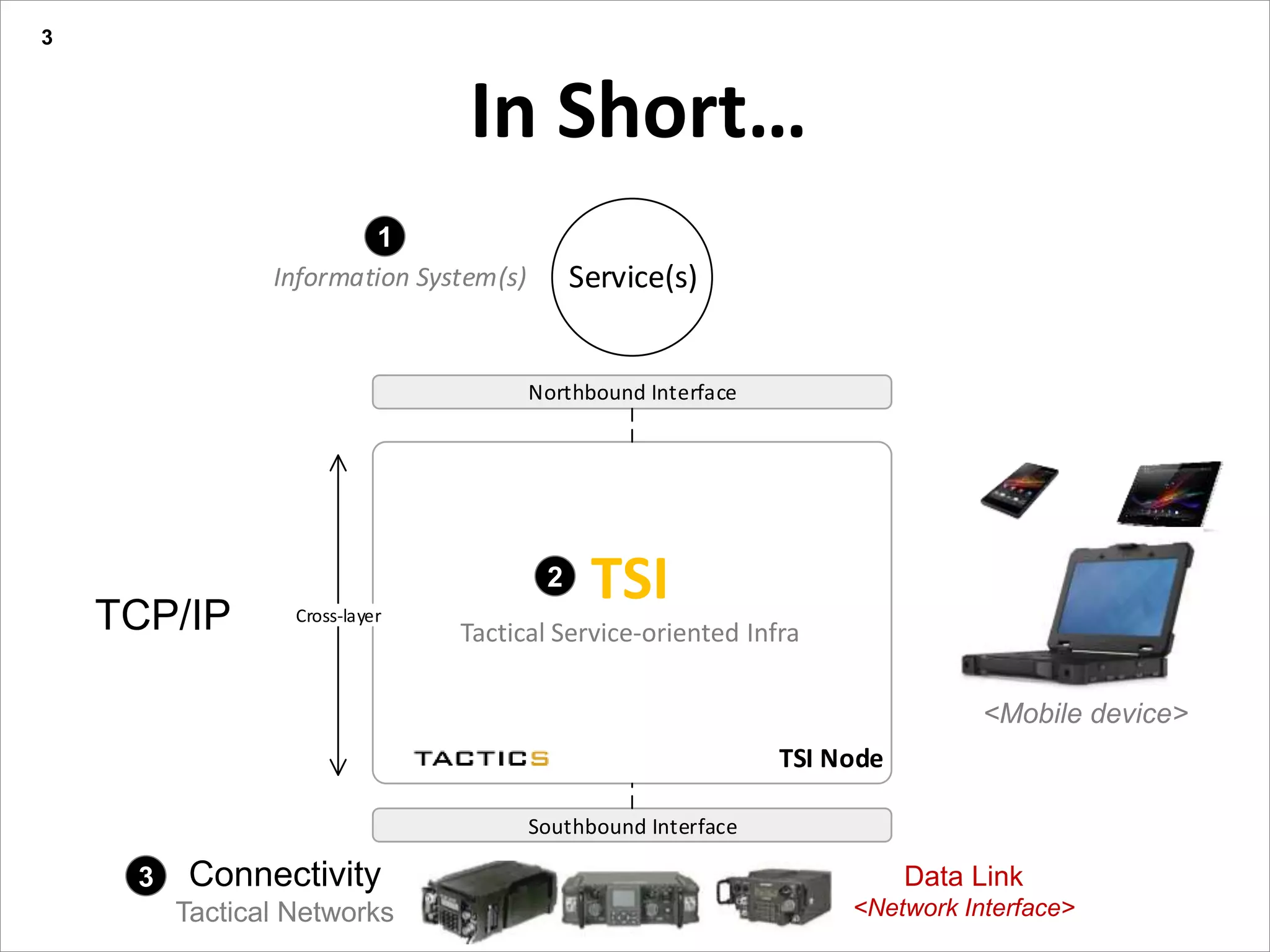
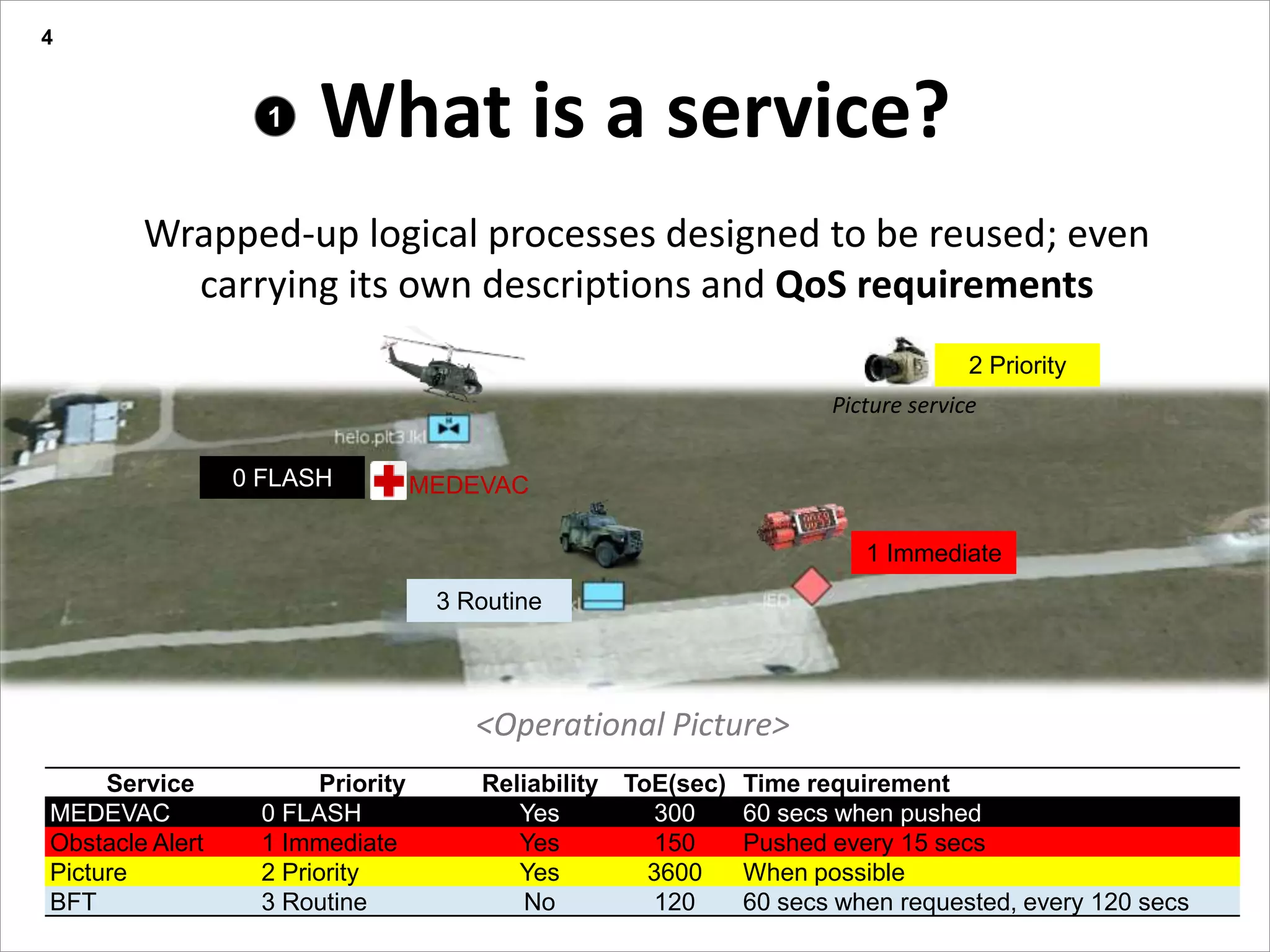
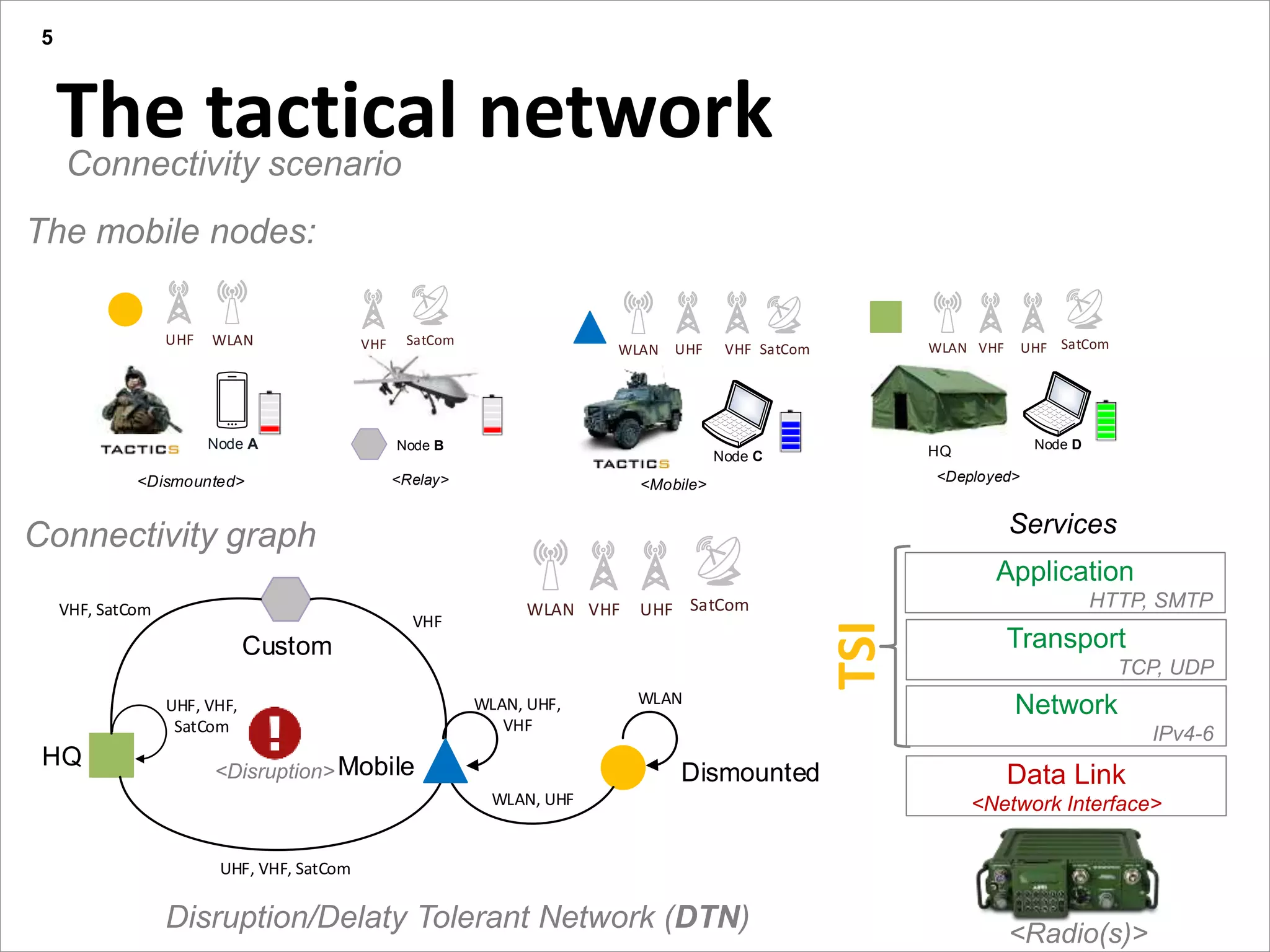
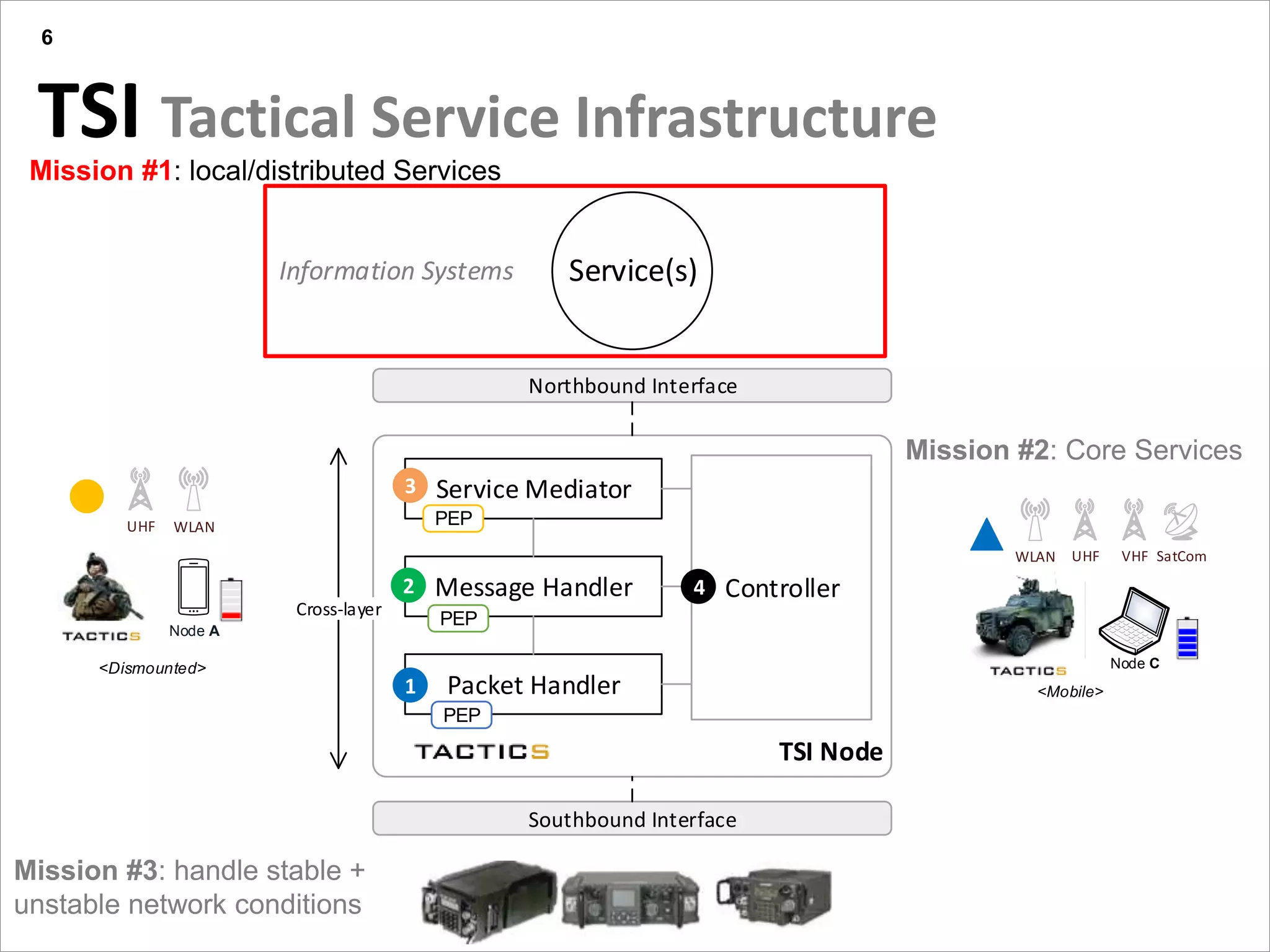
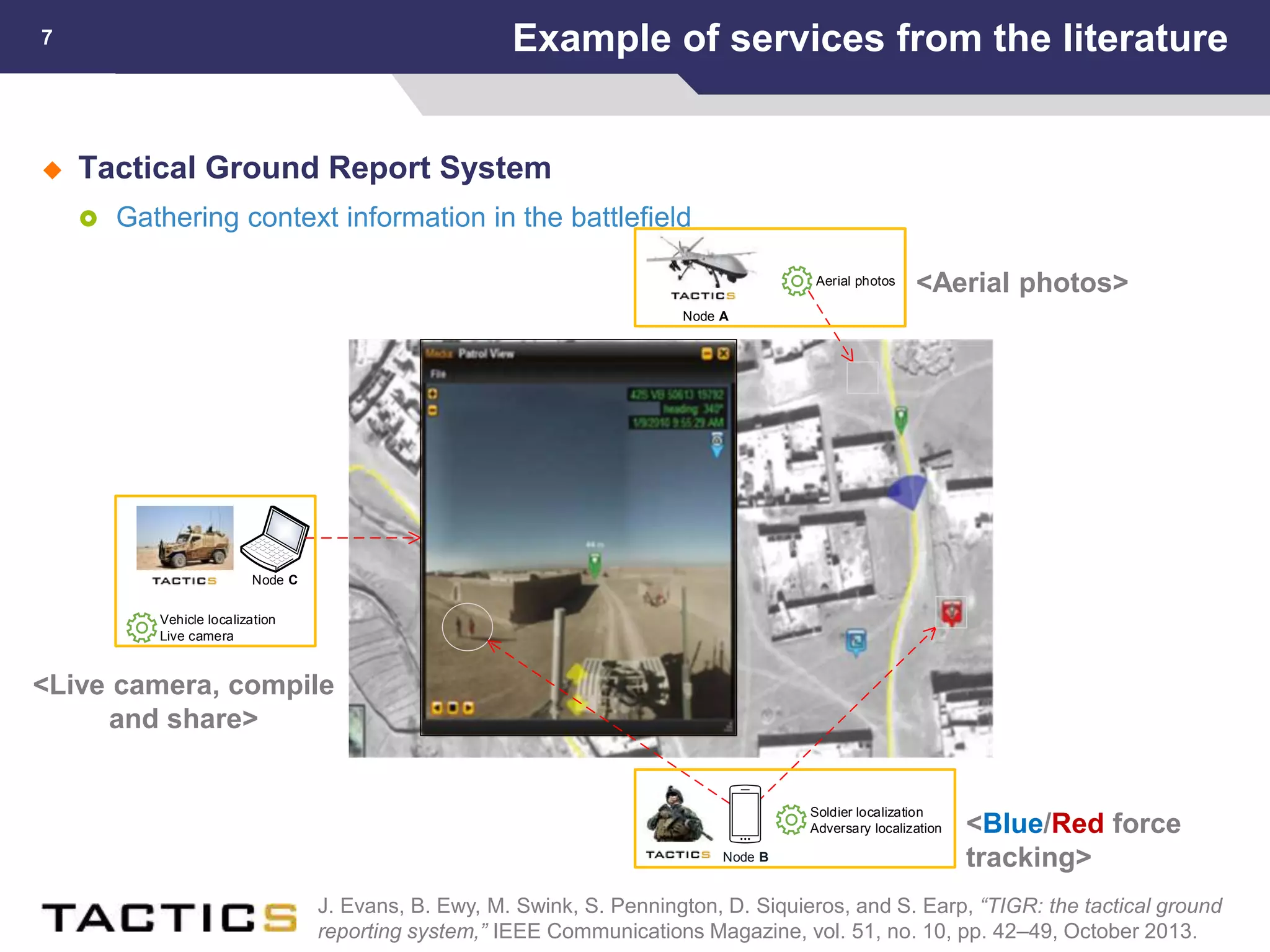
