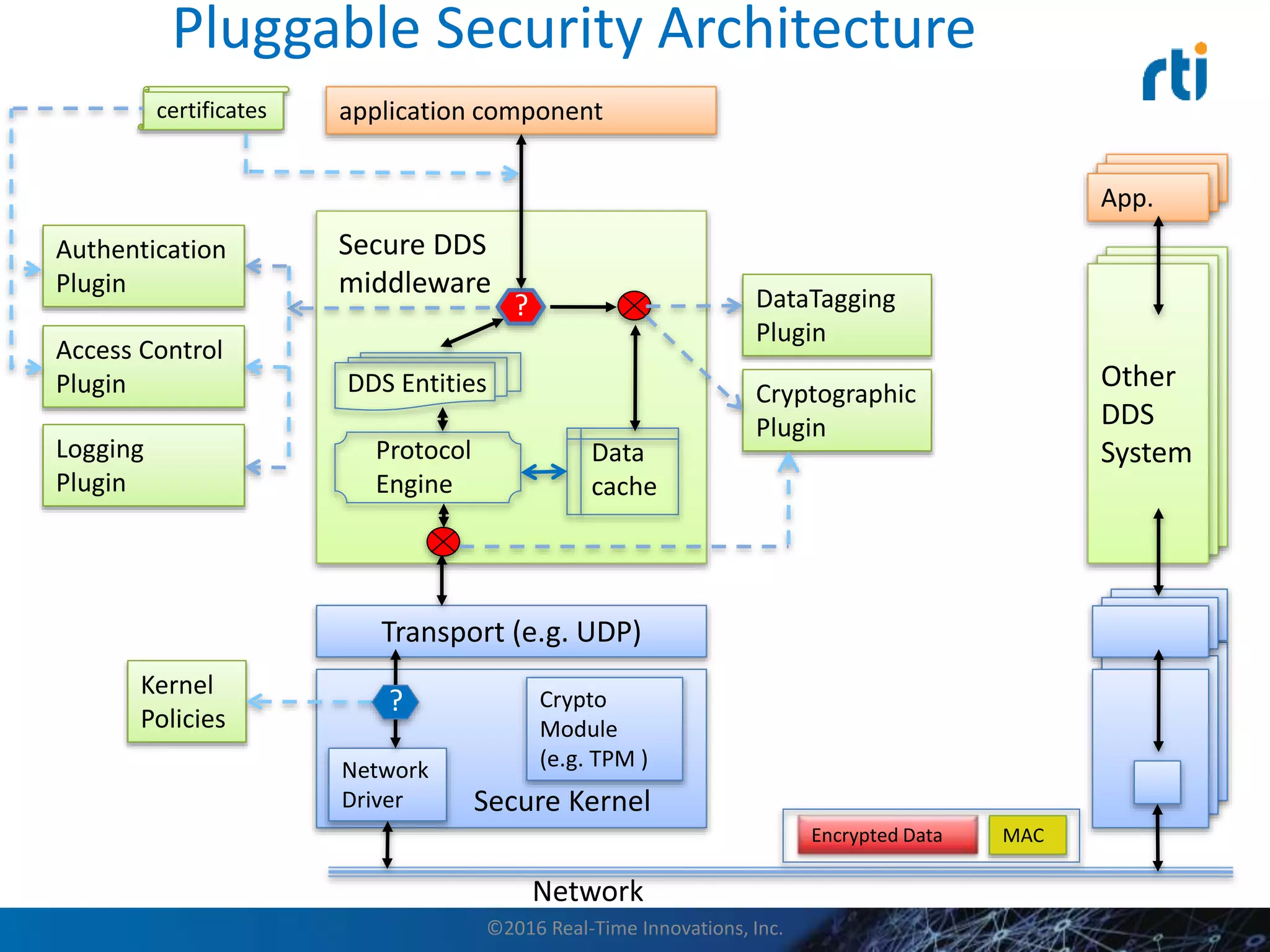
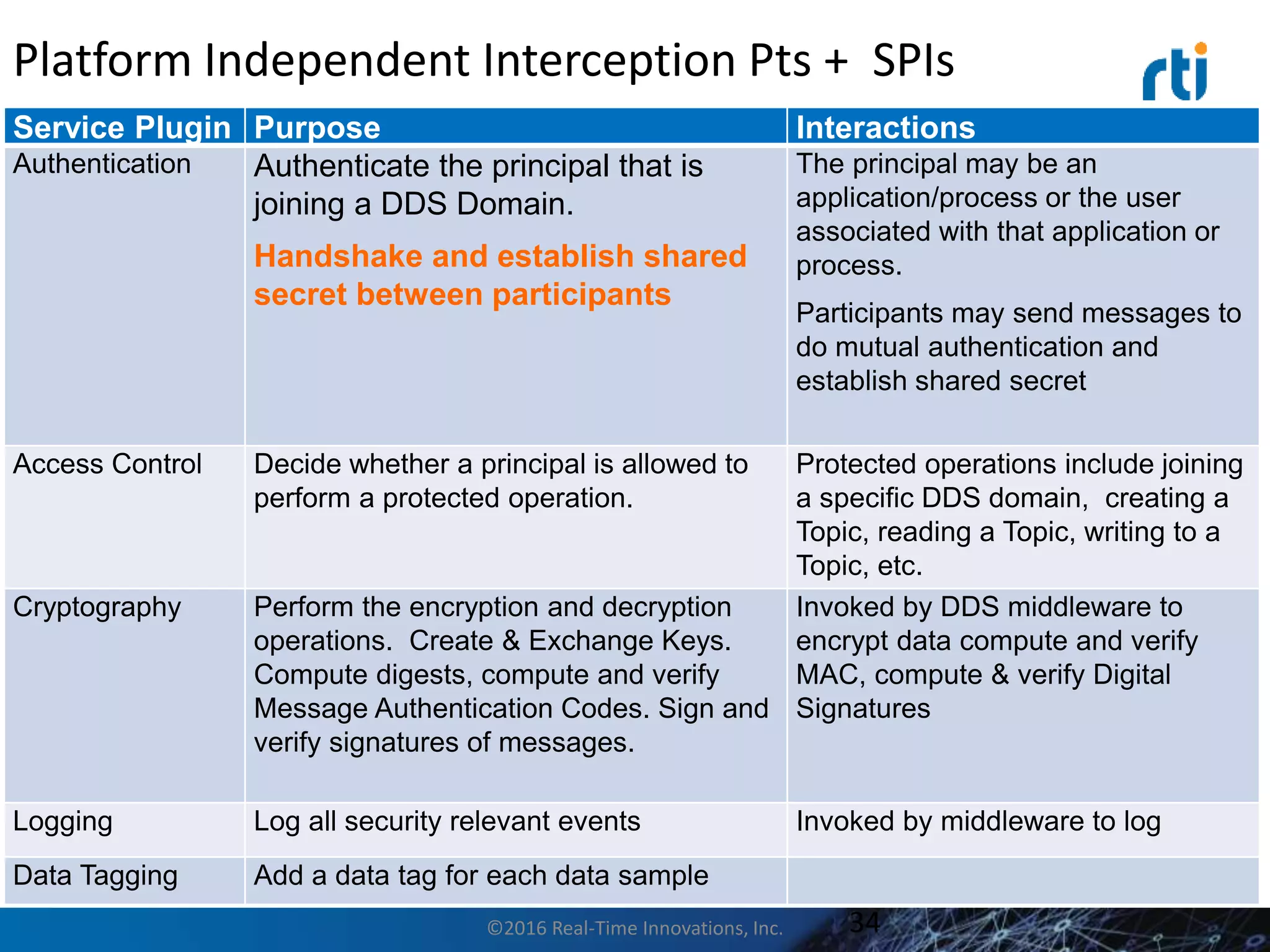
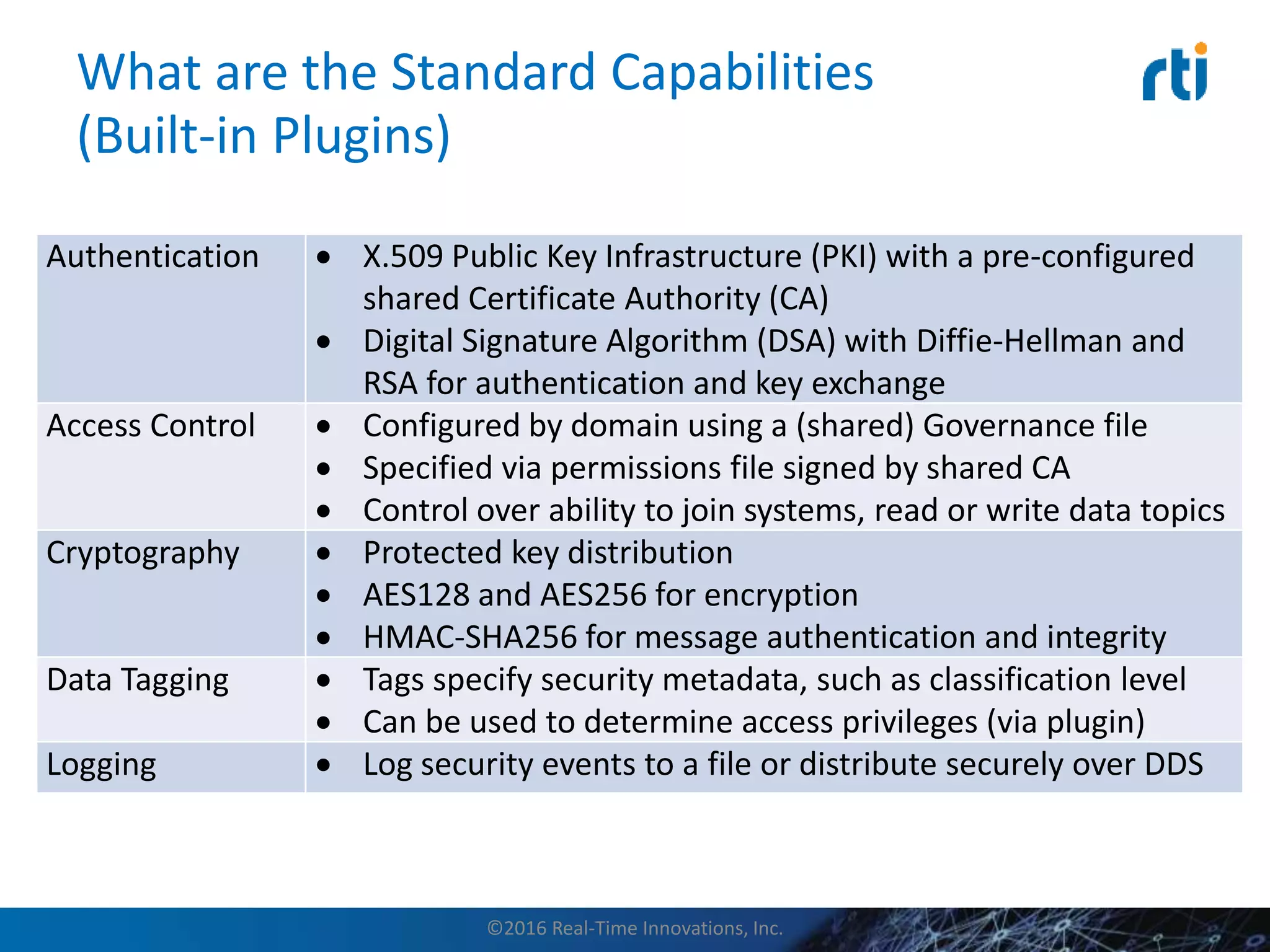
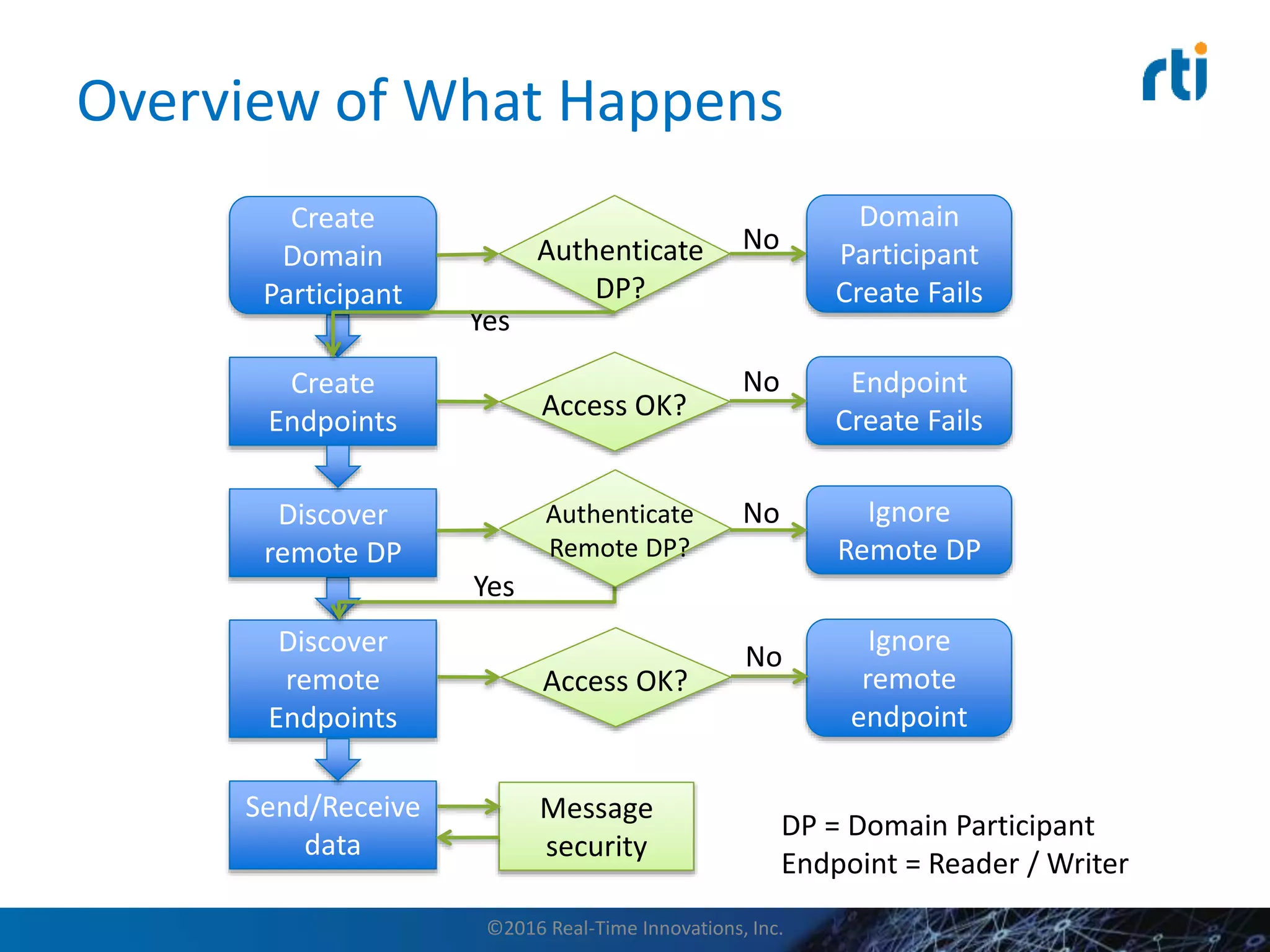
