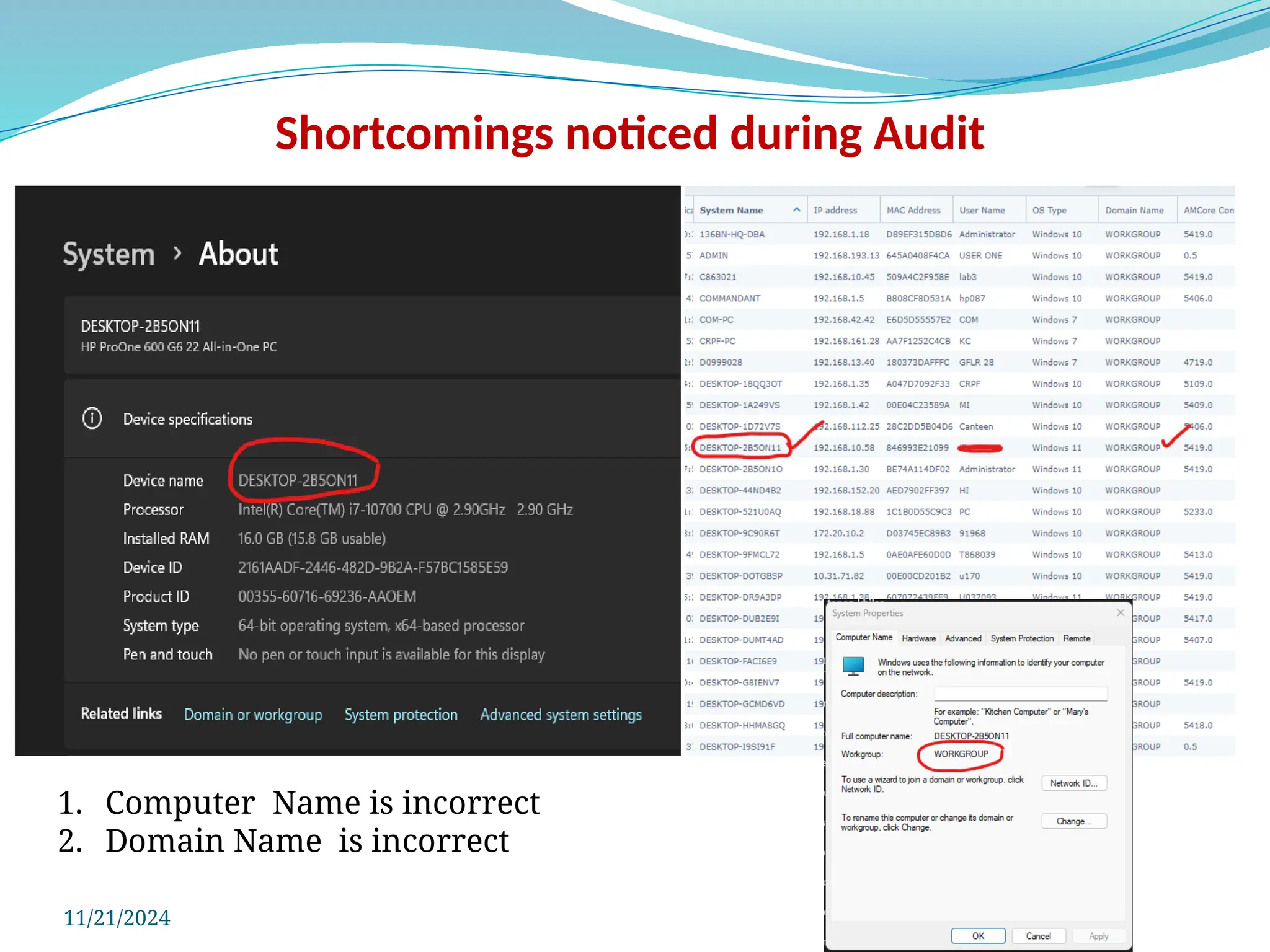
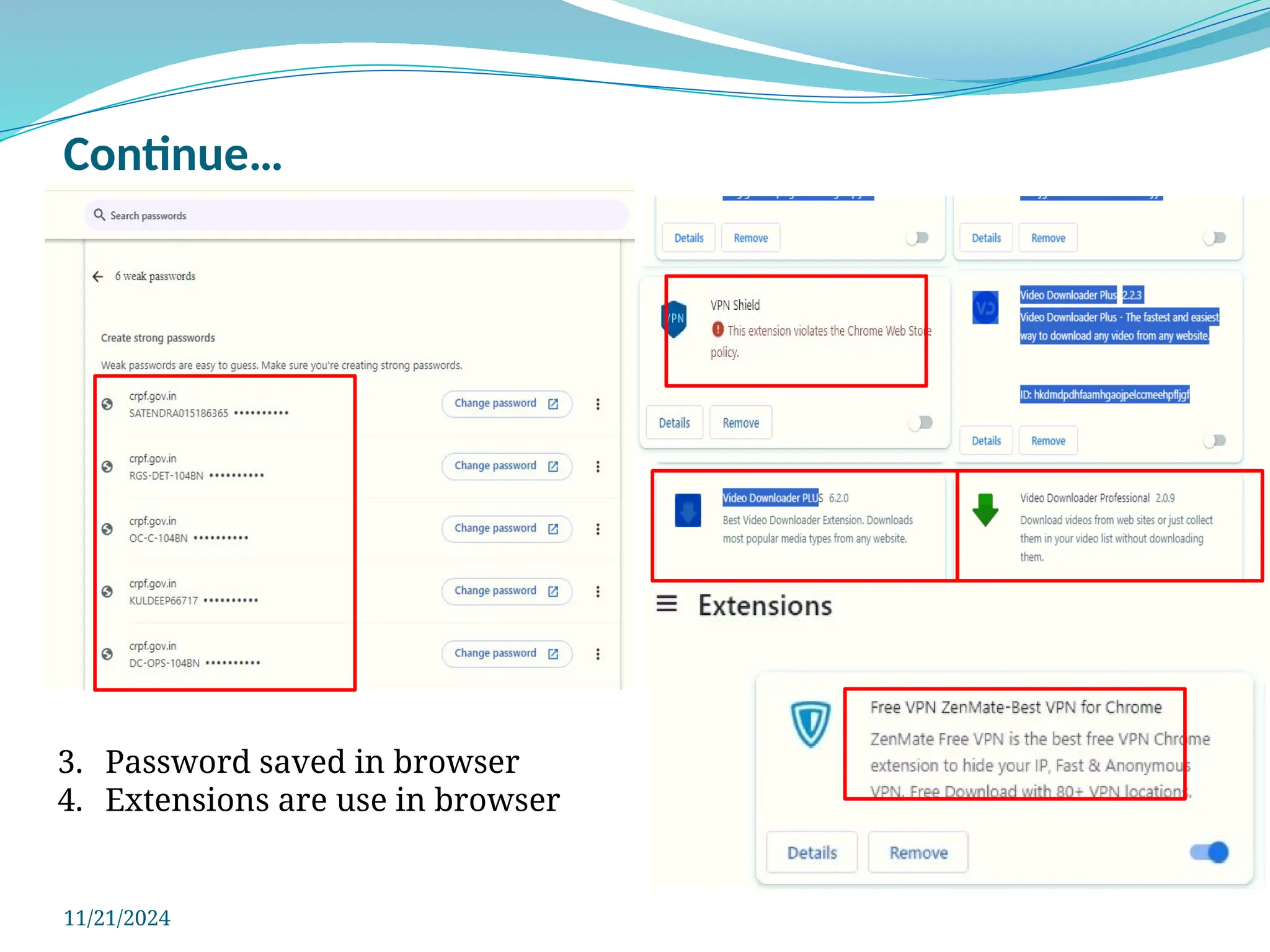
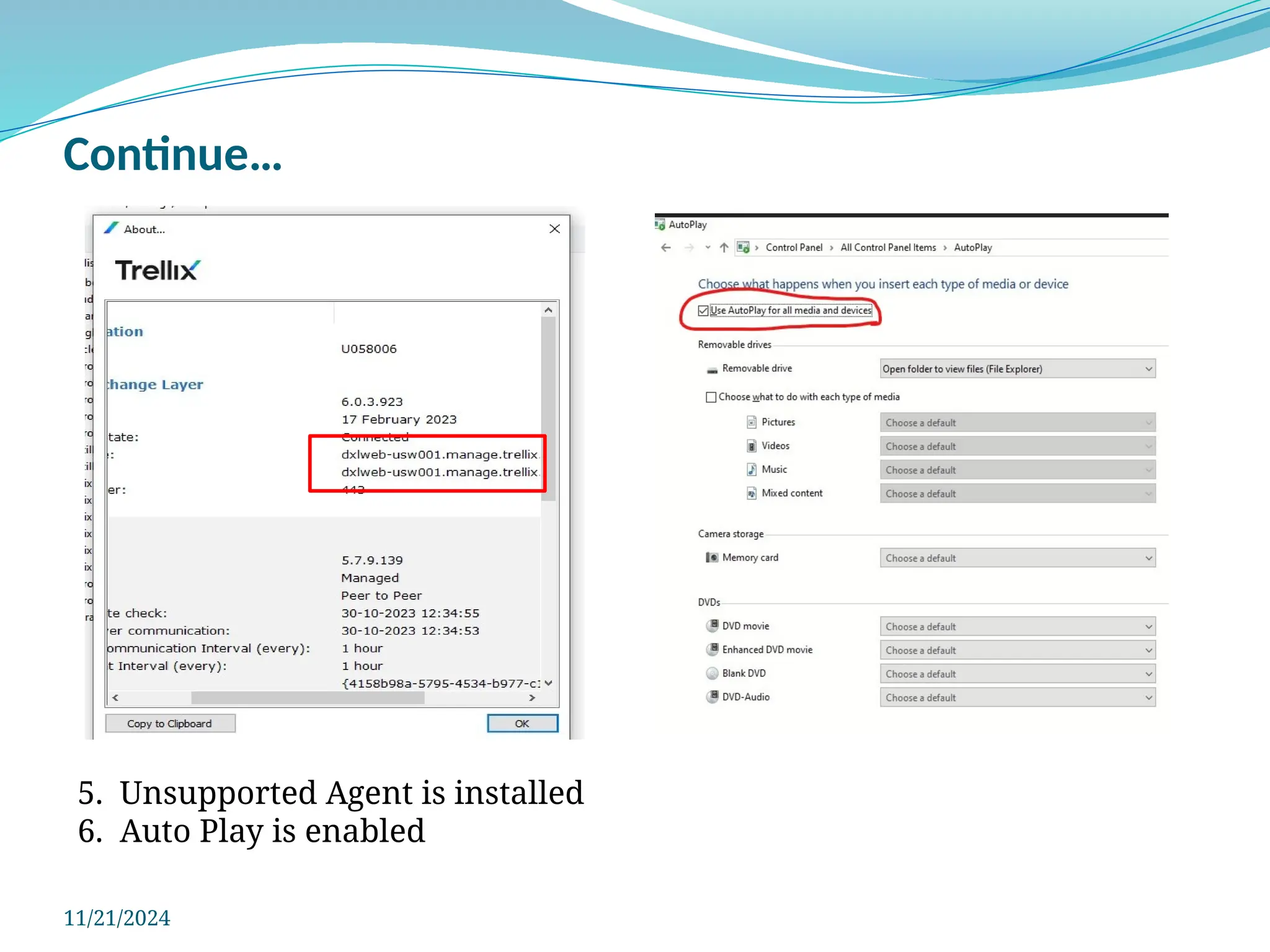
