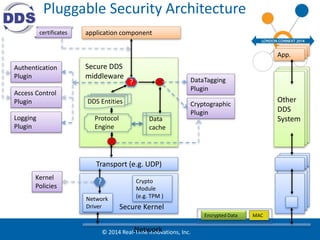
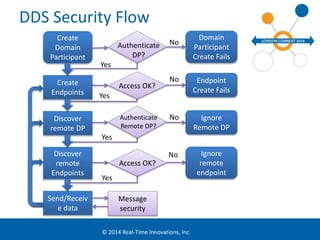
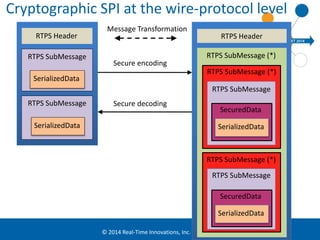
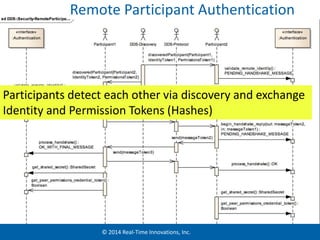
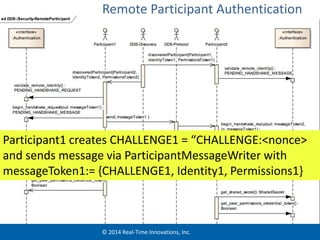
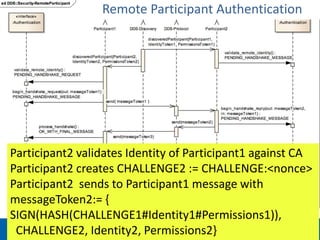
The document discusses security considerations for data-centric publish-subscribe systems like the Data Distribution Service (DDS). It describes how DDS can implement security features like authentication, access control, confidentiality and integrity without conflicting with its global data space model. A pluggable security architecture is proposed that uses authentication, access control and cryptography plugins to enforce security policies while remaining decoupled.








![Security Model Example:
UNIX FileSystem (simplified)
• Subjects: Users, specifically processes executing on behalf of a specific userid
• Protected Objects: Files and Directories
• Protected Operations on Objects:
– Directory.list, Directory.createFile, Directory.createDir, Directory.removeFile,
Directory.removeDir, Directory.renameFile
– File.view, File.modify, File.execute
© 2014 Real-Time Innovations, Inc.
• Access Control Model:
– A subject is given a userId and a set of groupId
– Each object is assigned a OWNER and a GROUP
– Each Object is given a combination of READ, WRITE, EXECUTE permissions
for the assigned OWNER and GROUP
– Each protected operation is mapped to a check, for example
• File.view is allowed if and only if
– File.owner == Subject.userId AND File.permissions(OWNER) includes READ
– OR File.group IS-IN Subject.groupId[] AND File.permissions(GROUP) includes READ](https://image.slidesharecdn.com/201410emeasecurityexternal-141027174311-conversion-gate02/85/DDS-Security-for-the-Industrial-Internet-London-Connext-DDS-Conference-12-320.jpg)