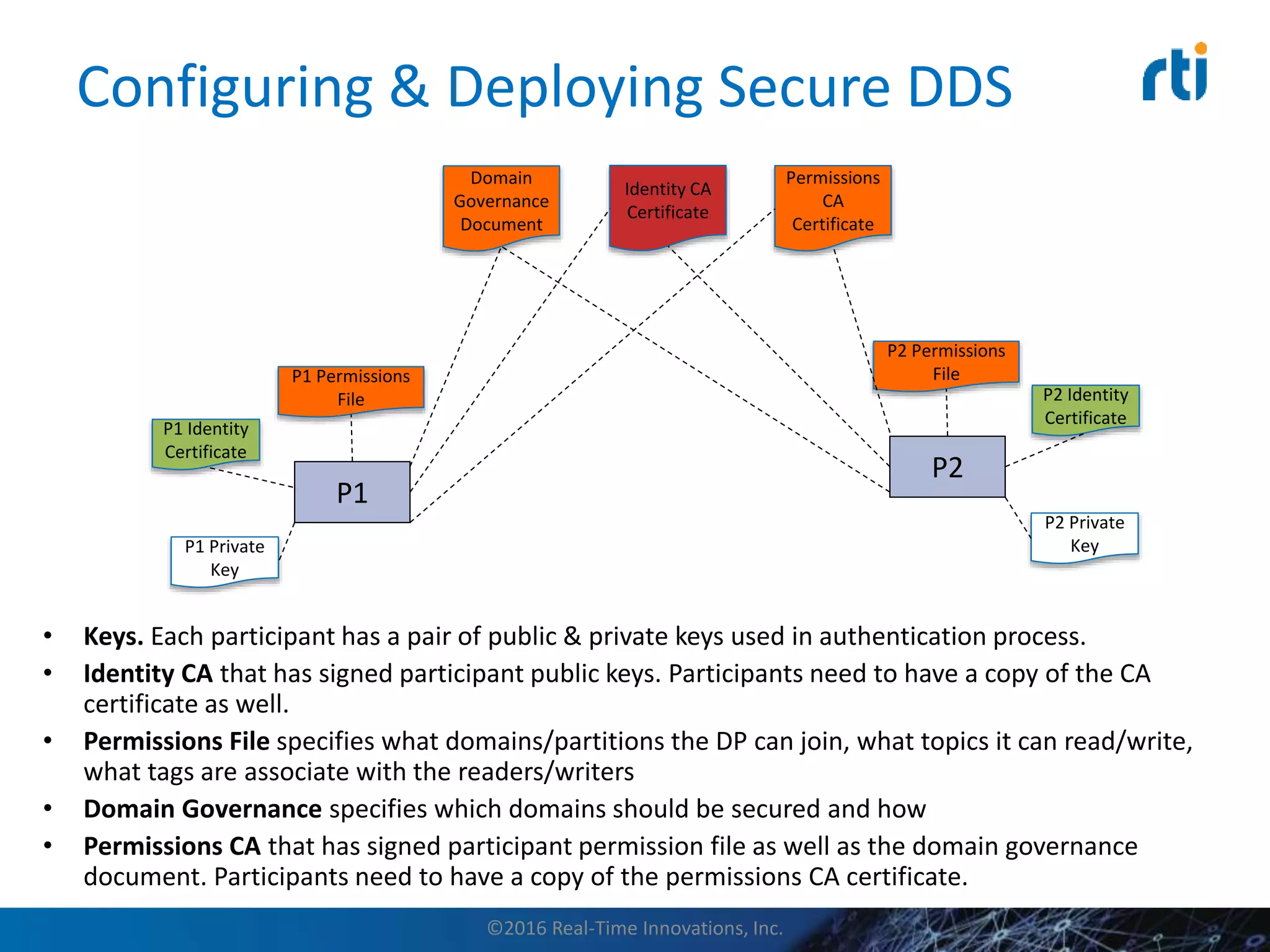
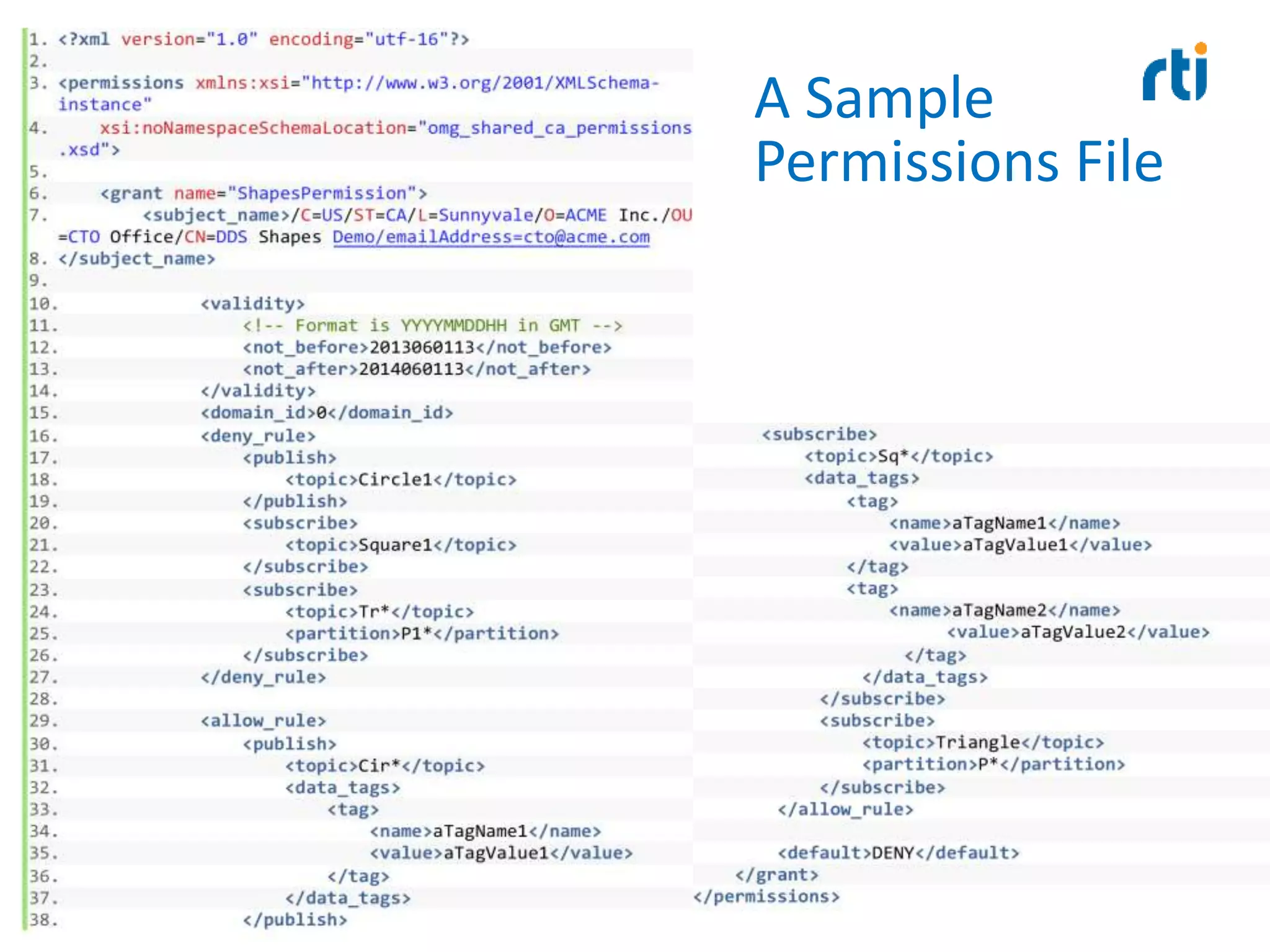
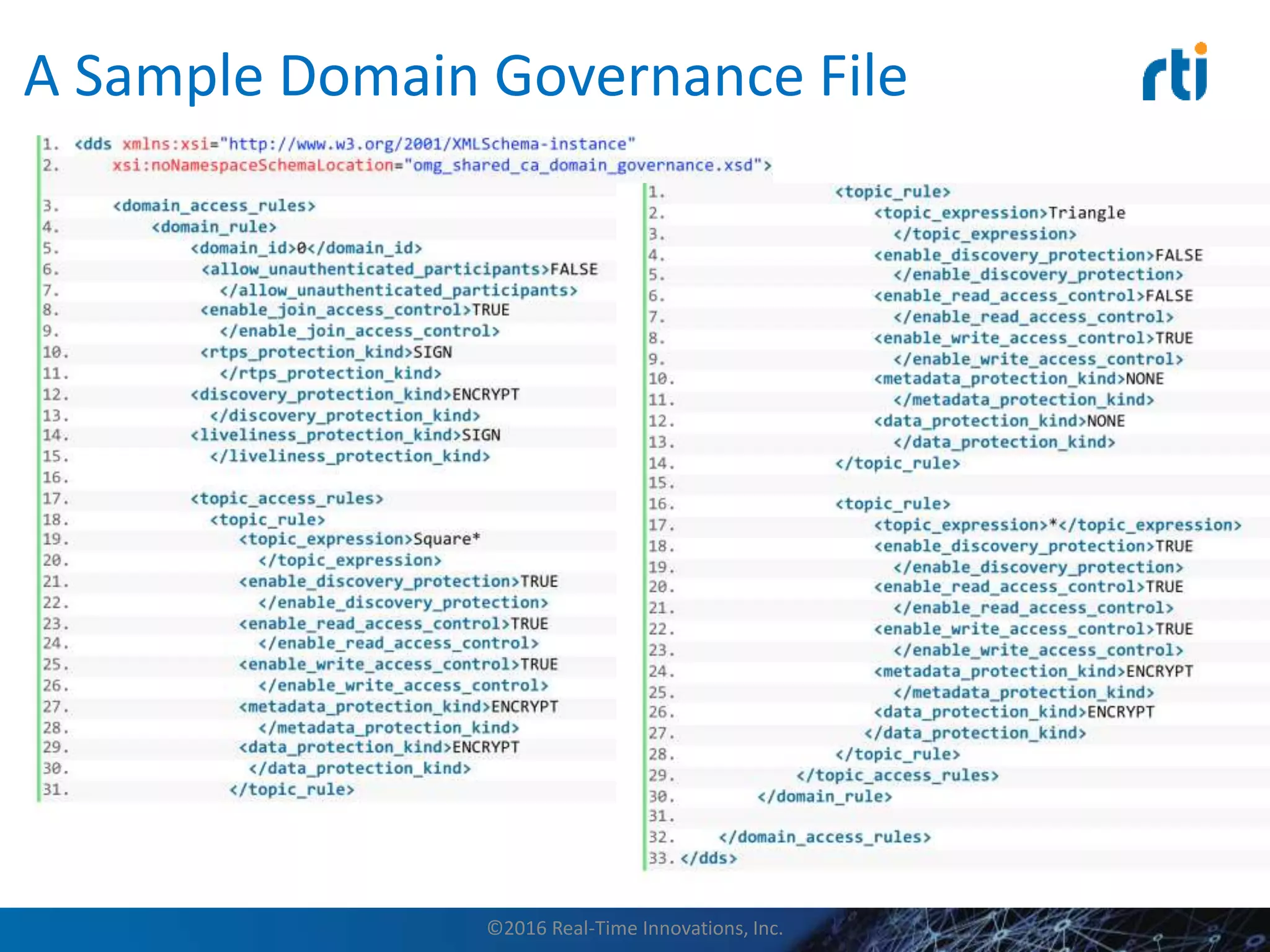
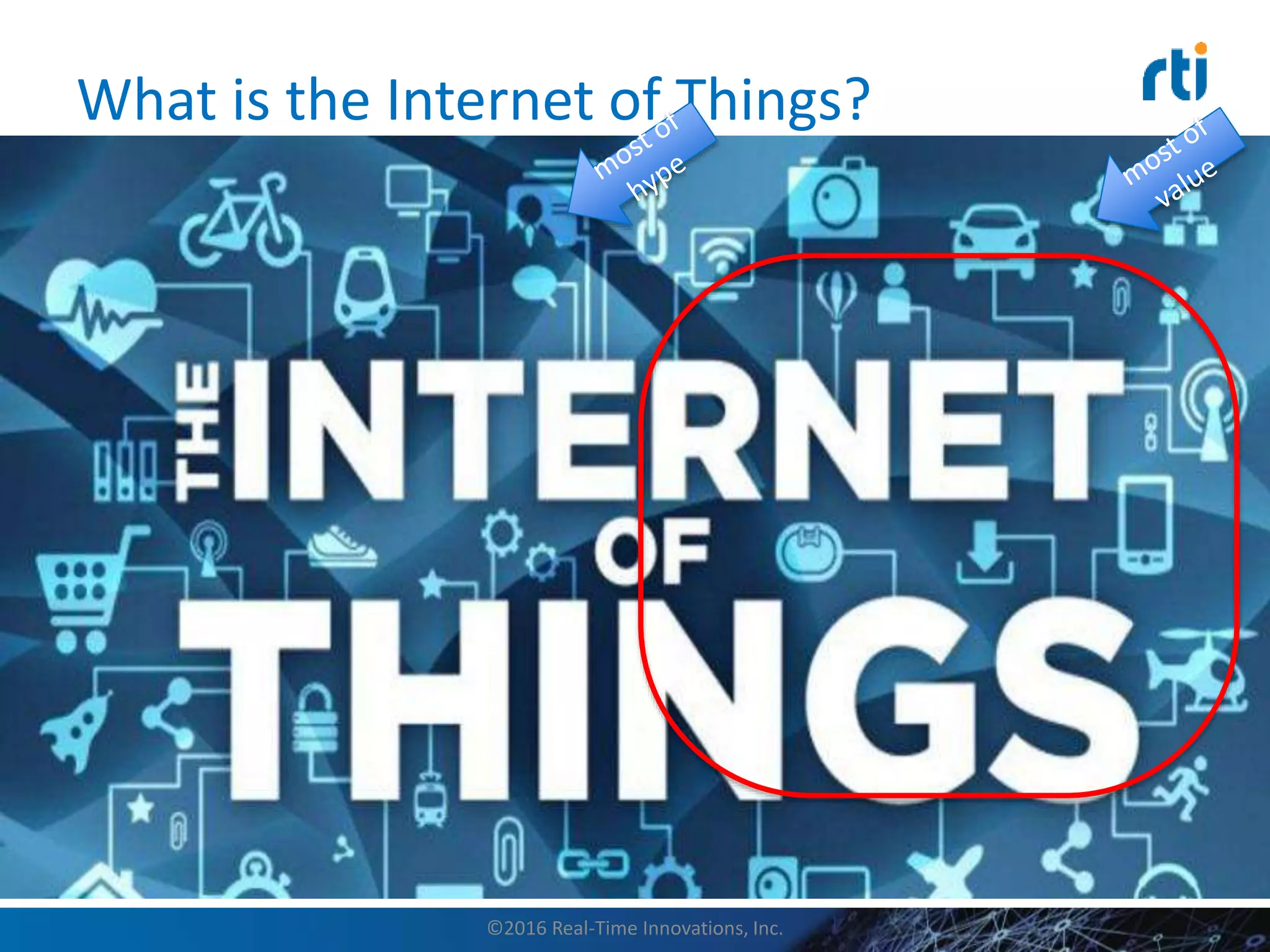