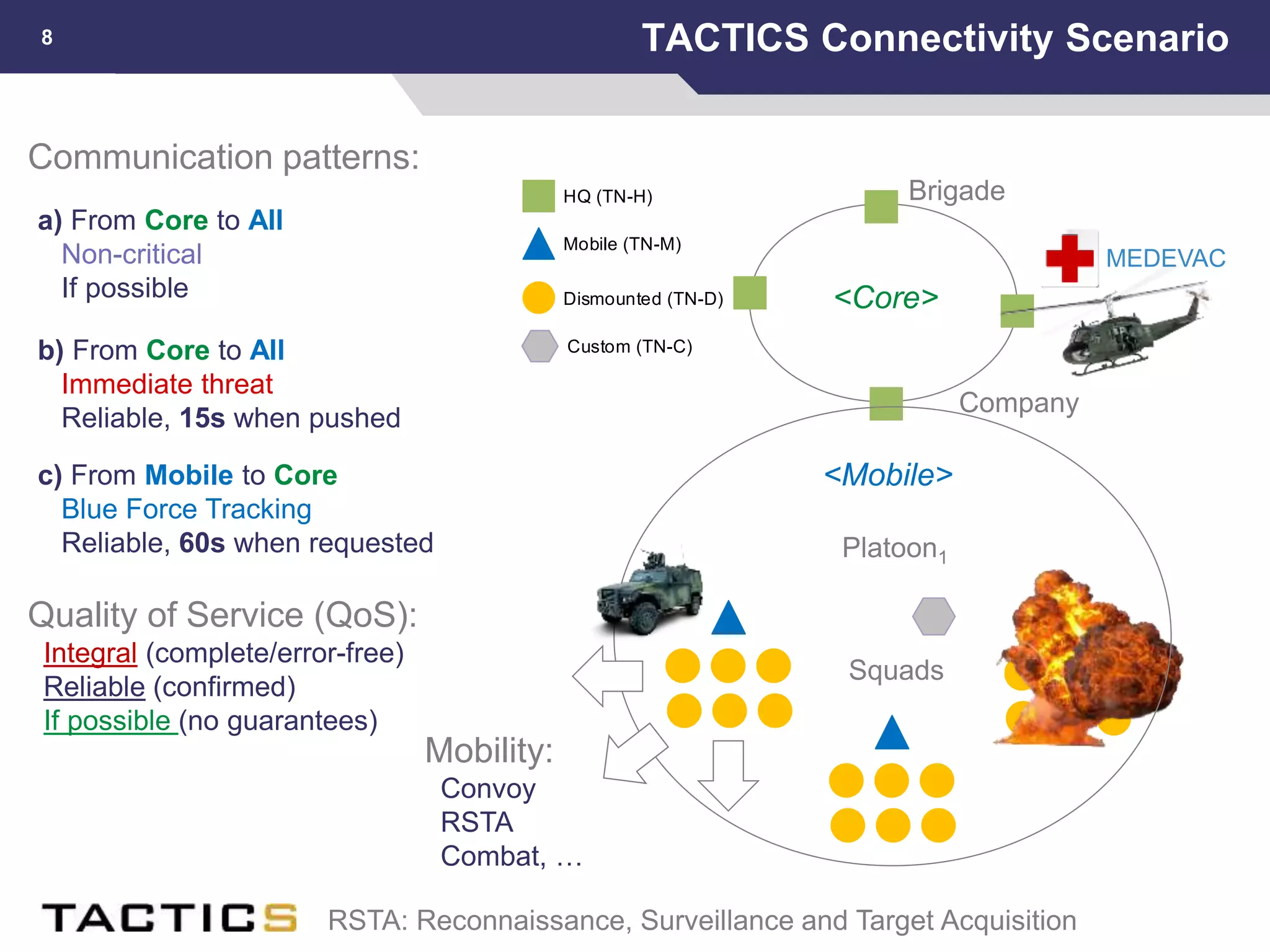
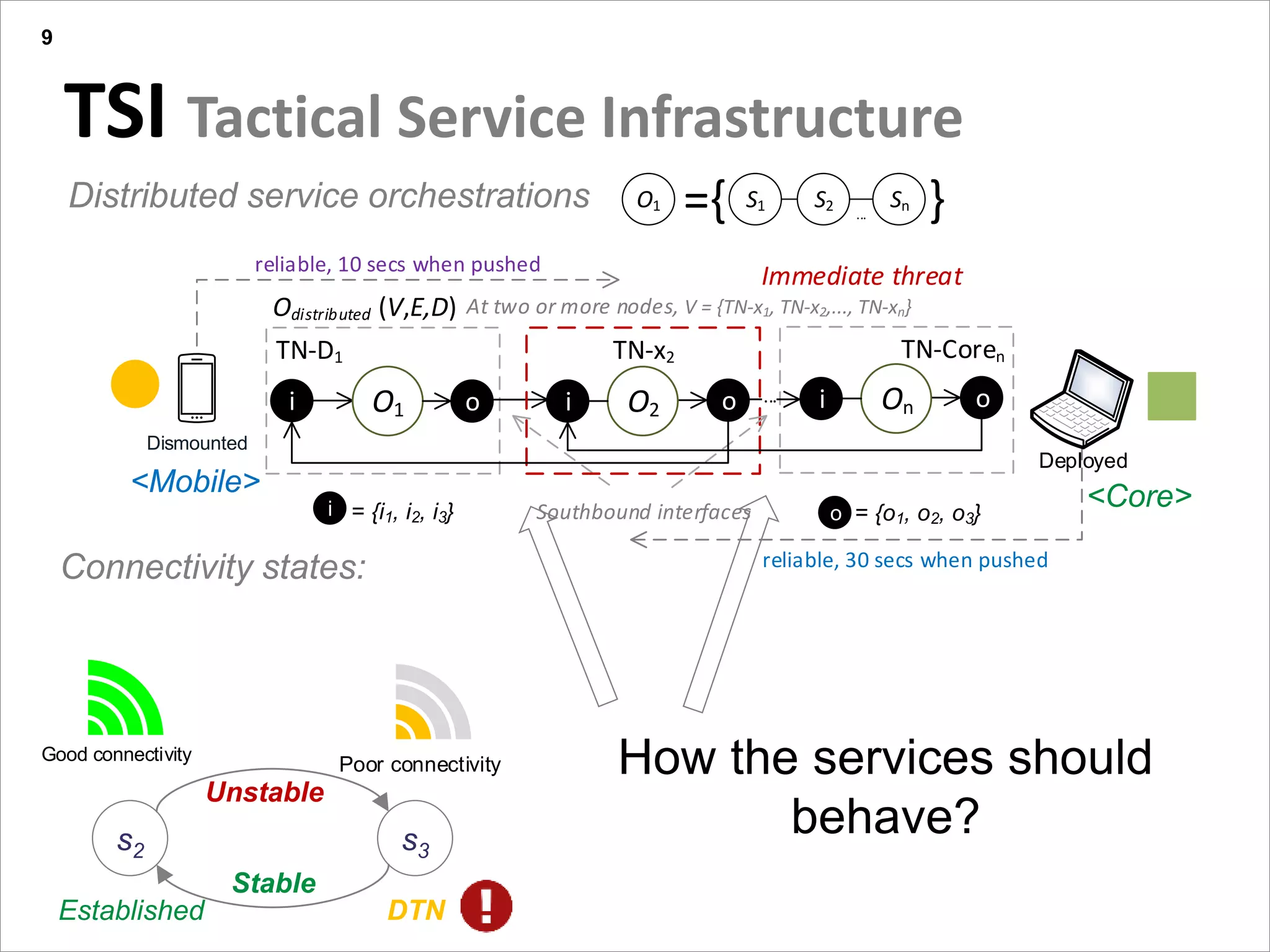
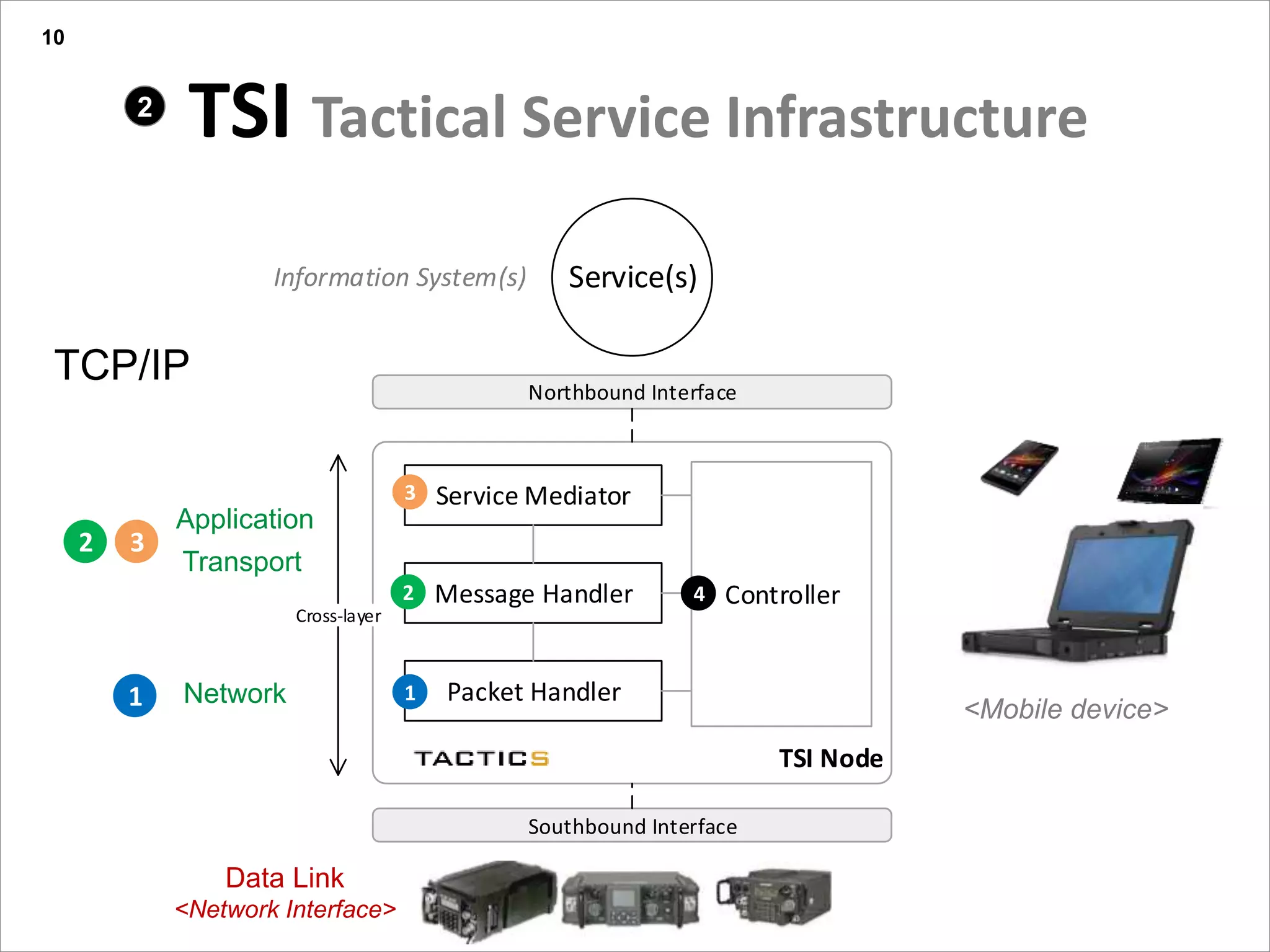
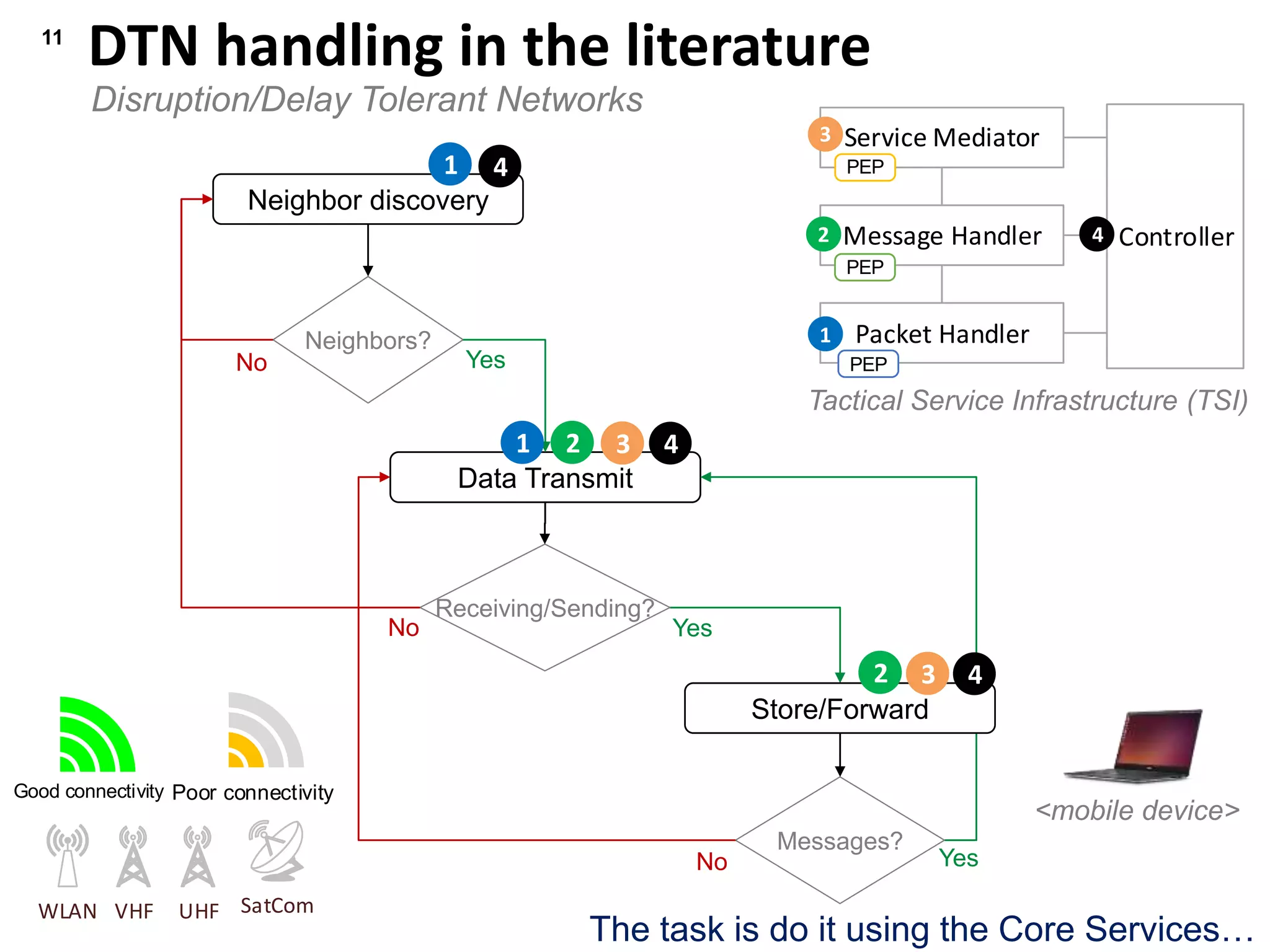
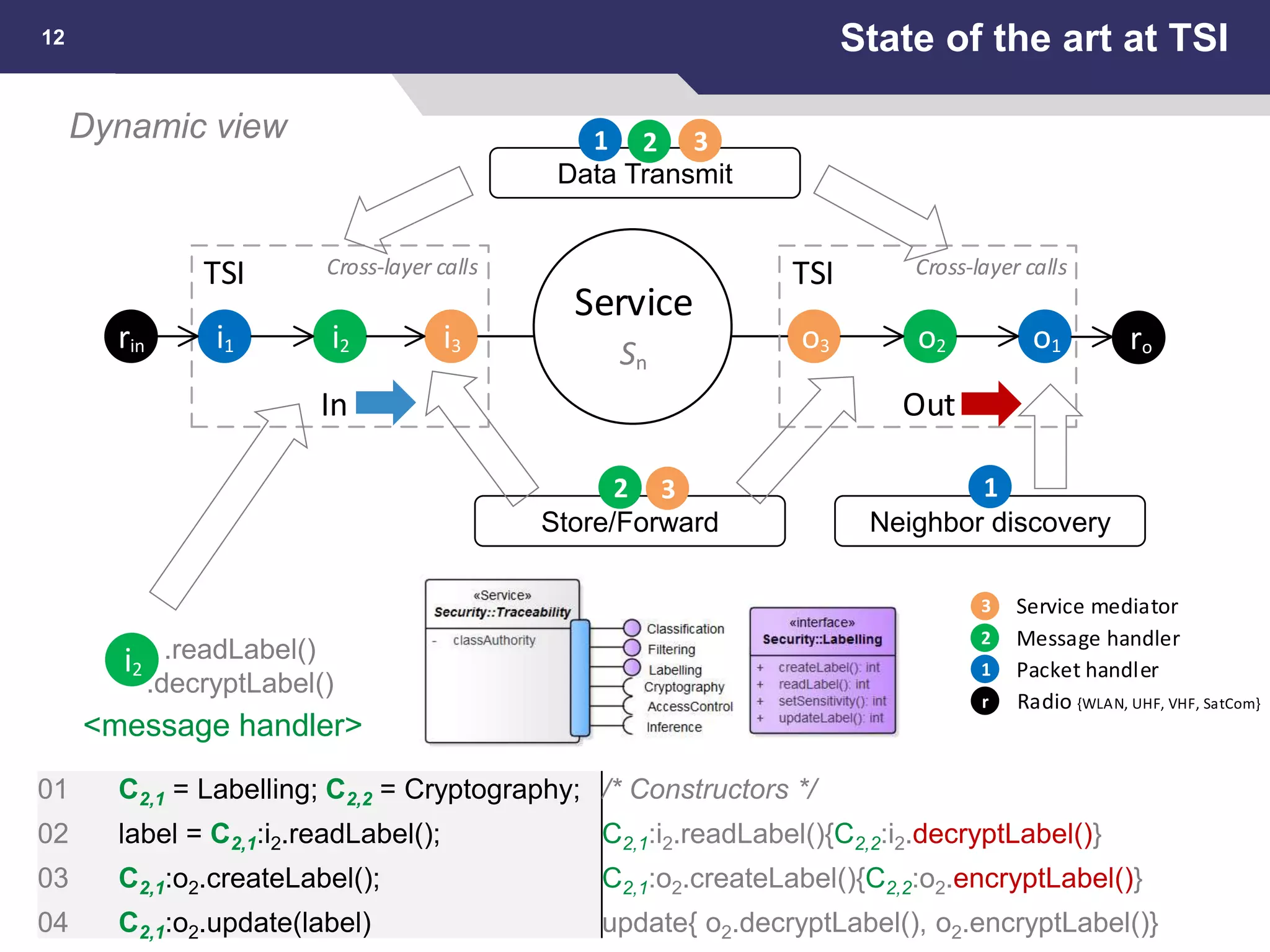
