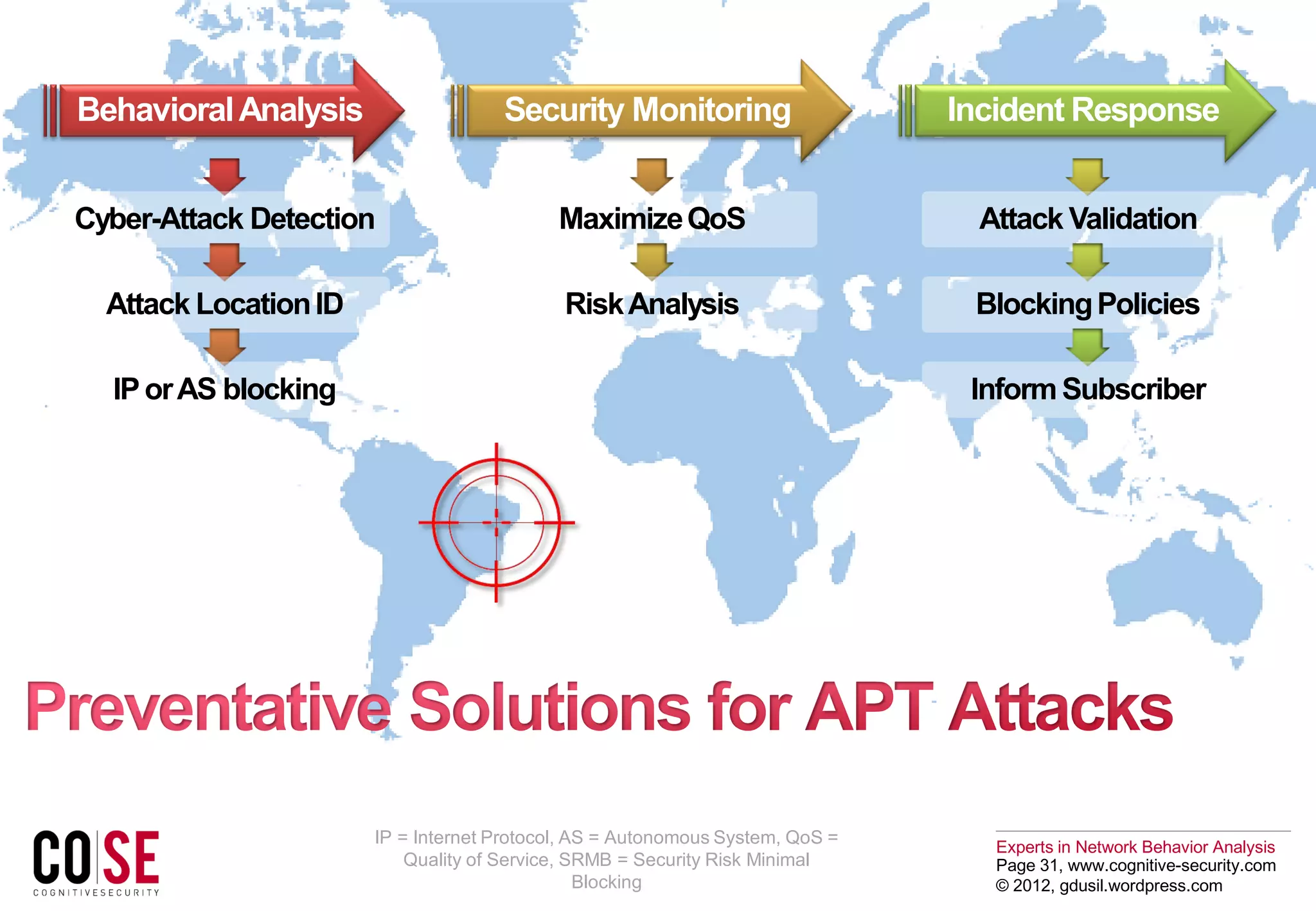
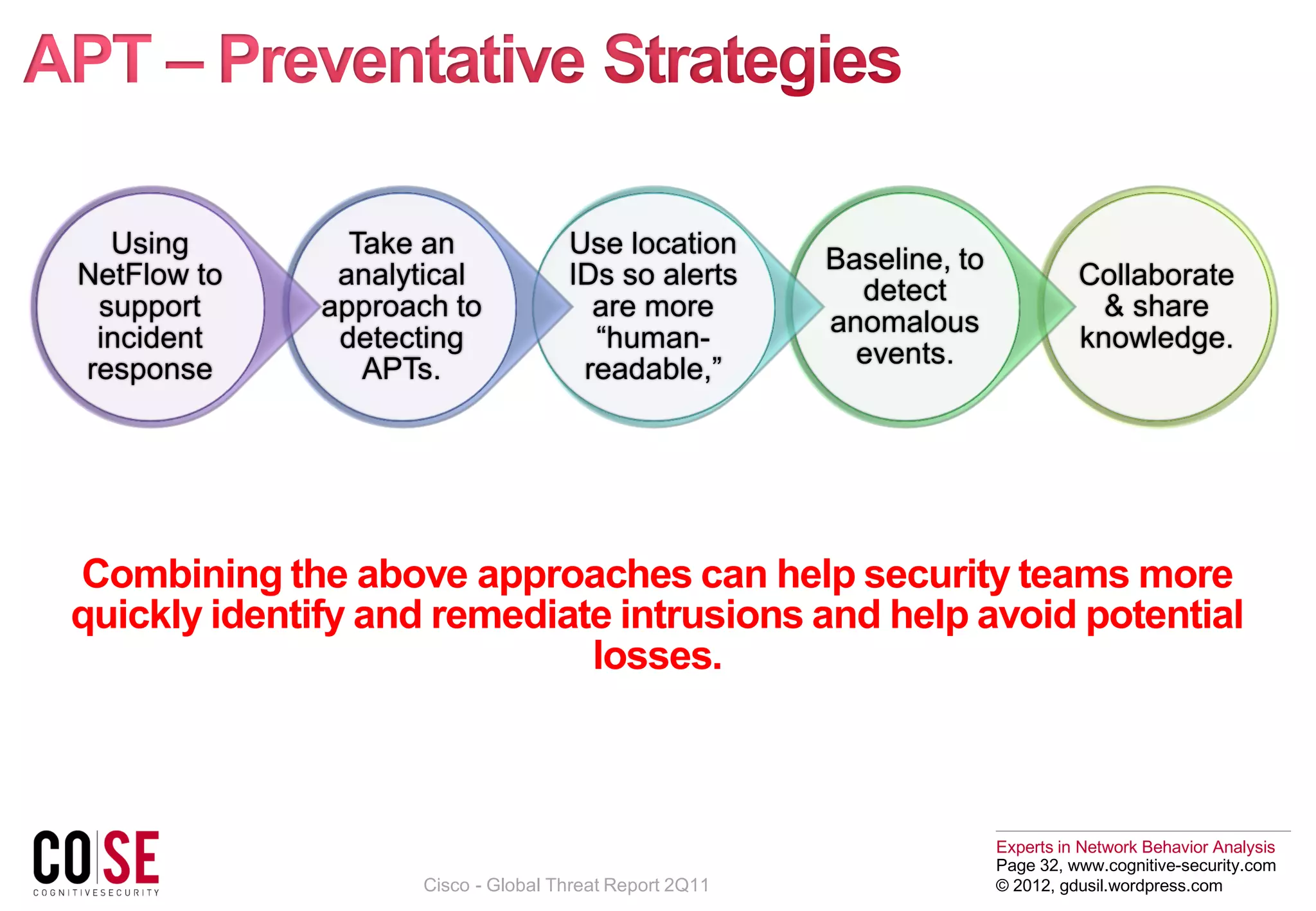
The document discusses the evolution of cyber threats, particularly focusing on advanced persistent threats (APTs) which use strategic approaches and sophisticated techniques to compromise networks. It emphasizes the need for robust security measures, such as network behavior analysis, to detect and mitigate these threats effectively. Additionally, it highlights challenges organizations face in integrating security protocols and the importance of protecting critical infrastructures and sensitive data from increasingly complex cyber attacks.