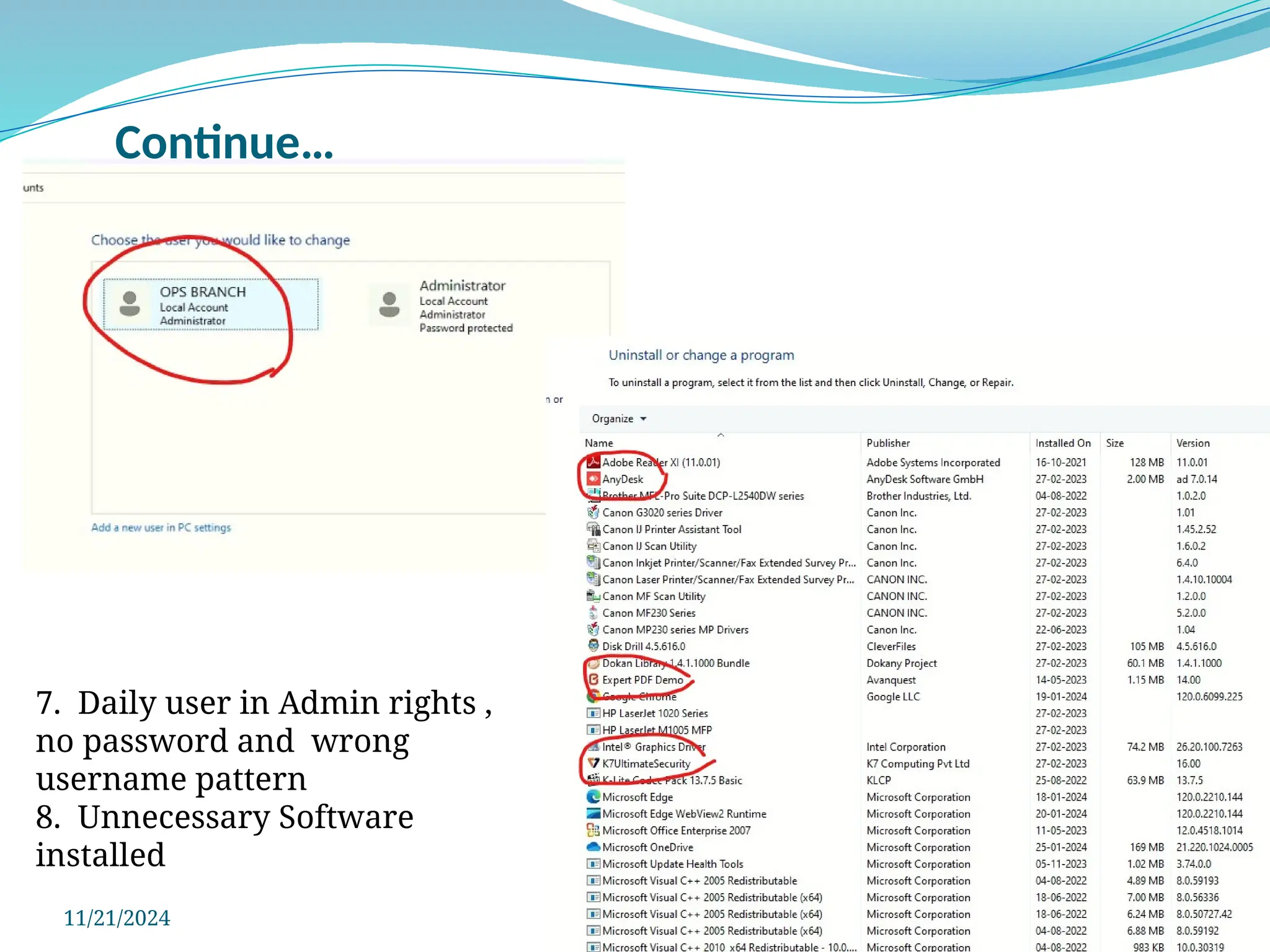
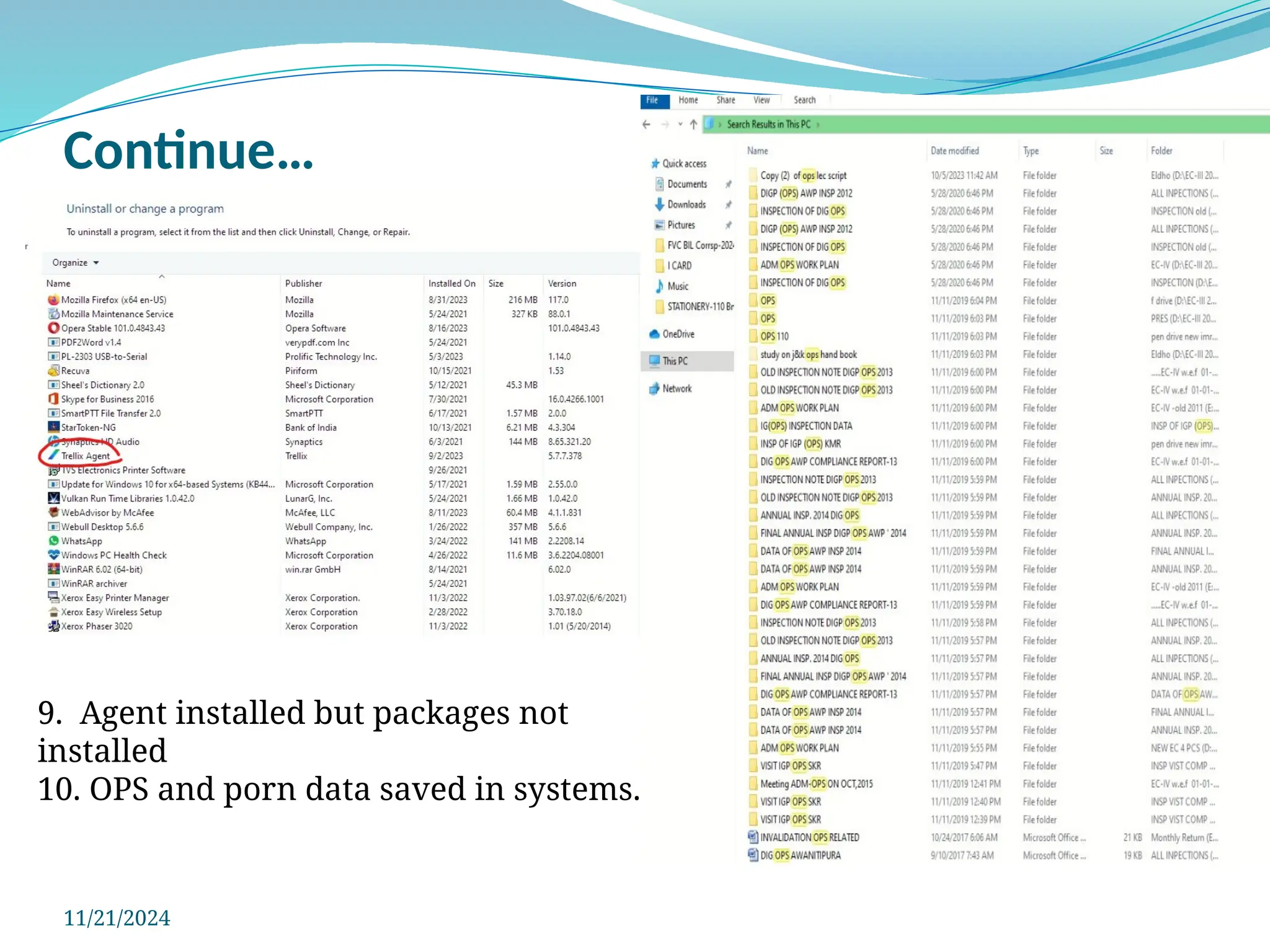
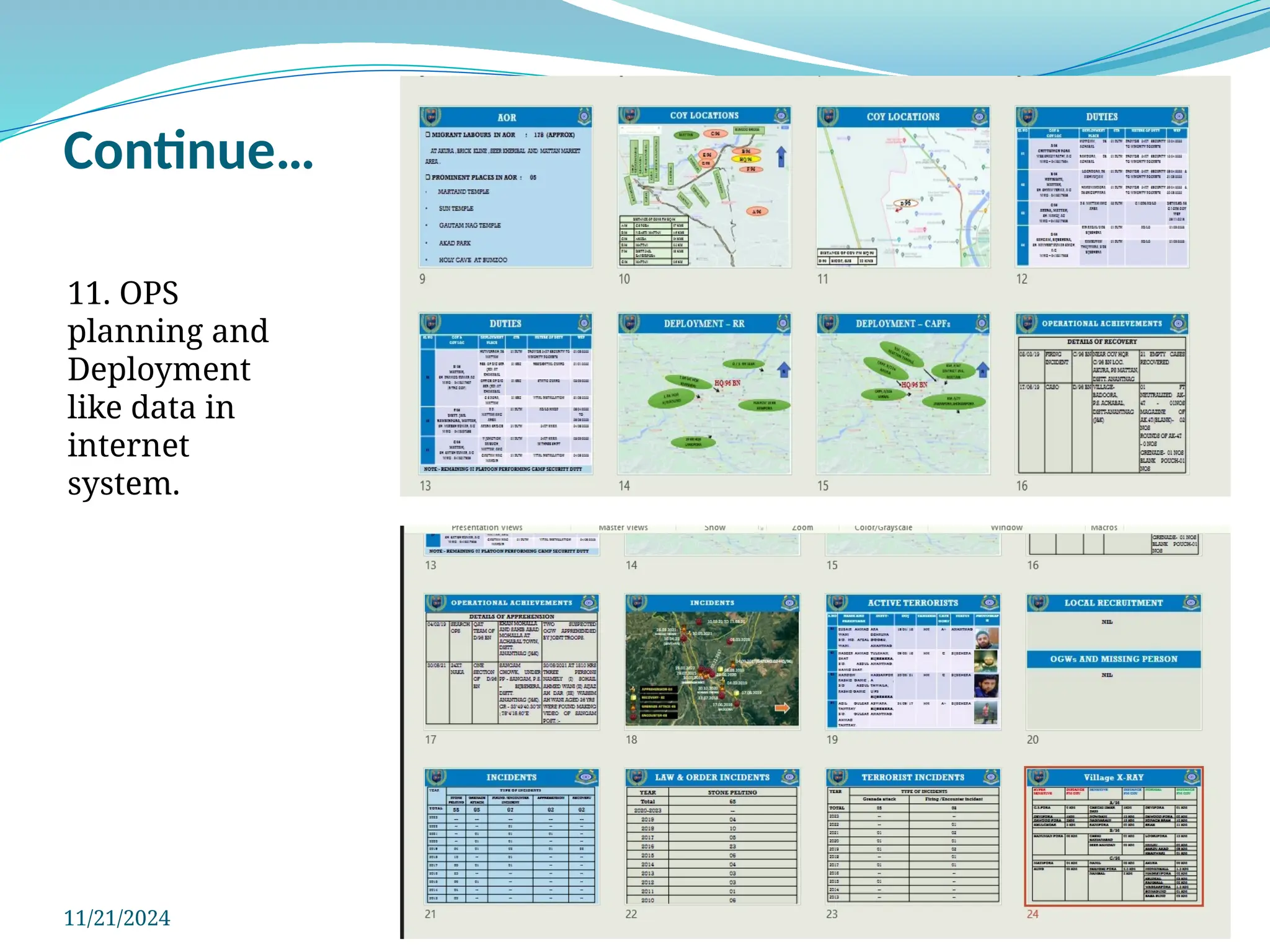
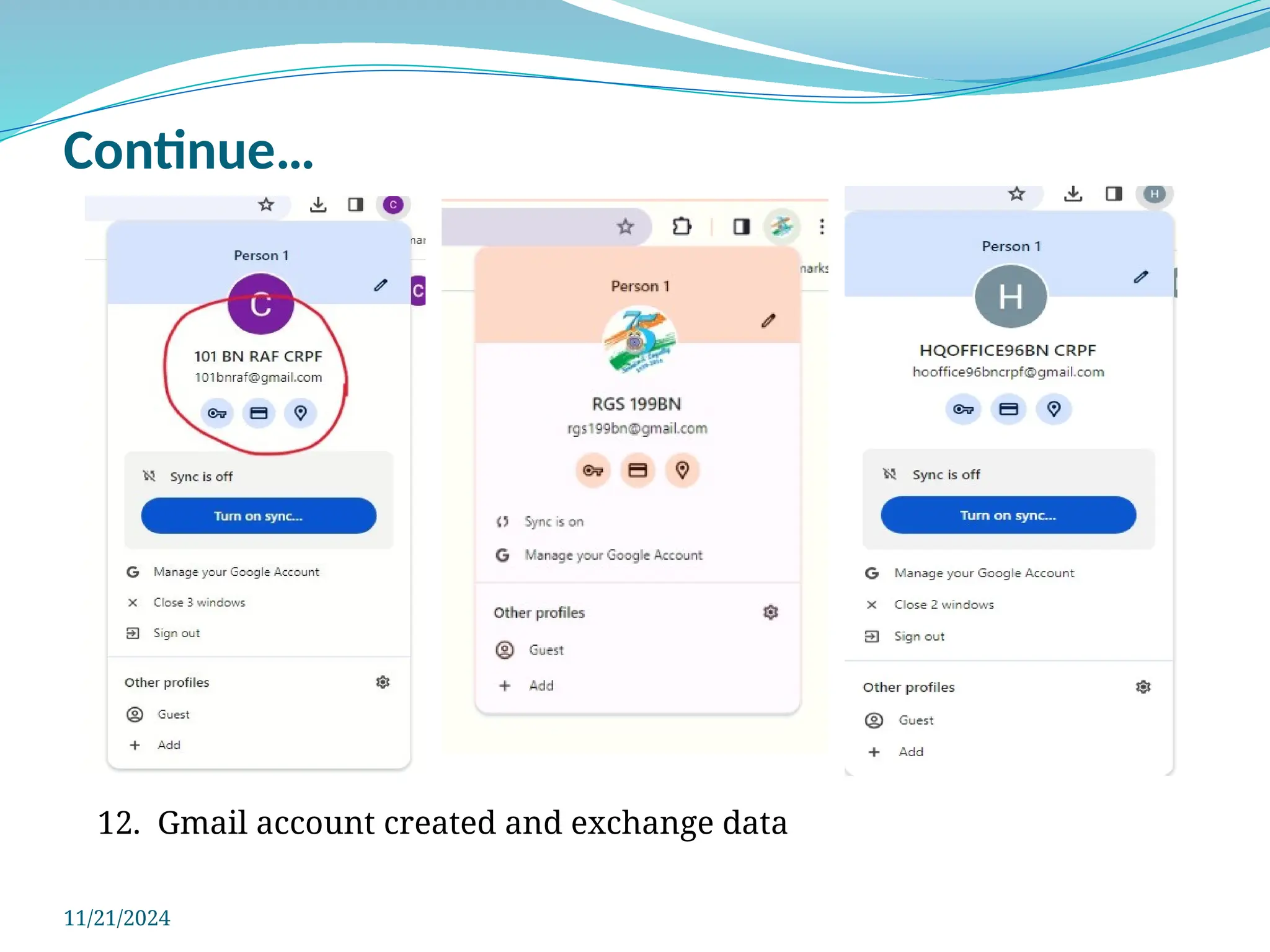
