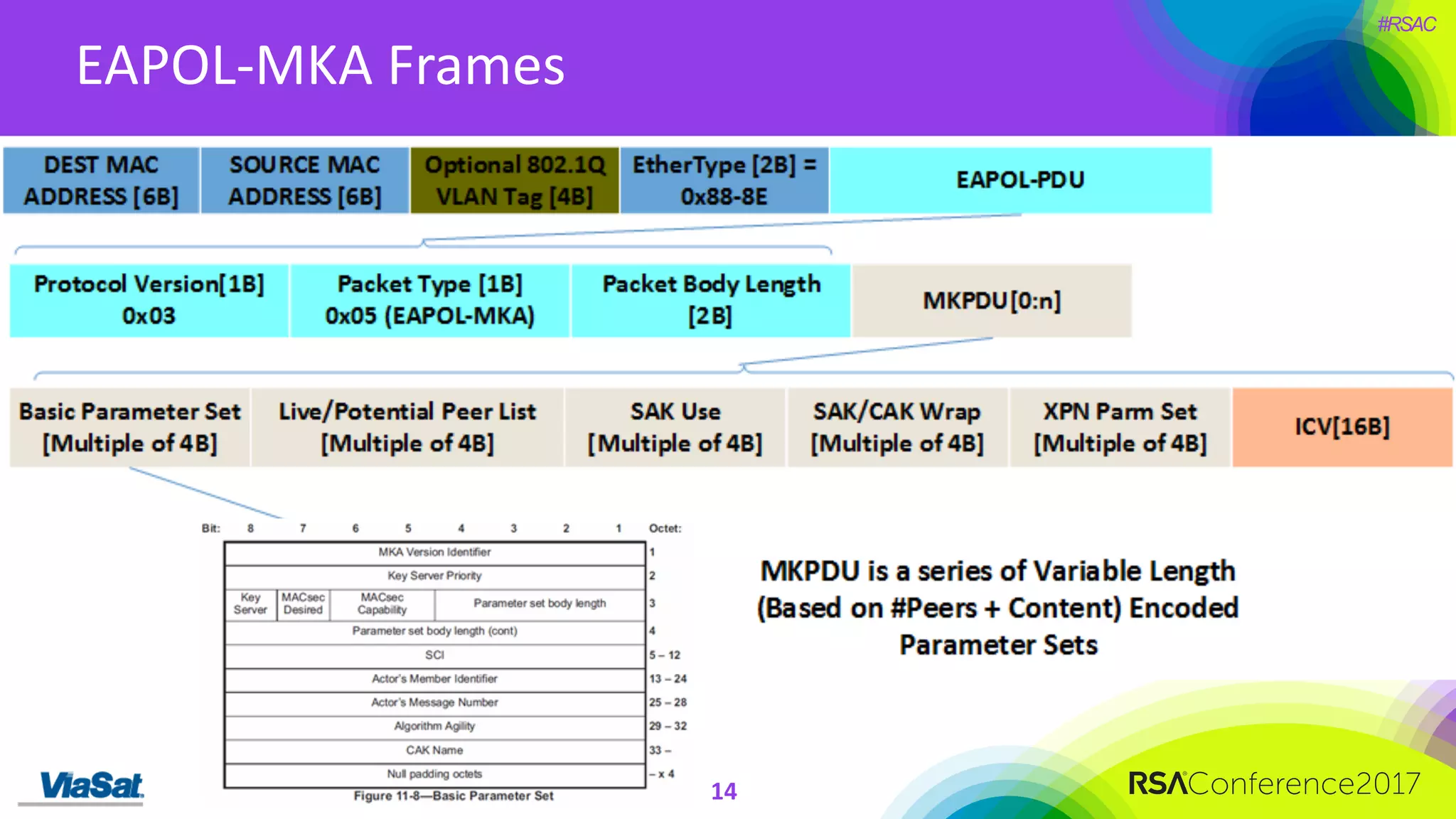
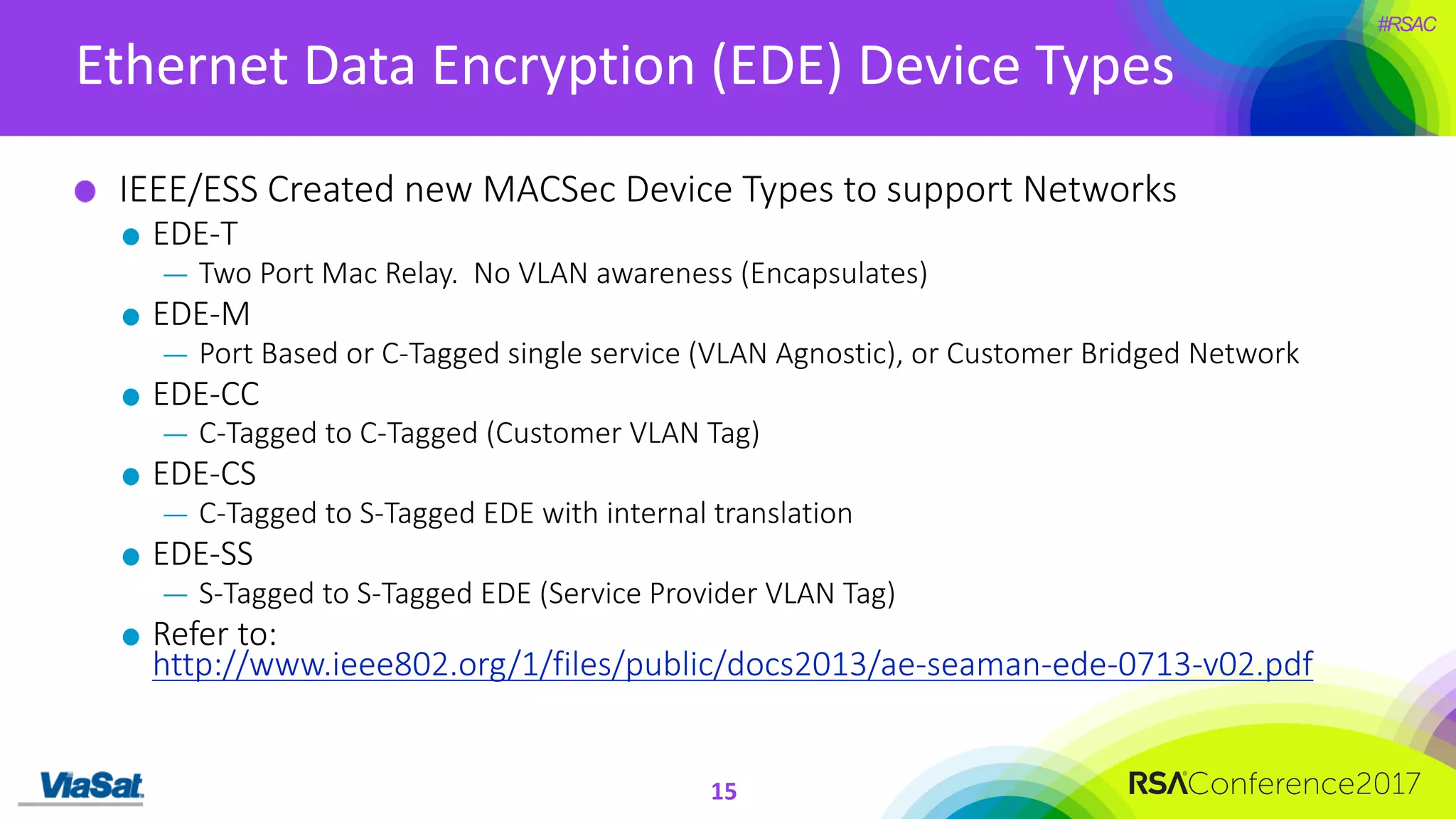
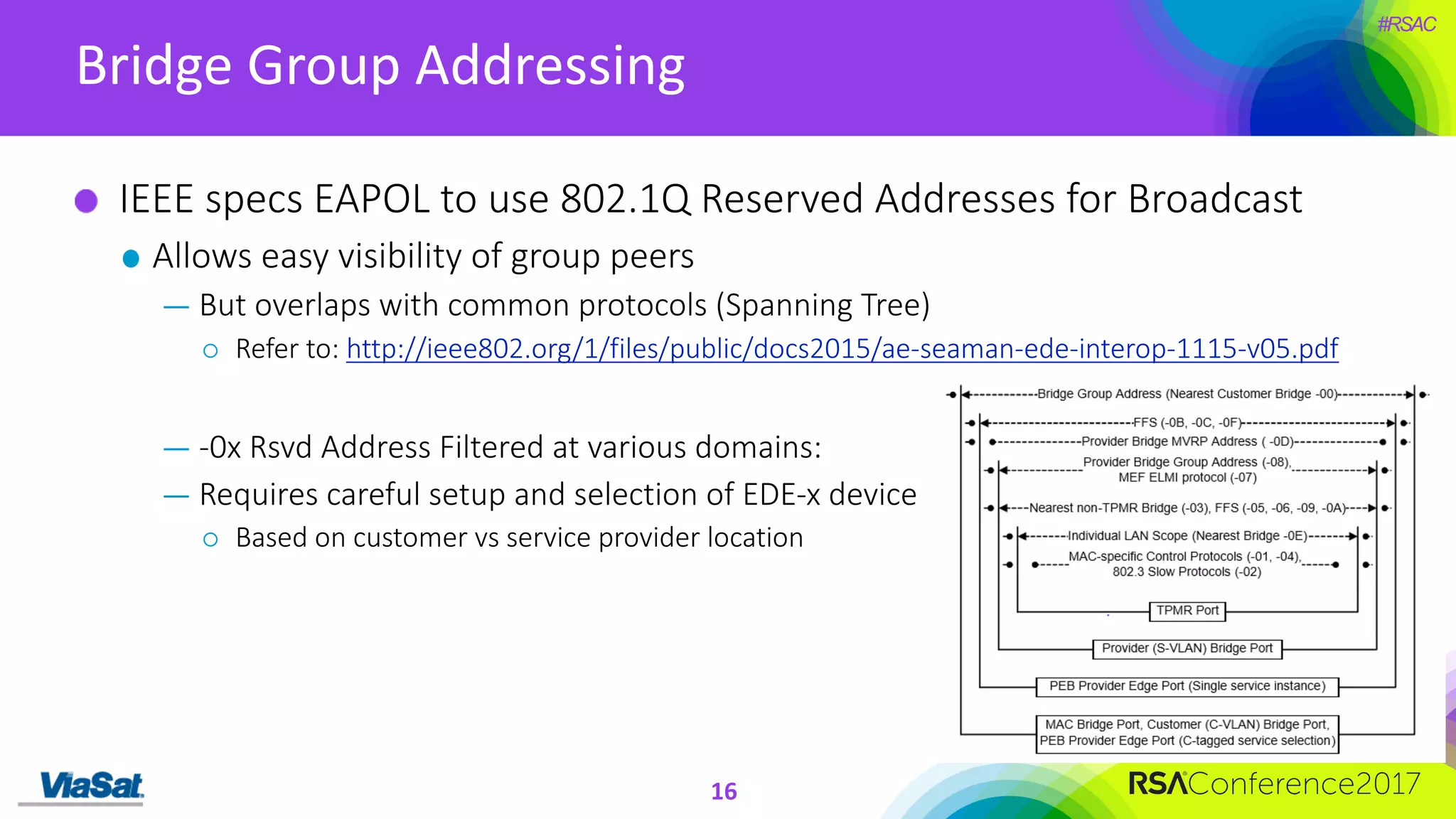