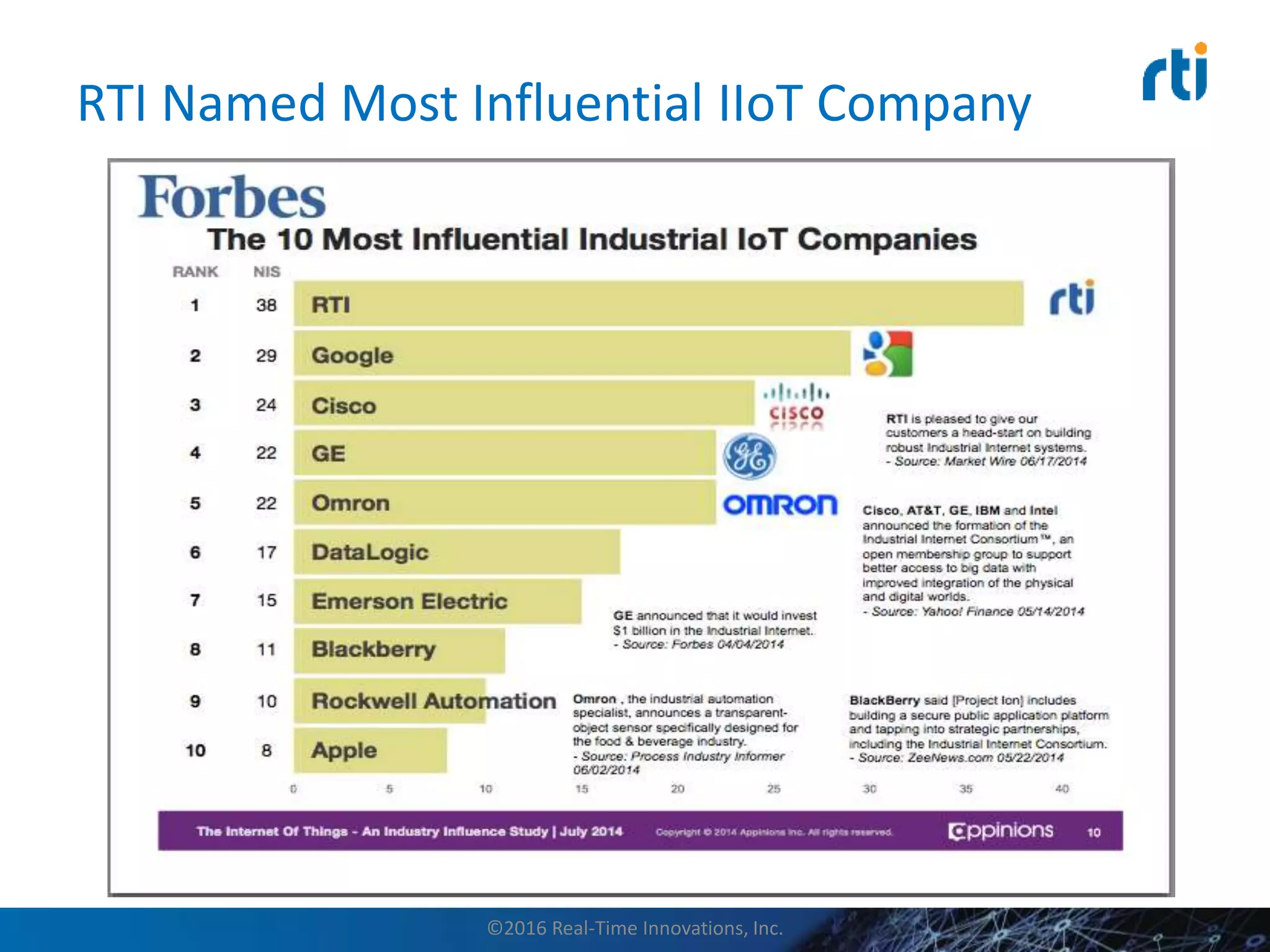
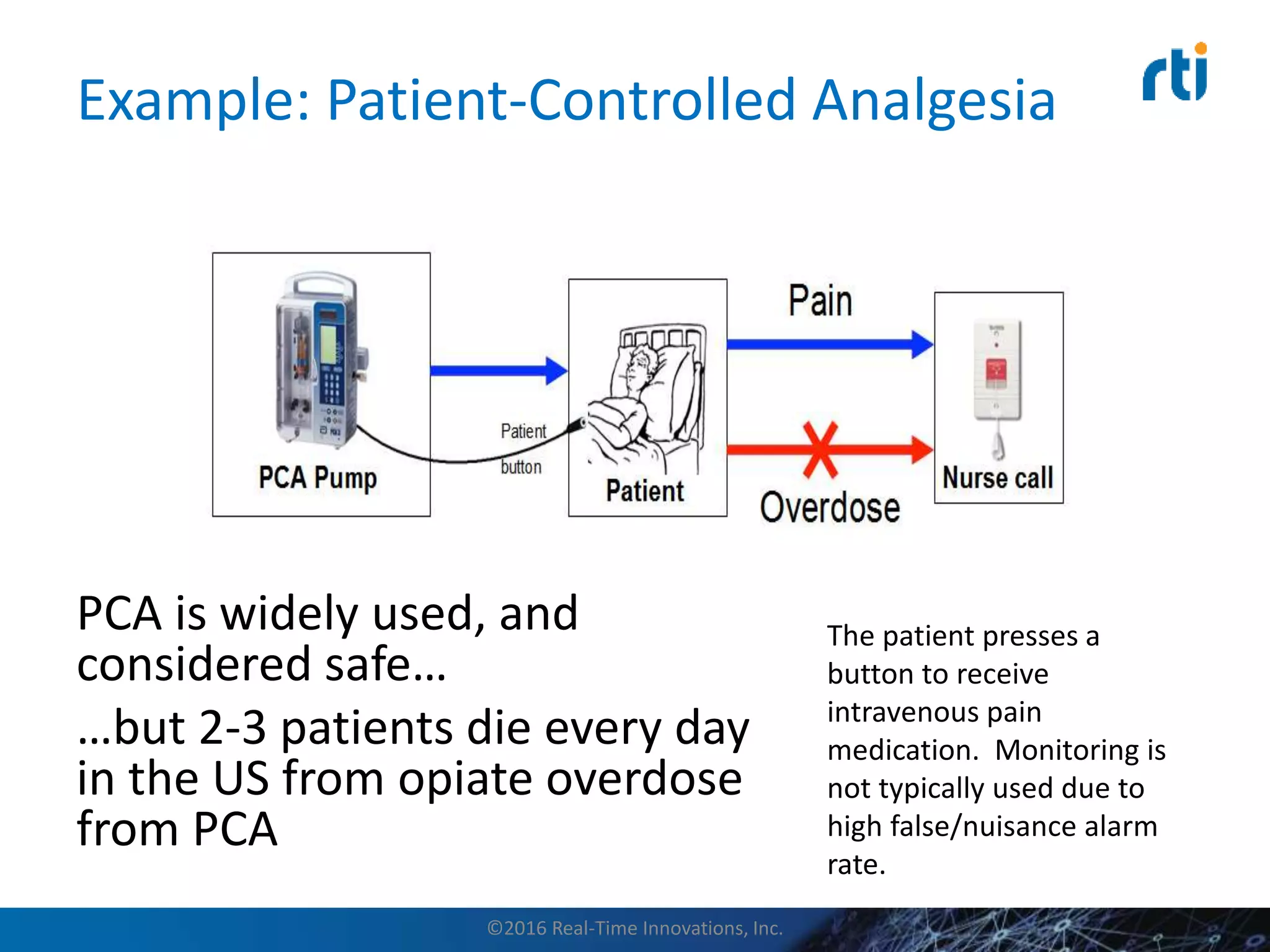
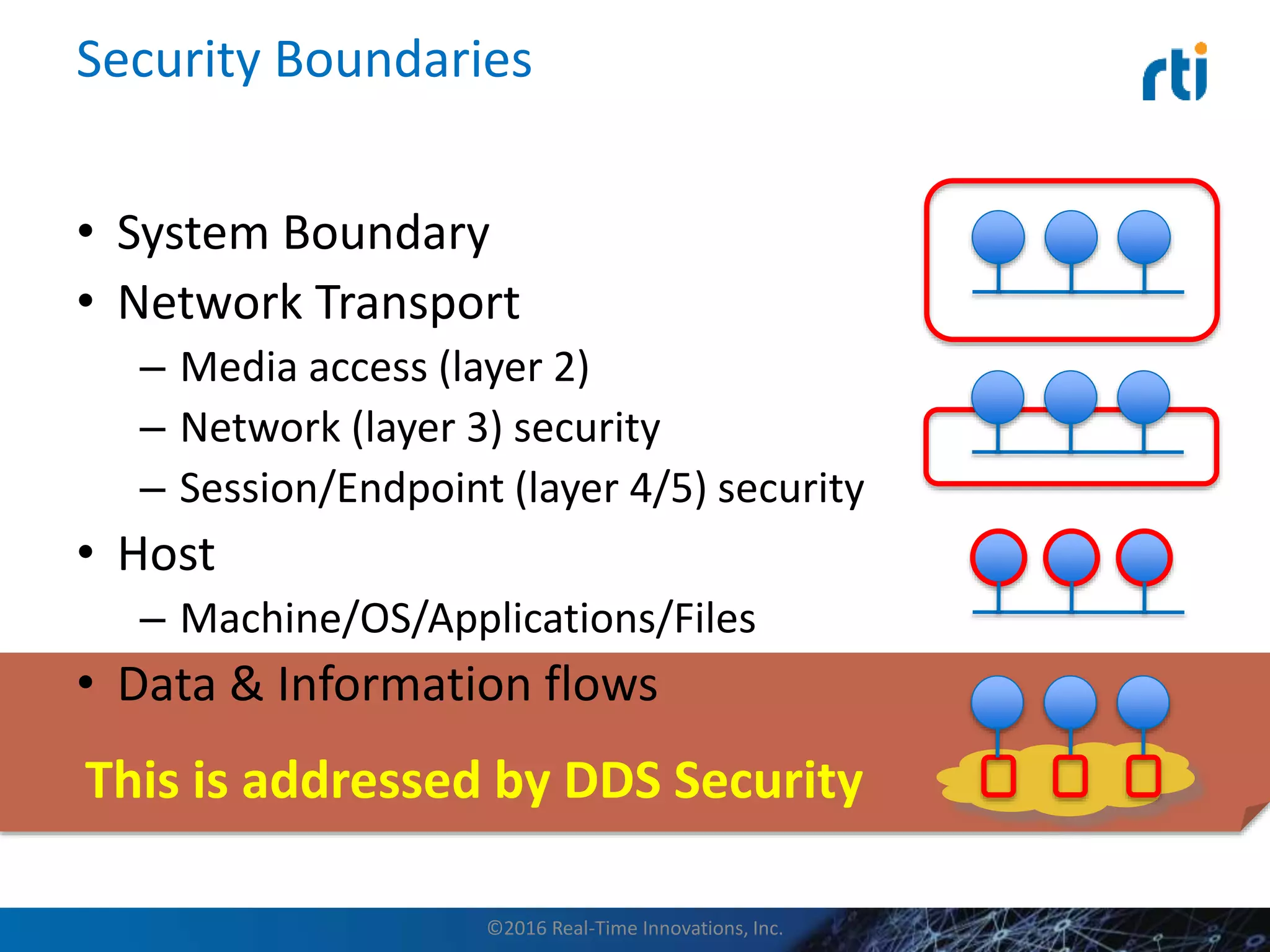