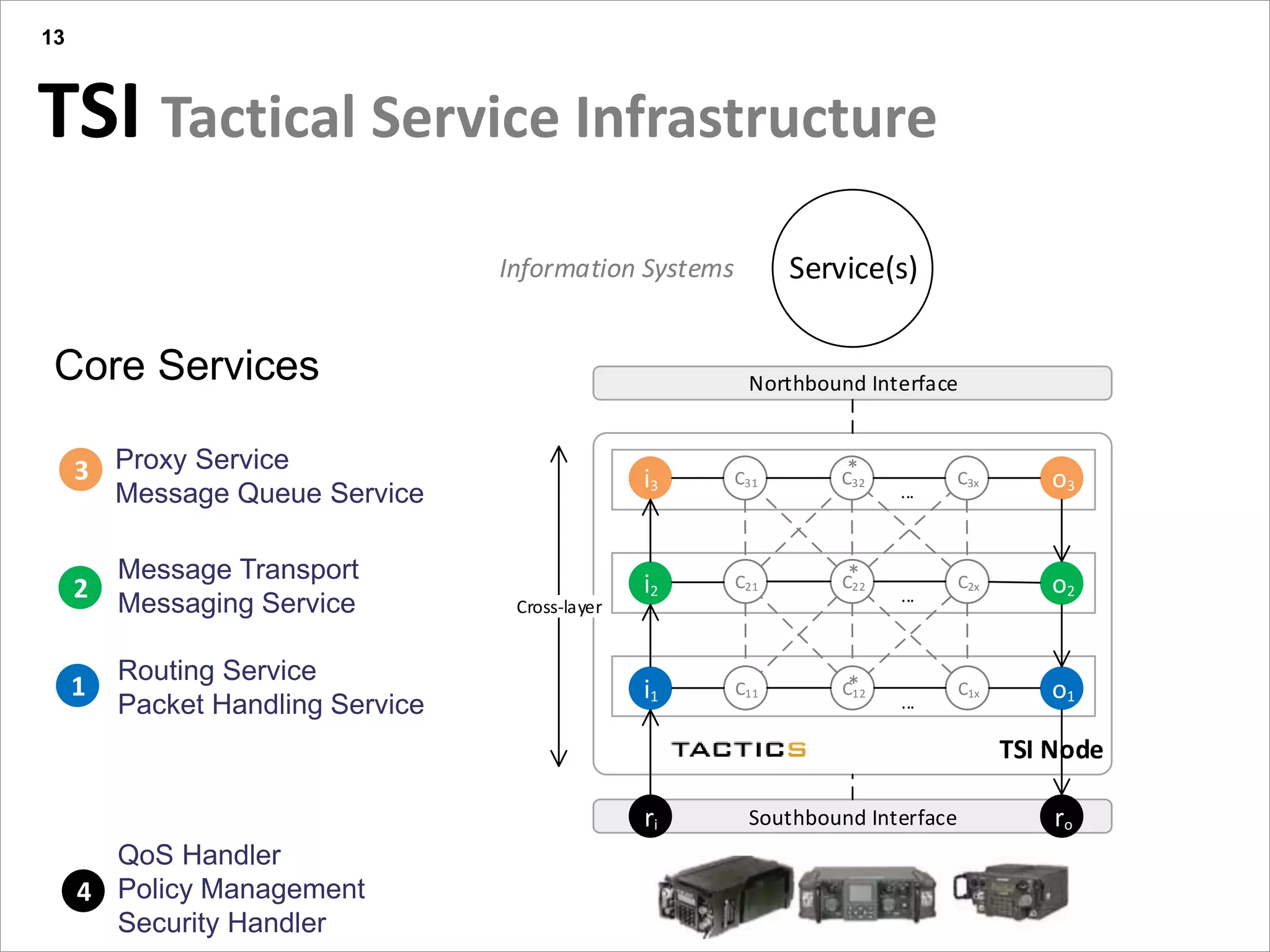
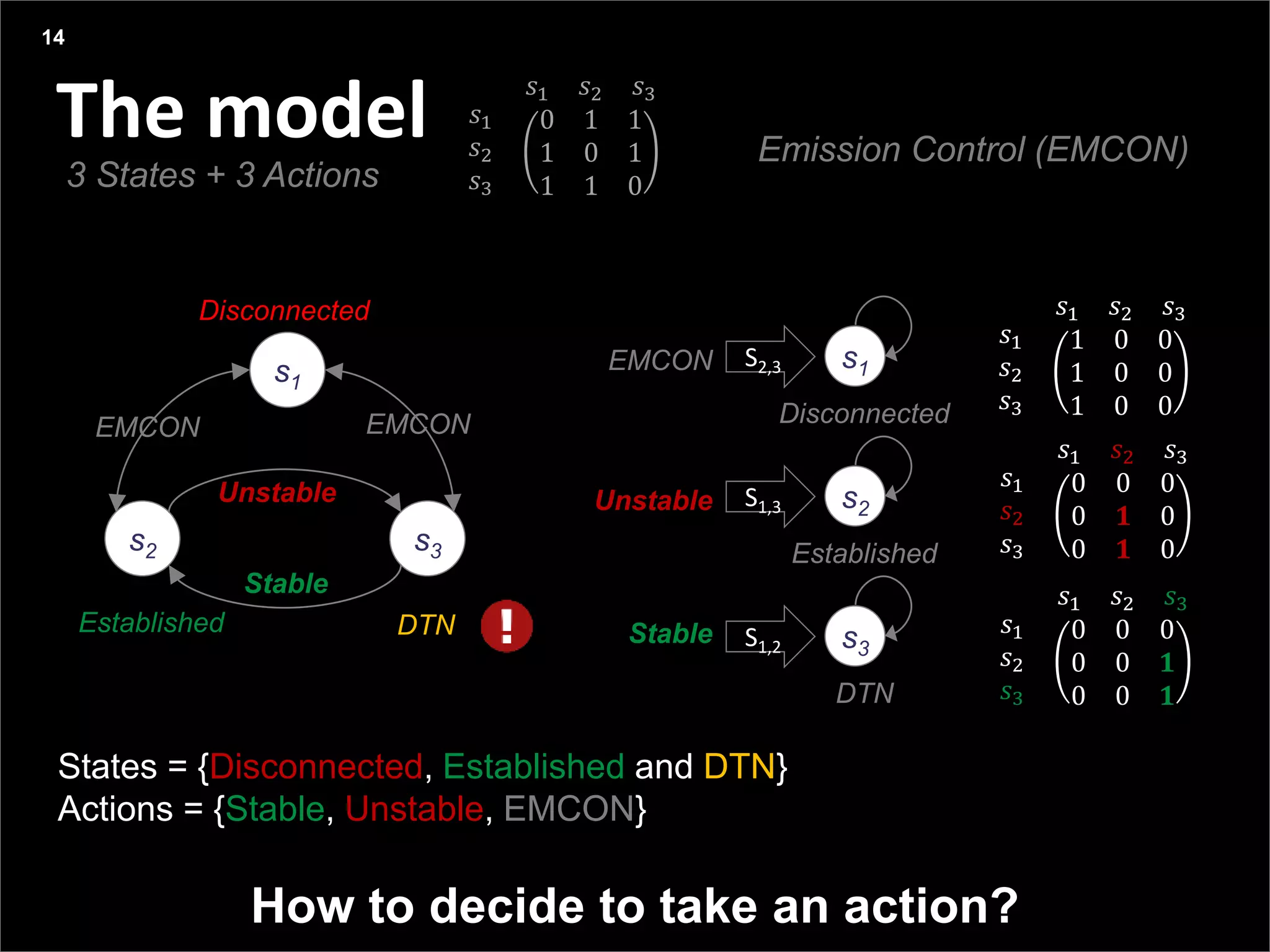
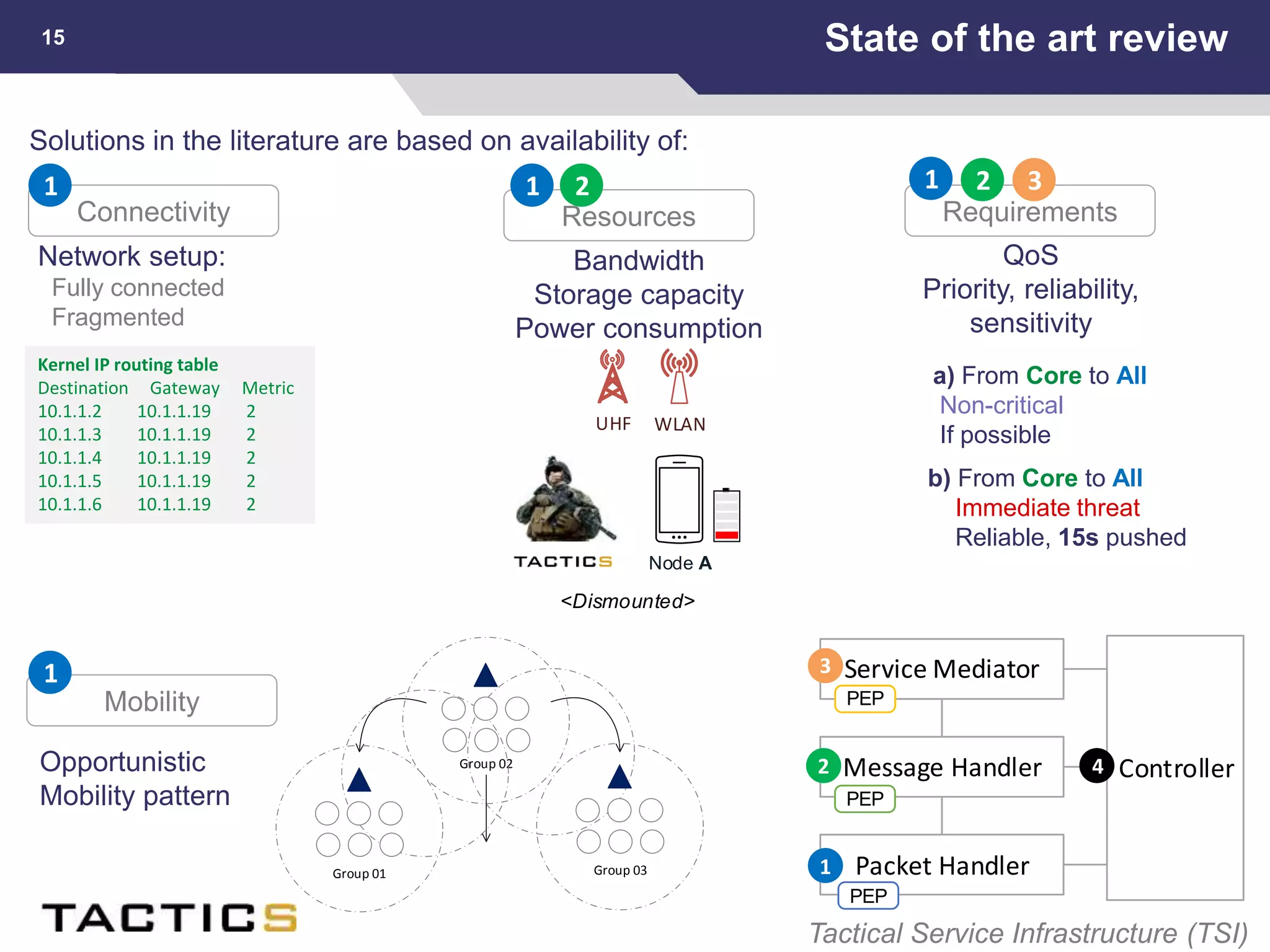
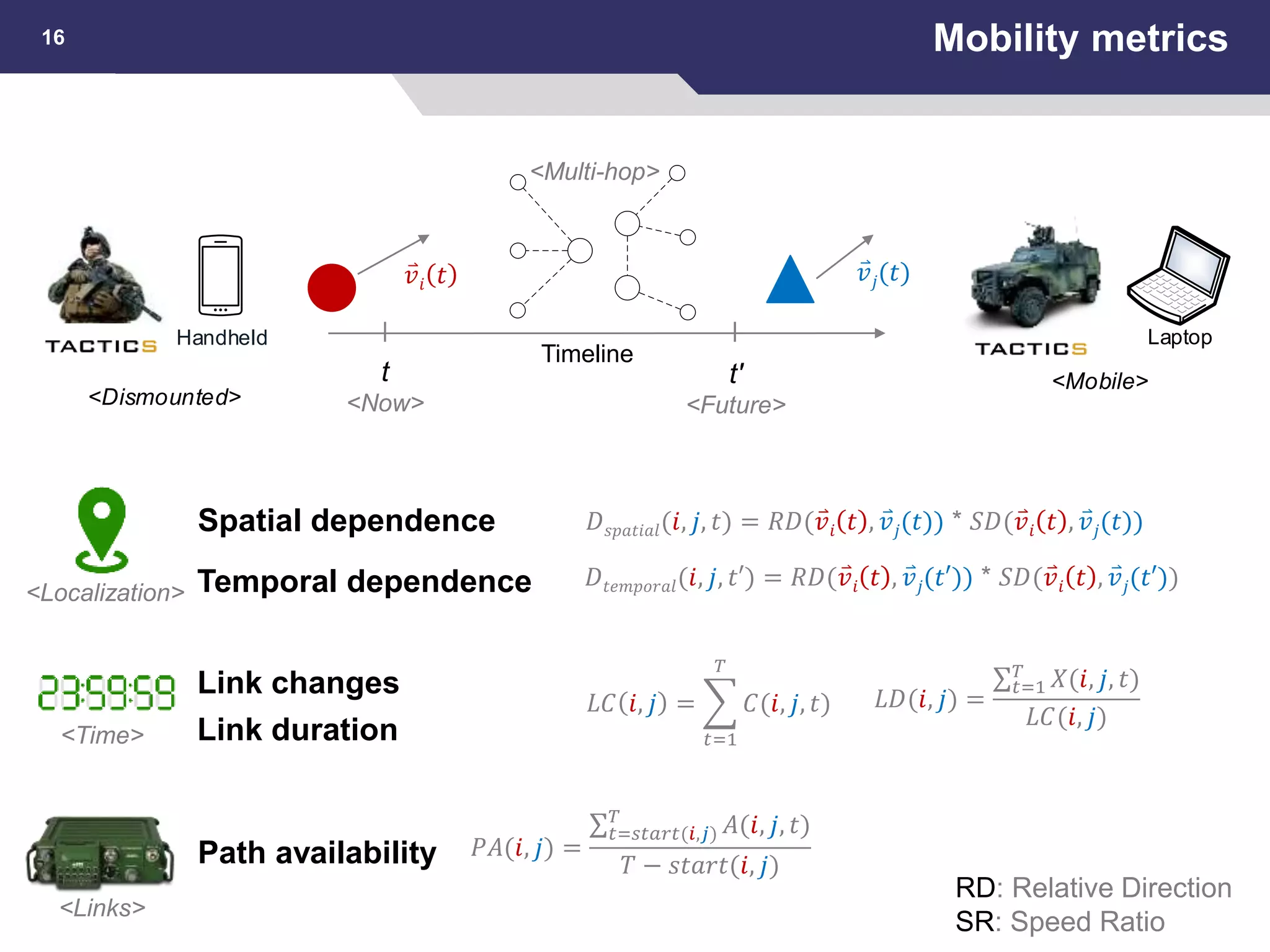
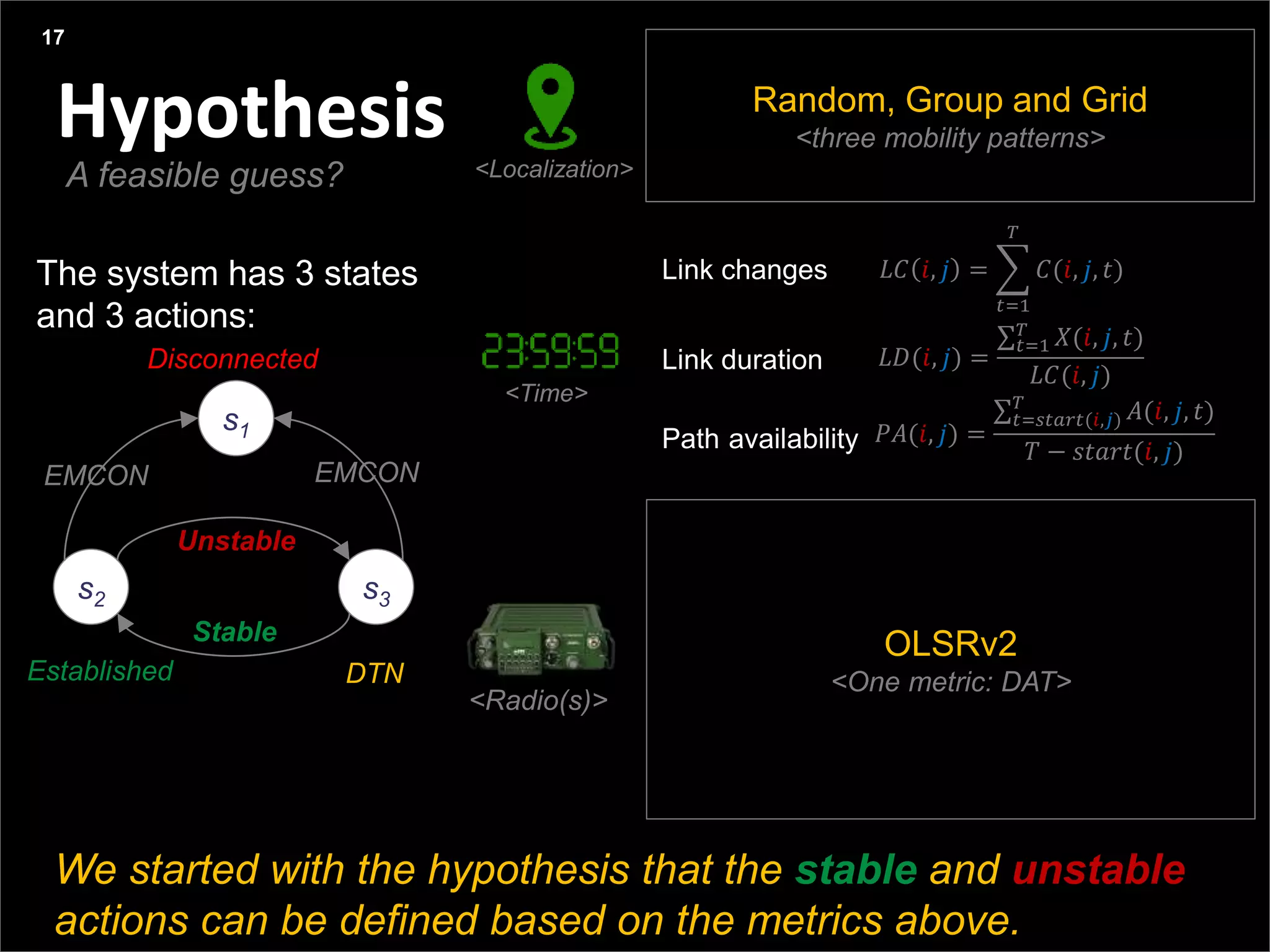
