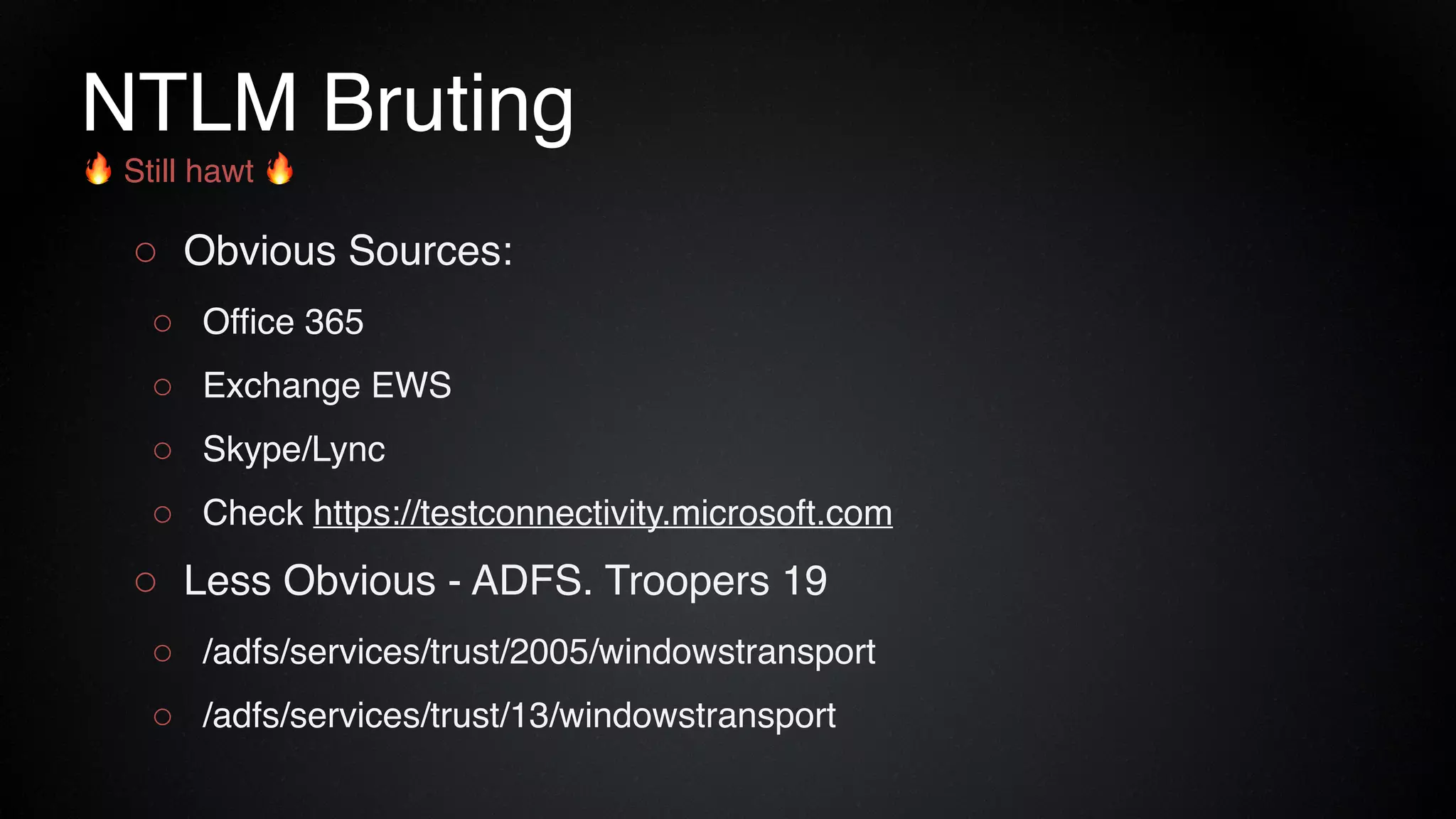
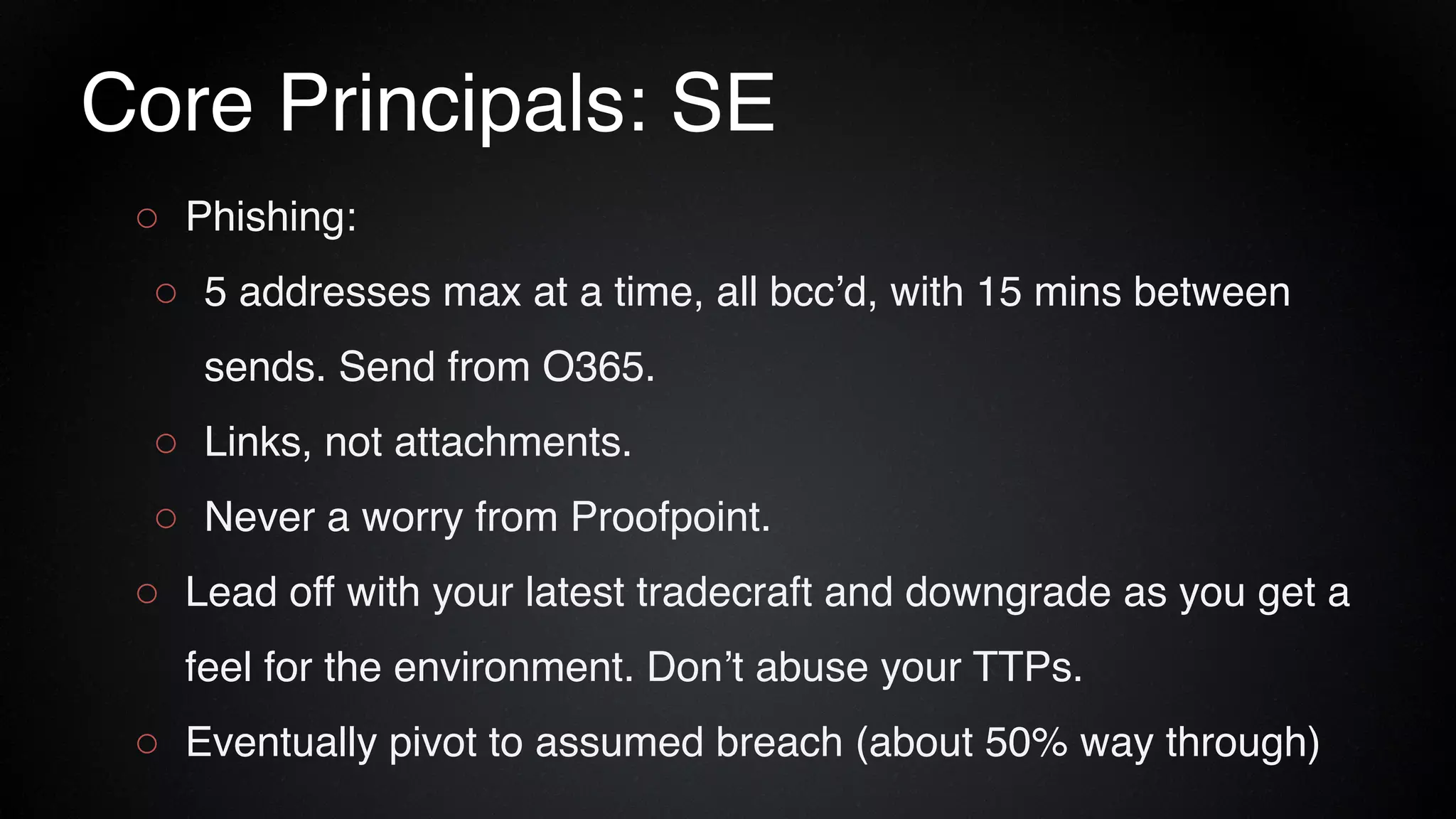
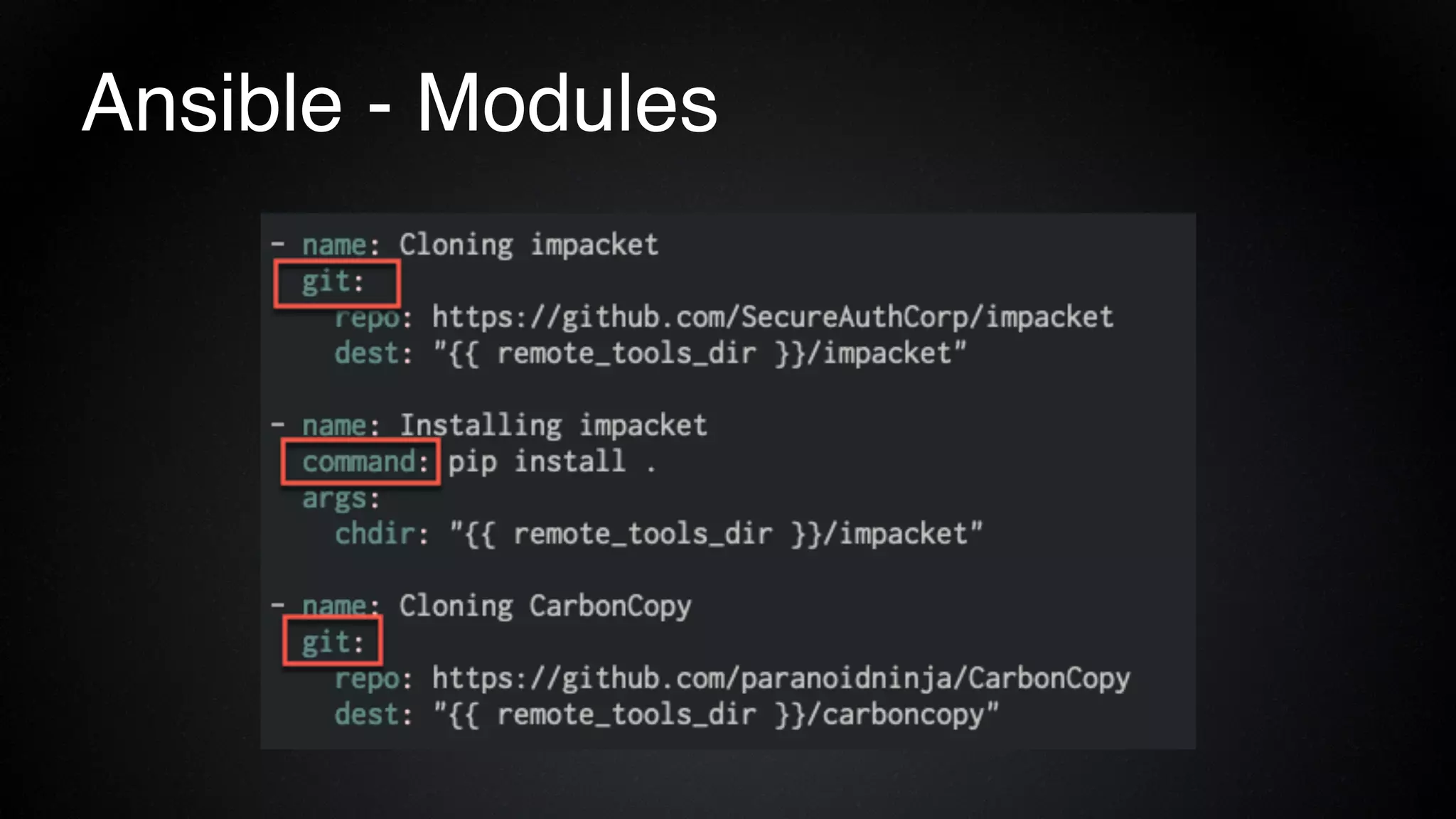
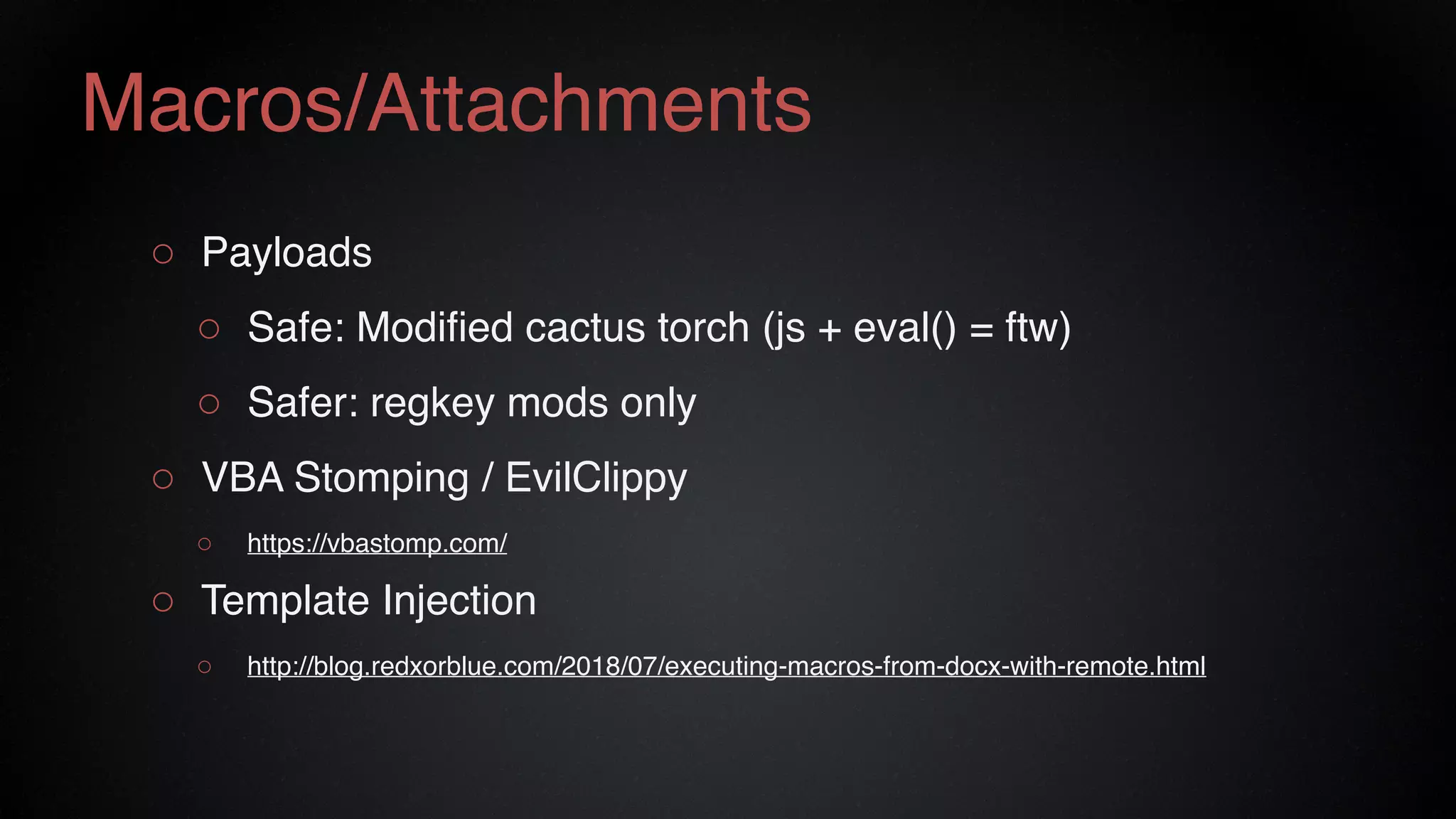