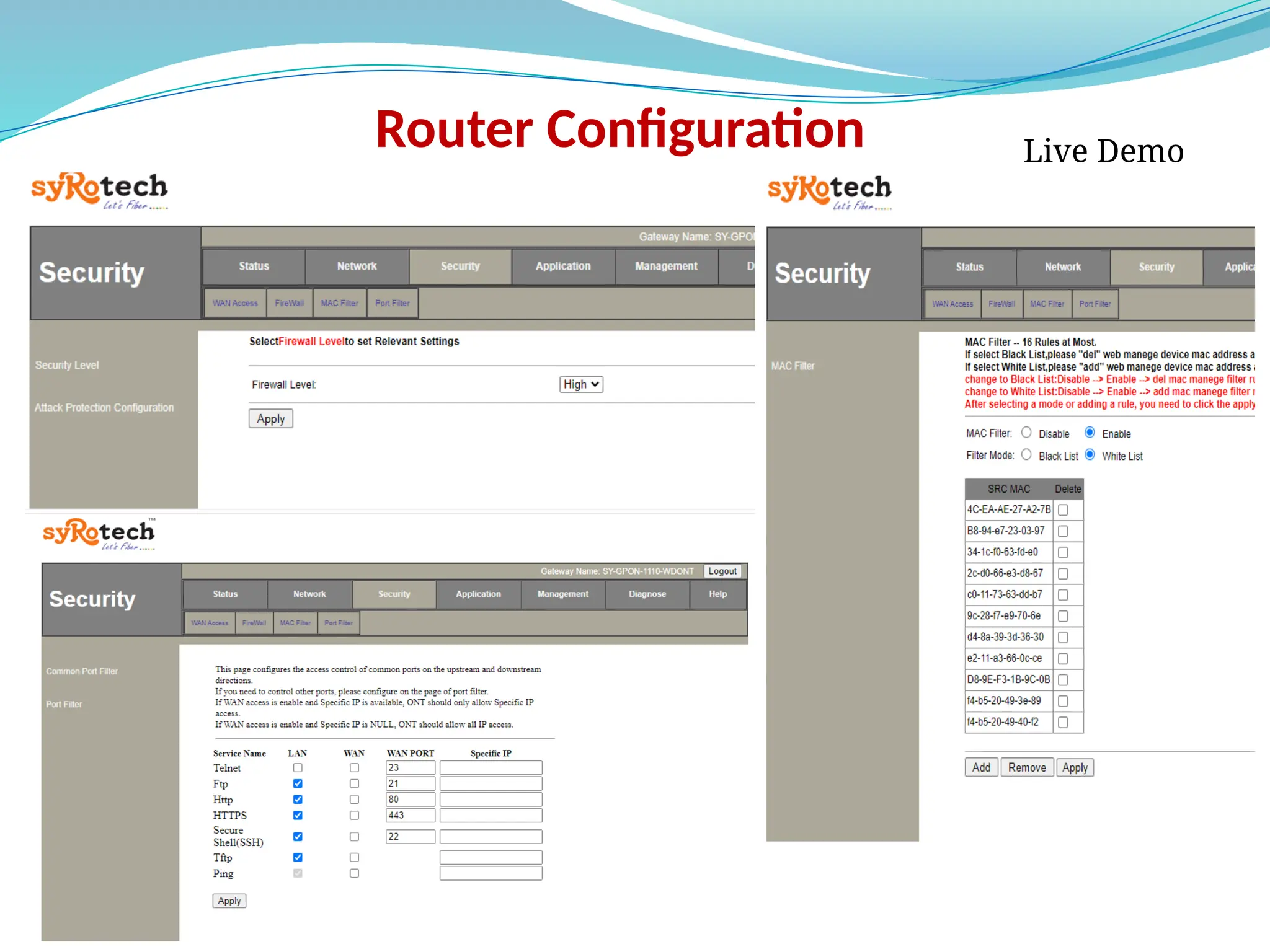
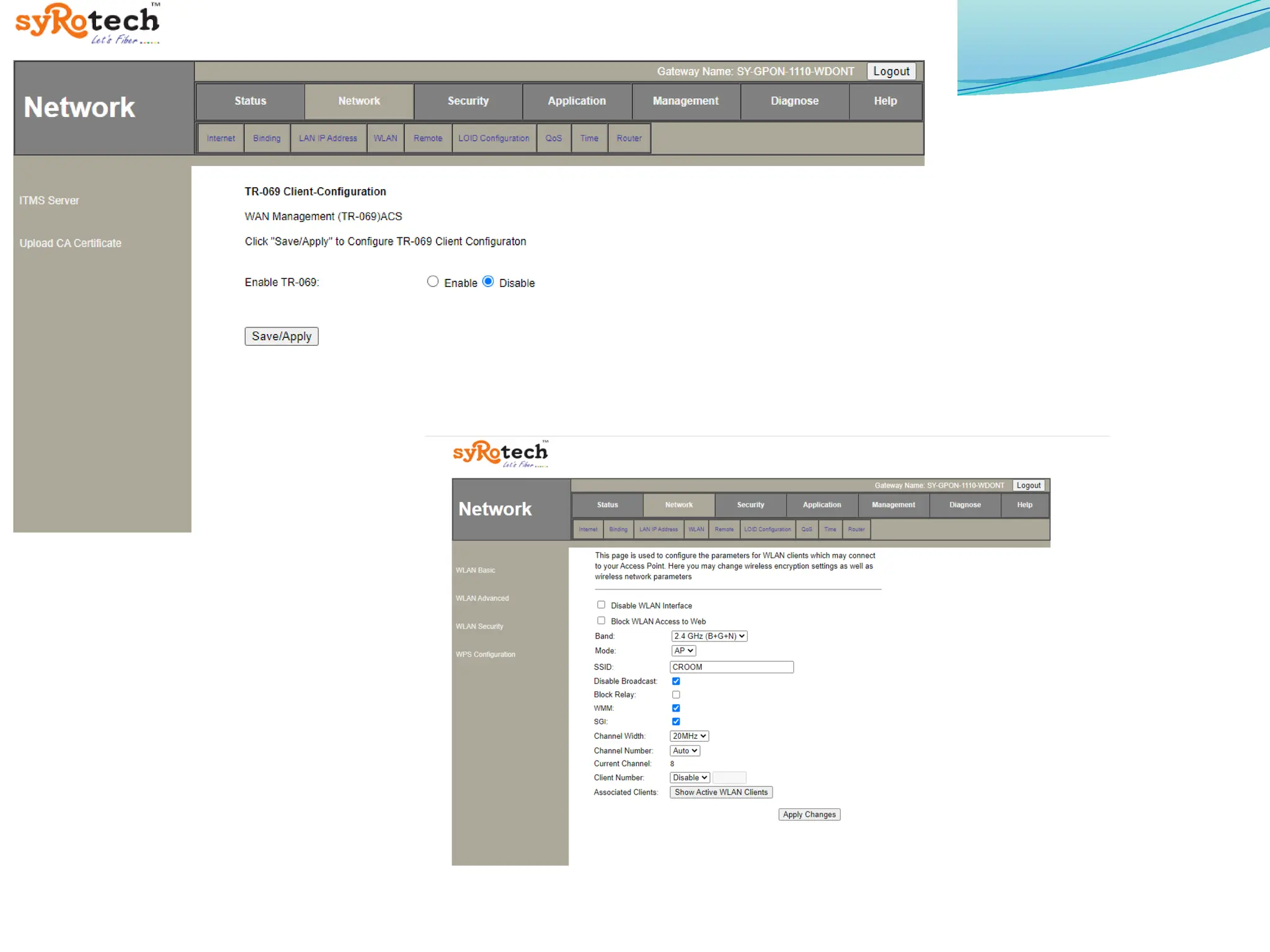
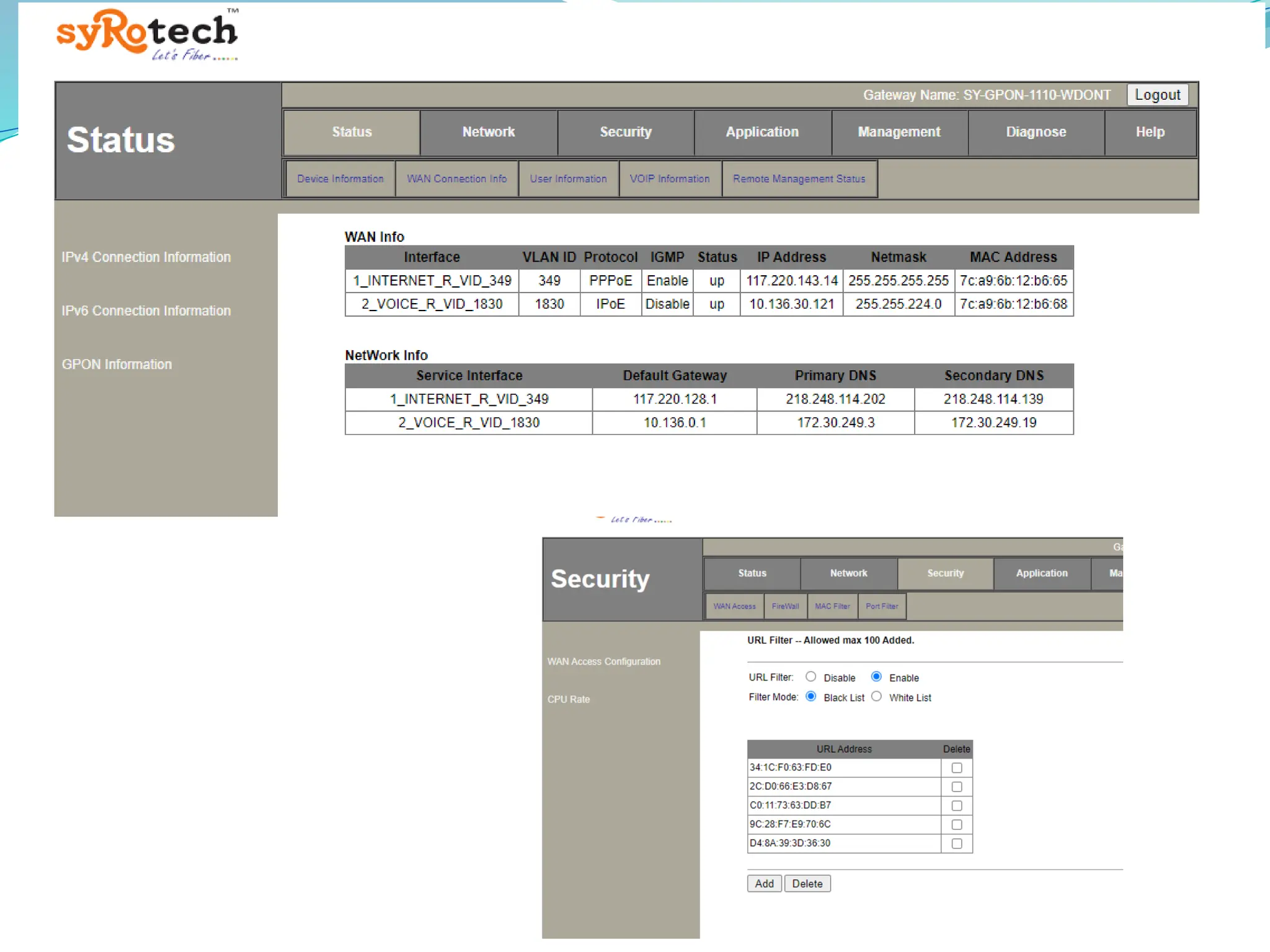
