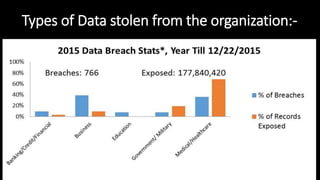
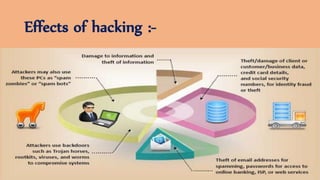
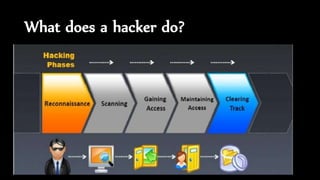
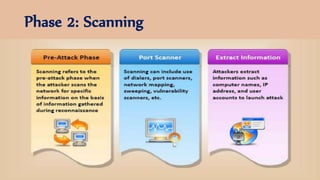
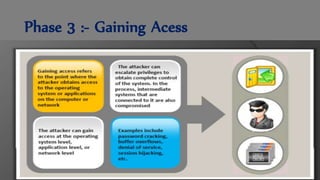
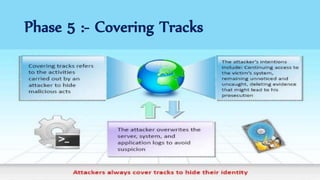
The document discusses ethical hacking, defining it as adherence to standards of right conduct, and contrasts different types of hackers: black hat (malicious), white hat (ethical) and grey hat (between the two). It outlines the history of hacking, starting from the 1960s with skilled programmers at MIT, evolving into various forms including hacktivism and social engineering attacks. The document also details specific attack methods, emphasizing the importance of ethical hackers in securing systems against unauthorized access.