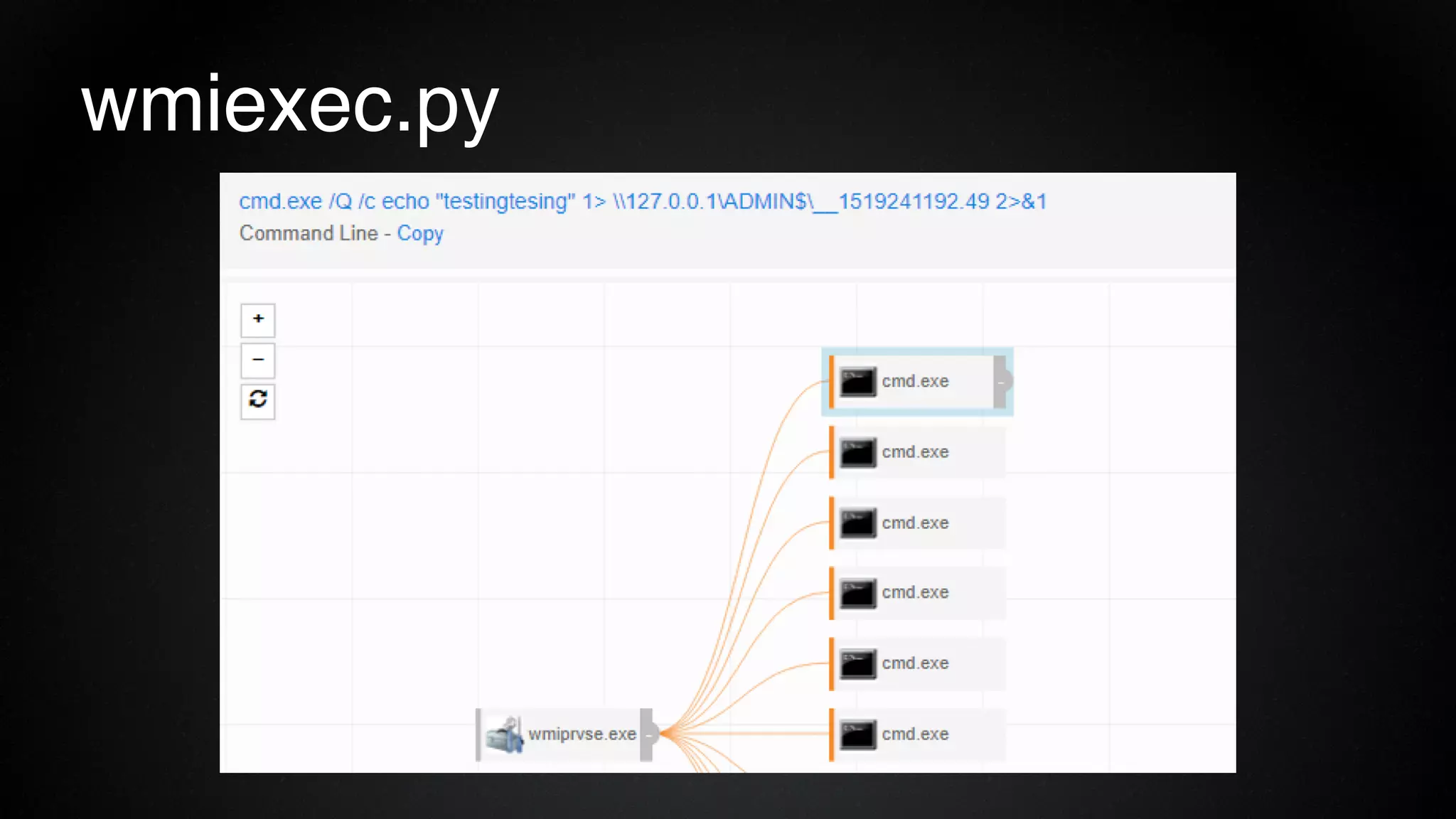
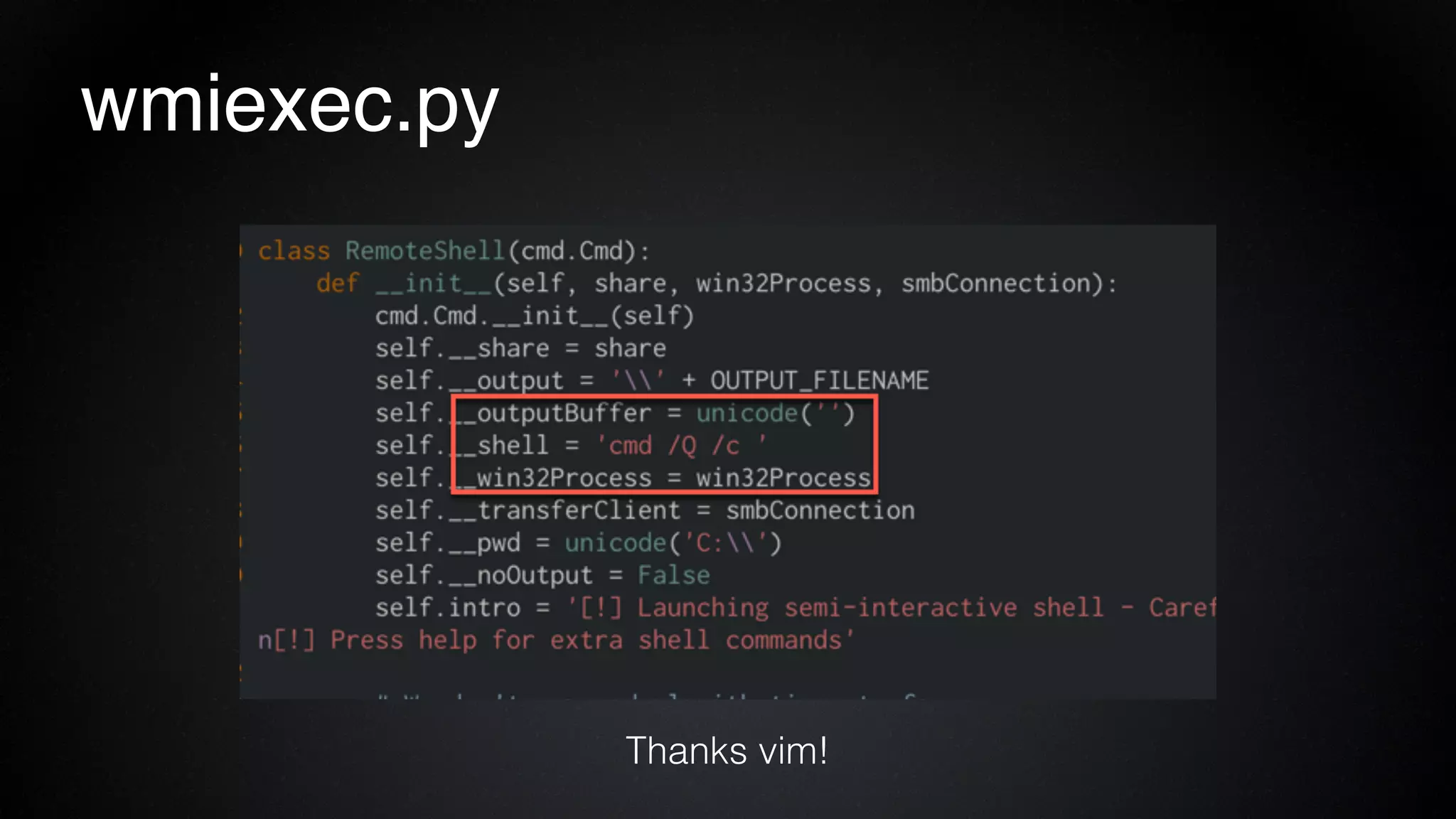
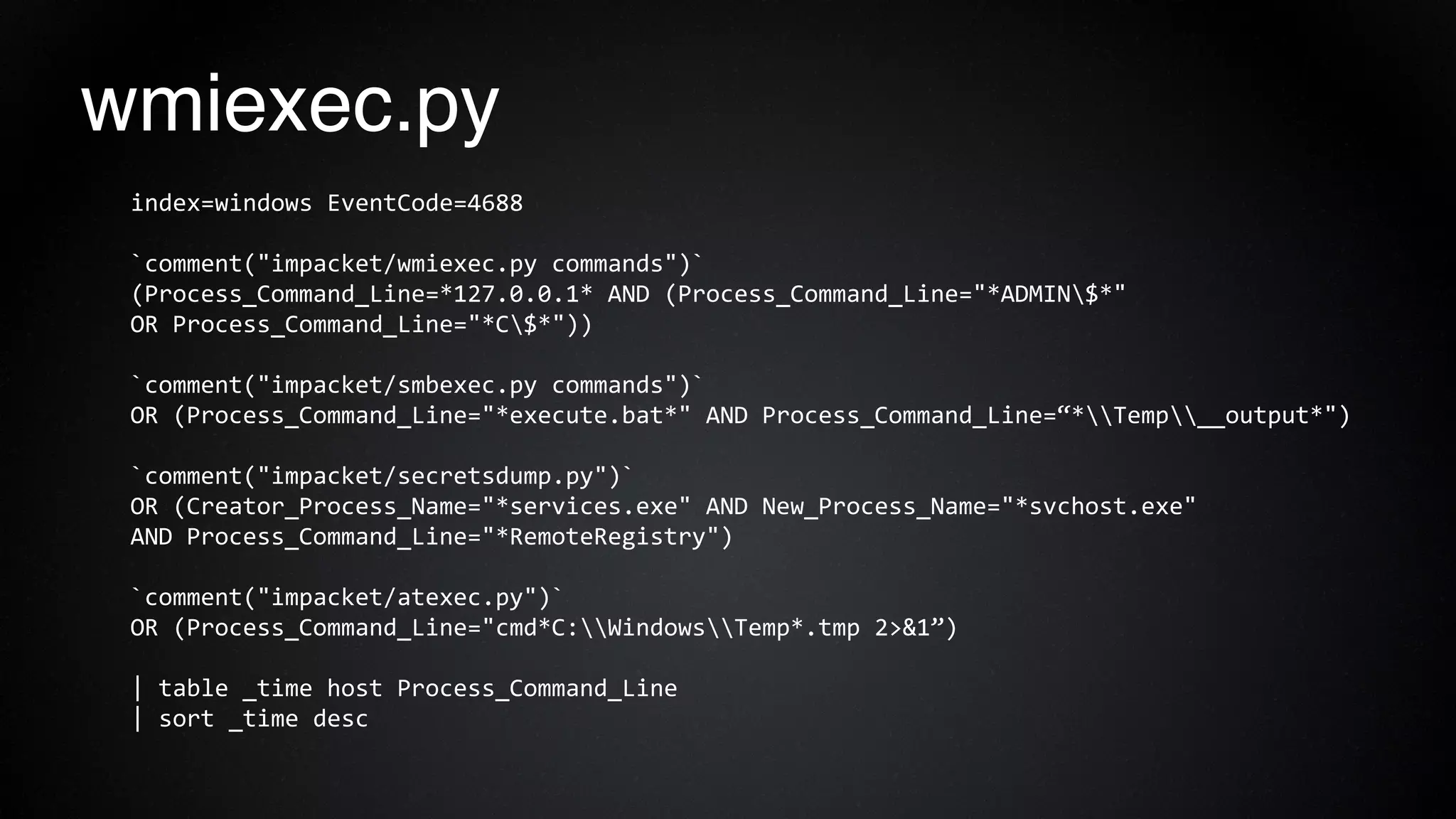
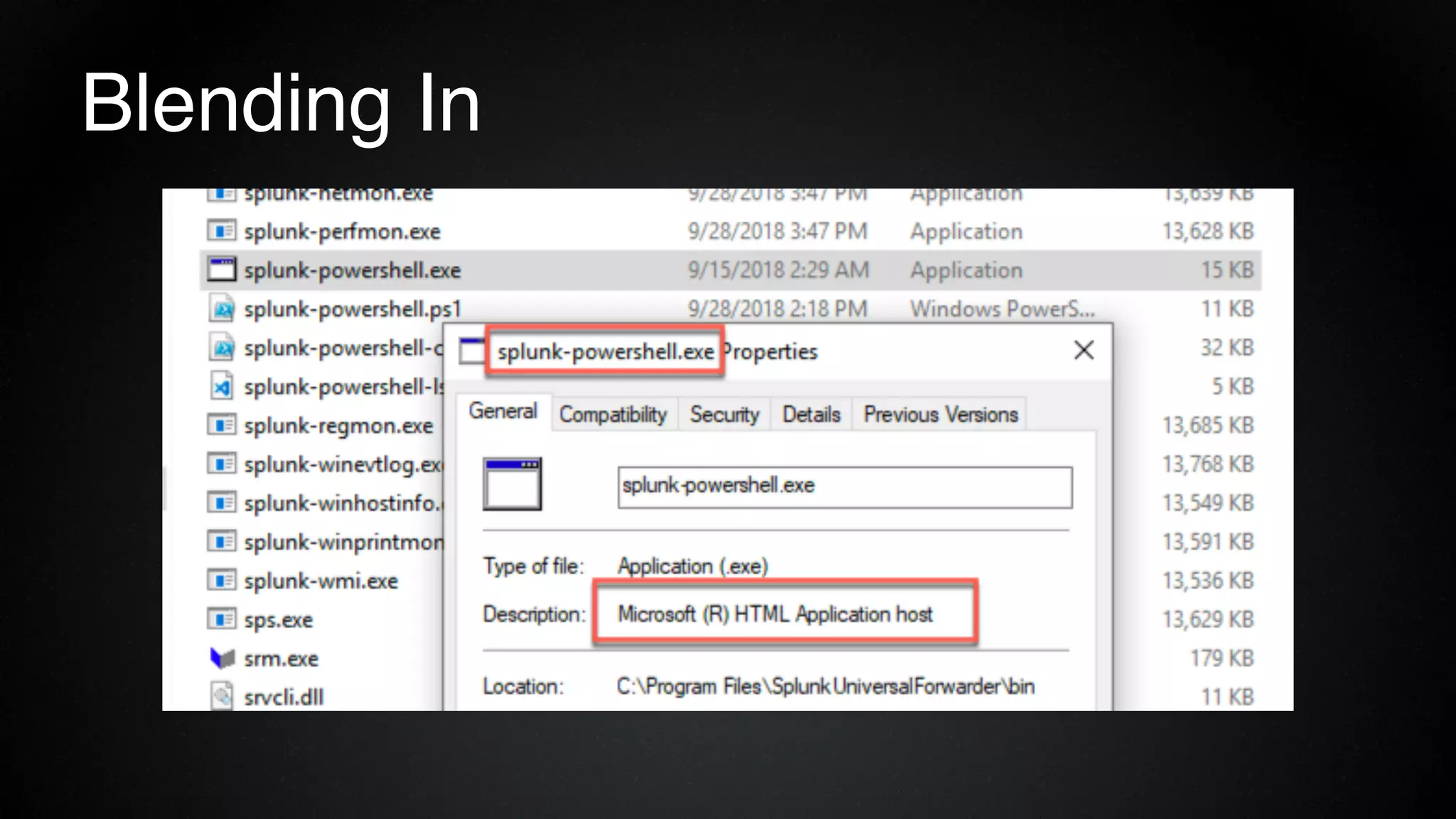
The document provides an overview of a red team consultant's methodology for penetration testing engagements. It discusses various stages of an engagement including pre-engagement reconnaissance using tools like LinkedIn and domain research. It covers external testing techniques like NTLM brute forcing. Internal testing focuses on privileges escalation using tools like Mimikatz and movement using techniques like DLL hijacking. Reporting emphasizes providing a full narrative and findings of high quality over large quantities.












![LinkedIn - Build It Fast
1. Build a decent profile. Be thorough.
Be sure to add colleges/organization.
2. Click “My Network”
3. Scroll way down to fill the page
4. Run in Browser dev tools
$("[data-control-name*='invite']").each(function(index) { $(this).trigger('click'); })
Thanks @mandreko & @Glitch1101!](https://image.slidesharecdn.com/redteammethodology-anakedlook-190907213330/75/Red-Team-Methodology-A-Naked-Look-15-2048.jpg)