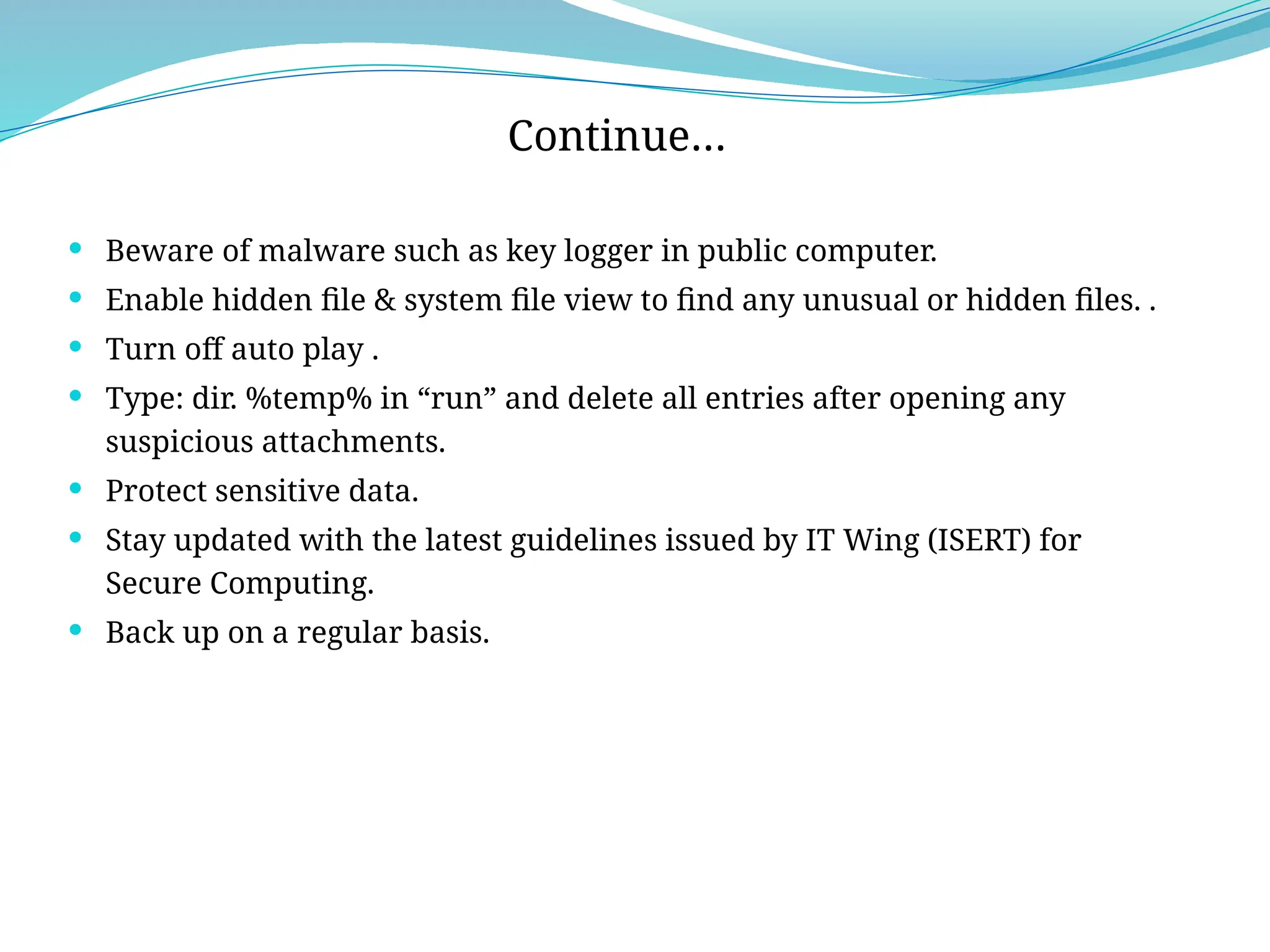
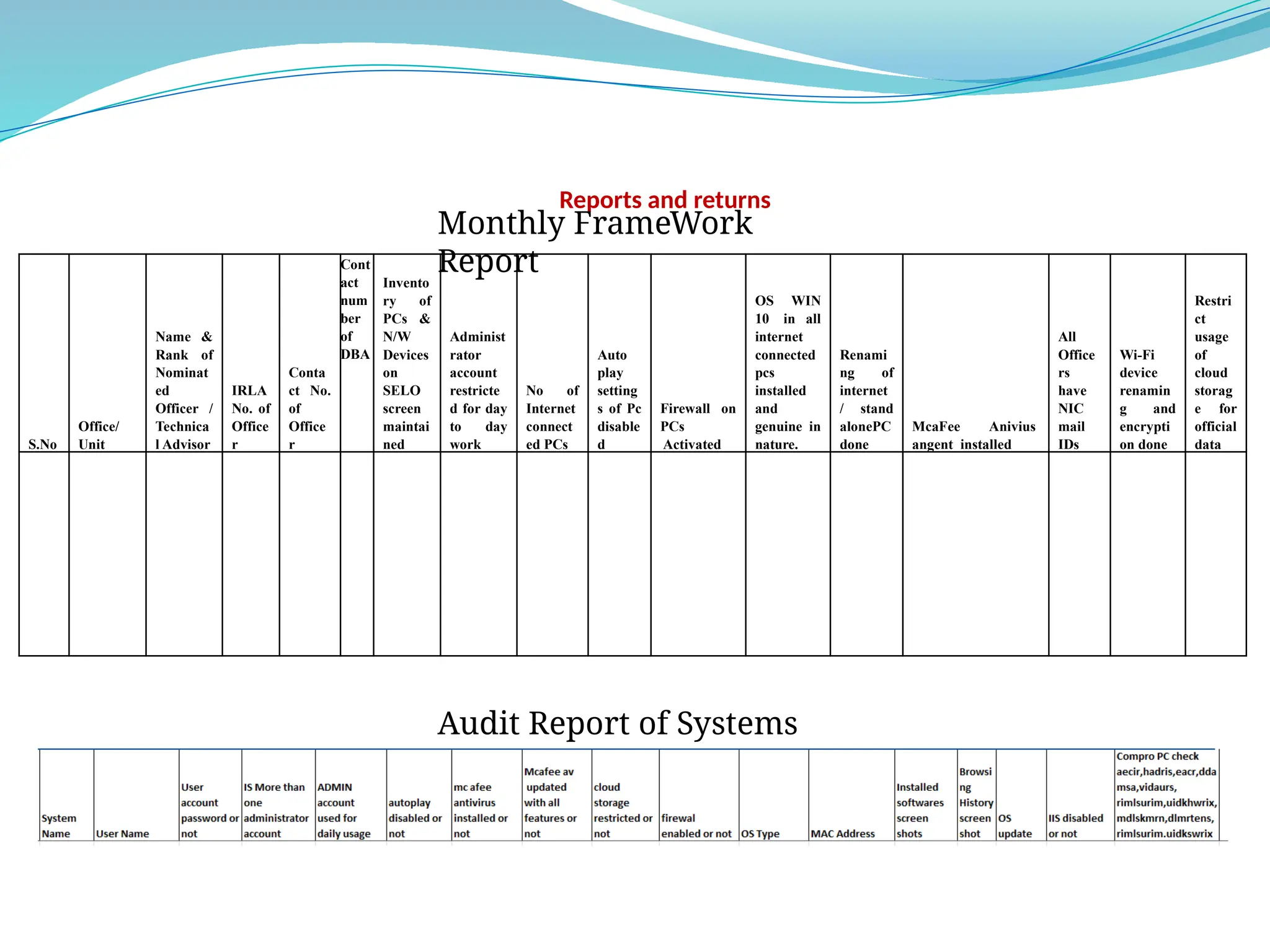
The document outlines a comprehensive cyber security framework and auditing procedures for the Central Reserve Police Force (CRPF), detailing naming conventions for computers, installation of antivirus software, audit checklists, and router configurations. It highlights common shortcomings found during audits, and emphasizes incident response strategies in the event of cyber attacks. Additionally, the document stresses the importance of maintaining proper security protocols for desktops, LAN security, and safe internet browsing practices to protect sensitive information.