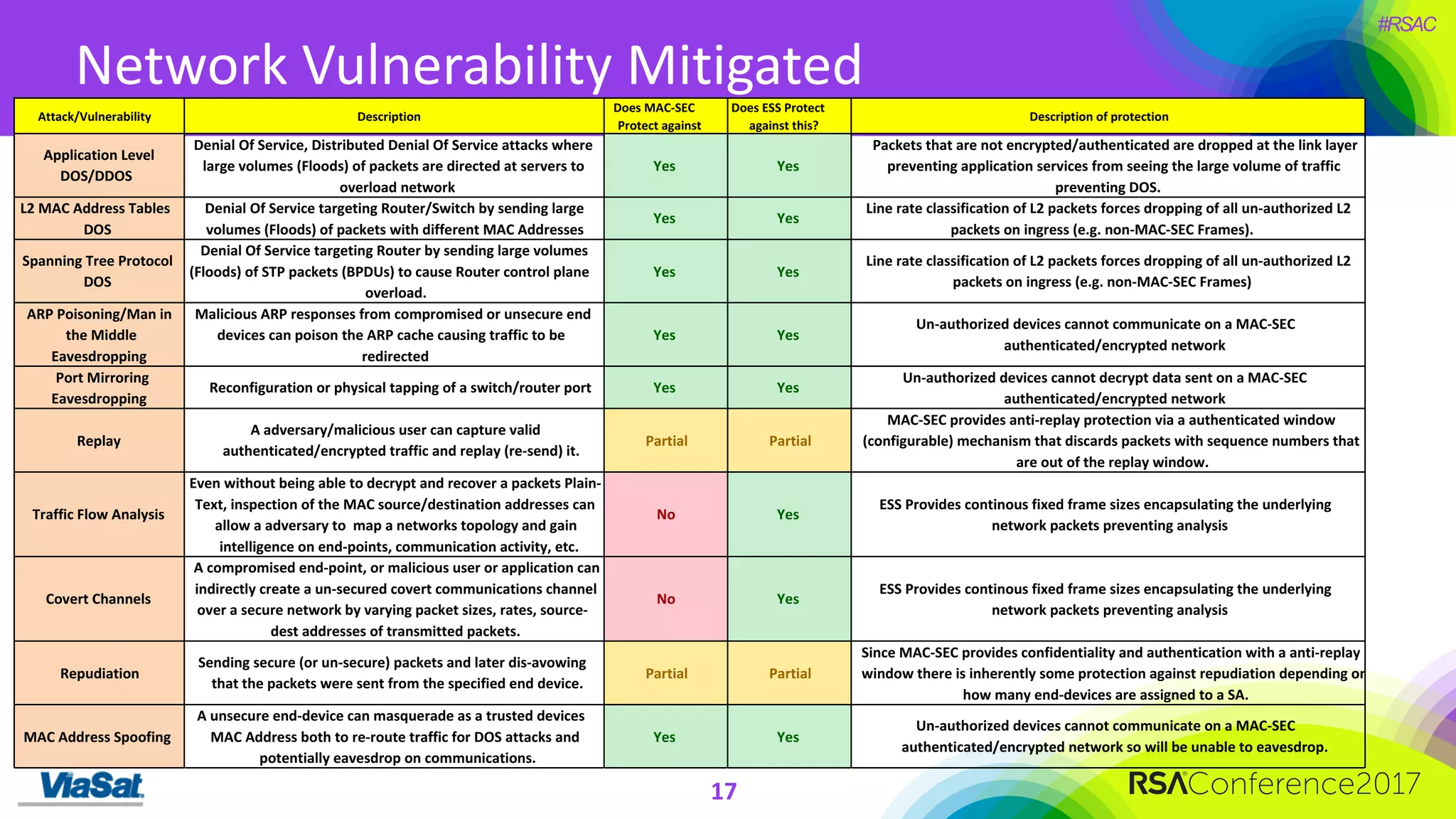
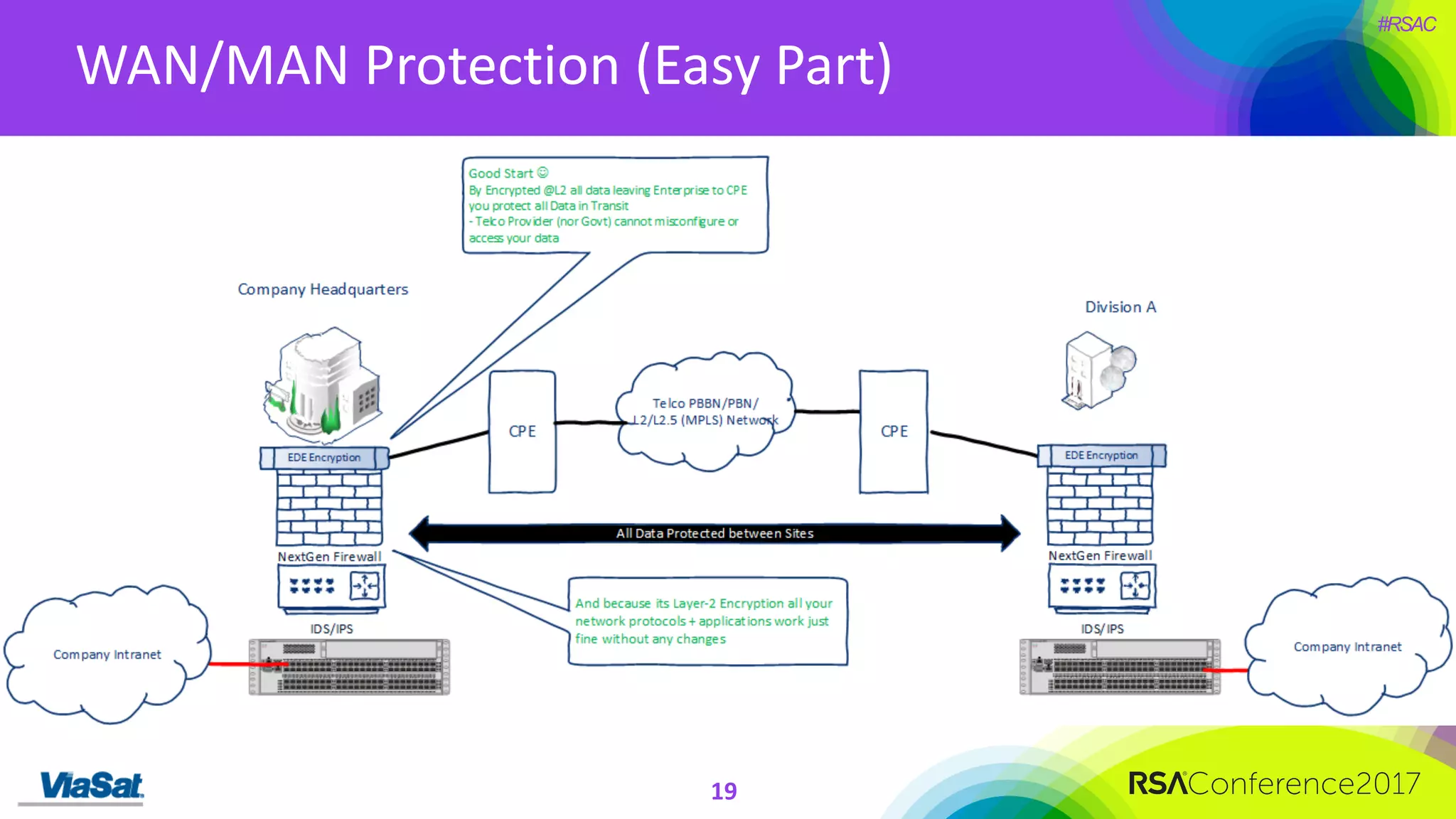
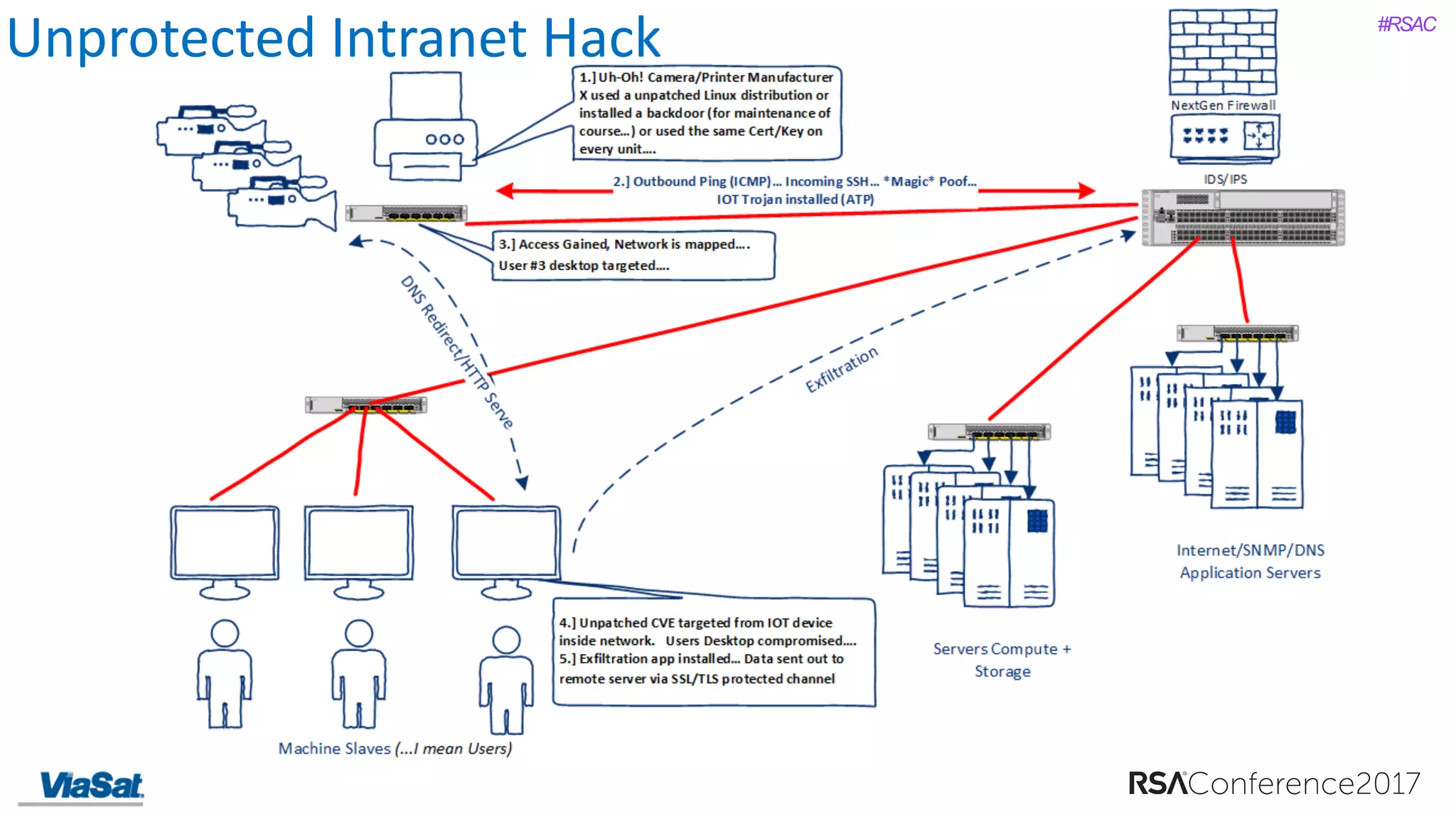