![Experts in Network Behavior Analysis
Page 14, www.cognitive-security.com
© 2012, gdusil.wordpress.com
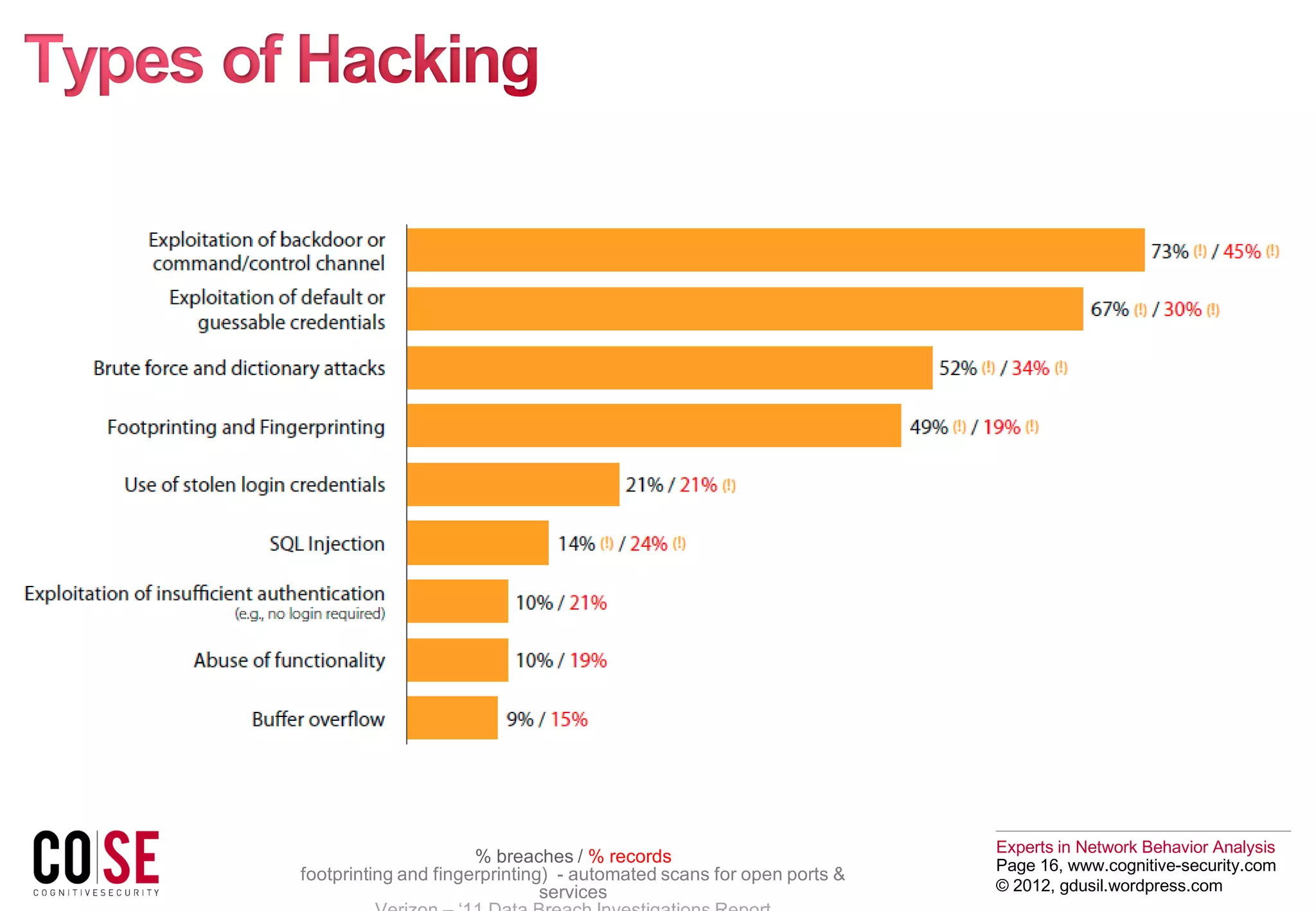
“[Hacking] Breaches… …can be because
they may contain sensitive data on clients as well as employees that even an
average attacker can sell on the underground economy.”
Source: OSF DataLoss DB,
Symantec – Internet Security Threat Report ‘11.Apr](https://image.slidesharecdn.com/portfolio-cognitivesecurityanatomyofadvancedpersistentthreats12-130605034056-phpapp01/75/Cognitive-Security-Anatomy-of-Advanced-Persistent-Threats-12-14-2048.jpg)