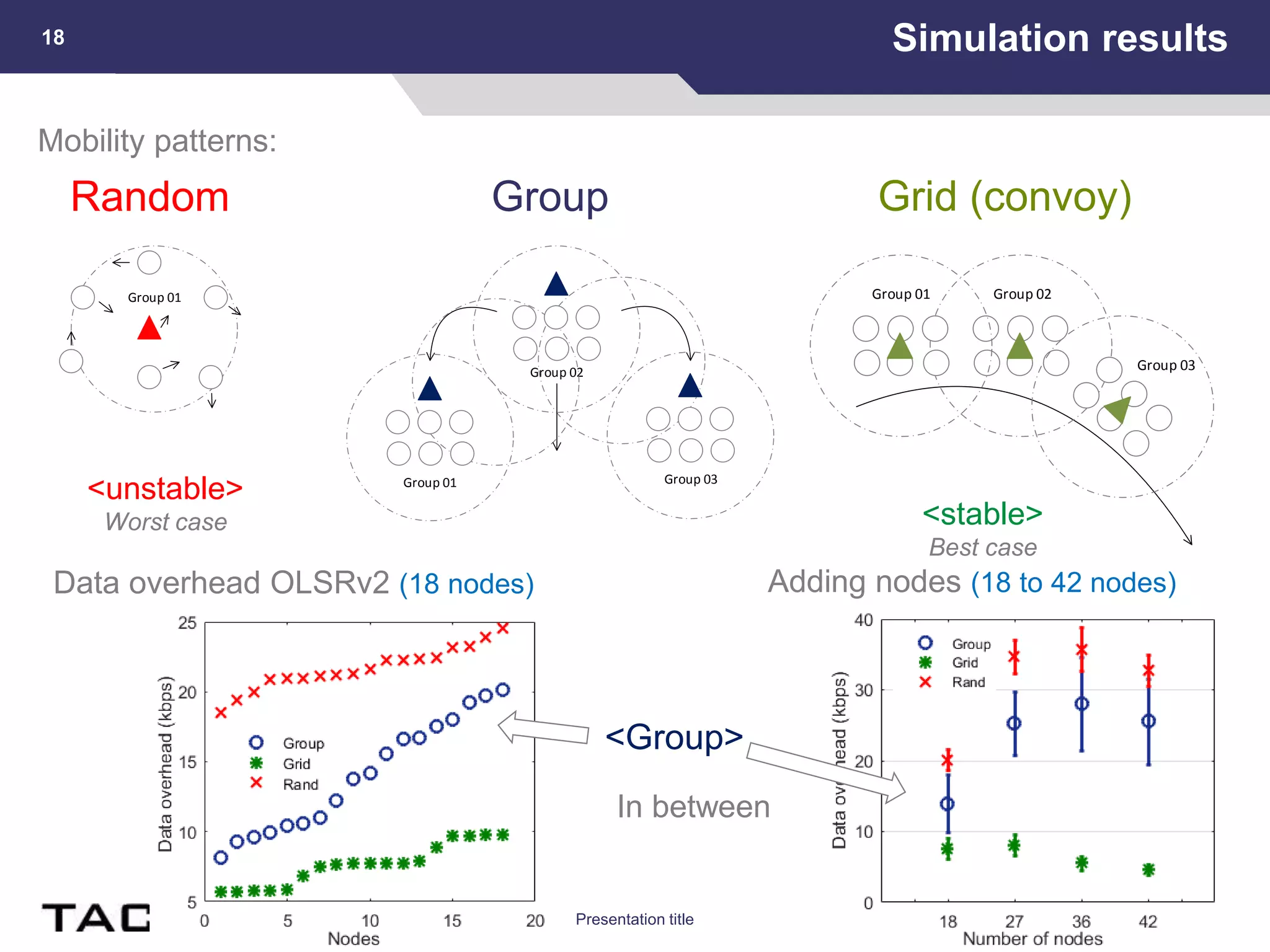
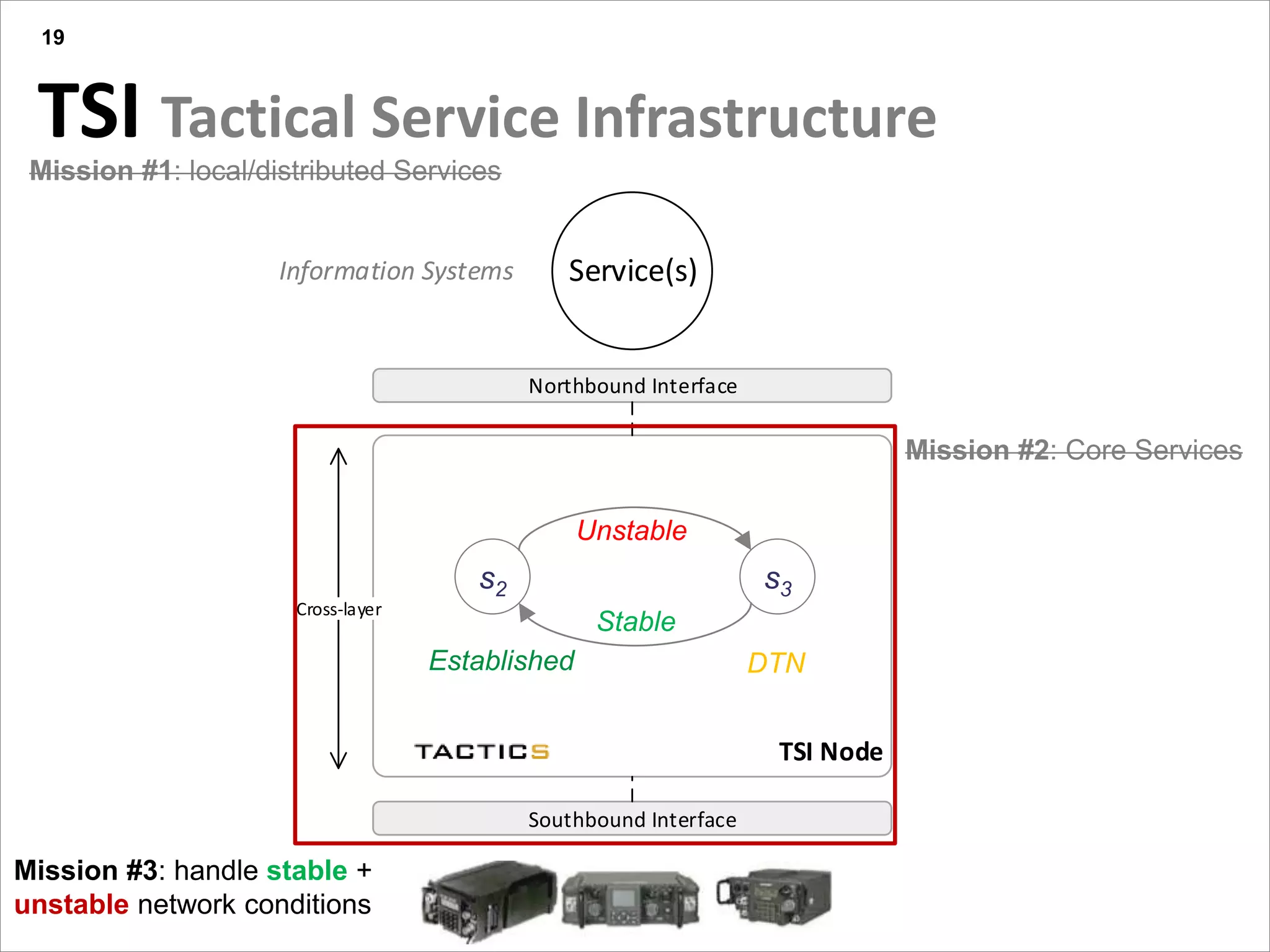
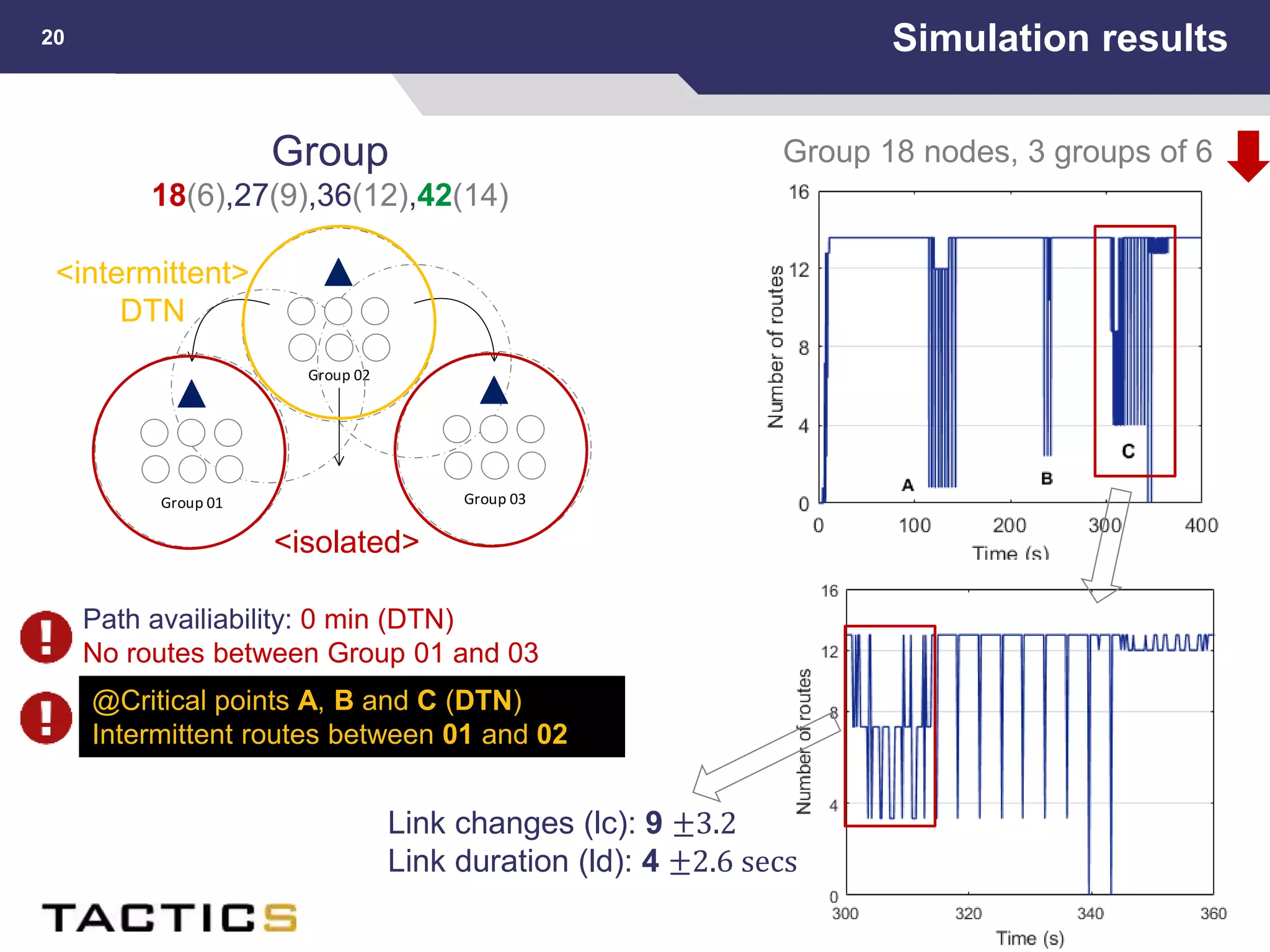
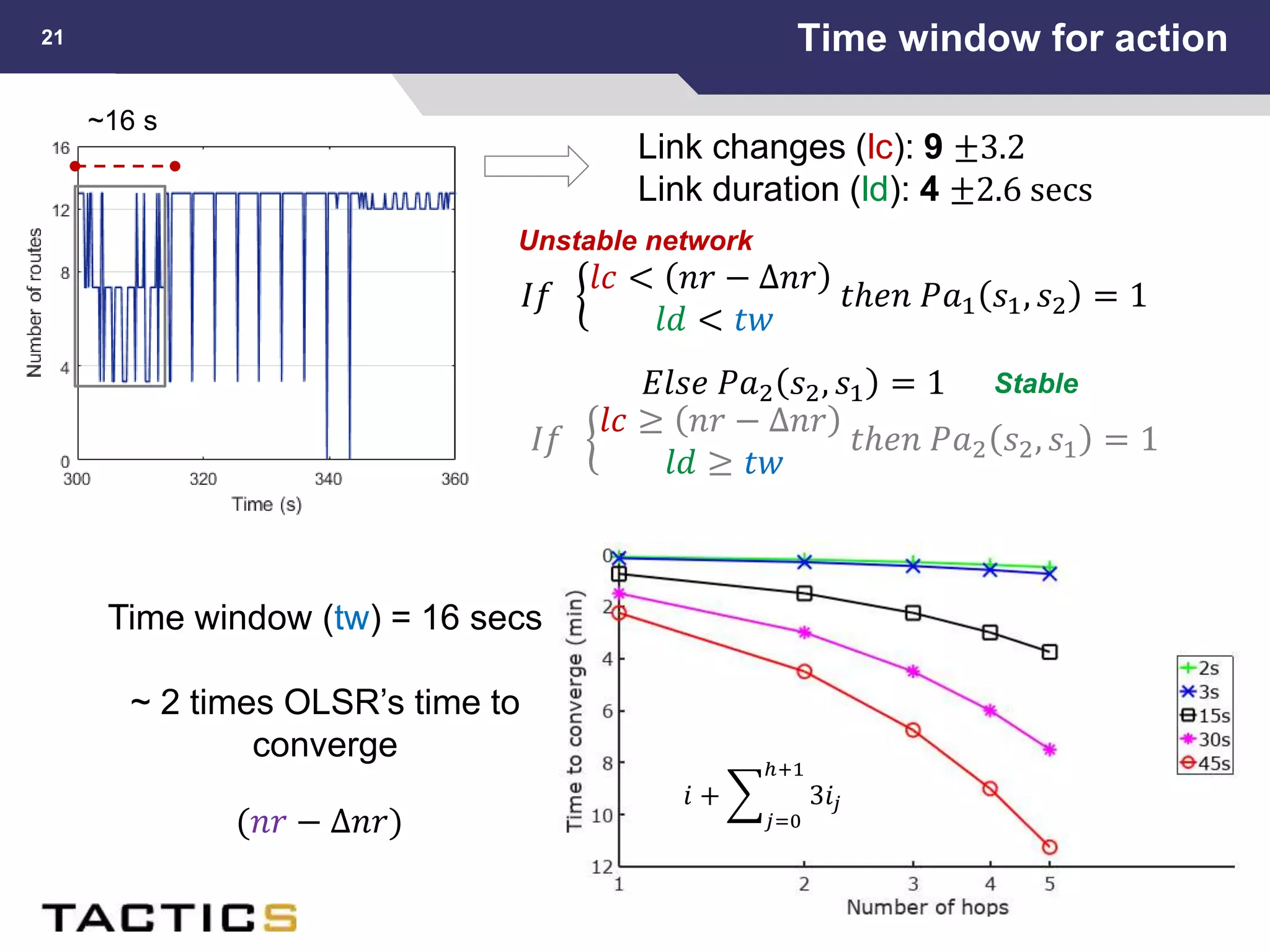
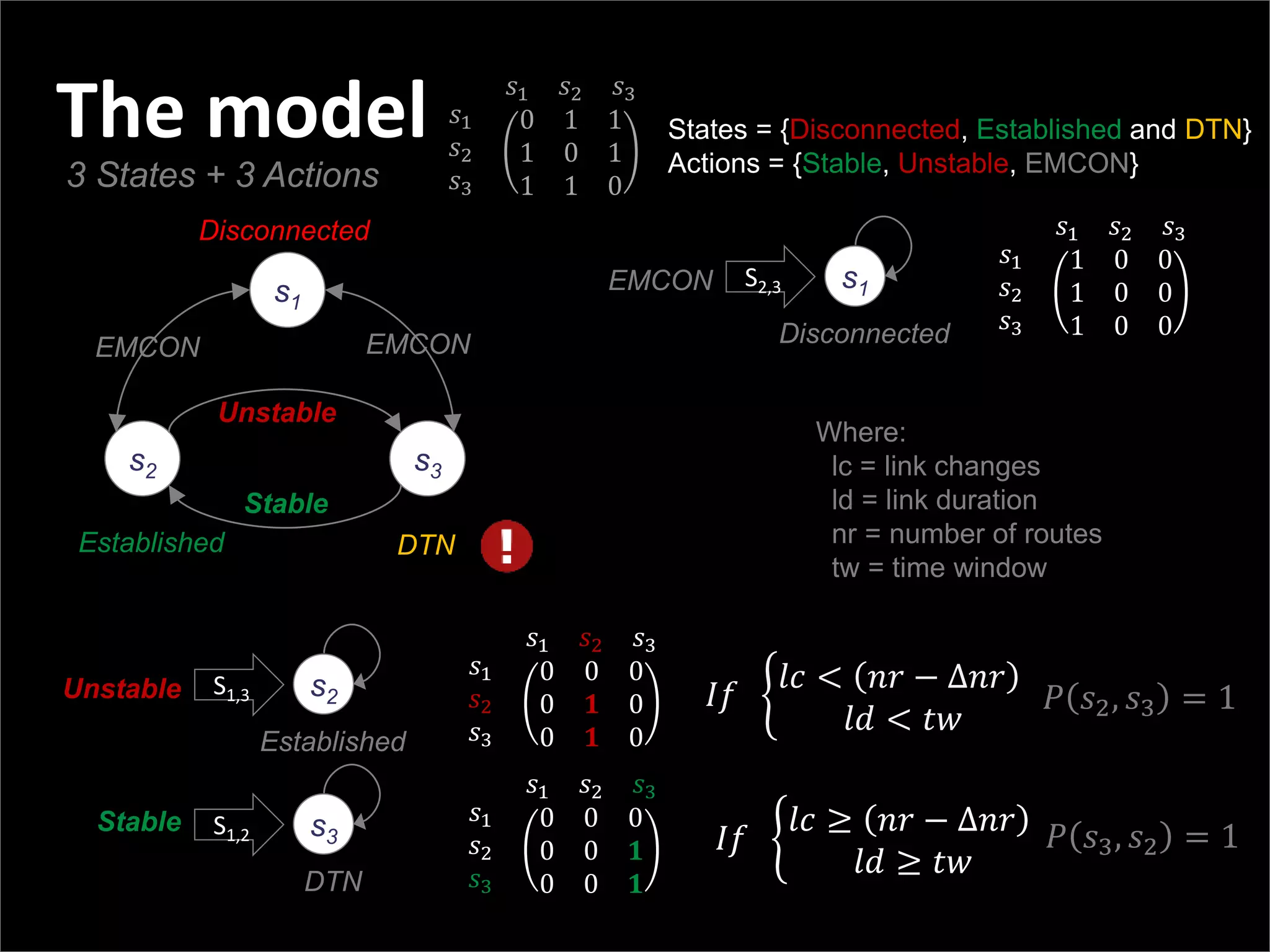