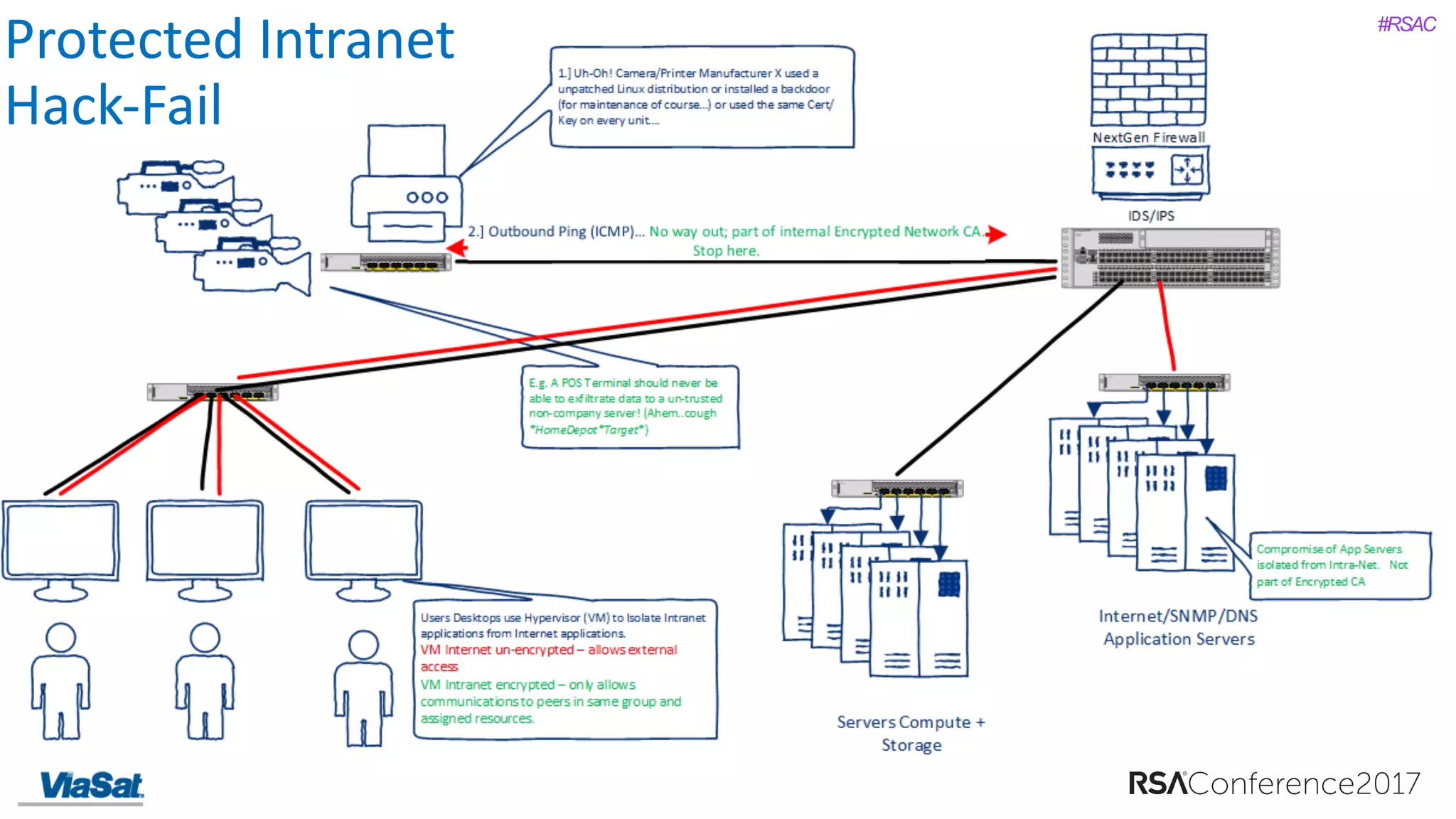
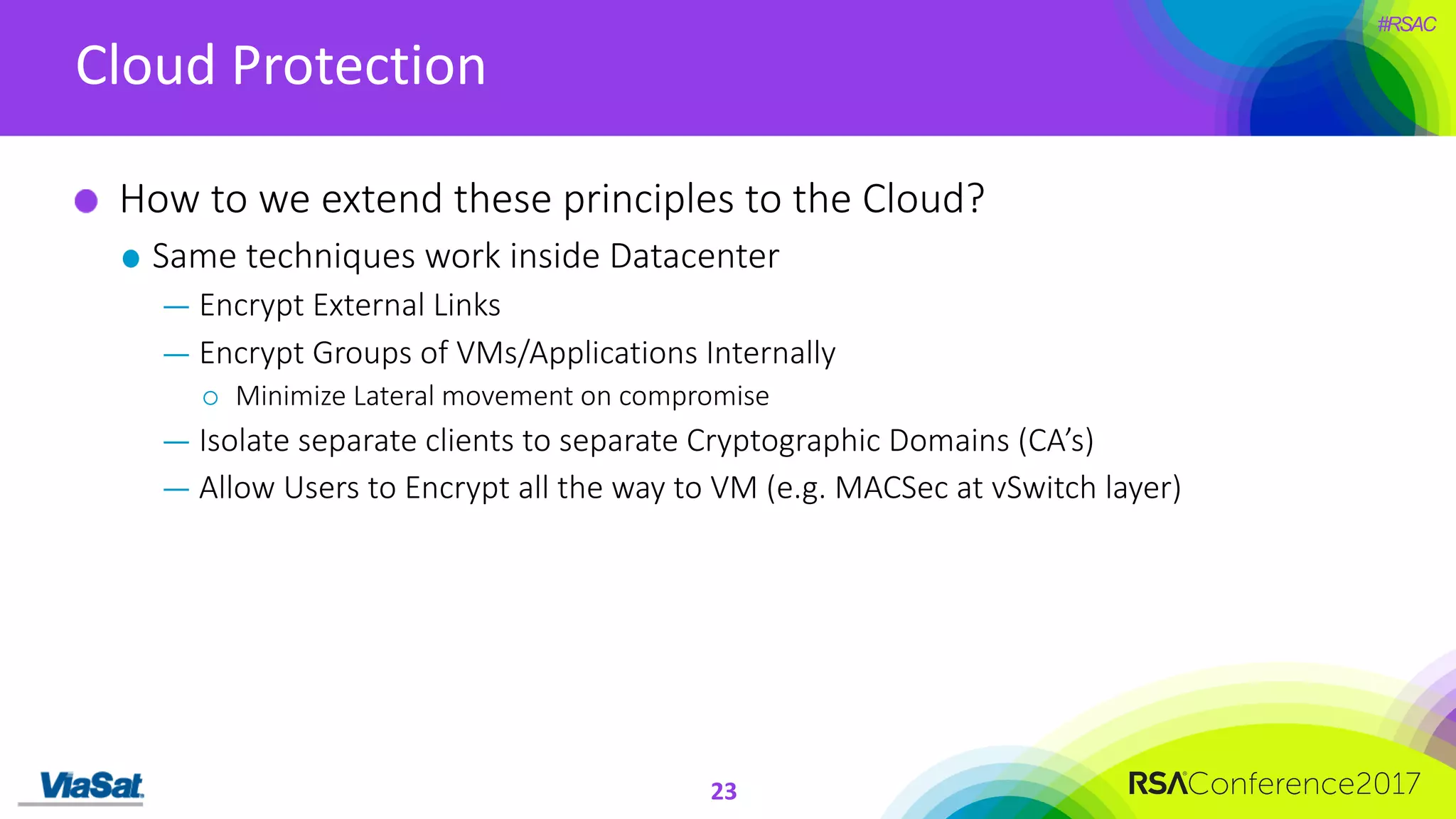
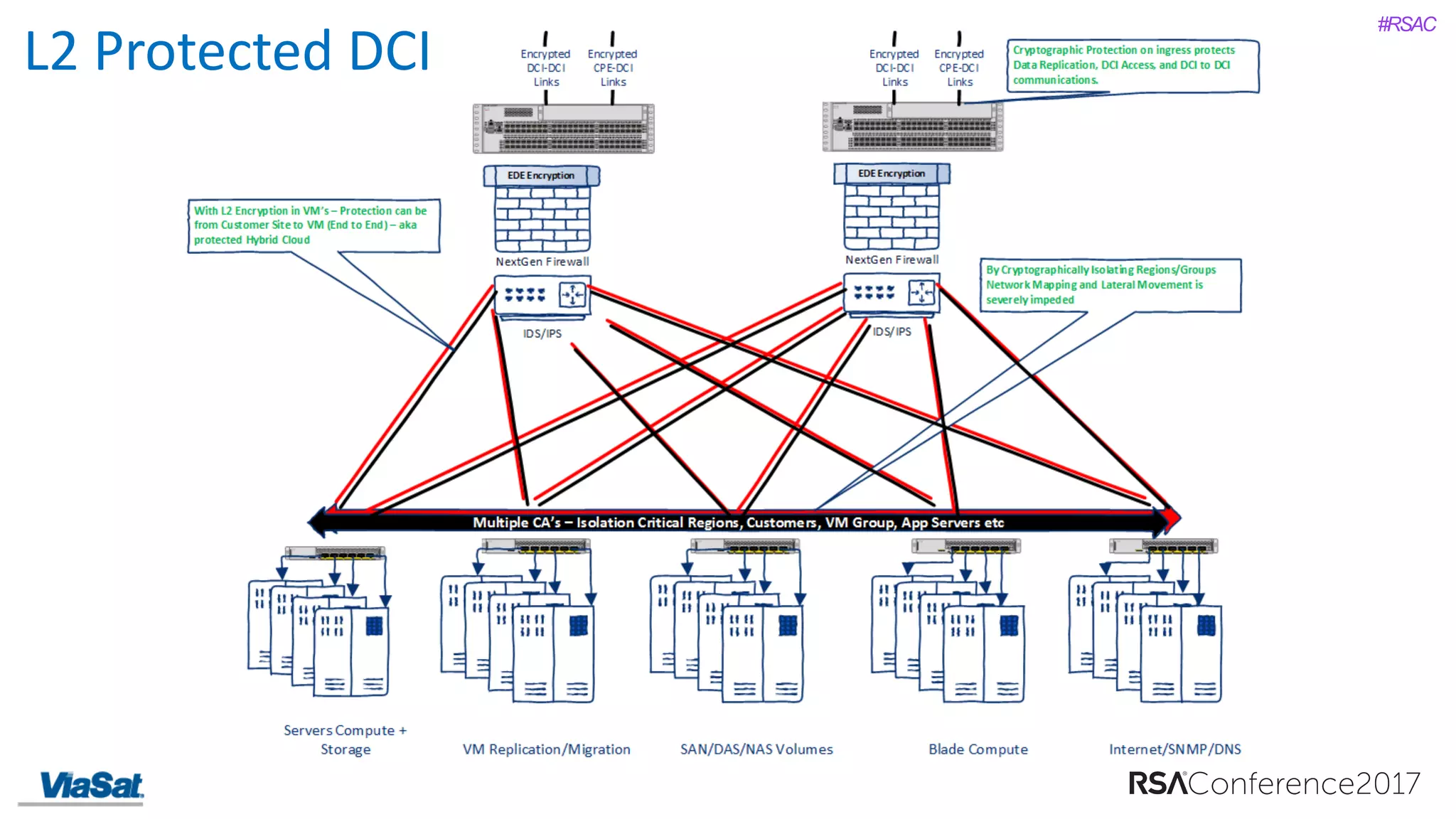
The document discusses the significant security vulnerabilities in enterprise networks, highlighting that up to 97% of networks remain unsecured, particularly in east-west traffic within data centers and the cloud. It emphasizes the necessity of robust encryption solutions like MACsec and ESS to protect data in transit, detailing how they can mitigate various attacks and secure internal communications. The author advocates for organizations to adopt strong encryption strategies and integrate MACsec across all network ports to effectively safeguard against cyber threats.