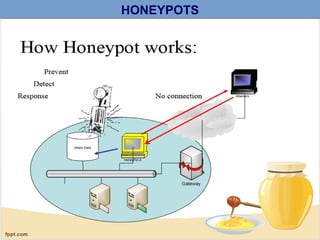
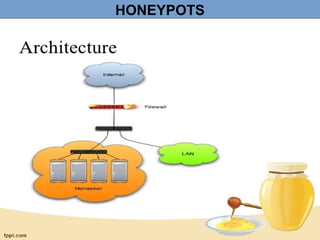
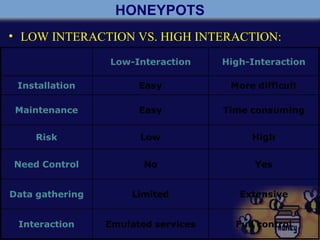
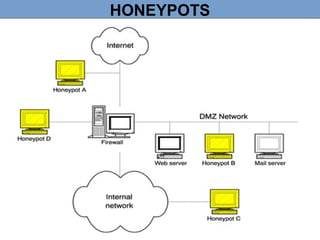
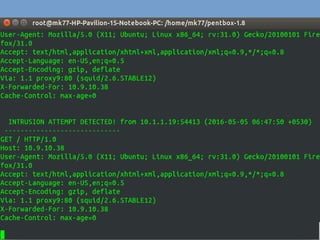
A honeypot is a computer security mechanism designed to detect and counter unauthorized access by simulating a valuable target for attackers. They can be classified by implementation (physical or virtual), purpose (production or research), and interaction level (high, low, or middle). Honeypots serve to prevent, detect, and respond to attacks, although they are primarily effective for research and limited information capture in production settings.