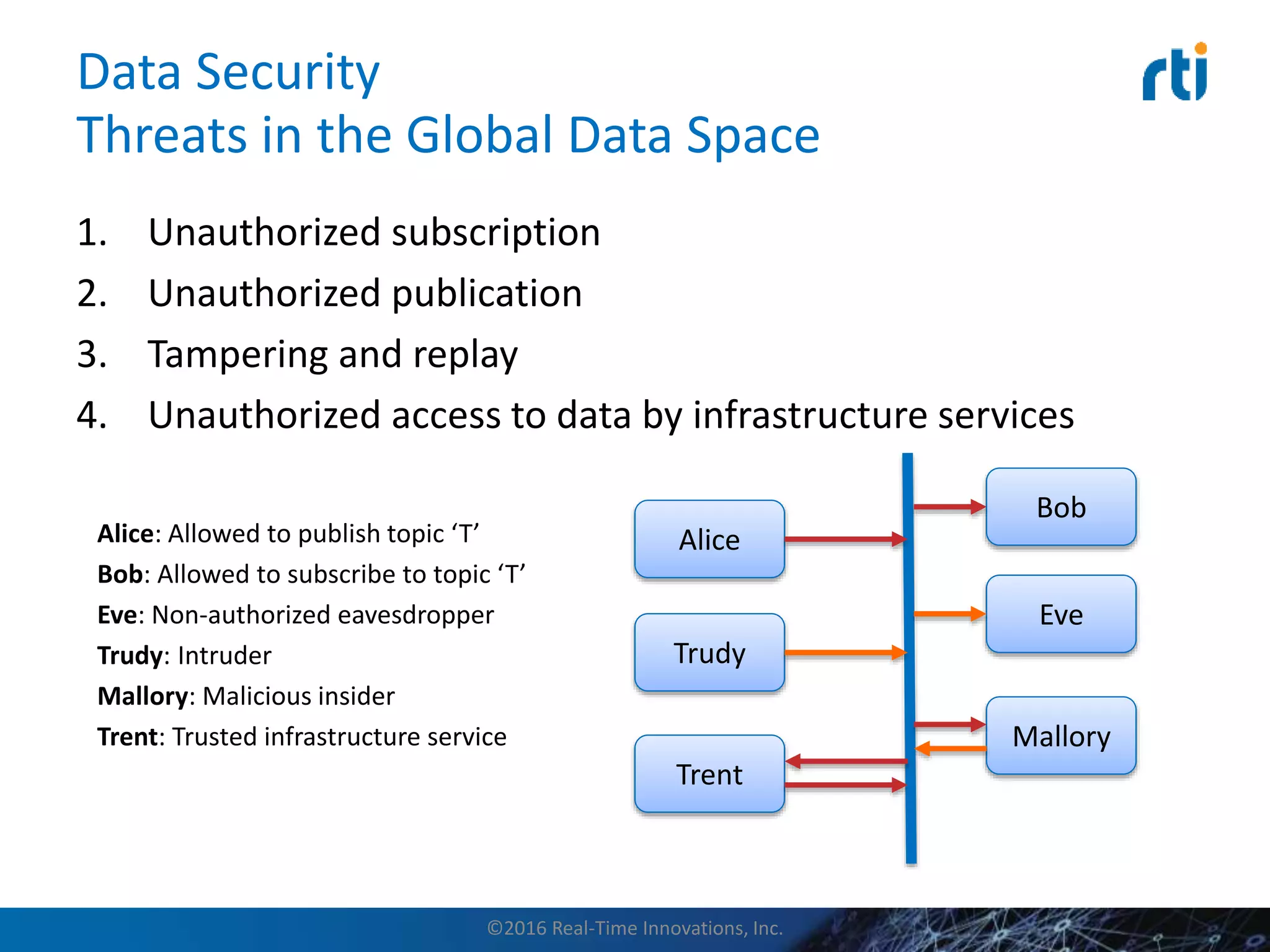
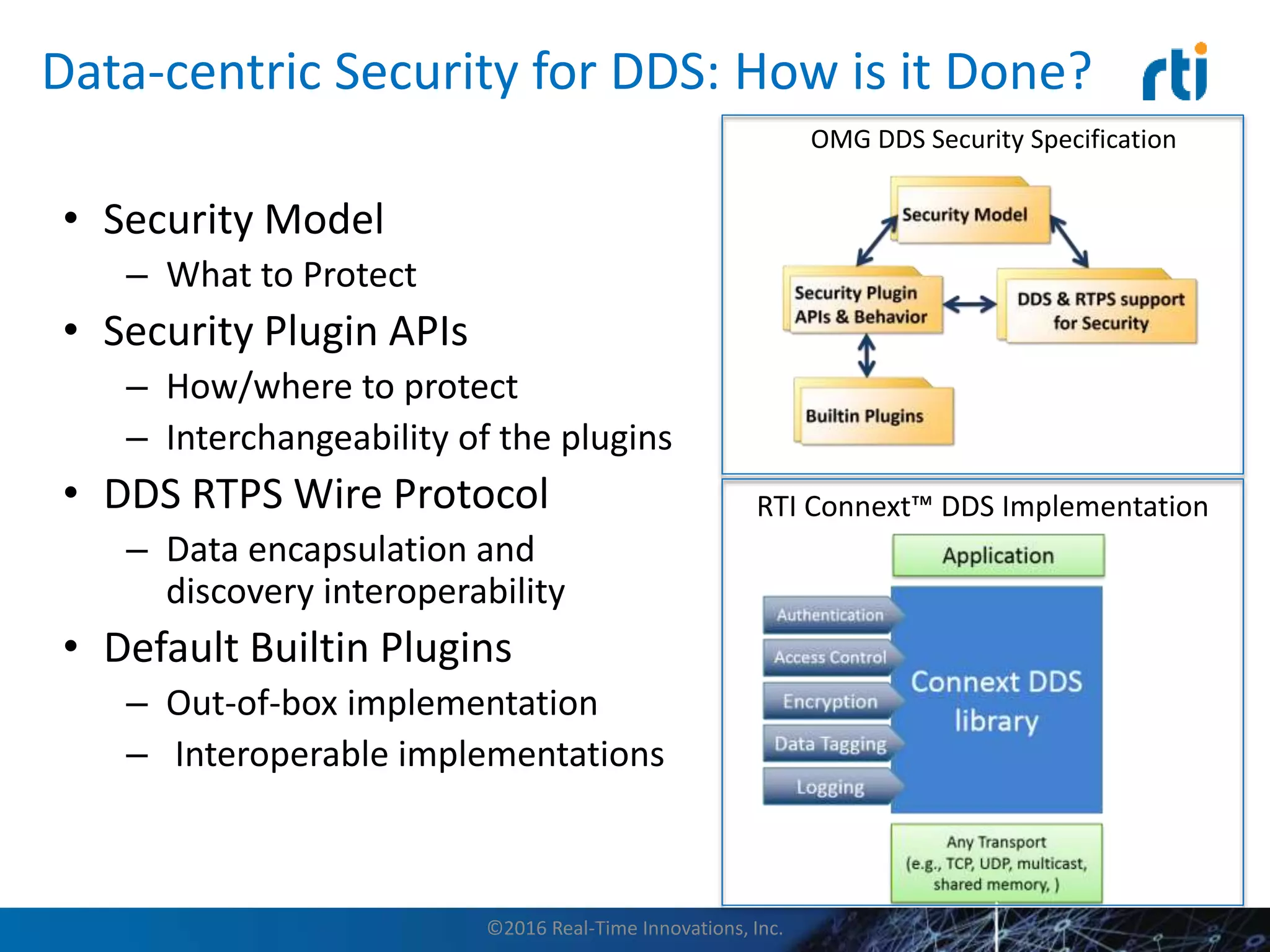
This document discusses data distribution service (DDS) security for the industrial internet of things (IIoT). It provides background on DDS and the IIoT. It then discusses how DDS security works, including pluggable security architectures, authentication, access control, and message security. The goal of DDS security is to prevent unauthorized access to data in the global data space shared by DDS applications. Built-in security capabilities include X.509 authentication, access control configuration, and encryption/message authentication algorithms.















