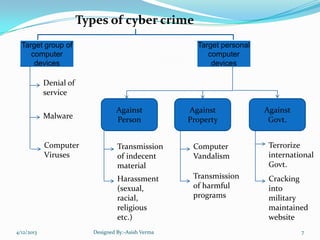
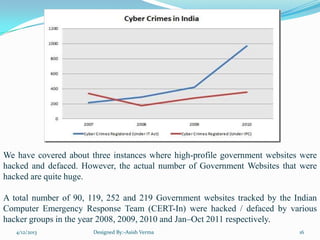
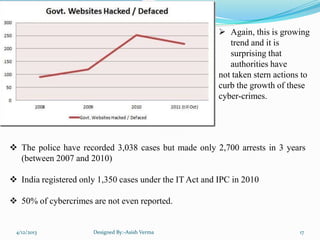
The document summarizes a presentation on cyber crime in India. It discusses what cyber crime is, the history and types of cyber crimes, how crimes are committed, relevant laws, case studies, and recommendations. Cyber crime in India is growing rapidly due to increasing internet usage. Common crimes include phishing, hacking, and identity theft. The document outlines India's IT Act and amendments that created laws to address cyber crimes.















![Information Technology Amendment Act,
2008
Section – 43,
Destroys, Deletes or Alters any Information residing in a computer resource or
diminishes its value or utility or affects it injuriously by any means;
Steals, conceals, destroys or alters or causes any person to steal, conceal, destroy or
alter any computer source code used for a computer resource with an intention to
cause damage;
“If any person, dishonestly, or fraudulently, does any act referred to in section 43, he
shall be punishable with imprisonment for a term which may extend to two three
years or with fine which may extend to five lakh rupees or with both.” [S.66]
4/12/2013 Designed By:-Asish Verma 19](https://image.slidesharecdn.com/ashucybercrime-130813172931-phpapp02/85/Asis-Verma-cyber-crime-ppt-19-320.jpg)







