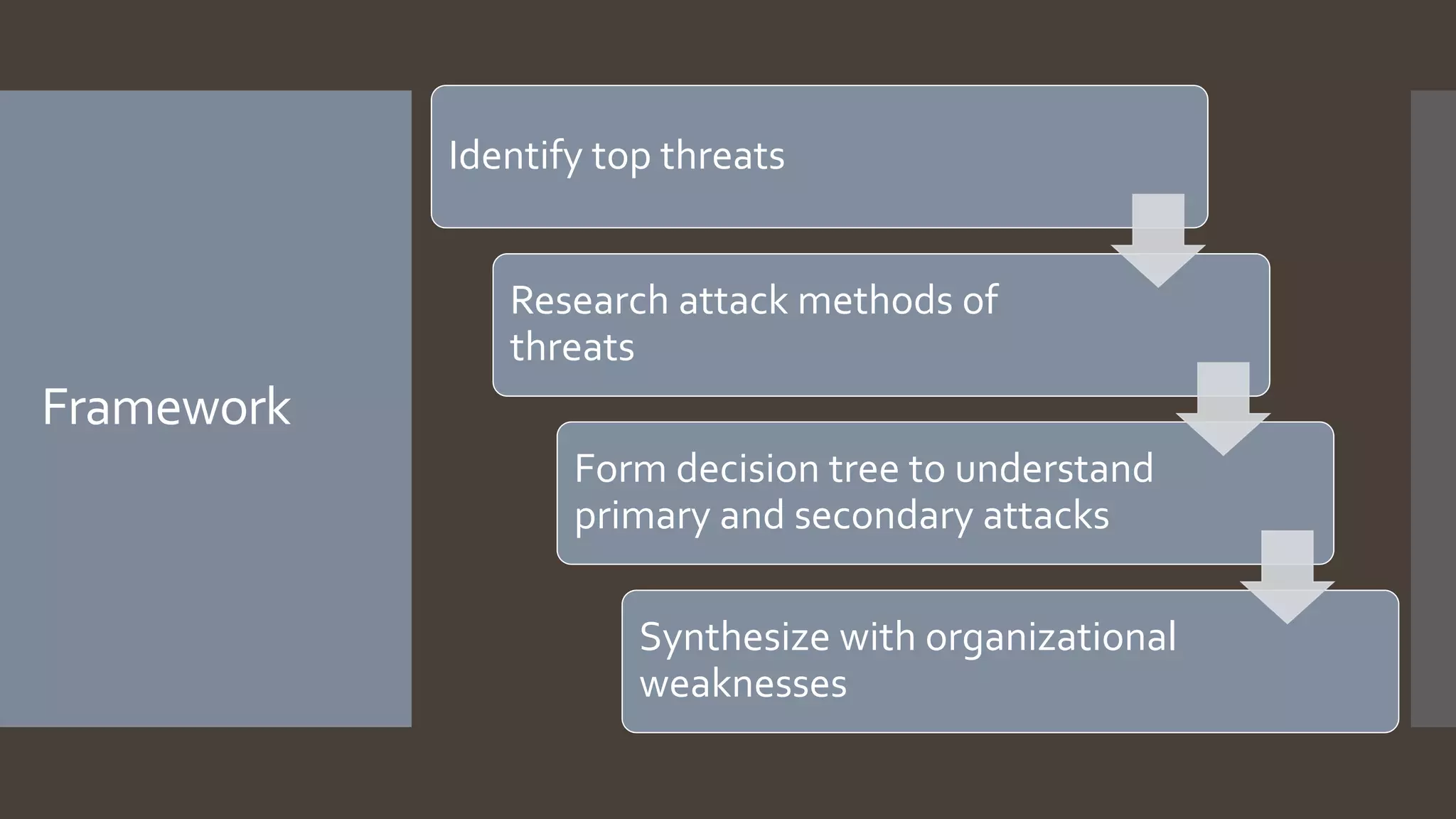
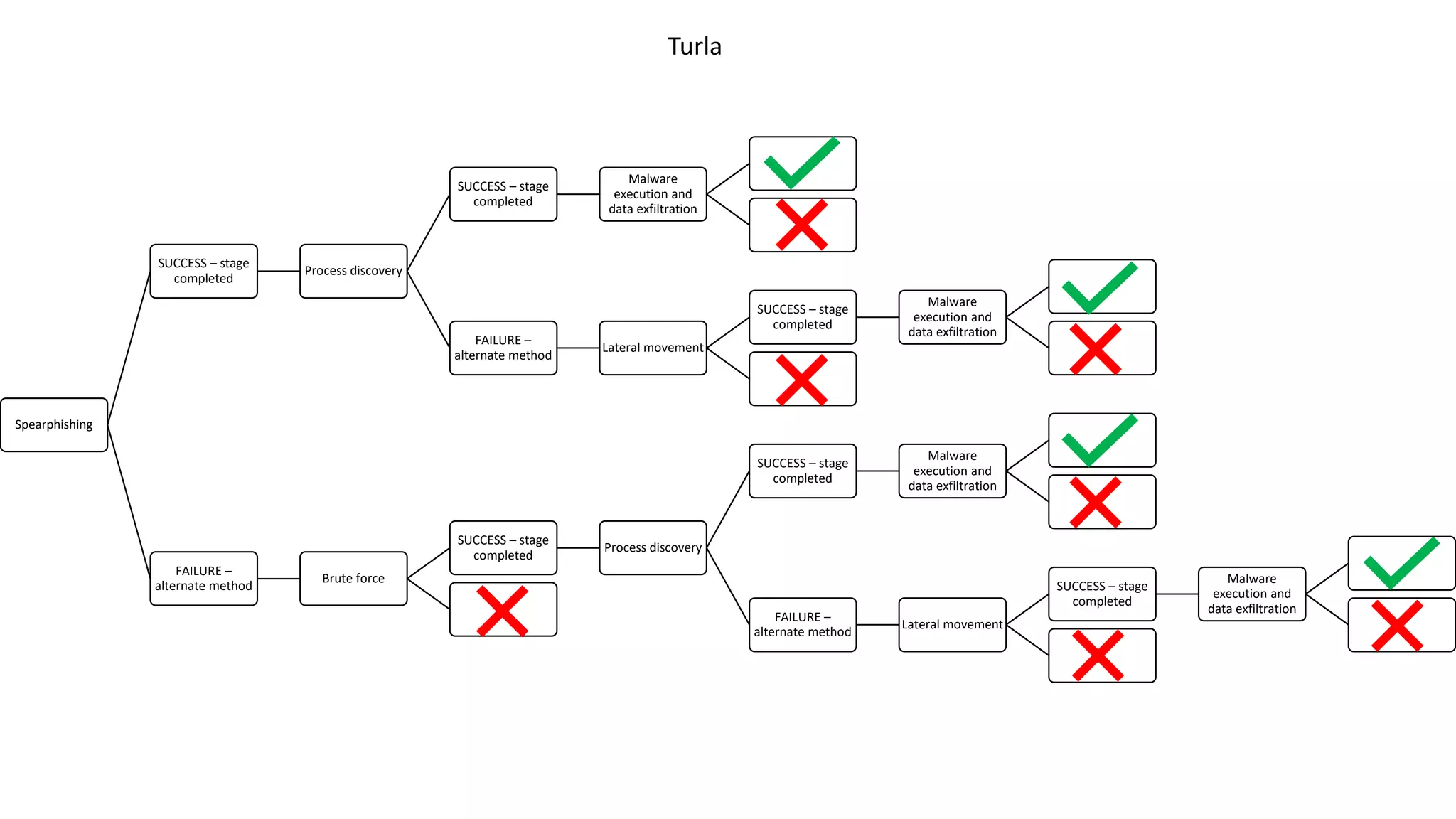
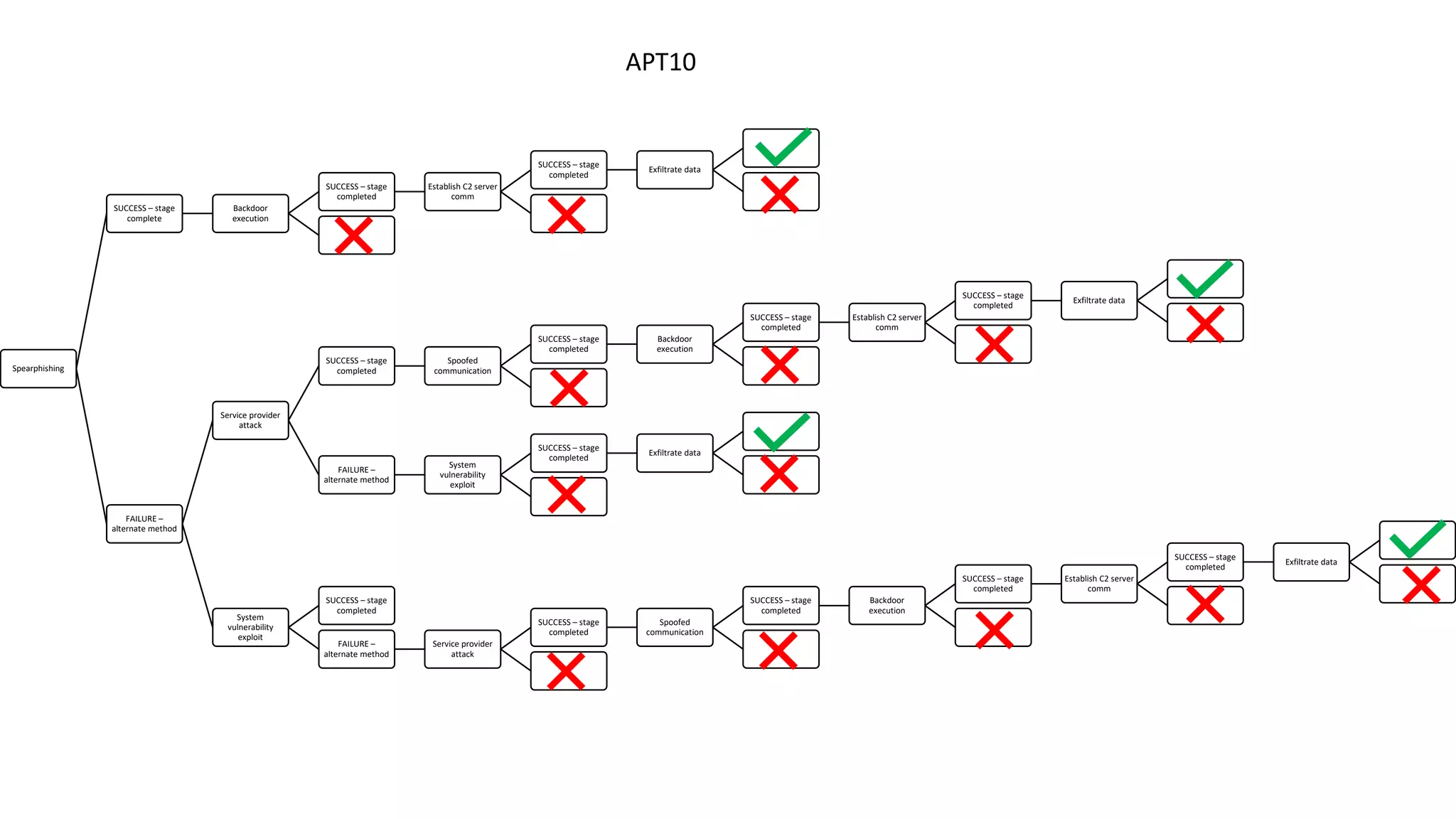
The document discusses decision analysis applications within threat analysis frameworks, focusing on identifying top threats and understanding attack methods through a decision tree. It highlights the success and failure stages of various attacks including spearphishing, malware execution, and service provider attacks, while emphasizing that the framework aids in the prioritization of mitigations and personalization of corporate policy. The presentation concludes by encouraging future directions and inquiries related to the framework's implementation.