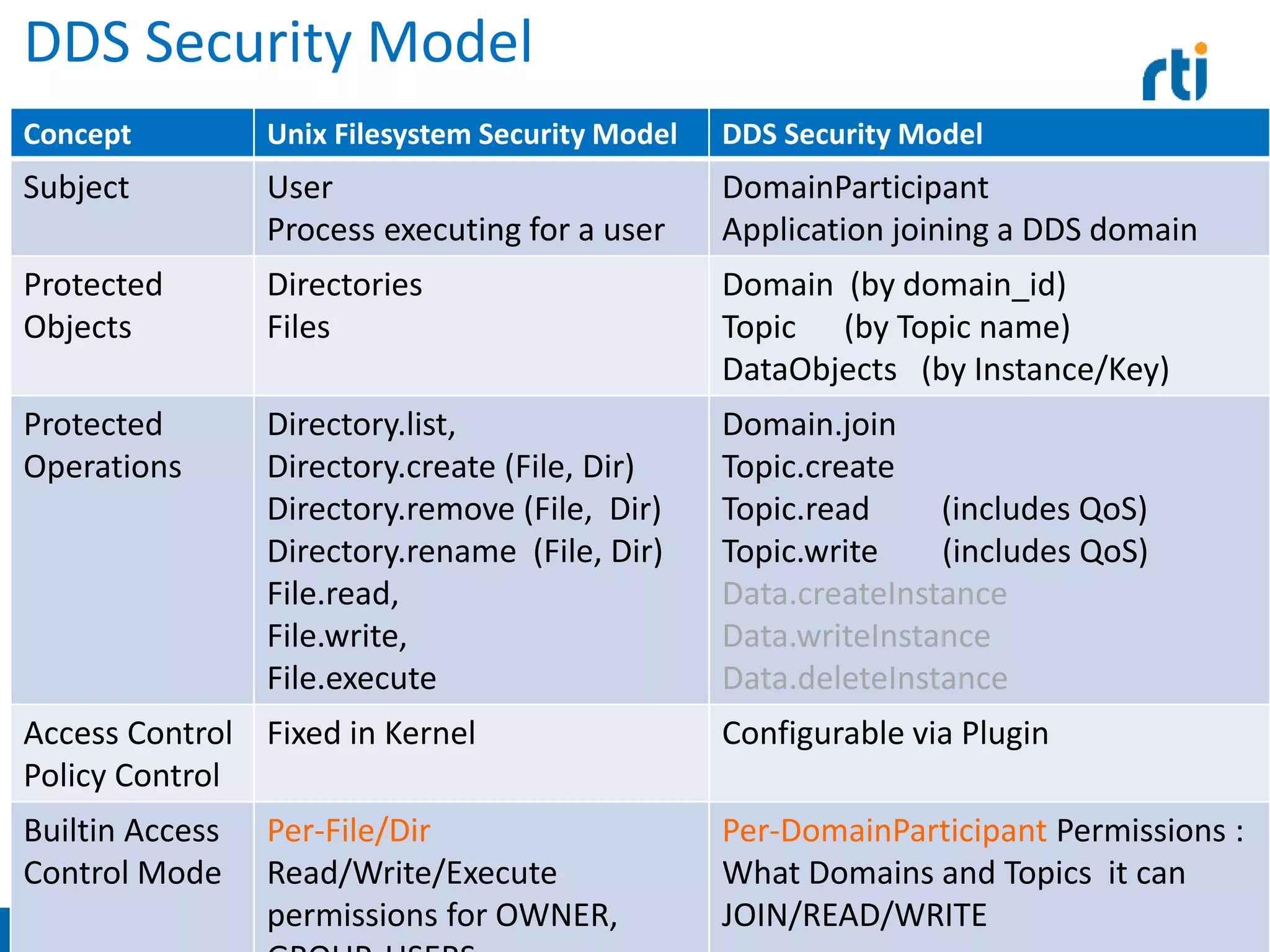
![Security Model Example:
UNIX FileSystem (simplified)
• Subjects: Users, specifically processes executing on behalf of a specific userid
• Protected Objects: Files and Directories
• Protected Operations on Objects:
– Directory.list, Directory.createFile, Directory.createDir, Directory.removeFile,
Directory.removeDir, Directory.renameFile
– File.view, File.modify, File.execute
• Access Control Model:
– A subject is given a userId and a set of groupId
– Each object is assigned a OWNER and a GROUP
– Each Object is given a combination of READ, WRITE, EXECUTE permissions
for the assigned OWNER and GROUP
– Each protected operation is mapped to a check, for example
• File.view is allowed if and only if
– File.owner == Subject.userId AND File.permissions(OWNER) includes READ
– OR File.group IS-IN Subject.groupId[] AND File.permissions(GROUP) includes READ
©2016 Real-Time Innovations, Inc.](https://image.slidesharecdn.com/datadistributionservicesecurityandtheindustrialinternetofthings-160115190450/75/Data-Distribution-Service-Security-and-the-Industrial-Internet-of-Things-31-2048.jpg)