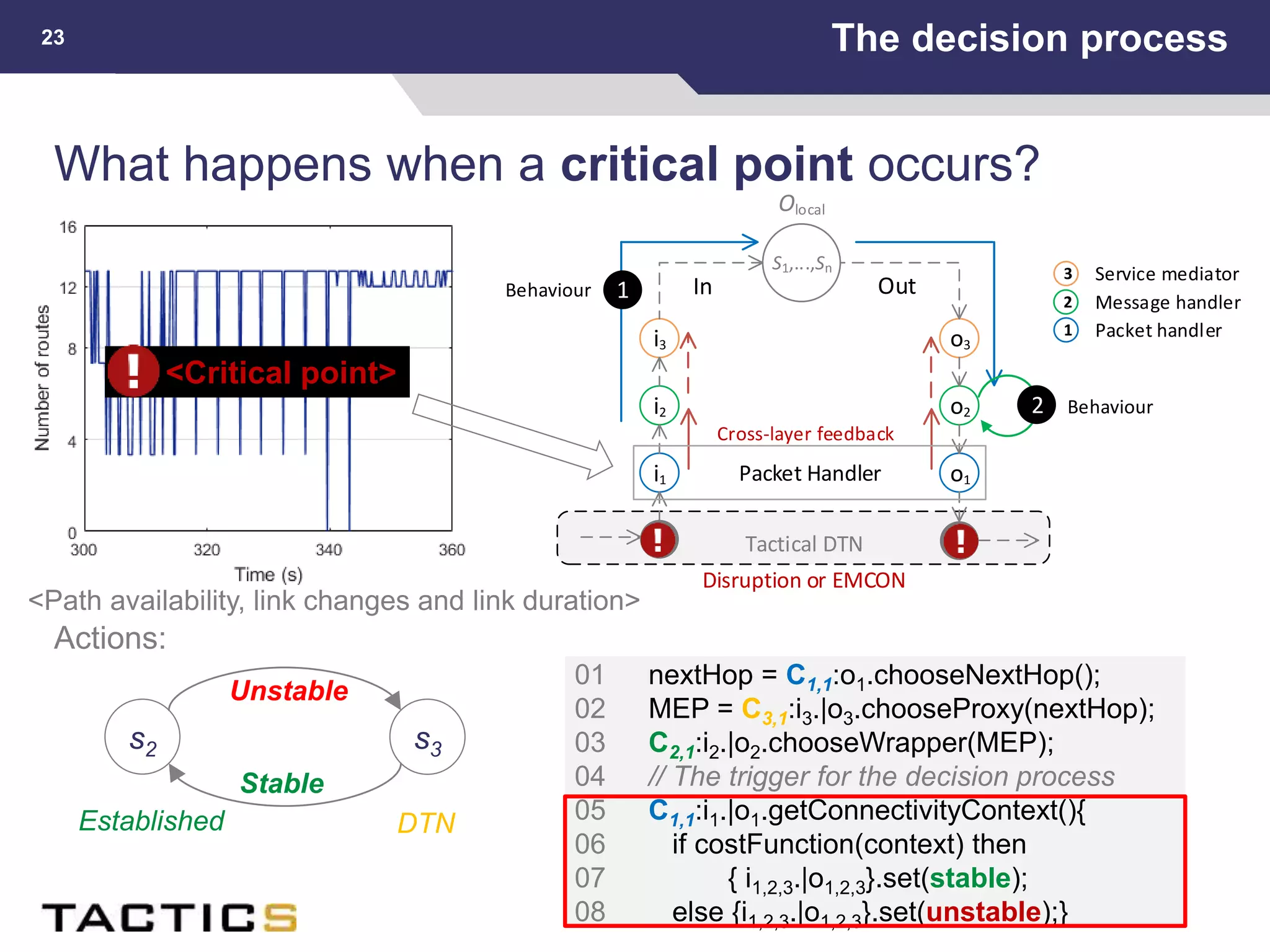
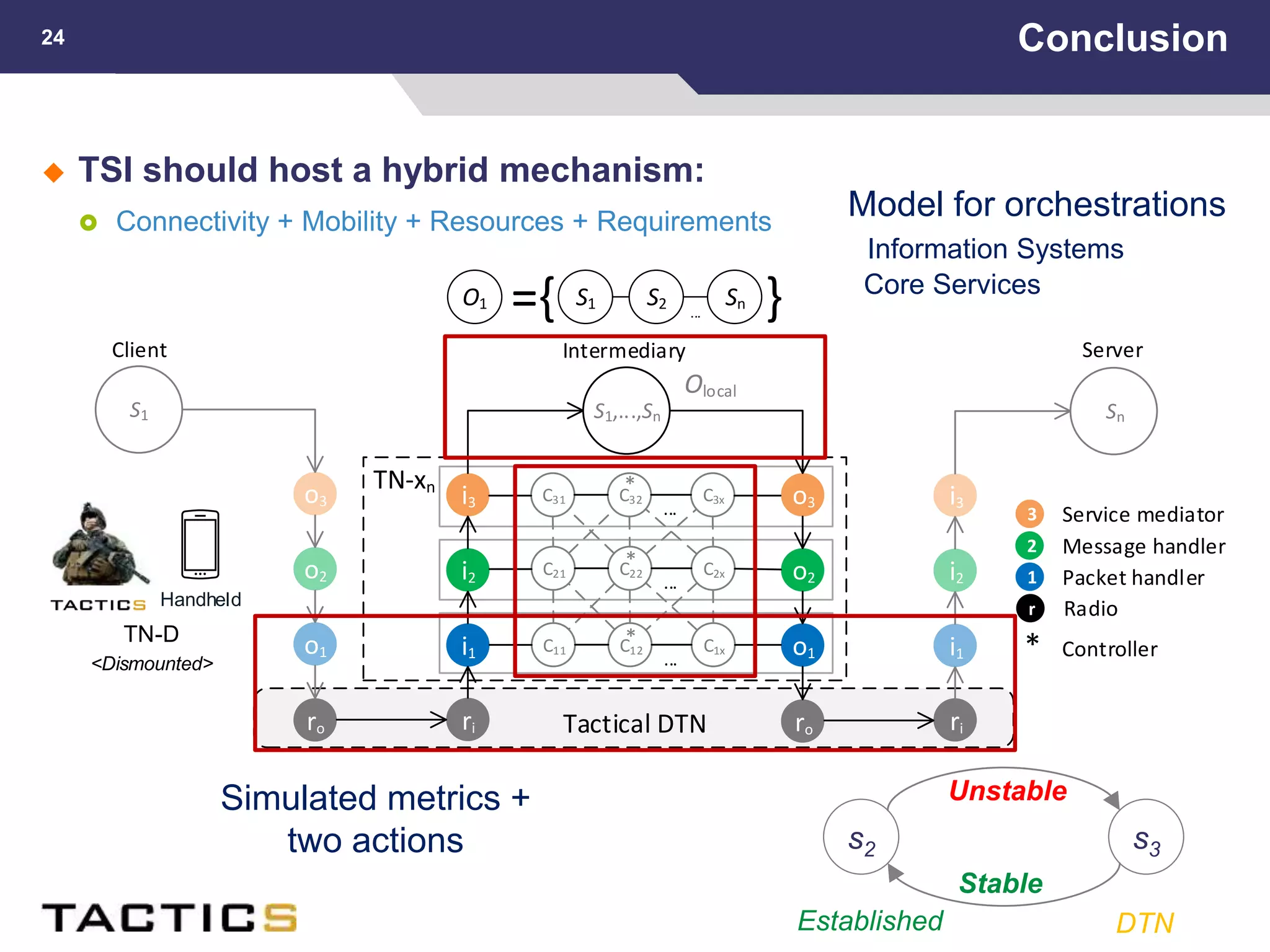
This document summarizes a presentation on reactive and proactive connectivity management in a tactical service-oriented infrastructure. The presentation covers three main topics: 1) introducing a scenario and quality of service requirements for tactical networks, 2) describing a service-oriented model and connectivity management approach, and 3) presenting quantitative analysis results from simulating different mobility patterns and network sizes. The goal of the research is to develop an architecture called Tactical Service Infrastructure (TSI) that can manage connectivity challenges in tactical networks by handling both stable and unstable network conditions through distributed services and core services.