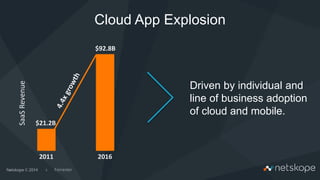
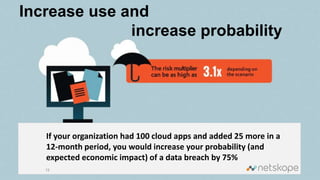
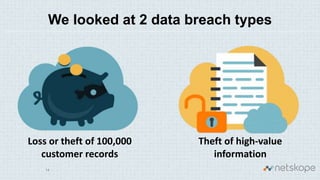
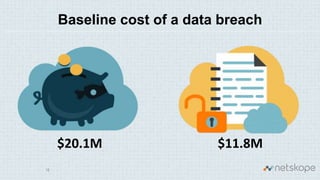
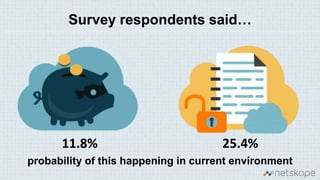
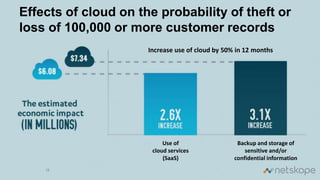
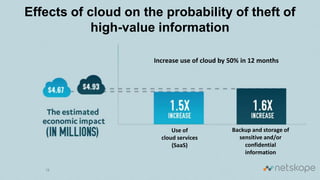
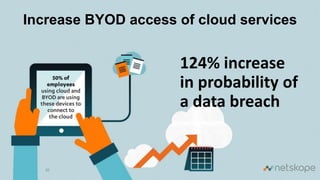
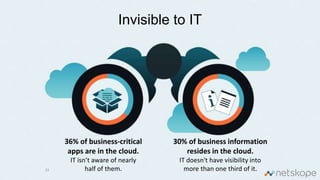
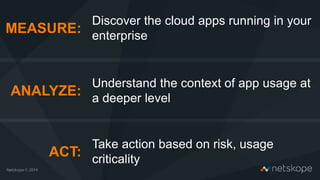
The document discusses the increasing security risks associated with cloud app adoption in organizations, highlighting that a significant percentage of IT respondents are unaware of the true number of cloud services in use. It outlines the economic impact of data breaches, indicating that the probability of a breach increases with additional cloud applications. Key recommendations include assessing cloud app usage, understanding risk context, and taking actions to protect data and ensure compliance.